The project allows you to bring the culprit to justice for failures in vital equipment.
A new Python project called Wall of Flippers is designed to detect Bluetooth spam attacks originating from Flipper Zero and Android devices.
Earlier, it became known about a new Bluetooth LE (Bluetooth Low Energy, BLE) attack using Flipper Zero, during which Apple devices received false notifications about connecting via Bluetooth. However, soon other developers created a special firmware for Flipper Zero, which allows spam attacks on Android smartphones and Windows laptops. Then developer Simon Dunkelmann adapted the attack for the Android app, which allowed attacks to be carried out without using Flipper Zero.
Visitors to the Midwest FurFest 2023 conference felt the effects of these attacks. Many people have experienced problems with Square payment terminals, and in some cases there are more serious threats, such as failures in the operation of insulin pump controllers. Users of hearing aids and heart rate monitoring devices also reported problems.
A researcher from the company Greynoise under the nickname "remy" shared information about the risks of such attacks. He warned that BLE spam can seriously affect the health of victims. For BTLE-enabled medical equipment, even minor disruptions can worsen the quality of life of those affected.
While some claim that Apple has quietly introduced measures to counter BLE attacks in iOS 17.2, this issue has not yet been resolved in Android. BleepingComputer conducted tests and found that BLE spam from Android devices to iOS devices still works after installing iOS 17.2. Google has not yet received a response about plans to solve this problem.
The Wall of Flippers (WoF) project aims to detect attackers conducting Bluetooth LE spam attacks so that victims can respond quickly. The Python script is designed to run continuously on Linux and Windows, constantly notifying the user about the status of nearby BTLE devices, potential threats, and general activity.
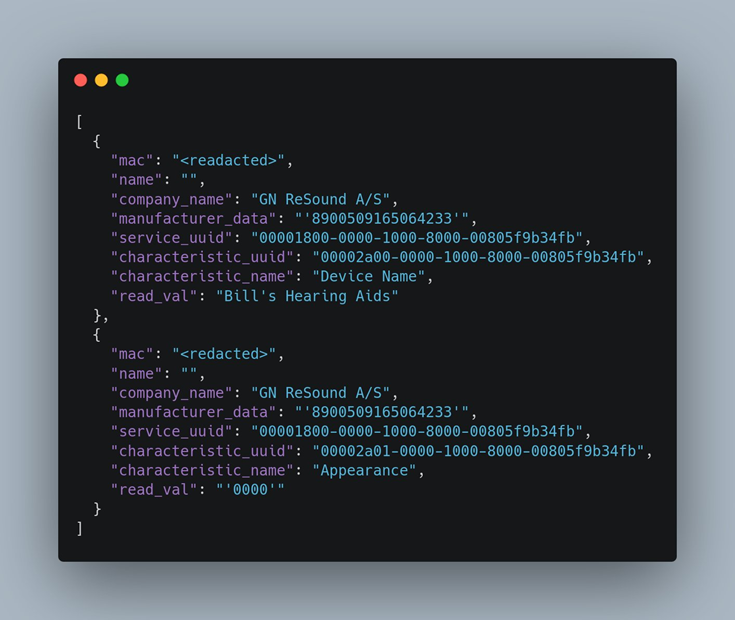
WoF scans BTLE packets in the vicinity and analyzes the transmitted packets for compliance with predefined patterns that are considered signs of malicious activity. Threats detected include Flipper Zero attacks and spam on iOS, Android, and Windows. WoF captures the MAC address of the "spam" device, signal strength, and data contained in the packets.
Instructions for installing WoF and configuring the project can be found in the developer's GitHub repository. To make sure that the script is secure, we recommend checking the code before installing it.
A new Python project called Wall of Flippers is designed to detect Bluetooth spam attacks originating from Flipper Zero and Android devices.
Earlier, it became known about a new Bluetooth LE (Bluetooth Low Energy, BLE) attack using Flipper Zero, during which Apple devices received false notifications about connecting via Bluetooth. However, soon other developers created a special firmware for Flipper Zero, which allows spam attacks on Android smartphones and Windows laptops. Then developer Simon Dunkelmann adapted the attack for the Android app, which allowed attacks to be carried out without using Flipper Zero.
Visitors to the Midwest FurFest 2023 conference felt the effects of these attacks. Many people have experienced problems with Square payment terminals, and in some cases there are more serious threats, such as failures in the operation of insulin pump controllers. Users of hearing aids and heart rate monitoring devices also reported problems.
A researcher from the company Greynoise under the nickname "remy" shared information about the risks of such attacks. He warned that BLE spam can seriously affect the health of victims. For BTLE-enabled medical equipment, even minor disruptions can worsen the quality of life of those affected.
While some claim that Apple has quietly introduced measures to counter BLE attacks in iOS 17.2, this issue has not yet been resolved in Android. BleepingComputer conducted tests and found that BLE spam from Android devices to iOS devices still works after installing iOS 17.2. Google has not yet received a response about plans to solve this problem.
The Wall of Flippers (WoF) project aims to detect attackers conducting Bluetooth LE spam attacks so that victims can respond quickly. The Python script is designed to run continuously on Linux and Windows, constantly notifying the user about the status of nearby BTLE devices, potential threats, and general activity.

WoF scans BTLE packets in the vicinity and analyzes the transmitted packets for compliance with predefined patterns that are considered signs of malicious activity. Threats detected include Flipper Zero attacks and spam on iOS, Android, and Windows. WoF captures the MAC address of the "spam" device, signal strength, and data contained in the packets.
Instructions for installing WoF and configuring the project can be found in the developer's GitHub repository. To make sure that the script is secure, we recommend checking the code before installing it.
