At the end of a terrible spring, I was already depressed.
Tired of the daily monotony.
All tired... no development...
These thoughts in my head were eating me up.
I didn't have to strain my head for inventing any topic for a long time, because I knew that I always had an influx of "online entertainment" before the onset of summer.»:
Right now, a bunch of cool-school hackers will appear on the network, who will download a bunch of parsers and other software for draining databases and loading shells, and, of course, they will immediately get out for sales and part-time work in various boards.
Knowing about such "daily" crawls, we expect the appearance of topics with questions about where to get a free VPN.
This is how the program codenamed "Zombie Slaves" was born and launched.
Based on my plan, computers under the guidance of "schoolchildren" become my obedient "bots", so to speak, and then everything is in my hands.
Step number one.
Gradually approaching the beginning of launching the topic into work, I understood about minor improvements. And, in addition to all this, so that in the future I would not be bothered with configuration questions, I created virtual machines with the necessary software installed and VPN settings, as well as so that my VPN server would not go for a walk on the network at least in the first months after the start of the Zombie Slaves theme.
VMs are ready for replication. The VPN server is ready.
Step number two.
I install great software. I don't advertise it, but the developers are good (traffer). It is installed in two commands in automatic mode, and is installed on the Ubuntu OS within 10 minutes. Intercepts even the entered User passwords before sending and each request. It also intercepts all messages
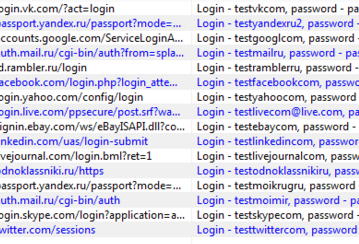
in messengers, Pic and Get information transfer, Ftp ... yes, anyway, everything is intercepted in the clear. I don't have my own screenshots from this theme, just those times (summer), but it looks like this:
and so
And now almost everything is ready. I'm testing it on myself. Everything is working, the interception is at its best. The settings in the car are all done. Therefore, you don't need to run and watch, you don't need to change anything. But there was one BUT-SSL certificate authentication at the first connection and browser launch. I resolved this issue as quickly as it appeared, saving the certificate and specifying the path to it.
On the next runs, there were no more problems with the certificate.
I multiplied virtual machines and went to different boards with mass ads, offering part-time work to "Schoolchildren", with an expression of respect for these young school hackers, soaked in summer, sun and positivity, and not condescending Forum Gurus " Schoololo is sick again."
Sometimes it pleases me that I have been registered on a huge number of hacker-related boards since ancient times and all accounts are old, so none of the accs has caused suspicion of fake (in connection with these fictions, I still create an account there when a new board is discovered).
The topic has been created. In Kratz, it sounded something like this:
"I am looking for partners for a topic on gray earnings with the provision of training, I am ready to pass the admin test" (And if I don't pass it , I don't ask for money, I just give information, software, manuals, all training and pay money for the result).
Therefore, there were no problems at all.
Everyone who is ready to spend time online and get paid during the holidays!
Waiting for everyone!
Send your contacts in a private message!
Everything you need is provided at your own expense!
And messages began to fall in piles, messing and communication went on in messengers. The zombie apocalypse has begun)))
Everyone was interviewed and everyone was satisfied with my proposed work option, which I offered "in connection with leaving for a long period...for two, maybe two and a half months...and since there are already a lot of orders, I recruit partners... in fact, I just become a small link that will take your information, transfer it to one or another , and from them transfer money to you. ..for the period of our cooperation ...".
Ready to work, I provided a VMWARE program with an already installed system equipped with the necessary software:
- VPN configured for anonymous operation
- Everything is paid for the duration of your online business trip
- On the desktop there are all the necessary manuals, which contain guides to action with an approximate content: "The first task is not interesting, but it is necessary - - using a php parser. Help the users listed in the guide to collect sites and check them for vulnerabilities.
The second task is to merge databases, collect database data by topic.
The third task is to fill in shells that are located in folders on the desktop, with information - how, where and why."
Everything is chewed up so that even I would have accepted my own offer without much hesitation. Manuals on the action from starting up to turning off the computer - for the dumbest and very greedy little man, who is under the impression of the movie "Kingston" - "Feel like a spy". Although we have a little different… Probably, the movie "Hacker" is still closer. .Damn, I should have uploaded this movie to their desktop.
It is very convenient to distribute the necessary software in this way))). All I had to do was multiply the configured VMs and upload them for distribution. Now the idea arises that why reproduce these typewriters-let the "Schoolboys" just merge them from somewhere (everyone would have their own copy).
Yes, an option, of course. But only 10 people could connect to the VPN with one username and password , so everyone would have to give out an individual username and password after downloading. Too much trouble for me. It is for this reason that I decided on the first option.
As a result - I spent the whole day without depression, with a feeling of Great self-satisfaction-On nah-I'm the first)))!!!. No longer boring, already more fun))).
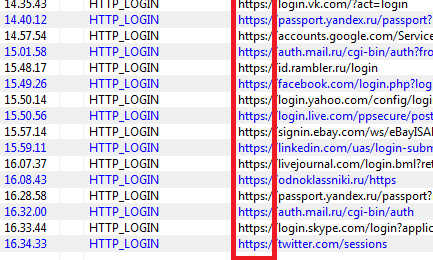
The sniffer intercepted everything-from the communication that the "Schoolboys" conducted in social networks from my virtual machines, to every password that was transmitted. The intercept view is shown in the drawing. The sniffer is very convenient, as it indicates the full path from the request to the script itself that the user goes to. Also, an amazing moment - when clicking on this request, you could see the TITLE of the page that the User clicked on, which greatly facilitated the search for the addresses of flooded shells.
My shell, which I prepared for them, had a specific welcome window (TITLE), for its prompt recognition in the Sniffer Logs.
I did not become completely impudent and offend our young hackers by merging all their accesses and accounts that fell into my hands. In addition, none of them fully understood what had happened, only at the end of the work period messages were sent in the topics to my address " Where did you go? How can I contact you? And So On )))".
)))".
Yes, and I don't consider myself an asshole, since each of them has gained a lot of experience and useful detailed information from a to z: pouring shells into all sorts of LMS engines , searching for dorks, decrypting hashes, searching for admins and other small things.
Information that, of course, can be found on the Internet, but collect it bit by bit, since mostly these topics are not fully disclosed.
Once a week, I merged logs from the Sniffer, sifted out in the logs everything that displays the greeting window – the "TITLE" of my shell. And just harvested, then draining it already on their favorite private boards.
Where it is not the fate of a simple schoolchild to register.
As a result, the summer was secure and time was spent not on the monotony of monotonous and not interesting work, but on the development of new talents.
What I caught looked like this:
17.23.47 GET / / http// http://www.arnoldrak.com.ua/inc/head2.php - still a live shell, it is much worse than wso in terms of functionality, but it does not burn most favs. They hang for a very long time until they are found manually. Next, I dumped databases if they were worth paying attention to, and the shells themselves were sold in bundles.
Having done everything on my own, without anyone's help, I confidently declare that it is better to spend time launching your VPN server than to worry at first, and eventually realize that your information went not only to the starting point you set. And don't use "super anonymously private" VPN SERVICES.... where you will be robbed and you will pay for it!
You can get a closer look at the Sniffer program that I used on the site
Price list http://ptraffer.ru/razlichia-i-tseni and functionality http://ptraffer.ru/http-sniffer
We are proud - this is Russian software!
You can request a demo version for the test. Initially, the program was created to search for information leaks among employees, then it developed into a full-fledged Sniffer, absolutely all data.
I'll say this – this shit is worth the money. Well, I still do not advise such greedy people as me to merge this software with all sorts of quacks, since the information drain will not only go into your hands))).
Tired of the daily monotony.
All tired... no development...
These thoughts in my head were eating me up.
I didn't have to strain my head for inventing any topic for a long time, because I knew that I always had an influx of "online entertainment" before the onset of summer.»:
Right now, a bunch of cool-school hackers will appear on the network, who will download a bunch of parsers and other software for draining databases and loading shells, and, of course, they will immediately get out for sales and part-time work in various boards.
Knowing about such "daily" crawls, we expect the appearance of topics with questions about where to get a free VPN.
This is how the program codenamed "Zombie Slaves" was born and launched.
Based on my plan, computers under the guidance of "schoolchildren" become my obedient "bots", so to speak, and then everything is in my hands.
Step number one.
Gradually approaching the beginning of launching the topic into work, I understood about minor improvements. And, in addition to all this, so that in the future I would not be bothered with configuration questions, I created virtual machines with the necessary software installed and VPN settings, as well as so that my VPN server would not go for a walk on the network at least in the first months after the start of the Zombie Slaves theme.
VMs are ready for replication. The VPN server is ready.
Step number two.
I install great software. I don't advertise it, but the developers are good (traffer). It is installed in two commands in automatic mode, and is installed on the Ubuntu OS within 10 minutes. Intercepts even the entered User passwords before sending and each request. It also intercepts all messages

in messengers, Pic and Get information transfer, Ftp ... yes, anyway, everything is intercepted in the clear. I don't have my own screenshots from this theme, just those times (summer), but it looks like this:

and so

And now almost everything is ready. I'm testing it on myself. Everything is working, the interception is at its best. The settings in the car are all done. Therefore, you don't need to run and watch, you don't need to change anything. But there was one BUT-SSL certificate authentication at the first connection and browser launch. I resolved this issue as quickly as it appeared, saving the certificate and specifying the path to it.
On the next runs, there were no more problems with the certificate.
I multiplied virtual machines and went to different boards with mass ads, offering part-time work to "Schoolchildren", with an expression of respect for these young school hackers, soaked in summer, sun and positivity, and not condescending Forum Gurus " Schoololo is sick again."
Sometimes it pleases me that I have been registered on a huge number of hacker-related boards since ancient times and all accounts are old, so none of the accs has caused suspicion of fake (in connection with these fictions, I still create an account there when a new board is discovered).
The topic has been created. In Kratz, it sounded something like this:
"I am looking for partners for a topic on gray earnings with the provision of training, I am ready to pass the admin test" (And if I don't pass it , I don't ask for money, I just give information, software, manuals, all training and pay money for the result).
Therefore, there were no problems at all.
Everyone who is ready to spend time online and get paid during the holidays!
Waiting for everyone!
Send your contacts in a private message!
Everything you need is provided at your own expense!
And messages began to fall in piles, messing and communication went on in messengers. The zombie apocalypse has begun)))
Everyone was interviewed and everyone was satisfied with my proposed work option, which I offered "in connection with leaving for a long period...for two, maybe two and a half months...and since there are already a lot of orders, I recruit partners... in fact, I just become a small link that will take your information, transfer it to one or another , and from them transfer money to you. ..for the period of our cooperation ...".
Ready to work, I provided a VMWARE program with an already installed system equipped with the necessary software:
- VPN configured for anonymous operation
- Everything is paid for the duration of your online business trip
- On the desktop there are all the necessary manuals, which contain guides to action with an approximate content: "The first task is not interesting, but it is necessary - - using a php parser. Help the users listed in the guide to collect sites and check them for vulnerabilities.
The second task is to merge databases, collect database data by topic.
The third task is to fill in shells that are located in folders on the desktop, with information - how, where and why."
Everything is chewed up so that even I would have accepted my own offer without much hesitation. Manuals on the action from starting up to turning off the computer - for the dumbest and very greedy little man, who is under the impression of the movie "Kingston" - "Feel like a spy". Although we have a little different… Probably, the movie "Hacker" is still closer. .Damn, I should have uploaded this movie to their desktop.
It is very convenient to distribute the necessary software in this way))). All I had to do was multiply the configured VMs and upload them for distribution. Now the idea arises that why reproduce these typewriters-let the "Schoolboys" just merge them from somewhere (everyone would have their own copy).
Yes, an option, of course. But only 10 people could connect to the VPN with one username and password , so everyone would have to give out an individual username and password after downloading. Too much trouble for me. It is for this reason that I decided on the first option.
As a result - I spent the whole day without depression, with a feeling of Great self-satisfaction-On nah-I'm the first)))!!!. No longer boring, already more fun))).
The sniffer intercepted everything-from the communication that the "Schoolboys" conducted in social networks from my virtual machines, to every password that was transmitted. The intercept view is shown in the drawing. The sniffer is very convenient, as it indicates the full path from the request to the script itself that the user goes to. Also, an amazing moment - when clicking on this request, you could see the TITLE of the page that the User clicked on, which greatly facilitated the search for the addresses of flooded shells.

My shell, which I prepared for them, had a specific welcome window (TITLE), for its prompt recognition in the Sniffer Logs.
I did not become completely impudent and offend our young hackers by merging all their accesses and accounts that fell into my hands. In addition, none of them fully understood what had happened, only at the end of the work period messages were sent in the topics to my address " Where did you go? How can I contact you? And So On
Yes, and I don't consider myself an asshole, since each of them has gained a lot of experience and useful detailed information from a to z: pouring shells into all sorts of LMS engines , searching for dorks, decrypting hashes, searching for admins and other small things.
Information that, of course, can be found on the Internet, but collect it bit by bit, since mostly these topics are not fully disclosed.
Once a week, I merged logs from the Sniffer, sifted out in the logs everything that displays the greeting window – the "TITLE" of my shell. And just harvested, then draining it already on their favorite private boards.
Where it is not the fate of a simple schoolchild to register.
As a result, the summer was secure and time was spent not on the monotony of monotonous and not interesting work, but on the development of new talents.
What I caught looked like this:
17.23.47 GET / / http// http://www.arnoldrak.com.ua/inc/head2.php - still a live shell, it is much worse than wso in terms of functionality, but it does not burn most favs. They hang for a very long time until they are found manually. Next, I dumped databases if they were worth paying attention to, and the shells themselves were sold in bundles.
Having done everything on my own, without anyone's help, I confidently declare that it is better to spend time launching your VPN server than to worry at first, and eventually realize that your information went not only to the starting point you set. And don't use "super anonymously private" VPN SERVICES.... where you will be robbed and you will pay for it!
You can get a closer look at the Sniffer program that I used on the site
Price list http://ptraffer.ru/razlichia-i-tseni and functionality http://ptraffer.ru/http-sniffer
We are proud - this is Russian software!
You can request a demo version for the test. Initially, the program was created to search for information leaks among employees, then it developed into a full-fledged Sniffer, absolutely all data.
I'll say this – this shit is worth the money. Well, I still do not advise such greedy people as me to merge this software with all sorts of quacks, since the information drain will not only go into your hands))).
