Foreword
Actually, why is the title of the article “emulation” and not “anonymization”?
Emulation in terms of technical parameters when working with the same Facebook is, first of all, an attempt to make everything as similar as possible to an ordinary user. With anonymization, the user does not think about how to randomize everything as much as possible and be like an ordinary user, the main thing for him is to hide his main technical solution.
Which gave a good tip in the form of "graph theory", you can think of this in terms of technical solutions. If you are using the same WebRTC (it is blocked, for example, or statically merges your real one) and ONLY through it, then there should be nothing wrong with that. But if this goes, for example, in a compartment with the same parameters, which are also unchanged, then this is already a wake-up call for AI. And after a certain number of accounts, he will already throw you in a selfie and block you whenever possible.
Therefore, for us, the goal is to make emulation as much as possible so that the AI bot has fewer reasons to cling to several parameters. And what parameters and where to look at them - I'll tell you now.
whoer.net
The first site we need: whoer.net
Do not look at these percentages from the top right after visiting a site where whoer calculates your "anonymity". This is a complete game for our affairs and will give us nothing in terms of information.
We go directly to the "Extended version".
IP, WebRTC
I will not touch on IP and WebRTC here. There is too much talk about these parameters and, moreover, I will touch upon WebRTC in one of the next articles, namely, how to organize its substitution in a virtual machine with one of the powerful technical solutions for antidetect.
But I will throw off the link to the article for general development about WebRTC.
Flash
Flash merging IP - must not be skipped. Now, of course, many people no longer have an installed flash on your desktop solution, but if there is one and you do not want to get rid of it, then you will have to perform the following manipulations:
It is necessary to modify the mms.cfg file (if Flash is installed on the computer).
If there is no file, then create along the path:
But it is better to demolish it anyway, it is practically no longer needed anywhere. Since the same plugins are drained through it.
Time

We look at the system. It would seem that they set the time as at the location of the proxy/ip and that's it? No, this is not enough. Some of the technical points that will merge you:
Language
The language, namely the share of one (q = 0.9 or 90%) of the user is determined by his history and cookies. The higher the value, the higher the likelihood that the user is using this language as their native language.
The value after the forward slash in the Title and JavaScript is determined by the settings in the browser. (In Chrome: Settings -> Advanced -> Languages -> Language).
Before changing settings in Chrome:

After changing settings in Chrome:

The value in brackets 100% will be different for different virtual machines with different history in the browser.
TCP / IP stack fingerprinting (Passive OS fingerprinting)

As for the operating system, I will not debate anything, the virtual machines close this case for sure. The last parameter, TCP / IP , is interesting here .
What to read about this:

 habr.com
habr.com
In short - the MTU value for wired Internet and some Wi-Fi modems should be 1500 (maximum value).
Mobile operators have 1400 or 1500 (sometimes there are less than 1400, usually a multiple of 10, such as 1380). Some usb modems have 1340-1380, the same usb modems 1340.
Also, the text value (Windows NT kernel) gives you a user not as a mobile operator, but on the desktop Internet. The same Android user will have at least a text about Linux 2.2.x-3.x, etc. Sometimes some (Megafon modem) have an inscription about VPN.
Why am I all this? If you emulate a mobile user, but sit with a modem - this item will give you up with giblets. Bad VPN / Proxy rental service providers who do not bother with such a security setting will also "pass" this item. Moreover, they may close the problem with the numerical value of MTU, but few people on the market have solutions with a text value at the moment.
One of the solutions: there is an emulation of a mobile device - use a mobile device to distribute the Internet. From a desktop - of course a desktop, a modem, a cable.
DNS
I don't see anything wrong with DNS from Google (8.8.8.8 and 8.8.4.4), but at a distance using only it on one subnet is already a suspicious thing for AI. Better, in my opinion, to use the standard DNS of your subnet:
Navigator
Data required for us:
Here, in terms of substitution, I cannot suggest anything (at least in this article at the moment, since I use my templates for this). But in one of the next articles I think I will.
The remaining data in the Navigator submenu does not matter, the virtual machine closes the problem with it.
Plugins
If chrome - you will be shown a more or less standard set of three plugins. Naturally, the site sees more of them. To do this, you must have a set of links to the most popular 25-30 plugins and install 2-3 plugins each time you set up your own antidetect browser.
Location
I see no point in discussing the location, since if the IP is configured correctly, the location will be tied to it.
Screen resolution and bitness
There is no reason to be perverted and use some obsolete computer permissions. You can use the standard and most popular 1366x768, and it doesn’t take too much steam. Of course, at a distance of 50-100, it is already necessary to change something, but I do not think that the negative from AI will go according to this parameter.
Most popular permissions statistics:

 gs.statcounter.com
gs.statcounter.com
Bitness 24 is the standard. And there is no point in changing it.
HTTP headers
Virtualka also closes the problem with them.
What will happen in the second part of the article?
I will cover AudioContext Fingerprint and how to bypass it, font fingerprint, SocialMedia Login Detection, etc.
browserleaks.com
I am writing the second part of my article on "emulation" of technical parameters. If you didn't have time to get acquainted with the first part - welcome .
Regarding this article, I will immediately make a reservation - I do not touch on those points that I personally consider not particularly worthy of attention. So head over to browserleaks.com and get started.
We go to the left menu on the site and select JavaScript:
JavaScript
What are we paying attention to?
The screen resolution parameter also has such a parameter as the viewport (the working area in the browser). That is, because of the address bar and tabs in the browser, the taskbar strip at the bottom with the start button and the scroll button in the browser on the right, the viewport resolution will differ downward from the screen resolution. This should be taken into account if you emulate, for example, a resolution that is larger than the monitor screen size (let 1920 × 1080), but leave the viewport the same as at a lower resolution (for example, viewport 1349 × 657, which belongs to the 1366x768 resolution). This will be very harmful for detection systems, especially if it is repeated.
I don't touch on the doNotTrack parameter, it doesn't really affect anything when working with the same virtual machine, rather, its forced change already allows you to think of you as a more sophisticated user.
I talked about hardwareConcurrency and deviceMemory in the previous article and will not add anything new.
Battery Status API
I specially checked whether the latest version of Chrome has a drain for this parameter by turning off my laptop from the network. It has:
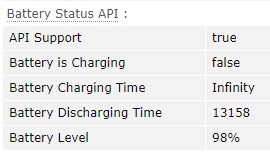
Therefore, when working with a laptop, you must have a 100% charge and a constant connection to the network (when logging out and logging into different accounts, especially in the same IP subnet).
Web Audio API
I'll touch on when discussing AudioContext Fingerprint (below).
Installed Plug-Ins
I touched on in the last article. Keep a list of links to the 30 most popular plugins and install randomly every 3-5 times.
Silverlight
Next, in the left menu, skip Flash (as discussed in the last article) and select Silverlight.
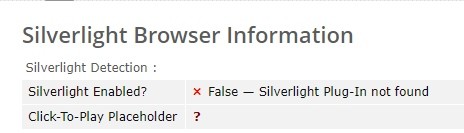
If you see this inscription, then everything is fine and you have one of the latest versions of your browser (checked on the latest Chrome and Firefox), which does not support this outdated and insecure plugin.
In the same case, if it is present and you do not want to get rid of it, then it is worth clearing all the data on your virtual (host) machine every time along the way:
Java Applet
The next item in the menu on the left is Java Applet.
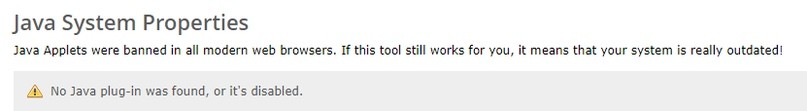
As you can imagine, the situation is the same here as with Silverlight. An outdated and insecure plugin that has been removed from support in newer versions of browsers. So outdated that I won't even tell you how to enable it. Do you need it?
WebGL
I will tell you only with changing the values: Unmasked Vendor, Unmasked Renderer and WebGL Report Hash (which changes after changing the first two). And only for Mozilla. I will analyze the latter meaning later in one of the following articles.
To do this, type about:config in the address bar, then type Vendor in the search and change it to any value. For example, just Mozilla.

Next, enter Renderer and select webgl.renderer-string-override:
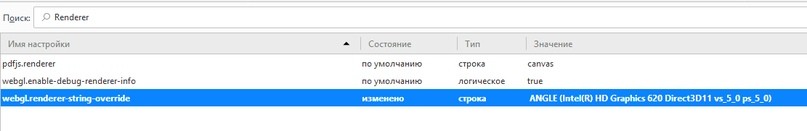
I entered for example ANGLE (Intel (R) HD Graphics 620 Direct3D11 vs_5_0 ps_5_0).
WebGL Report Hash should change for us too. But with Image Hash you have to work hard. I will leave this moment, perhaps I will supplement it, but while I do not have a handicraft solution for this point, I can only say that it is different in different browsers. I do not need this, since I have my own self-written browser, where there is an automatic substitution of this moment.
You can, of course, block access to WebGL - but this is a powerful call to Zucker and a quick subsequent ban.
WebRTC Leak Test
With WebRTC, I can single out one thing here - the so-called Media Devices. Again, this moment is changed in my browser, but here I can tell you that you can add some devices to this list using the Virtual Audio Cable program (found on torrents). Play around with this program, no matter what parameters you change. The main thing is to change the final value of the audio footprint.
About the presence / absence of a video camera and a microphone - a request is provided by the site and the user himself confirms whether he wants to provide the site with access to them or not. So there can't be a drain here.
Canvas Fingerprint
You can use the Canvas Defender extension to replace the Canvas fingerprint. It is available for both Mozilla and Chrome. Yes, this is pale to some extent, for sure the sites can pull up that you are using this extension at the moment. But if there are no other ways out, then you can do just that.
Alternatively, in Mozilla you can go to Settings and find this section in the General menu:

Select Advanced and uncheck the box next to Allow websites to use their fonts instead of the ones above. Let's save the changes. And now let's select the default font (supporting Cyrillic) with some size (better standard).
This will change our Canvas (like the Font Fingerprint, by the way).
Font Fingerprint
As I said in the last article - you need to have a set of fonts, randomly install some of them before starting a new virtual machine, for example. I will add some thoughts - it is necessary to install the most popular fonts (and have a set of the most popular fonts). Since when pulling using JS, the site pulls the installed fonts according to its internal list (that is, it may not detect your overseas fonts and your fingerprint will be similar to the past). He can pull out the entire list only with the help of Flash, which has been disabled for a long time.
Content filtering
What I was talking about. Canvas Protection is burning and the alternative solution is better in this regard.

Adblock fires, it's natural, BUT ESPECIALLY a non-standard and repetitive set of block lists will fire. The way out is not to use Adblock, or not to touch it in any way, so as not to differ from a group of people.
Features Detection
A huge set for highlighting any working / non-working parameters on the machine. What can you say? When an account is banned on a virtual machine and you did not demolish the Windows or clean everything thoroughly, it is possible that this set remained and will give you its fingerprint on the next account. That is, do not install unnecessary drivers like the KLite Media Codec Pack. Of course, you do not need to peer at each stage, but compare, for interest, what values you have on the host and virtual machine for Modernizr.video.h264 and, for example, Modernizr.jpeg2000 and Modernizr.jpegxr. On the host machine, h264 is probably true, but on virtual machines itis not. And the values from jpeg both there and there are false. This is quite a normal thing, but if there is something unusual and for a long time, this will again make an unfavorable imprint on you in the eyes of anti-fraud systems. You should not cling to this, as to one of the moments of the ban, but with a chain of values where the drain will occur - this will play more negatively than vice versa.
More Tools
Select More Tools next and I will explain some of the options:
Firefox Resources Reader is not up-to-date, as it was drained on older versions of Firefox. The drain consisted in the fact that Firefox gave out that it was Firefox and merged some data hashes that were stored in its JS files.
ClientRects Fingerprinting - The method of fighting is exactly the same as with Canvas. That is, changing the default font in Mozilla.
CSS Media Queries - Should be different on different virtual machines.
Social Media Login Detection is one of the most interesting things in this article as I haven't seen any thoughts about it anywhere. As you will notice, the site will determine on your machine which of the social networks you are logged into. And, for sure, Facebook will do the same before your registration. How unpleasant it will be for him to be your very first social network, in which you will be registered, do you agree? Save this list to yourself and each time before registering register for any of them randomly.
audiofingerprint.openwpm.com
I use a separate site audiofingerprint.openwpm.com for the audio print. As I said above, to change it, you need to play around in the installed Virtual Audio Cable program. To check your fingerprint, click Fingerprint me! and see.
Epilogue
Hope it was helpful. Let me also remind you that this is not the last article in this direction. In the next articles I will describe how to work with some of the most powerful antidetect systems of virtual machines.
Actually, why is the title of the article “emulation” and not “anonymization”?
Emulation in terms of technical parameters when working with the same Facebook is, first of all, an attempt to make everything as similar as possible to an ordinary user. With anonymization, the user does not think about how to randomize everything as much as possible and be like an ordinary user, the main thing for him is to hide his main technical solution.
Which gave a good tip in the form of "graph theory", you can think of this in terms of technical solutions. If you are using the same WebRTC (it is blocked, for example, or statically merges your real one) and ONLY through it, then there should be nothing wrong with that. But if this goes, for example, in a compartment with the same parameters, which are also unchanged, then this is already a wake-up call for AI. And after a certain number of accounts, he will already throw you in a selfie and block you whenever possible.
Therefore, for us, the goal is to make emulation as much as possible so that the AI bot has fewer reasons to cling to several parameters. And what parameters and where to look at them - I'll tell you now.
whoer.net
The first site we need: whoer.net
Do not look at these percentages from the top right after visiting a site where whoer calculates your "anonymity". This is a complete game for our affairs and will give us nothing in terms of information.
We go directly to the "Extended version".
IP, WebRTC
I will not touch on IP and WebRTC here. There is too much talk about these parameters and, moreover, I will touch upon WebRTC in one of the next articles, namely, how to organize its substitution in a virtual machine with one of the powerful technical solutions for antidetect.
But I will throw off the link to the article for general development about WebRTC.
Flash
Flash merging IP - must not be skipped. Now, of course, many people no longer have an installed flash on your desktop solution, but if there is one and you do not want to get rid of it, then you will have to perform the following manipulations:
It is necessary to modify the mms.cfg file (if Flash is installed on the computer).
If there is no file, then create along the path:
Code:
Windows (32Bit): C: \ Windows \ System32 \ Macromed \ Flash \
Windows (64Bit): C: \ Windows \ SysWOW64 \ Macromed \ Flash \
And write at the end of the file: DisableSockets = 1But it is better to demolish it anyway, it is practically no longer needed anywhere. Since the same plugins are drained through it.
Time

We look at the system. It would seem that they set the time as at the location of the proxy/ip and that's it? No, this is not enough. Some of the technical points that will merge you:
- Accordingly, the time itself and the coincidence with the IP time zone.
- The system time has text in brackets (Moscow, standard time). Sometimes it happens that it says, for example, Saudi Arabia (one of the machines had such a problem), although everything is indicated correctly in the time settings in Windows. As it seems to me, this is due to the Windows itself and you can change this only by demolition and reinstallation with a different image. All virtual machines hosted on it had the same problem as Zennoposter.
- Deviation in seconds. As you can see the difference between local and system is 21 seconds. How many cars with the same time deviation can be logged into Facebook accounts in a row? And even more so on the same IP subnet?
Language
The language, namely the share of one (q = 0.9 or 90%) of the user is determined by his history and cookies. The higher the value, the higher the likelihood that the user is using this language as their native language.
The value after the forward slash in the Title and JavaScript is determined by the settings in the browser. (In Chrome: Settings -> Advanced -> Languages -> Language).
Before changing settings in Chrome:

After changing settings in Chrome:

The value in brackets 100% will be different for different virtual machines with different history in the browser.
TCP / IP stack fingerprinting (Passive OS fingerprinting)

As for the operating system, I will not debate anything, the virtual machines close this case for sure. The last parameter, TCP / IP , is interesting here .
What to read about this:
Определяем пользователей VPN (и их настройки!) и прокси со стороны сайта
We can save the day from dark, from bad There's no one we need Многие из вас используют VPN или прокси в повседневной жизни. Кто-то использует его постоянно, получая доступ к заблокированным на...
In short - the MTU value for wired Internet and some Wi-Fi modems should be 1500 (maximum value).
Mobile operators have 1400 or 1500 (sometimes there are less than 1400, usually a multiple of 10, such as 1380). Some usb modems have 1340-1380, the same usb modems 1340.
Also, the text value (Windows NT kernel) gives you a user not as a mobile operator, but on the desktop Internet. The same Android user will have at least a text about Linux 2.2.x-3.x, etc. Sometimes some (Megafon modem) have an inscription about VPN.
Why am I all this? If you emulate a mobile user, but sit with a modem - this item will give you up with giblets. Bad VPN / Proxy rental service providers who do not bother with such a security setting will also "pass" this item. Moreover, they may close the problem with the numerical value of MTU, but few people on the market have solutions with a text value at the moment.
One of the solutions: there is an emulation of a mobile device - use a mobile device to distribute the Internet. From a desktop - of course a desktop, a modem, a cable.
DNS
I don't see anything wrong with DNS from Google (8.8.8.8 and 8.8.4.4), but at a distance using only it on one subnet is already a suspicious thing for AI. Better, in my opinion, to use the standard DNS of your subnet:
- Shows you as a less experienced computer user;
- The distance to DNS servers is closer (Google has the nearest ones in Finland);
- Different subnets are different DNS.
Navigator
Data required for us:
- hardwareConcurrency - number of cores.
- deviceMemory - the number of GB of RAM.
Here, in terms of substitution, I cannot suggest anything (at least in this article at the moment, since I use my templates for this). But in one of the next articles I think I will.
The remaining data in the Navigator submenu does not matter, the virtual machine closes the problem with it.
Plugins
If chrome - you will be shown a more or less standard set of three plugins. Naturally, the site sees more of them. To do this, you must have a set of links to the most popular 25-30 plugins and install 2-3 plugins each time you set up your own antidetect browser.
Location
I see no point in discussing the location, since if the IP is configured correctly, the location will be tied to it.
Screen resolution and bitness
There is no reason to be perverted and use some obsolete computer permissions. You can use the standard and most popular 1366x768, and it doesn’t take too much steam. Of course, at a distance of 50-100, it is already necessary to change something, but I do not think that the negative from AI will go according to this parameter.
Most popular permissions statistics:

Screen Resolution Stats Worldwide | Statcounter Global Stats
This graph shows the stats of screen resolutions worldwide based on over 5 billion monthly page views.
Bitness 24 is the standard. And there is no point in changing it.
HTTP headers
Virtualka also closes the problem with them.
What will happen in the second part of the article?
I will cover AudioContext Fingerprint and how to bypass it, font fingerprint, SocialMedia Login Detection, etc.
browserleaks.com
I am writing the second part of my article on "emulation" of technical parameters. If you didn't have time to get acquainted with the first part - welcome .
Regarding this article, I will immediately make a reservation - I do not touch on those points that I personally consider not particularly worthy of attention. So head over to browserleaks.com and get started.
We go to the left menu on the site and select JavaScript:
JavaScript
What are we paying attention to?
The screen resolution parameter also has such a parameter as the viewport (the working area in the browser). That is, because of the address bar and tabs in the browser, the taskbar strip at the bottom with the start button and the scroll button in the browser on the right, the viewport resolution will differ downward from the screen resolution. This should be taken into account if you emulate, for example, a resolution that is larger than the monitor screen size (let 1920 × 1080), but leave the viewport the same as at a lower resolution (for example, viewport 1349 × 657, which belongs to the 1366x768 resolution). This will be very harmful for detection systems, especially if it is repeated.
I don't touch on the doNotTrack parameter, it doesn't really affect anything when working with the same virtual machine, rather, its forced change already allows you to think of you as a more sophisticated user.
I talked about hardwareConcurrency and deviceMemory in the previous article and will not add anything new.
Battery Status API
I specially checked whether the latest version of Chrome has a drain for this parameter by turning off my laptop from the network. It has:

Therefore, when working with a laptop, you must have a 100% charge and a constant connection to the network (when logging out and logging into different accounts, especially in the same IP subnet).
Web Audio API
I'll touch on when discussing AudioContext Fingerprint (below).
Installed Plug-Ins
I touched on in the last article. Keep a list of links to the 30 most popular plugins and install randomly every 3-5 times.
Silverlight
Next, in the left menu, skip Flash (as discussed in the last article) and select Silverlight.

If you see this inscription, then everything is fine and you have one of the latest versions of your browser (checked on the latest Chrome and Firefox), which does not support this outdated and insecure plugin.
In the same case, if it is present and you do not want to get rid of it, then it is worth clearing all the data on your virtual (host) machine every time along the way:
Code:
C: \ Users \% Username% \ AppData \ LocalLow \ Microsoft \ Silverlight \ is \Java Applet
The next item in the menu on the left is Java Applet.

As you can imagine, the situation is the same here as with Silverlight. An outdated and insecure plugin that has been removed from support in newer versions of browsers. So outdated that I won't even tell you how to enable it. Do you need it?
WebGL
I will tell you only with changing the values: Unmasked Vendor, Unmasked Renderer and WebGL Report Hash (which changes after changing the first two). And only for Mozilla. I will analyze the latter meaning later in one of the following articles.
To do this, type about:config in the address bar, then type Vendor in the search and change it to any value. For example, just Mozilla.

Next, enter Renderer and select webgl.renderer-string-override:

I entered for example ANGLE (Intel (R) HD Graphics 620 Direct3D11 vs_5_0 ps_5_0).
WebGL Report Hash should change for us too. But with Image Hash you have to work hard. I will leave this moment, perhaps I will supplement it, but while I do not have a handicraft solution for this point, I can only say that it is different in different browsers. I do not need this, since I have my own self-written browser, where there is an automatic substitution of this moment.
You can, of course, block access to WebGL - but this is a powerful call to Zucker and a quick subsequent ban.
WebRTC Leak Test
With WebRTC, I can single out one thing here - the so-called Media Devices. Again, this moment is changed in my browser, but here I can tell you that you can add some devices to this list using the Virtual Audio Cable program (found on torrents). Play around with this program, no matter what parameters you change. The main thing is to change the final value of the audio footprint.
About the presence / absence of a video camera and a microphone - a request is provided by the site and the user himself confirms whether he wants to provide the site with access to them or not. So there can't be a drain here.
Canvas Fingerprint
You can use the Canvas Defender extension to replace the Canvas fingerprint. It is available for both Mozilla and Chrome. Yes, this is pale to some extent, for sure the sites can pull up that you are using this extension at the moment. But if there are no other ways out, then you can do just that.
Alternatively, in Mozilla you can go to Settings and find this section in the General menu:

Select Advanced and uncheck the box next to Allow websites to use their fonts instead of the ones above. Let's save the changes. And now let's select the default font (supporting Cyrillic) with some size (better standard).
This will change our Canvas (like the Font Fingerprint, by the way).
Font Fingerprint
As I said in the last article - you need to have a set of fonts, randomly install some of them before starting a new virtual machine, for example. I will add some thoughts - it is necessary to install the most popular fonts (and have a set of the most popular fonts). Since when pulling using JS, the site pulls the installed fonts according to its internal list (that is, it may not detect your overseas fonts and your fingerprint will be similar to the past). He can pull out the entire list only with the help of Flash, which has been disabled for a long time.
Content filtering
What I was talking about. Canvas Protection is burning and the alternative solution is better in this regard.

Adblock fires, it's natural, BUT ESPECIALLY a non-standard and repetitive set of block lists will fire. The way out is not to use Adblock, or not to touch it in any way, so as not to differ from a group of people.
Features Detection
A huge set for highlighting any working / non-working parameters on the machine. What can you say? When an account is banned on a virtual machine and you did not demolish the Windows or clean everything thoroughly, it is possible that this set remained and will give you its fingerprint on the next account. That is, do not install unnecessary drivers like the KLite Media Codec Pack. Of course, you do not need to peer at each stage, but compare, for interest, what values you have on the host and virtual machine for Modernizr.video.h264 and, for example, Modernizr.jpeg2000 and Modernizr.jpegxr. On the host machine, h264 is probably true, but on virtual machines itis not. And the values from jpeg both there and there are false. This is quite a normal thing, but if there is something unusual and for a long time, this will again make an unfavorable imprint on you in the eyes of anti-fraud systems. You should not cling to this, as to one of the moments of the ban, but with a chain of values where the drain will occur - this will play more negatively than vice versa.
More Tools
Select More Tools next and I will explain some of the options:
Firefox Resources Reader is not up-to-date, as it was drained on older versions of Firefox. The drain consisted in the fact that Firefox gave out that it was Firefox and merged some data hashes that were stored in its JS files.
ClientRects Fingerprinting - The method of fighting is exactly the same as with Canvas. That is, changing the default font in Mozilla.
CSS Media Queries - Should be different on different virtual machines.
Social Media Login Detection is one of the most interesting things in this article as I haven't seen any thoughts about it anywhere. As you will notice, the site will determine on your machine which of the social networks you are logged into. And, for sure, Facebook will do the same before your registration. How unpleasant it will be for him to be your very first social network, in which you will be registered, do you agree? Save this list to yourself and each time before registering register for any of them randomly.
audiofingerprint.openwpm.com
I use a separate site audiofingerprint.openwpm.com for the audio print. As I said above, to change it, you need to play around in the installed Virtual Audio Cable program. To check your fingerprint, click Fingerprint me! and see.
Epilogue
Hope it was helpful. Let me also remind you that this is not the last article in this direction. In the next articles I will describe how to work with some of the most powerful antidetect systems of virtual machines.
Last edited by a moderator:
