High-profile leaks, hacks, and cyberattacks around the world occur weekly. Some of them are forgotten in one day, others become the subject of long discussions.
The main reason for the hype is the sensitivity of leaked data or other tangible" impact " from a cyberattack. But the company's controversial self-positioning during the incident may also contribute.
This article will analyze negative and positive examples of companies ' behavior during an incident from the point of view of positioning in the media sphere.
It is important to mention that such behavior may be justified and appropriate if the statements are true and do not serve as an excuse for ignoring the incident.
However, if the company claims that there is no incident without supporting it with some facts, for example, by analyzing a document posted in public access, then this looks like an unsubstantiated excuse.
The same category includes statements that the incident took place, but the attackers did not gain access to sensitive data, client accounts, and so on.
For example, this position was followed by Apple during the incident with the theft of drawings of its devices. The focus of attention still remained on "Apple", and Quanta Computer appears in the list
It can be assumed that in this particular case, the application is caused by legal aspects and is aimed at preparing a protective base for future claims in advance. However, from the point of view of our own positioning and understanding of how information security works, this is an absolute failure.
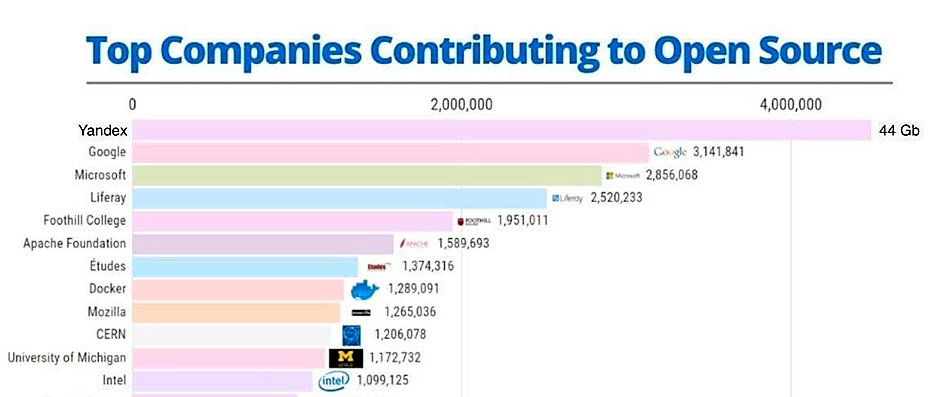
But thanks to the operational work of the company and statements about the irrelevance of the code stolen from repositories, the leak, at least in the Russian information field, was more remembered by memes about Yandex's contribution to Open Source.
In both cases, the companies showed a high level of maturity and readiness to respond quickly not only from the point of view of information security, but also from the point of view of their own positioning for a wide audience.
However, it is necessary to note the general trend of users ' desire to get an objective assessment of the situation from a company that (presumably) faced a cyberattack.
You can deduce three of the most universal tips:
It is important to remember that most people, if the incident did not cause significant losses or other damage, will forget about its details after a month, and the overall impression of the company will remain for a long time.
The main reason for the hype is the sensitivity of leaked data or other tangible" impact " from a cyberattack. But the company's controversial self-positioning during the incident may also contribute.
This article will analyze negative and positive examples of companies ' behavior during an incident from the point of view of positioning in the media sphere.
Not best practices
Considering the practice of recent years, we can distinguish several typical models of behavior of companies during an incident, which, to put it mildly, raise questions either from society or the information security community.It is important to mention that such behavior may be justified and appropriate if the statements are true and do not serve as an excuse for ignoring the incident.
There was no incident
Indeed, you can find quite a few cases where cybercriminals ' claims were false, supported by dubious screenshots, or databases compiled from other leaks. In the Russian segment, the channel "Information Leaks"has repeatedly issued refutations of such leaks.However, if the company claims that there is no incident without supporting it with some facts, for example, by analyzing a document posted in public access, then this looks like an unsubstantiated excuse.
The same category includes statements that the incident took place, but the attackers did not gain access to sensitive data, client accounts, and so on.
It's not us, it's them
The incident occurred in the area of responsibility of the contractor, provider, operator or other person who is not directly related to the company. This approach is probably optimal from the point of view of communication, for example, with the relevant regulator, but not with society, since:- the focus of attention will be on the largest and most well-known company, even if the fault is 100% on the contractor;
- if the contractor is to blame, but the company's users suffer, then distancing looks like an attempt to avoid responsibility.
For example, this position was followed by Apple during the incident with the theft of drawings of its devices. The focus of attention still remained on "Apple", and Quanta Computer appears in the list
It's anyone's fault, but not ours
Some companies in the way of denying their guilt during the incident go so far as to blame their own customers, even if they work in the b2c segment. This is exactly what representatives of 23andMe, a company that deals with genetic research, did.It can be assumed that in this particular case, the application is caused by legal aspects and is aimed at preparing a protective base for future claims in advance. However, from the point of view of our own positioning and understanding of how information security works, this is an absolute failure.
When proper communication helped reduce damage
Along with negative examples that cause a wave of disapproval from users and ironic comments from the profile community, there are also positive examples when companies were able to find the right words, timings and actions to reduce reputational damage from an incident.Investing in Open Source
At the beginning of last year, a large-scale source code leak occurred at Yandex. In the future, it was analyzed by many different researchers who found some use for this data, and according to some statements, even up – to-date data of customers of some services, for example, Yandex contractors, were found.Taxi.But thanks to the operational work of the company and statements about the irrelevance of the code stolen from repositories, the leak, at least in the Russian information field, was more remembered by memes about Yandex's contribution to Open Source.

What about Russian information security companies?
Also last year, there were two incidents with Russian information security companies-BI. ZONE and Infotex. Both stories did not cause serious consequences for their business and did not affect their customers, but they caused a wide discussion in the relevant environment.In both cases, the companies showed a high level of maturity and readiness to respond quickly not only from the point of view of information security, but also from the point of view of their own positioning for a wide audience.
Three recommendations for the company's behavior during the incident
Of course, there are a large number of special cases when a company cannot afford to openly talk about an incident. For the private sector, ransomware attacks are a good example.Dmitry Ovchinnikov
Chief Specialist of the Integrated Information Security Systems Department of Gazinformservis
The practice of denying incidents is quite widely used all over the world, and not only in the field of information security incidents. As soon as there is a public recognition, then after that there is no need to prove anything. The culprit himself confessed and can already be "crucified" in the media. But if you do not admit it, then there is a very high probability that in a week this event will be removed from the information agenda and no one will remember about it. In the modern world of "post-truth", this is usually the case. Therefore, denial, unfortunately, is the most logical action on the part of the management. In addition, if we talk about some countries, they do not have the custom to admit their guilt at all. Hence this result.
Of course, there are still special cases related to state secrets, protection of particularly important information and objects, when incidents must be deliberately hidden from the public in order to minimize damage from the event and not give unnecessary trump cards to opponents.
However, it is necessary to note the general trend of users ' desire to get an objective assessment of the situation from a company that (presumably) faced a cyberattack.
You can deduce three of the most universal tips:
- Manage the subpoena. If within 4-6 hours you have not issued at least a statement that you are studying information on the network or conducting an investigation – the information in the media field will begin to live its own life.
- Don't discount everything on one specialist. PR, information security and the legal department see the incident differently. If you entrust communication to one direction, there is a high risk of repeating the previously described 23andMe "file".
- Give interested people instructions. Regardless of the specifics of the incident, it is important to explain to the user what to do, what to fear, and what to expect. Then they will change their password, not write negative comments.
It is important to remember that most people, if the incident did not cause significant losses or other damage, will forget about its details after a month, and the overall impression of the company will remain for a long time.
