How new tools with unknown origins are monetized.
According to a new Cisco Talos report, Vietnamese hackers have been distributing a new infostealer since May 2023 in order to get their hands on financial data. Called CoralRaider, the campaign targeted victims in India, China, South Korea, Bangladesh, Pakistan, Indonesia and Vietnam.
The attackers ' goal is to steal user credentials, financial information, and social media accounts, including business and advertising accounts. To achieve their goals, hackers use RotBot (a modified version of the Quasar RAT Trojan) and the XClient infostiler. The attackers arsenal also includes AsyncRAT, NetSupport RAT, and Rhadamanthys.
Special attention is paid to business and advertising accounts. After they are stolen using Ducktail and NodeStealer, cybercriminals monetize the accounts. Data from victims computers is exported via Telegram and sold on the black market.
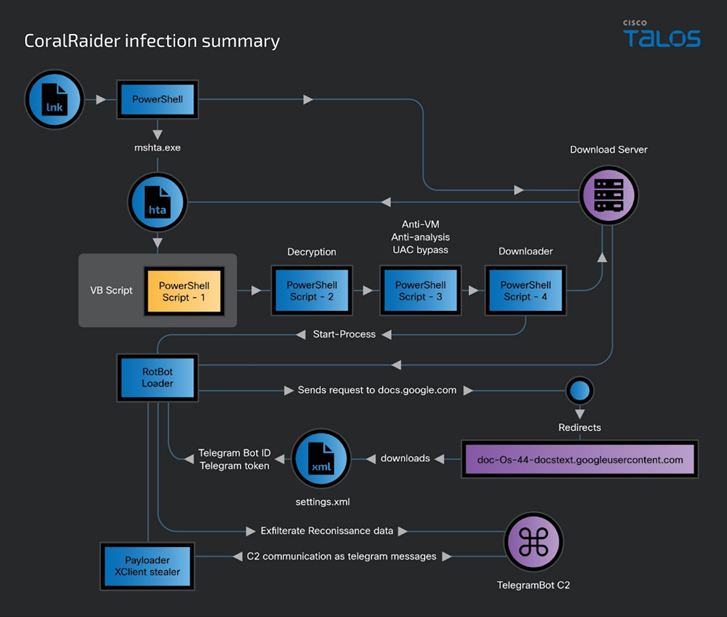
CoralRaider Infection Chain
The attack chain begins with the distribution of the LNK label. At the moment, experts do not know exactly how the labels are delivered to the victims computers. Opening the LNK file loads and executes the HTML application (HTA) from the attackers ' server. The app runs scripts that disable the security system and load RotBot.
RotBot is designed to establish communication with the Telegram bot, deliver the XClient infostiler and execute it in memory, which ultimately leads to the creation of screenshots, theft of cookies, credentials and financial information from various browsers, as well as from Discord and Telegram.
XClient is also designed to exfiltrate data from victims Facebook, Instagram, TikTok, and YouTube accounts, collecting detailed information about payment methods and permissions associated with business and advertising accounts on Facebook.
The researchers claim that CoralRaider operators are based in Vietnam, which is confirmed by messages in their Telegram channels and the preference for the Vietnamese language when naming bots and in malware code.
According to a new Cisco Talos report, Vietnamese hackers have been distributing a new infostealer since May 2023 in order to get their hands on financial data. Called CoralRaider, the campaign targeted victims in India, China, South Korea, Bangladesh, Pakistan, Indonesia and Vietnam.
The attackers ' goal is to steal user credentials, financial information, and social media accounts, including business and advertising accounts. To achieve their goals, hackers use RotBot (a modified version of the Quasar RAT Trojan) and the XClient infostiler. The attackers arsenal also includes AsyncRAT, NetSupport RAT, and Rhadamanthys.
Special attention is paid to business and advertising accounts. After they are stolen using Ducktail and NodeStealer, cybercriminals monetize the accounts. Data from victims computers is exported via Telegram and sold on the black market.

CoralRaider Infection Chain
The attack chain begins with the distribution of the LNK label. At the moment, experts do not know exactly how the labels are delivered to the victims computers. Opening the LNK file loads and executes the HTML application (HTA) from the attackers ' server. The app runs scripts that disable the security system and load RotBot.
RotBot is designed to establish communication with the Telegram bot, deliver the XClient infostiler and execute it in memory, which ultimately leads to the creation of screenshots, theft of cookies, credentials and financial information from various browsers, as well as from Discord and Telegram.
XClient is also designed to exfiltrate data from victims Facebook, Instagram, TikTok, and YouTube accounts, collecting detailed information about payment methods and permissions associated with business and advertising accounts on Facebook.
The researchers claim that CoralRaider operators are based in Vietnam, which is confirmed by messages in their Telegram channels and the preference for the Vietnamese language when naming bots and in malware code.
