A rootkit is a type of software that is designed to increase privileges and mask malicious effects on the system. Despite the fact that the share of such programs in the total amount of malware is extremely small (no more than 1% according to Bitdefender), they pose a serious threat.
Rootkit programs are particularly relevant in the context of the growing number of APT attacks, which are characterized by a high level of execution, time dilation, and presence masking.
In this article, we will look at the main threats posed by rootkits, how they work, and effective lines of defense.
The goals can be very different: installing a miner, keylogger, gaining control over the OS, data theft, or monitoring. The key characteristic is an emphasis on long-term operation of the infected system.
If we talk about detection methods, leaving out specialized software, then the following markers can indicate infection:
Such consequences can be caused by a poorly configured rootkit that conflicts with the operating system. Professionally executed software behaves much less noticeably, and is often "covered up" by several payload processes.
There are rootkits for almost every popular operating system. Some of them can even be called cross-platform. At the same time, the leading position in terms of the amount of HPE produced is firmly held by Windows OS.
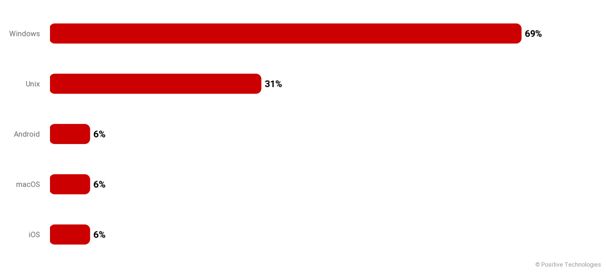
Source: © Positive Technologies. Distribution of rootkits by OS type.
Among the already known rootkits, there are several striking examples:
According to the principle of operation, it is customary to distinguish two types of rootkits:
Current research suggests that user-level rootkits are more popular and more common. So, for example, consider in Positive Technologies.
There are two reasons for such a large-scale distribution:
At the same time, any type of rootkit can be used for targeted attacks. The main parameter is high quality of execution.
This once again confirms the thesis that information security ceases to be an "optional option" for business, becoming a vital necessity for most modern companies.
Rootkit programs are particularly relevant in the context of the growing number of APT attacks, which are characterized by a high level of execution, time dilation, and presence masking.
In this article, we will look at the main threats posed by rootkits, how they work, and effective lines of defense.
General information
Rootkits do not bring anything new to the world of tools for malicious influence on systems. Infection occurs in two main ways:- through exploiting vulnerabilities;
- using social engineering.
The goals can be very different: installing a miner, keylogger, gaining control over the OS, data theft, or monitoring. The key characteristic is an emphasis on long-term operation of the infected system.
Roman Laminin
leading information security specialist eXpress
Mechanisms for distributing rootkits are not much different from the classic ones, for example, under the guise of free applications or when visiting an infected website, in which case the victim does not even have to download anything. Rootkits can also get to your computer from an external storage device.
You can remove the malware – there is special software for such tasks, but not everything is so simple – in some cases, you may need to reinstall the OS or even flash the BIOS. Therefore, it is better to deal with the prevention of infection, rather than eliminate its consequences.
What to do:
- Use comprehensive cybersecurity solutions — ME, IDS/IPS systems both gateway and network, as well as HIPS, use anti-virus protection and TDR/EDR systems.
- Use secure web surfing, and when downloading files, use sanitization algorithms and sandboxes.
- Conduct mandatory educational events and trainings with staff.
- Try to eliminate the human factor as much as possible, automate and robotize processes as much as possible, such as transferring files, signing them, etc.
- Be sure to perform log analysis and use orchestration tools as part of building the SOC.
If we talk about detection methods, leaving out specialized software, then the following markers can indicate infection:
- changing OS settings without user permission;
- reduced system performance, freezes;
- incorrect browser operation or incorrect display of web pages;
- the "blue screen" appears.
Such consequences can be caused by a poorly configured rootkit that conflicts with the operating system. Professionally executed software behaves much less noticeably, and is often "covered up" by several payload processes.
There are rootkits for almost every popular operating system. Some of them can even be called cross-platform. At the same time, the leading position in terms of the amount of HPE produced is firmly held by Windows OS.

Source: © Positive Technologies. Distribution of rootkits by OS type.
Among the already known rootkits, there are several striking examples:
- Stuxnet. With the help of this VPO, significant damage was caused to Iran's nuclear program in 2010.
- Necrus. It was identified in 2012, at the same time almost 90 thousand cases of infection were detected.
- ZeroAcces. This rootkit has not lost its relevance for more than a decade and is actively used to create infected networks. For example, for further DDoS attacks.
What is the rootkit used for?
The main task of rootkit is to control the infected system. Depending on the scale and security tools used, this control may take hours or weeks to complete.Anton Kuznetsov
Leading Information Security Engineer at R-Vision
Rootkits are dangerous because they can perform actions both on behalf of the user account and gain full access to the system at the OS kernel level. And even work at the driver level, which makes them difficult to detect.
This is primarily due to the architecture of the Windows family of operating systems. In them, user-level applications interact closely with components in the kernel space, building a chain of system calls and allowing rootkits to intercept them at different stages. In some cases, even without creating separate processes for this purpose. At the same time, rootkits for operating systems based on the Linux kernel are different, although they can also work at the kernel level and intercept system calls through modules loaded into it.
One of the easiest ways to counteract rootkits is to use secure and reliable downloads. For this purpose, the digital signature of the boot loader is verified by a legitimate certificate, after which, before loading the operating system, the digital signature of the Windows kernel is checked. And the kernel itself checks all components loaded into the operating system: download drivers, startup files, etc.
You can detect rootkits in Linux after viewing the logs of the dmesg kernel, which usually reports: the loaded module failed verification.
According to the principle of operation, it is customary to distinguish two types of rootkits:
- User-level rootkits. These programs run at the same privilege level as most applications. They can be used to intercept system calls and replace the values returned by the API.
- Running in kernel mode. The most complex group in terms of execution. It takes more time to create such software, because any error in the code can lead to a system crash. In this case, failure will mean detection.
Igor Grachev
Head of Information Security Department at BRR Bank
The speed of network infection using a rootkit depends on how the organization's information security system is built and how effective it is. If the network is not segmented, users work with administrator rights, and firewalls are disabled, then it is quite natural to talk about compromising the entire infrastructure of the organization.
But there is also a reverse example for organizations where the level of information security is quite high – even if the email with HPE was able to start working through IDS/IPS, antivirus on the firewall, protection on the mail server and on the user's computer, only the network segment where the user's computer is located will be compromised (of course, if there is a correct one a segmented network where access from one segment to another is closed and only the necessary ports for certain resources are open).
In organizations with an even more mature level of information security, the SIEM system will "pay attention" to uncharacteristic activity on one of the monitored computers and, based on pre-configured rules, transmit information to the SOAR system, which in turn, according to a previously configured typical scenario, will give the command to disable the port of the managed switch to which the compromised computer is connected until the circumstances are clarified.
Current research suggests that user-level rootkits are more popular and more common. So, for example, consider in Positive Technologies.
There are two reasons for such a large-scale distribution:
- sufficient functionality of "custom" rootkits to solve current problems of a cybercriminal;
- insufficient level of competence of most hackers to create effective kernel-level rootkits.
At the same time, any type of rootkit can be used for targeted attacks. The main parameter is high quality of execution.
Results
Rootkits perfectly fit into the new trend of cybercrime: the transition to planned and long-term attacks. In the near future, we can talk about the growth of the segment of software that masks malicious effects and is able to "survive" in the system for as long as possible.This once again confirms the thesis that information security ceases to be an "optional option" for business, becoming a vital necessity for most modern companies.
