The Kapersky lab showed how to bypass monitoring systems using virtualization.
During a complex cyberattack on a large company, attackers used the open QEMU hypervisor platform as a tool for creating a network tunnel. QEMU is a free emulator and hypervisor that allows you to run other operating systems as a guest on your computer.
Kaspersky Lab analysts found that hackers used QEMU to create virtual network interfaces and a socket-type network device to connect to a remote server. Such actions allowed attackers to create a network tunnel with minimal impact on system performance, which is an unusual example of the variety of methods used by cybercriminals to maintain secrecy.
Network tunnels are used to establish a hidden and secure communication channel between hackers and a compromised system, usually with traffic encryption to bypass firewalls and Intrusion Detection Systems (IDS).
According to experts, in 10% of the investigated cases over the past 3 years, hackers used the FRP and ngrok utilities to create tunnels, among others. Due to frequent abuse, defenders and monitoring tools are suspicious of such tools.
However, in this case, the attackers chose a less traditional tool that does not require traffic encryption and was launched with non-standard parameters, which did not arouse suspicion among monitoring tools. It is important to note that the lack of encryption makes it possible to analyze the transmitted data when intercepting traffic. Such activity, despite the use of legitimate tools, can be detected using specialized solutions for detecting and protecting against complex and targeted attacks.
QEMU offers unique features such as emulating a wide range of hardware and virtual networks, allowing hackers to disguise their activity as legitimate virtualization traffic and connect segmented parts of the network by strategically configuring virtual machine reference points.
As part of the attack, hackers used Angry IP Scanner to scan the network, mimikatz to steal credentials, and QEMU to create a complex network tunneling scheme that provides a hidden communication channel. In an effort to minimize their presence, the attackers allocated only 1 MB of RAM for the created VM, which significantly reduced the chances of detection based on resource consumption.
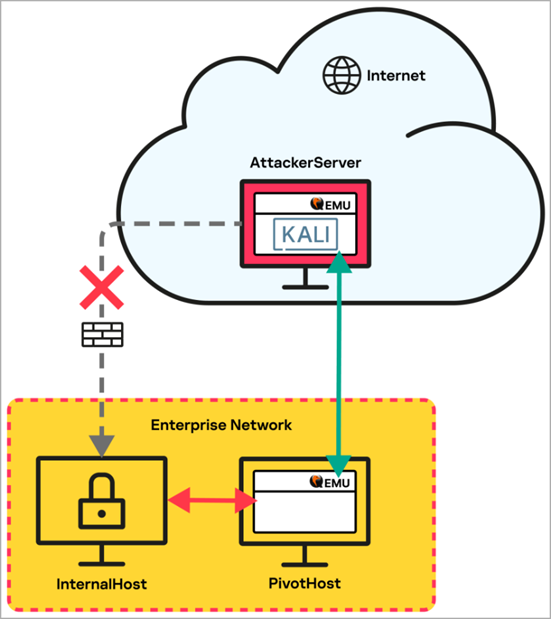
Traffic routing scheme
Using QEMU, the attackers installed a network tunnel from the target internal host, which did not have access to the Internet, to the reference host with Internet access, which, in turn, connects to the C2 server in the cloud running the Kali Linux VM.
Experiments with QEMU have confirmed its effectiveness as a tool for creating tunnels that allow attackers to gain access to isolated systems within the corporate network. For example, a successful connection to a system isolated from the Internet via RDP demonstrates the practical applicability of this approach.
Kaspersky Lab recommends that companies adopt multi-level protection to detect the use of legitimate tools, including round-the-clock network monitoring, which may not be affordable for many small businesses. Only comprehensive security, including network monitoring (NDR, NGFW) and endpoints (EDR, EPP) with the participation of SOC experts, can detect anomalies in a timely manner and block an attack at the initial stage.
During a complex cyberattack on a large company, attackers used the open QEMU hypervisor platform as a tool for creating a network tunnel. QEMU is a free emulator and hypervisor that allows you to run other operating systems as a guest on your computer.
Kaspersky Lab analysts found that hackers used QEMU to create virtual network interfaces and a socket-type network device to connect to a remote server. Such actions allowed attackers to create a network tunnel with minimal impact on system performance, which is an unusual example of the variety of methods used by cybercriminals to maintain secrecy.
Network tunnels are used to establish a hidden and secure communication channel between hackers and a compromised system, usually with traffic encryption to bypass firewalls and Intrusion Detection Systems (IDS).
According to experts, in 10% of the investigated cases over the past 3 years, hackers used the FRP and ngrok utilities to create tunnels, among others. Due to frequent abuse, defenders and monitoring tools are suspicious of such tools.
However, in this case, the attackers chose a less traditional tool that does not require traffic encryption and was launched with non-standard parameters, which did not arouse suspicion among monitoring tools. It is important to note that the lack of encryption makes it possible to analyze the transmitted data when intercepting traffic. Such activity, despite the use of legitimate tools, can be detected using specialized solutions for detecting and protecting against complex and targeted attacks.
QEMU offers unique features such as emulating a wide range of hardware and virtual networks, allowing hackers to disguise their activity as legitimate virtualization traffic and connect segmented parts of the network by strategically configuring virtual machine reference points.
As part of the attack, hackers used Angry IP Scanner to scan the network, mimikatz to steal credentials, and QEMU to create a complex network tunneling scheme that provides a hidden communication channel. In an effort to minimize their presence, the attackers allocated only 1 MB of RAM for the created VM, which significantly reduced the chances of detection based on resource consumption.

Traffic routing scheme
Using QEMU, the attackers installed a network tunnel from the target internal host, which did not have access to the Internet, to the reference host with Internet access, which, in turn, connects to the C2 server in the cloud running the Kali Linux VM.
Experiments with QEMU have confirmed its effectiveness as a tool for creating tunnels that allow attackers to gain access to isolated systems within the corporate network. For example, a successful connection to a system isolated from the Internet via RDP demonstrates the practical applicability of this approach.
Kaspersky Lab recommends that companies adopt multi-level protection to detect the use of legitimate tools, including round-the-clock network monitoring, which may not be affordable for many small businesses. Only comprehensive security, including network monitoring (NDR, NGFW) and endpoints (EDR, EPP) with the participation of SOC experts, can detect anomalies in a timely manner and block an attack at the initial stage.
