The Insikt Group team (Recorded Future project) investigated the capabilities, culture, and organization principles of Chinese and Russian hacking communities. To do this, the guys analyzed advertisements, created fictitious accounts, and communicated with participants in hacking forums.
Recorded Future-the company tracks everything that happens on the Internet in real time. Predicts and analyzes cyber threats. It works with the support of the CIA and Google.
If you're interested in hacker culture: what drives their actions, how communities work, and where to expect threats from-read our extract from the Insikt Group study. We squeezed out the most interesting things + our thoughts on this matter.
As Insikt Group notes, most often we talk about hackers as an abstract mass. But in fact, there are several very different communities in this environment with their own history, motives and, if you want, code. Each country's hackers are unique. Often researchers do not take this into account — they talk about everyone at once or single out Russians.
Insikt Group employees compared the leaders of the cyber-criminal world: Russians and Chinese. And we started with their history.
As Insikt Group notes: although both Chinese and Russian carder groups come from similar authoritarian states — their history and motives are different.
Russian-speaking cybercriminals value money first, although the phenomenon of financially motivated hacking itself originated in the United States.

Homepage of the Counterfeit Library, one of the first forums for carders and other scammers
When cybercriminals in Russia and China were just starting to form communities, the FBI was already hunting them down in America. This is evidenced by high-profile operations such as Shrouded Horizon, Firewall, and DarkMarket liquidation.
High technologies reached Russia and other countries of the former USSR by the early 2000s. Then there was a boom in Internet fraud. Because of low wages, hackers have become educated, tech-savvy people.
If the Russians were motivated by money, the Chinese united on the background of patriotism. To avoid repeating the "century of humiliation" — a period when great foreign powers forced China to sign unequal treaties, concessions and provoked opium wars (XIX-early XX centuries).
Against the backdrop of the anti-Chinese riots in Indonesia in the 1990s, users created forums, social media groups and electronic bulletin boards. We discussed deface actions against Indonesian government websites (Deface is a type of attack that results in the substitution of the content of the main page of the site, and access to other pages is blocked. Approx. transl.). As a result, the first groups of Chinese hackers appeared: the Green Army, China Eagle Union and Hongke (or Honker) Union. They also participated in the first attacks on the United States and other opponents of China.

Result of the deface of an American website by the Hongke (Honker) Union group
Today, Russian hackers also care about money, while Chinese hackers also care about patriotism. But since the appearance of these communities, many things have become more complicated: the organization of forums, promotion abroad, and relations with the authorities. We grouped the main findings of the Insikt Group by points — here's what happened:
For Russians, of course, money. There is little room for friendship on their forums. These are more business resources than platforms for communication. Respect and trust are gained by the most successful hackers: more deals — higher rating. There is no mentoring institute in this corner of the darknet — to train someone without a clear financial motivation?
But if Russian hackers are businessmen, then they are good, customer-oriented businessmen. Carders-wholesalers return funds for rejected cards. Sellers of Trojans and spam mailings arrange holiday discounts and sales. And abusive hosters transfer rewards to their clients for attracting referrals. They learn marketing from the largest corporations, which then attack.
Chinese carding forums, on the other hand, are imbued with the spirit of community. This culture is well represented by the term "geek spirit "(极客精神) - refers to technically educated people who hope to create an ideal society. Perfect? A fairer society? There is little context, but the idea of how much the Chinese geek on the community is clear.
People on the forums sincerely praise the wonderful skimmers, encoders, and sniffers. They write heartfelt thanks to sellers personally and actively share feedback to improve their products. To maintain communication, the Chinese set special requirements. If you decide to buy or sell malware, please contact the counterparty via a comment or private message. If you want to keep your membership — be an active user and communicate with other members on a daily basis. Such activists are even encouraged with intra-forum currency. A gamification system also works to engage in the community.

Post on the forum. To get access to the software that copies digital signatures, you need to answer
Supporting posts on the forum: the authors thank the user for sharing access to the program they created
There's nothing wrong with training here either. The Chinese promote special programs: experienced hackers train newcomers for money, and also take them under their care-for greater involvement in the community.
From the editor:
About the Chinese, of course, sounds super cool. Even somehow you forget that they also earn money by hacking. And the authors of the study mention the cost of training in passing. Сравните: про обучение у русских — «...few Russian forum members are willing to teach anyone anything without clear financial benefit.», и у китайцев «Chinese hackers advertise applications for apprenticeship programs on similar forums, where a more experienced hacker will teach an apprentice for a fee, dividing work among members based on skill level.». That is, " Russians don't teach newcomers (for free)", and "Chinese teach newcomers (for money)" — hmm... Well, the context escalates: Russians earn money, the Chinese build a community.
Although the first groups of Chinese hackers broke up — their cyber-patriotism marked the beginning of a close relationship between the state and hackers. Some forum participants were even hired to work in government agencies. Now some of them still work in the government, and some of them are heads of IT corporations.
Many patriotic hacking sites were later transformed into cybersecurity forums. But not all of them. As recent events show, when what happened in the East Asian region causes a public outcry, Chinese hacktivists are once again on the scene.
As for the rest of the cybercriminals, both Russian and Chinese, in order to remain at large, they must abide by one unwritten law: do not go against their own people. For Russians, this includes residents of the CIS. Moreover, it is possible for Russians to test developments on their fellow citizens. (It's not very clear what the authors meant: can I write a Trojan and test it on Yandex? Or are we talking about small companies and private owners? In any case, there are not enough proofs. Editor's note)
From the editor:
From the text, we can see that the Chinese are reluctant to shut down their hackers-more often when they have been exposed in major international scandals. This seems to be related to the concept of a face (面子).
Russian criminal forums are well-structured: scammers and hackers operate on different platforms. The Chinese do not have so many different sections. This once again confirms that the Russians focus on making a profit, and the Chinese on creating a community.
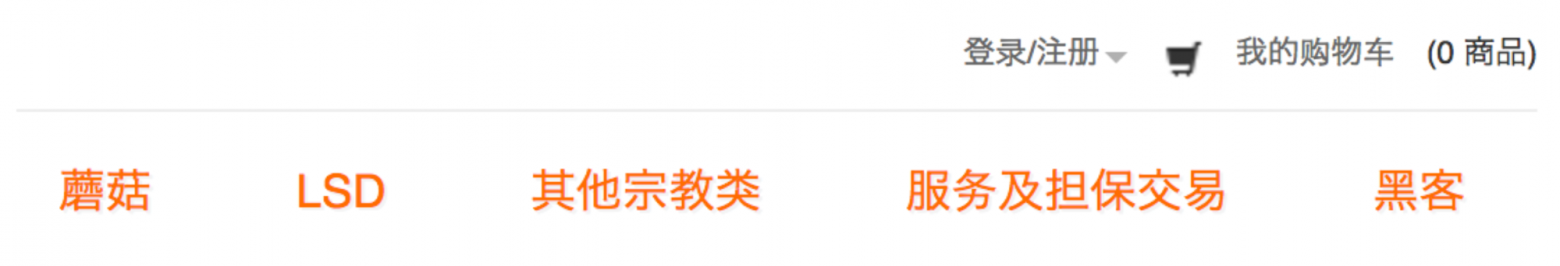
Menu of a drug-selling website with a "Carding" section, next to the "Mushrooms" and "LSD" sections
Both countries have open, semi-private, and closed forums. The more inaccessible a resource is, the more complex and high-quality its products are. It is enough to register at open sites. For semi-privates — you can make an entry fee of about$ 50 or confirm your membership on other resources. To access private forums, you need to find a sponsor among existing members and / or confirm the authenticity of your products.

kidala.info — this is a site dedicated to scam hackers. There are 15,839 of them on the site, and this number is growing
Access to most Russian forums is open. When you need tools to bypass blockages, Tor mirrors are most often used. In China, there is a strict censorship regime — since 2000, the Golden Shield project or the "Great Chinese Firewall" has been operating. At first, the goal of the project was to introduce the latest technologies to combat crime, and then — to limit the access of Chinese citizens to content that the state considers inappropriate or offensive.
The great Firewall even knows how to detect and interrupt outgoing connections to the Tor network — and this complicates access to international forums and trading platforms for cybercriminals. The last way to jump over this wall is to use a VPN. But since 2017, the state has introduced mandatory licensing of VPN services, and many of them have been closed. Visiting international hacking portals has become even more difficult.
From the editor:
In general, the organization of the community among Russians and Chinese is very similar. But the Great Firewall — a sad irony — is hitting Chinese hackers, despite their hacktivism and loyalty to the state.
As we remember, Russian hackers are primarily interested in money. There is no great Firewall, and they actively sell their services abroad. They publish posts in Russian and English, sell databases and credit cards of residents from all over the world.
It is not easy for Chinese hackers to break through with their products abroad because of the Great Firewall. Therefore, they develop their own communities: create more open hacking forums that are easily accessible on the local Internet, and develop groups based on the first patriotic forums. They also actively use closed chats and forums in popular messengers and social networks: QQ, Baidu, and WeChat.
If Russians sell data of people and companies from all countries, then there is much more Chinese data on Chinese forums. And you won't find them on foreign sites.
Why aren't the Chinese leaking data abroad? There are several possible reasons:
So, the Chinese like to develop their community, and when the Great Firewall came and they had difficulties entering the foreign market, they began to develop their community more actively. All this is true, but now researchers note the opposite trend. The great Firewall does not allow you to sell services in your own country-the Chinese are trying to break through abroad. This is evidenced by Chinese posts on Russian and English forums.
It turns out that the government is literally pushing Chinese hackers abroad. And, as we remember, they go there with the unique data of Chinese citizens and companies, as well as the means of hacking Chinese resources. Well, now the international community of cybercriminals has more opportunities to attack targets in China, steal accounts and other data.
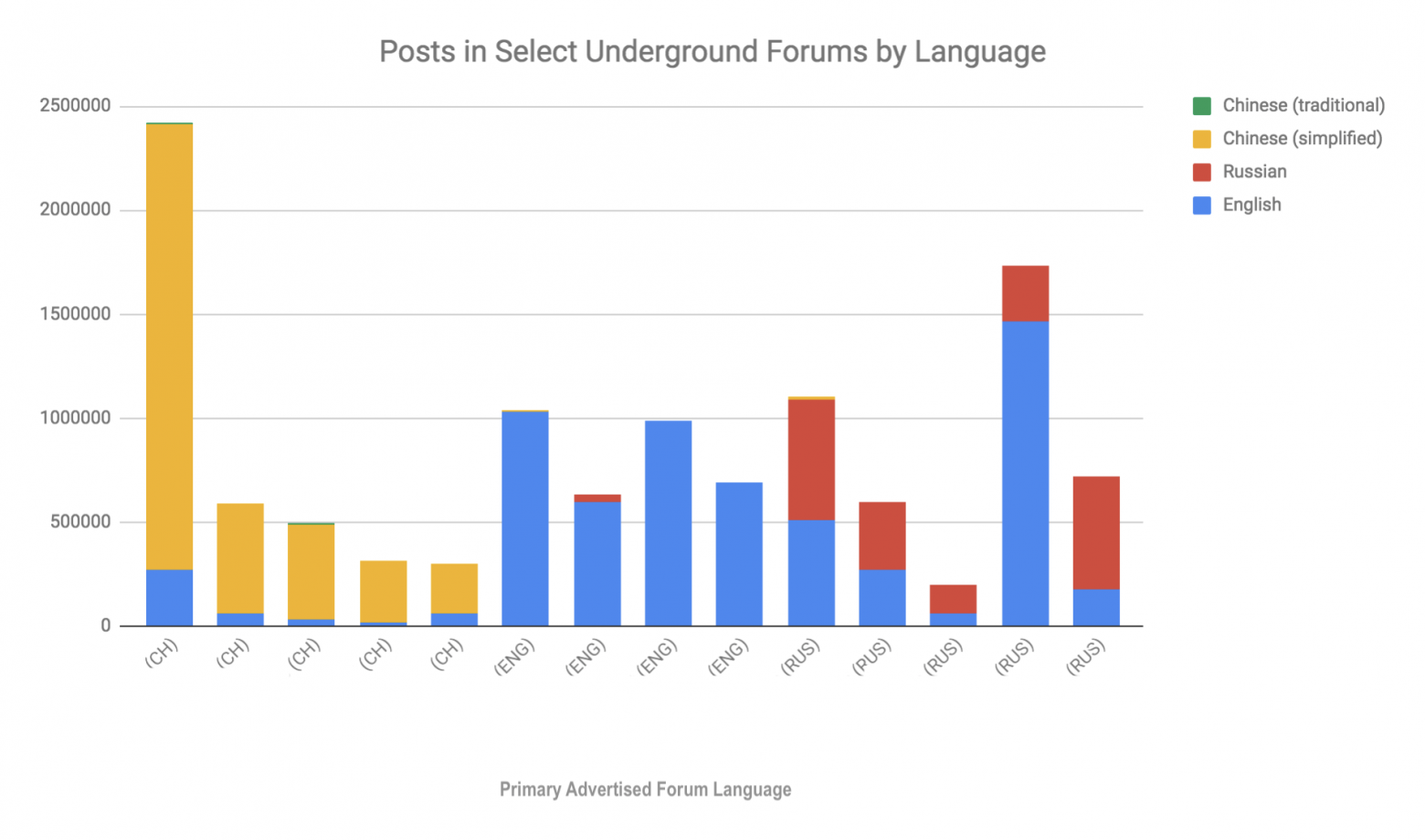
Breakdown of individual forum posts by language, Recorded Future data
From the editor:
Do you see the yellowish bars on the right? And I can't see them, but they're there.
Insikt Group researchers believe that the Russians will continue to focus on money, and the Chinese will continue to react sharply to political events.
Most of all, you should be afraid of the Russians with their sophisticated methods and peculiar tactics. These guys want to earn all the money in the world, and under the gun of the organization of all countries.
As for the Chinese, Insikt Group believes that the government will not be able to shut down all hacking resources. And thanks to the growing activity of Chinese people in international forums, they will learn from the experience of their colleagues.
The authors advise you to track events on underground forums, see what products are currently popular, and monitor the political situation (especially if your business is located in East Asia).
From the editor:
If you are interested in reading about Russian hackers, Kaspersky Lab published a study about them in 2016- "Russian carders: what they break, how much they pay, and why they are the best in the world".
As for the work of Insikt Group, I remember most of all "Chinese — community, Russians-money". The idea runs through the entire text, and this is not a skew in the squeeze-you can make sure by reading the full translation (be careful, keep the pseudoscientific style of the original). I don't know about you, but I still have the feeling that the Chinese do not earn money by hacking at all. Perhaps you have this feeling even more, because we threw out a piece about content on forums (what they sell) and payment methods (not very interesting, but at least there is China and money in one sentence).
In general, the authors do not say why they consider Chinese and Russian (Russian-speaking) hackers. About the fact that it's about leadership in the cybercrime market-editorial freedom. But with this shift of the Chinese from money to the community, the question "how did they get into the top hacker powers" becomes even more relevant. Or not — what do you think?
(c) Original author: Winnona DeSombre and Dan Byrnes
Recorded Future-the company tracks everything that happens on the Internet in real time. Predicts and analyzes cyber threats. It works with the support of the CIA and Google.
If you're interested in hacker culture: what drives their actions, how communities work, and where to expect threats from-read our extract from the Insikt Group study. We squeezed out the most interesting things + our thoughts on this matter.
As Insikt Group notes, most often we talk about hackers as an abstract mass. But in fact, there are several very different communities in this environment with their own history, motives and, if you want, code. Each country's hackers are unique. Often researchers do not take this into account — they talk about everyone at once or single out Russians.
Insikt Group employees compared the leaders of the cyber-criminal world: Russians and Chinese. And we started with their history.
Patriotism or money-history and motives
Russian carders — the spirit of theft
As Insikt Group notes: although both Chinese and Russian carder groups come from similar authoritarian states — their history and motives are different.
Russian-speaking cybercriminals value money first, although the phenomenon of financially motivated hacking itself originated in the United States.
One of the first hacking forums-Counterfeit Library-appeared in 2000 and was aimed at the English-speaking community. In response, 20 Ukrainians created the "Odessa Summit", which later grew to the Russian-language "Alliance of Carders" or "Planet of Carders". The forum was distinguished by a strict hierarchy of moderators who carefully checked all suppliers of CVV codes, eBay accounts, skimmers, etc. Western scammers adopted this experience of organizing the community and created ShadowCrew. A few years later (in 2005), Carders Market appeared, where Western and Eastern hackers could make transactions with each other.

Homepage of the Counterfeit Library, one of the first forums for carders and other scammers
When cybercriminals in Russia and China were just starting to form communities, the FBI was already hunting them down in America. This is evidenced by high-profile operations such as Shrouded Horizon, Firewall, and DarkMarket liquidation.
High technologies reached Russia and other countries of the former USSR by the early 2000s. Then there was a boom in Internet fraud. Because of low wages, hackers have become educated, tech-savvy people.
Pyotr Levashov, aka Severa — distributed fake antivirus software. It turned the victim's computer into part of the infamous Waledac and Kelihos botnets.
Evgeny Bogachev developed a special Zeus Trojan. With its help, JabberZeuS, Business Club and other criminal communities managed to steal more than $200 million from financial institutions in the United States and Great Britain.
Chinese carders — the spirit of patriotism
If the Russians were motivated by money, the Chinese united on the background of patriotism. To avoid repeating the "century of humiliation" — a period when great foreign powers forced China to sign unequal treaties, concessions and provoked opium wars (XIX-early XX centuries).
Against the backdrop of the anti-Chinese riots in Indonesia in the 1990s, users created forums, social media groups and electronic bulletin boards. We discussed deface actions against Indonesian government websites (Deface is a type of attack that results in the substitution of the content of the main page of the site, and access to other pages is blocked. Approx. transl.). As a result, the first groups of Chinese hackers appeared: the Green Army, China Eagle Union and Hongke (or Honker) Union. They also participated in the first attacks on the United States and other opponents of China.
One of the most famous: a DDoS attack on the websites of the White House and major American corporations - a month after a collision between an American reconnaissance plane and a Chinese fighter jet over the island of Hainan.

Result of the deface of an American website by the Hongke (Honker) Union group
Modern Carders are Still Money and Patriotism
Today, Russian hackers also care about money, while Chinese hackers also care about patriotism. But since the appearance of these communities, many things have become more complicated: the organization of forums, promotion abroad, and relations with the authorities. We grouped the main findings of the Insikt Group by points — here's what happened:
Money or Community
For Russians, of course, money. There is little room for friendship on their forums. These are more business resources than platforms for communication. Respect and trust are gained by the most successful hackers: more deals — higher rating. There is no mentoring institute in this corner of the darknet — to train someone without a clear financial motivation?
But if Russian hackers are businessmen, then they are good, customer-oriented businessmen. Carders-wholesalers return funds for rejected cards. Sellers of Trojans and spam mailings arrange holiday discounts and sales. And abusive hosters transfer rewards to their clients for attracting referrals. They learn marketing from the largest corporations, which then attack.
Chinese carding forums, on the other hand, are imbued with the spirit of community. This culture is well represented by the term "geek spirit "(极客精神) - refers to technically educated people who hope to create an ideal society. Perfect? A fairer society? There is little context, but the idea of how much the Chinese geek on the community is clear.
People on the forums sincerely praise the wonderful skimmers, encoders, and sniffers. They write heartfelt thanks to sellers personally and actively share feedback to improve their products. To maintain communication, the Chinese set special requirements. If you decide to buy or sell malware, please contact the counterparty via a comment or private message. If you want to keep your membership — be an active user and communicate with other members on a daily basis. Such activists are even encouraged with intra-forum currency. A gamification system also works to engage in the community.

Post on the forum. To get access to the software that copies digital signatures, you need to answer

Supporting posts on the forum: the authors thank the user for sharing access to the program they created
There's nothing wrong with training here either. The Chinese promote special programs: experienced hackers train newcomers for money, and also take them under their care-for greater involvement in the community.
From the editor:
About the Chinese, of course, sounds super cool. Even somehow you forget that they also earn money by hacking. And the authors of the study mention the cost of training in passing. Сравните: про обучение у русских — «...few Russian forum members are willing to teach anyone anything without clear financial benefit.», и у китайцев «Chinese hackers advertise applications for apprenticeship programs on similar forums, where a more experienced hacker will teach an apprentice for a fee, dividing work among members based on skill level.». That is, " Russians don't teach newcomers (for free)", and "Chinese teach newcomers (for money)" — hmm... Well, the context escalates: Russians earn money, the Chinese build a community.
Hacktivism and relations with the authorities
Although the first groups of Chinese hackers broke up — their cyber-patriotism marked the beginning of a close relationship between the state and hackers. Some forum participants were even hired to work in government agencies. Now some of them still work in the government, and some of them are heads of IT corporations.
Many patriotic hacking sites were later transformed into cybersecurity forums. But not all of them. As recent events show, when what happened in the East Asian region causes a public outcry, Chinese hacktivists are once again on the scene.
In general, many Chinese carders admitted to providing services to national intelligence agencies and military organizations (such as the Ministry of State Security and the People's Liberation Army).In 2012, China declared sovereignty over the Diaoyu Islands. After intense diplomatic disputes with Japan, the country needed support. And on the Hongke Union forum (8 years after the official dissolution of the group), a post appeared with potential goals for deface, all 300 of them are Japanese organizations.
In 2014, China put a drilling rig in the territorial waters of Vietnam, followed by a series of Chinese pogroms. In response, the new hacktivist group 1937CN compromised a number of Vietnamese websites. In 2016, they also hacked the check-in systems of Vietnamese airports and published personal data of more than 400 thousand passengers. Presumably because Vietnam has deployed missile launchers on disputed islands in the South China Sea.
It is difficult to determine for sure how independent the actions of these hackers are. The malicious code used in the 1937CN attack on Vietnamese airports was also used in a larger cyber espionage campaign against Vietnam. The alleged sponsor is the Chinese government.
The Russians have also repeatedly acted as people's avengers. Victims of such attacks were Estonia, Georgia, and other states/officials and individuals who were perceived to be unfriendly to the Russian Federation.However, the 1937CN group definitely displayed elements of hacktivism as well. For example, 1937CN has its own account on the Zone-H deface portal, accounts in various social networks. social media links to their website, and even a promo video uploaded to a popular video hosting site in July 2017: several people in hoods and Guy Fawkes masks.
The attitude of the authorities to hackers in Russia, as in China, is quite loyal. Arbor Networks even singled out Kremlin-backed hackers: Karim Baratov and Alexey Belan. Researchers believe that these hackers were recruited by the FSB to lead the 2014 Yahoo hack.When a monument to Soviet soldiers was dismantled in Estonia, the pro-Kremlin youth group Nashi posted a DDoS bash script on LiveJournal that attacked a certain list of Estonian IP users. Thanks to this, any concerned citizen could take part in the fight.
During the brief Russo-Georgian war, a DDoS attack (BlackEnergy botnets) was launched simultaneously with the advance of Russian tanks. According to one source, hacker Pyotr Levashov (Severa) sent spam with unconfirmed information that the Kremlin, Mikhail Prokhorov and hackers from the Civil Anti-Terror community attacked the websites of Chechen militants and Islamists.
Data from the study "Politically motivated DDoS attacks" by Arbor Networks (a large American company that sells DDoS protection and other security solutions. Note:transl.).
As for the rest of the cybercriminals, both Russian and Chinese, in order to remain at large, they must abide by one unwritten law: do not go against their own people. For Russians, this includes residents of the CIS. Moreover, it is possible for Russians to test developments on their fellow citizens. (It's not very clear what the authors meant: can I write a Trojan and test it on Yandex? Or are we talking about small companies and private owners? In any case, there are not enough proofs. Editor's note)
So Dmitry Fedorov aka "Paunch" distributed malware around the world through Blackhole, a proprietary program. However, he was detained only after selling Blackhole for use in Carberp Trojans, which were victims of Russians.
Pavel Vrublevsky, owner of the Russian processing service ChronoPay, provided money laundering services from the sale of illegal drugs and fake antiviruses. The Russian government did not object in any way. But when he ordered a DDoS attack on Assist (a domestic payment system) — he was immediately arrested.
From the editor:
From the text, we can see that the Chinese are reluctant to shut down their hackers-more often when they have been exposed in major international scandals. This seems to be related to the concept of a face (面子).
Researchers consider the concept of a person, but in the context of why the Chinese buy fake diplomas and business licenses. It seems that this concept also applies to the state's attitude to hackers.- involves gaining and retaining the respect of others. A lot of Chinese culture revolves around this concept, especially when it comes to family and business. The" loss of face " is so terrible for the Chinese that they are more likely to deceive than honestly talk about their failures and shortcomings. For example, single Chinese women who are going to visit their parents for the holidays often order the "groom for hire" service to mask failures in their personal lives.
Organizing communities
Russian criminal forums are well-structured: scammers and hackers operate on different platforms. The Chinese do not have so many different sections. This once again confirms that the Russians focus on making a profit, and the Chinese on creating a community.

Menu of a drug-selling website with a "Carding" section, next to the "Mushrooms" and "LSD" sections
Both countries have open, semi-private, and closed forums. The more inaccessible a resource is, the more complex and high-quality its products are. It is enough to register at open sites. For semi-privates — you can make an entry fee of about$ 50 or confirm your membership on other resources. To access private forums, you need to find a sponsor among existing members and / or confirm the authenticity of your products.
Both Russian and Chinese forums support blacklisting functionality. Users provide proof that they received low-quality or outright fake material, and admins, after checking this information, add the supplier to the ban list.There are also specific requirements. On some Russian forums, such as Exploit, only users with a certain number of posts get access to more valuable content. And some Chinese hacker groups in QQ and WeChat are promoted only on semi-private forums. So, to get into the group, you must first get to the forum.

kidala.info — this is a site dedicated to scam hackers. There are 15,839 of them on the site, and this number is growing
Access to most Russian forums is open. When you need tools to bypass blockages, Tor mirrors are most often used. In China, there is a strict censorship regime — since 2000, the Golden Shield project or the "Great Chinese Firewall" has been operating. At first, the goal of the project was to introduce the latest technologies to combat crime, and then — to limit the access of Chinese citizens to content that the state considers inappropriate or offensive.
The great Firewall even knows how to detect and interrupt outgoing connections to the Tor network — and this complicates access to international forums and trading platforms for cybercriminals. The last way to jump over this wall is to use a VPN. But since 2017, the state has introduced mandatory licensing of VPN services, and many of them have been closed. Visiting international hacking portals has become even more difficult.
From the editor:
In general, the organization of the community among Russians and Chinese is very similar. But the Great Firewall — a sad irony — is hitting Chinese hackers, despite their hacktivism and loyalty to the state.
Promotion of services abroad
As we remember, Russian hackers are primarily interested in money. There is no great Firewall, and they actively sell their services abroad. They publish posts in Russian and English, sell databases and credit cards of residents from all over the world.
It is not easy for Chinese hackers to break through with their products abroad because of the Great Firewall. Therefore, they develop their own communities: create more open hacking forums that are easily accessible on the local Internet, and develop groups based on the first patriotic forums. They also actively use closed chats and forums in popular messengers and social networks: QQ, Baidu, and WeChat.
If Russians sell data of people and companies from all countries, then there is much more Chinese data on Chinese forums. And you won't find them on foreign sites.
Why aren't the Chinese leaking data abroad? There are several possible reasons:
- it is difficult to use information — you need to know and understand local realities;
- inconvenient to use products-focused on the Chinese, the functionality and operating principles differ from their Western counterparts;
- the language barrier interferes.
So, the Chinese like to develop their community, and when the Great Firewall came and they had difficulties entering the foreign market, they began to develop their community more actively. All this is true, but now researchers note the opposite trend. The great Firewall does not allow you to sell services in your own country-the Chinese are trying to break through abroad. This is evidenced by Chinese posts on Russian and English forums.
It turns out that the government is literally pushing Chinese hackers abroad. And, as we remember, they go there with the unique data of Chinese citizens and companies, as well as the means of hacking Chinese resources. Well, now the international community of cybercriminals has more opportunities to attack targets in China, steal accounts and other data.

Breakdown of individual forum posts by language, Recorded Future data
From the editor:
Do you see the yellowish bars on the right? And I can't see them, but they're there.
Conclusions
Insikt Group researchers believe that the Russians will continue to focus on money, and the Chinese will continue to react sharply to political events.
Most of all, you should be afraid of the Russians with their sophisticated methods and peculiar tactics. These guys want to earn all the money in the world, and under the gun of the organization of all countries.
As for the Chinese, Insikt Group believes that the government will not be able to shut down all hacking resources. And thanks to the growing activity of Chinese people in international forums, they will learn from the experience of their colleagues.
The authors advise you to track events on underground forums, see what products are currently popular, and monitor the political situation (especially if your business is located in East Asia).
From the editor:
If you are interested in reading about Russian hackers, Kaspersky Lab published a study about them in 2016- "Russian carders: what they break, how much they pay, and why they are the best in the world".
As for the work of Insikt Group, I remember most of all "Chinese — community, Russians-money". The idea runs through the entire text, and this is not a skew in the squeeze-you can make sure by reading the full translation (be careful, keep the pseudoscientific style of the original). I don't know about you, but I still have the feeling that the Chinese do not earn money by hacking at all. Perhaps you have this feeling even more, because we threw out a piece about content on forums (what they sell) and payment methods (not very interesting, but at least there is China and money in one sentence).
In general, the authors do not say why they consider Chinese and Russian (Russian-speaking) hackers. About the fact that it's about leadership in the cybercrime market-editorial freedom. But with this shift of the Chinese from money to the community, the question "how did they get into the top hacker powers" becomes even more relevant. Or not — what do you think?
(c) Original author: Winnona DeSombre and Dan Byrnes
