A few weeks ago, it became known about a large-scale compromise of customers of the American retail corporation Target. Attackers managed to install malicious code on computers that are connected to payment terminals (POS, Point Of Sale) for purchases using credit cards. As a result of a well-planned operation by attackers to introduce and exploit malicious code, the confidential credit card data of more than 50 million users was compromised. In addition, a little later it was reported that the attackers also gained access to such confidential information of Target customers and employees as email addresses and phone numbers.

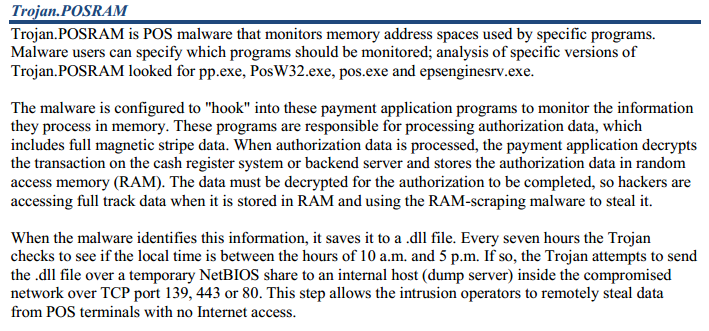
To steal credit card data, we used tools that are popular with carders, such as memory-grabber, to extract information from the memory of the desired process when performing a transaction. One of the first companies to provide detailed information about the new malicious code was iSight. The new malicious code is called Trojan. POSRAM (iSight). ESET antivirus products detect it as Win32/Spy. PosCardStealer. R, Win32/Spy.PosCardStealer. S, Win32/Spy.PosCardStealer. T (Symantec: Infostealer.Reedum.B, Microsoft: Trojan:Win32/Ploscato.A). This malicious code was written specifically to compromise POS, but the attackers also used other tools known as greyware or HackTool to perform certain operations (among them was the completely legitimate Sysinternals PsExec tool, equipped with a valid digital signature). This indicates that they had remote access to compromised computers (backdoor).
A few days ago, the company IntelCrawler, which is based in California, spread information in the media that a resident of St. Petersburg was involved in the development of the Trojan.POSRAM code. IntelCrawler dubbed this malicious code KAPTOXA, i.e. the word short for "potato", which is written in Latin. The company's report says that the attackers initially used this word to name their malicious code.
The scale of the operation carried out by the attackers is impressive. Previously, Target announced attacks on its systems in the fall of last year, it is quite possible that this was the initial intelligence for the operation to install malicious code.

To steal credit card data, we used tools that are popular with carders, such as memory-grabber, to extract information from the memory of the desired process when performing a transaction. One of the first companies to provide detailed information about the new malicious code was iSight. The new malicious code is called Trojan. POSRAM (iSight). ESET antivirus products detect it as Win32/Spy. PosCardStealer. R, Win32/Spy.PosCardStealer. S, Win32/Spy.PosCardStealer. T (Symantec: Infostealer.Reedum.B, Microsoft: Trojan:Win32/Ploscato.A). This malicious code was written specifically to compromise POS, but the attackers also used other tools known as greyware or HackTool to perform certain operations (among them was the completely legitimate Sysinternals PsExec tool, equipped with a valid digital signature). This indicates that they had remote access to compromised computers (backdoor).

A few days ago, the company IntelCrawler, which is based in California, spread information in the media that a resident of St. Petersburg was involved in the development of the Trojan.POSRAM code. IntelCrawler dubbed this malicious code KAPTOXA, i.e. the word short for "potato", which is written in Latin. The company's report says that the attackers initially used this word to name their malicious code.
The scale of the operation carried out by the attackers is impressive. Previously, Target announced attacks on its systems in the fall of last year, it is quite possible that this was the initial intelligence for the operation to install malicious code.
