Let's analyze the methods of penetration through a USB flash drive.
As a rule, most pentests are conducted according to a fairly simple scheme. First, with the help of social engineering, access to the target environment or its separate link is provided, and then it is infected with technical means.
Variations in the conduct of an attack can be different, but usually the classic penetration test is a fusion of technical part and social engineering in very different proportions. The disadvantage of the classic pentest is that you need to "grope" for that very employee and then move on to the next stage. If it were possible to automate the process of finding the weak link and its further exploitation, then this could speed up the process of penetration testing and significantly increase the ultimate chances of success.
In addition, any functioning system can be influenced by a number of random factors, which can also temporarily paralyze the security system:
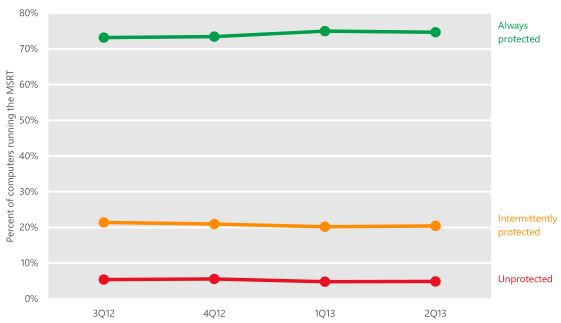
Percentage of computers for real-time protection
In fact, the task boils down to the following: determine that at the moment one of the random events has occurred, which led to a decrease in security, and then use this situation as a disguise and carry out an attack unnoticed.
In fact, the task comes down to finding a person who neglects security, and why not use flash drives for this?
Many virus writers are very fond of flash media, as they allow you to easily and quickly infect computers, and even the most basic USB virus has a good chance of success. The boom of autorun viruses that took place in 2008 does not slow down five years later, moreover, USB viruses have become even bolder and sometimes do not even hide their presence.
And at the same time, an infected flash drive is a universal indicator of the literacy of its owner in the matter of elementary information security. For example, if you collect ten flash drives from different people, then surely three or four of them will have viruses on the flash drives. If, after a week, you re-take the flash drives from these people, then two or three of them will have viruses.
Based on this, it can be argued that even the most basic protection is not needed on the computers with which they work from this flash drive, or for some reason it is disabled or does not work at all. Thus, even if the most common virus, which is successfully detected by all antiviruses, is distributed only among this group of people, it will be able to infect a large number of computers before being detected. And since these computers do not have protection, then it will also be able to remain operational for a long time.
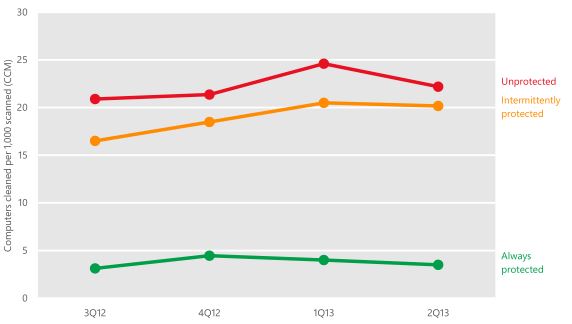
Exposure to computer threats based on the availability of real-time protection
Implementation
On a specific computer, to which flash drives are periodically connected, we install a special program that works according to the following algorithm. When connecting another flash drive, the program tries to determine if it is infected. Since it is impossible to take into account all the variety of USB viruses, it makes sense to use a heuristic approach to determine infection based on the following criteria:
If this flash drive is infected, the program writes it to the database indicating the serial number and hash of the suspicious file. If after a few days the flash drive is reconnected to this computer (and this happens almost always) and suspicious files still remain on it, then it is infected with our "virus"; if there is no suspicious file left, the program deletes the serial number of this flash drive from the database. When a new computer becomes infected, the virus remembers the serial number of the mother's flash drive and never infects or analyzes it, so that after a while it does not give itself out if the owner of the flash drive “grows wiser”.
To get the serial number, let's write the following function based on the GetVolumeInformation API:
It should be noted that the GetFlashSerial function does not receive a static unique device identifier, but only the volume serial number. This number is a random number and usually changes every time the device is formatted. For our purposes, only the serial number of the flash drive is enough, since the task of hard binding is not worth it, and formatting implies the complete destruction of information, in fact equating the formatted USB flash drive with a new one.
Now let's start implementing the heuristic itself.
bool IsItABadFlash (Ansi String DriveLetter)
The algorithm of the heuristic function is quite simple. First, we filter out all NTFS devices and those that do not contain the autorun.inf file. As a rule, all flash drives come with the FAT32 file system by default (less often FAT and even less often exFAT), but sometimes system administrators or other IT department employees format them into NTFS for their needs. We do not need "smart people", we immediately exclude them.
The next step is to check the autorun.inf file for the "hidden" and "system" attributes. The autorun.inf file may also belong to a completely legitimate program, but if these attributes are present in it, then it is very likely that the flash drive is infected with a virus.
Many virus writers are now less likely to use the autorun.inf file to infect machines. There are several reasons at once: firstly, almost all antiviruses or users disable the autorun option; secondly, there may be several viruses on the computer that use the same distribution method, and each of them overwrites the file in its own way. Therefore, the method of infection through creating shortcuts and hiding the original folders has been increasingly used. In order not to leave these flash drives unattended, we check for the presence of a shortcut file and the presence of a folder with the same name in the root of the volume. If the folder also has the attributes "hidden" and "system", then we mark this USB flash drive as infected.
Of course, the heuristic has its own inaccuracies and nuances, so it makes sense to work it out carefully for a specific task, but in our case it is possible to assert its correctness with 100% probability.
While everything is generally clear with the heuristic analysis of a flash drive, nuances are possible with the "infection". For example, you can simply overwrite an old virus with ours without any amendments to the autorun.inf file, files, shortcuts, etc. Thus, our "virus" will gain control on a new computer, but it is better to make an old copy of the virus and save it in the same directory with a slightly different name.
If for some reason an antivirus is running on another computer, it will detect the old virus, remove it, give the user a warning about the successful destruction of the threat - and thereby provide a false sense of security for the user, and our "virus" will remain unnoticed.
In addition, in the December issue of Hacker, we also wrote about DLL hijacking vulnerabilities in various software and its effective use. Therefore, if it is assumed that programs such as password managers or portable versions of various software may be on the flash drives, then it makes sense to exploit this vulnerability and thereby expand the range of affected machines and the value of the obtained data for penetration testing.
By the way, it does not always make sense to resort to infecting flash drives. For example, if the information security department has the task of simply periodically monitoring employees for the presence of "unreliable people", then it is wiser to install this program on several machines and just write down the serial numbers of flash drives and the time the malicious file was created to collect statistics. Thus, it is not required to literally search all employees, while maintaining the confidentiality of data on flash drives, and on the basis of the data obtained, one can also judge about possible infection of users' home computers and the state of information security in general. After all, as we wrote earlier, any system is subject to random factors and the risk of threats is not excluded.
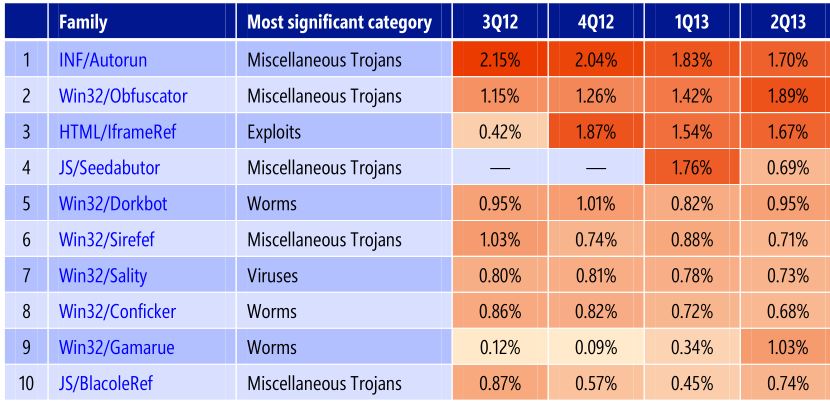
Values of the most popular threats
Testing
Having deployed the program in a relatively medium-sized network, a week later we received quite eloquent data. More than 20% of all connected flash drives were infected with some kind of virus or trojan, and more than 15% were still infected when reconnected after a couple of days. It should also be noted that many computers had anti-virus protection, which periodically performed its duties. However, the usual indifference to the pop-up antivirus warning that users have long been accustomed to when connecting a flash drive did not allow them to assume that they were dealing with a completely different threat. A false sense of security allowed users to connect a USB flash drive to various computers without embarrassment, and our program was able to successfully do its job.
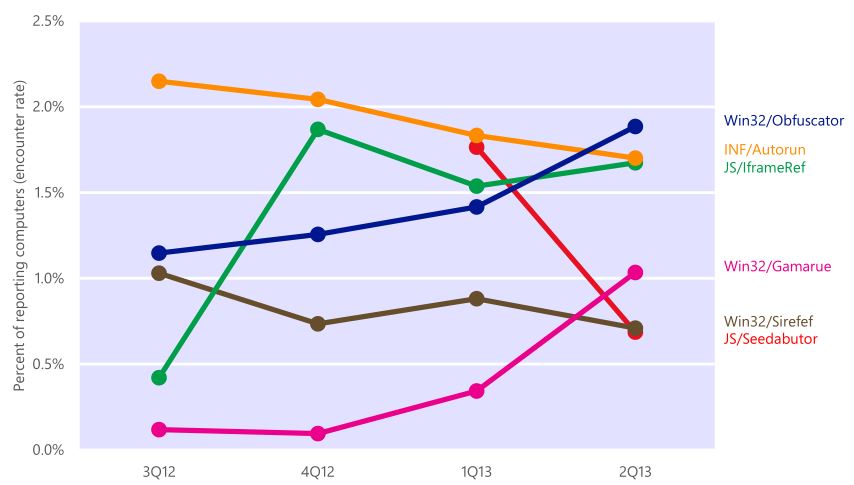
Graphical comparison of the most popular threats
Briefly about the algorithm
Summing up, we can say that the main disadvantage of this method is its uncertainty. Nobody knows when exactly the "suitable" flash drive will be connected to the computer, since it strongly depends on the environment in which the program is deployed. However, this disadvantage does not diminish the main advantage of the method. You can go unnoticed for a very long time and, dissolving among other threats, hit more and more new cars in fully automatic mode. It is easy to see that this technique has a certain economies of scale. The more employees work in the organization and the more diverse the internal communications, the greater the result will be.
xakep.ru
As a rule, most pentests are conducted according to a fairly simple scheme. First, with the help of social engineering, access to the target environment or its separate link is provided, and then it is infected with technical means.
Variations in the conduct of an attack can be different, but usually the classic penetration test is a fusion of technical part and social engineering in very different proportions. The disadvantage of the classic pentest is that you need to "grope" for that very employee and then move on to the next stage. If it were possible to automate the process of finding the weak link and its further exploitation, then this could speed up the process of penetration testing and significantly increase the ultimate chances of success.
Based on this, it can be argued that in any average company there is a certain group of people who are very dismissive of information security, and, in turn, it is these people who should be used to carry out an attack.According to the well-known statistics provided by antivirus companies, about 30% of users do not use antivirus programs, they simply turn them off or do not update their databases.
In addition, any functioning system can be influenced by a number of random factors, which can also temporarily paralyze the security system:
- the proxy server settings have failed, due to which the anti-virus databases have not been updated;
- the term of the antivirus license expired, and the management did not take care of its renewal in time;
- a network failure made it impossible to print files remotely, which forced all employees to copy documents to a USB flash drive and print them in another department.

Percentage of computers for real-time protection
In fact, the task boils down to the following: determine that at the moment one of the random events has occurred, which led to a decrease in security, and then use this situation as a disguise and carry out an attack unnoticed.
In fact, the task comes down to finding a person who neglects security, and why not use flash drives for this?
Many virus writers are very fond of flash media, as they allow you to easily and quickly infect computers, and even the most basic USB virus has a good chance of success. The boom of autorun viruses that took place in 2008 does not slow down five years later, moreover, USB viruses have become even bolder and sometimes do not even hide their presence.
And at the same time, an infected flash drive is a universal indicator of the literacy of its owner in the matter of elementary information security. For example, if you collect ten flash drives from different people, then surely three or four of them will have viruses on the flash drives. If, after a week, you re-take the flash drives from these people, then two or three of them will have viruses.
Based on this, it can be argued that even the most basic protection is not needed on the computers with which they work from this flash drive, or for some reason it is disabled or does not work at all. Thus, even if the most common virus, which is successfully detected by all antiviruses, is distributed only among this group of people, it will be able to infect a large number of computers before being detected. And since these computers do not have protection, then it will also be able to remain operational for a long time.

Exposure to computer threats based on the availability of real-time protection
Implementation
On a specific computer, to which flash drives are periodically connected, we install a special program that works according to the following algorithm. When connecting another flash drive, the program tries to determine if it is infected. Since it is impossible to take into account all the variety of USB viruses, it makes sense to use a heuristic approach to determine infection based on the following criteria:
- the presence of the autorun.inf file;
- RHS file attributes
- small size of the suspicious file;
- the file system is not NTFS;
- absence of a folder named autorun.inf;
- the presence of shortcut files.
If this flash drive is infected, the program writes it to the database indicating the serial number and hash of the suspicious file. If after a few days the flash drive is reconnected to this computer (and this happens almost always) and suspicious files still remain on it, then it is infected with our "virus"; if there is no suspicious file left, the program deletes the serial number of this flash drive from the database. When a new computer becomes infected, the virus remembers the serial number of the mother's flash drive and never infects or analyzes it, so that after a while it does not give itself out if the owner of the flash drive “grows wiser”.
To get the serial number, let's write the following function based on the GetVolumeInformation API:
Code:
String GetFlashSerial(AnsiString DriveLetter)
{
DWORD NotUsed;
DWORD VolumeFlags;
char VolumeInfo[MAX_PATH];
DWORD VolumeSerialNumber;
GetVolumeInformation( AnsiString(DriveLetter + ":\\").c_str() ,
NULL, sizeof(VolumeInfo), &VolumeSerialNumber, &NotUsed,
&VolumeFlags, NULL, 0);
String S;
return S.sprintf("%X", VolumeSerialNumber);
}It should be noted that the GetFlashSerial function does not receive a static unique device identifier, but only the volume serial number. This number is a random number and usually changes every time the device is formatted. For our purposes, only the serial number of the flash drive is enough, since the task of hard binding is not worth it, and formatting implies the complete destruction of information, in fact equating the formatted USB flash drive with a new one.
Now let's start implementing the heuristic itself.
bool IsItABadFlash (Ansi String DriveLetter)
The algorithm of the heuristic function is quite simple. First, we filter out all NTFS devices and those that do not contain the autorun.inf file. As a rule, all flash drives come with the FAT32 file system by default (less often FAT and even less often exFAT), but sometimes system administrators or other IT department employees format them into NTFS for their needs. We do not need "smart people", we immediately exclude them.
The next step is to check the autorun.inf file for the "hidden" and "system" attributes. The autorun.inf file may also belong to a completely legitimate program, but if these attributes are present in it, then it is very likely that the flash drive is infected with a virus.
Many virus writers are now less likely to use the autorun.inf file to infect machines. There are several reasons at once: firstly, almost all antiviruses or users disable the autorun option; secondly, there may be several viruses on the computer that use the same distribution method, and each of them overwrites the file in its own way. Therefore, the method of infection through creating shortcuts and hiding the original folders has been increasingly used. In order not to leave these flash drives unattended, we check for the presence of a shortcut file and the presence of a folder with the same name in the root of the volume. If the folder also has the attributes "hidden" and "system", then we mark this USB flash drive as infected.
Of course, the heuristic has its own inaccuracies and nuances, so it makes sense to work it out carefully for a specific task, but in our case it is possible to assert its correctness with 100% probability.
While everything is generally clear with the heuristic analysis of a flash drive, nuances are possible with the "infection". For example, you can simply overwrite an old virus with ours without any amendments to the autorun.inf file, files, shortcuts, etc. Thus, our "virus" will gain control on a new computer, but it is better to make an old copy of the virus and save it in the same directory with a slightly different name.
If for some reason an antivirus is running on another computer, it will detect the old virus, remove it, give the user a warning about the successful destruction of the threat - and thereby provide a false sense of security for the user, and our "virus" will remain unnoticed.
In addition, in the December issue of Hacker, we also wrote about DLL hijacking vulnerabilities in various software and its effective use. Therefore, if it is assumed that programs such as password managers or portable versions of various software may be on the flash drives, then it makes sense to exploit this vulnerability and thereby expand the range of affected machines and the value of the obtained data for penetration testing.
By the way, it does not always make sense to resort to infecting flash drives. For example, if the information security department has the task of simply periodically monitoring employees for the presence of "unreliable people", then it is wiser to install this program on several machines and just write down the serial numbers of flash drives and the time the malicious file was created to collect statistics. Thus, it is not required to literally search all employees, while maintaining the confidentiality of data on flash drives, and on the basis of the data obtained, one can also judge about possible infection of users' home computers and the state of information security in general. After all, as we wrote earlier, any system is subject to random factors and the risk of threats is not excluded.

Values of the most popular threats
Testing
Having deployed the program in a relatively medium-sized network, a week later we received quite eloquent data. More than 20% of all connected flash drives were infected with some kind of virus or trojan, and more than 15% were still infected when reconnected after a couple of days. It should also be noted that many computers had anti-virus protection, which periodically performed its duties. However, the usual indifference to the pop-up antivirus warning that users have long been accustomed to when connecting a flash drive did not allow them to assume that they were dealing with a completely different threat. A false sense of security allowed users to connect a USB flash drive to various computers without embarrassment, and our program was able to successfully do its job.

Graphical comparison of the most popular threats
Briefly about the algorithm
- We install our program on computers in the company.
- We scan plug-in flash drives for signs of infection.
- We "infect" users' flash drives with our test "virus" or rewrite their numbers for statistics.
- We report to the authorities, punish the gouging users, keep them, do not let them in, and prohibit them.
Summing up, we can say that the main disadvantage of this method is its uncertainty. Nobody knows when exactly the "suitable" flash drive will be connected to the computer, since it strongly depends on the environment in which the program is deployed. However, this disadvantage does not diminish the main advantage of the method. You can go unnoticed for a very long time and, dissolving among other threats, hit more and more new cars in fully automatic mode. It is easy to see that this technique has a certain economies of scale. The more employees work in the organization and the more diverse the internal communications, the greater the result will be.
Although this approach will work perfectly in a structure of absolutely any scale, because its main task is reduced not to a massive defeat of the system, but to a targeted strike at the weakest link - a person.
xakep.ru
