What the study is about
Other parts of the study
We present to your attention the results of a study on ensuring information security of one of the most vulnerable areas of the bank — the process of making non-cash payments.
The study turned out to be quite extensive, so it will be published in parts. And we will start with the first part, which will tell you what non-cash payments are from an economic point of view.
Terms, definitions, assumptions and conventions
The purpose of the study is to systematize knowledge, solutions and experience in ensuring information security of bank wire transfers.
Information sources:
Assumptions:
The standard scheme of organizational and technical interaction between credit institutions and the Bank of Russia adopted in the Moscow region is taken as a basis.
When considering the economic fundamentals, issues related to the collection of commissions and accounting will be omitted.
Terms and conditions:
The study will use terms and definitions in the sense in which they are used in the current legislation of the Russian Federation.
Synonyms:
Bank = credit institution.
Non-cash payment = transfer of funds.
Payments = settlements.
Historically, the first types of payments were made in cash. The buyer handed over banknotes to the seller, and in return received a product or service.

Let's analyze the pros and cons of this form of settlement from the point of view of the buyer and seller, as well as from the point of view of the state economy as a whole.
Thus, it is clear that cash payments for the state are an evil that it would gladly prohibit if it did not cause a sharp protest of the population. And if it is impossible to completely ban it, then restrictive measures are applied.
In Russia, in particular, legislation (Civil Code of the Russian Federation, Article 861, Bank of Russia Directive 3073-U of 07.10.2013) establishes that only citizens and only for personal purposes can use cash without restrictions, while the rest (sole proprietors, legal entities,...) are strictly limited in the use of cash.
Non-cash payments, in contrast to cash payments, imply the presence of a third trusted party between the seller and the buyer — an intermediary who, on behalf of the parties, performs settlements between them.
Cryptocurrencies such as Bitcoin, Ethereum, and others allow payments to be made without intermediaries (not counting miners), but so far the status of these systems is not legally defined, and their description is beyond the scope of this article. Here we will consider only "classic" non-cash payments, where credit organizations (banks) act as the third trusted party.
For making non-cash payments, money is used in a non-cash form. Consider the mechanisms for converting money from cash to non-cash and back.
It all starts with the fact that the client, whether an individual, a legal entity or an individual entrepreneur, enters into a contractual relationship with a credit institution that has a banking license from the Bank of Russia.
The Client transfers cash funds to the bank, the bank accepts them and reflects them on a bank account specially established for accounting for settlements with the client. If the client deposits money in the bank, the balance on this account increases, if he withdraws, it decreases.
After the client has deposited cash in the bank, it turns into non-cash money, which, if much simplified, is not even money, but the bank's obligations to do certain services for the client, which can include issuing cash to the client, transferring funds, and so on.
In addition to receiving and withdrawing cash, the client's bank account may increase or decrease due to receiving non-cash transfers from third parties and making transfers to third parties, respectively. It is important to note that non-cash money is not the obligations of the entire banking system, but the obligations of the bank where the corresponding bank account is opened. This realization comes especially vividly if the bank that serves this account goes bankrupt. Then the money (the balance on the account) seems to be there, but it is impossible to use it.
There are different types of bank accounts. Customers — individuals-open current or special card accounts with the bank. Clients — legal entities-open current accounts with banks. Banks open correspondent accounts with other banks to make payments. Without going into details, the functioning of all these accounts looks approximately the same: an increase in the account balance leads to an increase in the obligations of the bank in which it is opened, and vice versa, a decrease in the balance reduces the bank's obligations. For the sake of simplicity, in the future we will consider only work on settlement and correspondent accounts.
At this stage, the bank will consist of two main parts for us:
One of the main sources of income for banks is lending. The bank transfers the money for temporary use to the client, who returns it with interest. To support this type of business, the bank needs money that it will give on credit. And this is where customer money stored in non-cash accounts comes into play.
The basic idea is that the bank never holds all the money of its customers. Instead, the bank keeps statistical records of customers ' activities and "very accurately guesses" how much money they may need for current payments. The rest of the money is used by the bank for lending.
Let's look at how a non-cash payment is made between a payer and a recipient (hereinafter referred to as clients) who are served in the same bank.
When paying in cash, payments are always of the same type: the payer voluntarily transfers the required amount of money to the recipient. When using non-cash payments, the payment schemes may be different:
The most common form of settlement is based on payment orders.
Regardless of the settlement forms used, the Bank reports to the client for all transactions made on its account by providing a special document – an account statement.
The payment order and account statement are the main legally significant documents used by the client and the bank for accounting purposes and conflict resolution proceedings in court.
It is important to note that if a payment was received to the client's current account and it was reflected in the account statement, the bank does not have the right to return the payment to the sender, even if it was made by mistake or maliciously. Refund of payment is possible only by agreement with the recipient or by a court decision. The maximum that a bank can do is, in accordance with the legislation on countering the legalization of proceeds from crime, to block funds in the recipient's account.
Note
The Civil Code of the Russian Federation (Civil Code of the Russian Federation Article 1102. Obligation to return unjust enrichment) requires the recipient to return funds to the sender if they were sent without justification or by mistake.
Earlier, we looked at how transfers are made between clients served in the same bank. Now let's complicate the task and look at how settlements are made between clients served in two different banks.
For interbank settlements, banks must establish correspondent relations with each other. The essence of this relationship is that one bank, Bank 2 in the diagram below (Figure 3), becomes a client of Bank 1 and opens a special bank account called a correspondent account. After opening a correspondent account, Bank 2 deposits a certain amount of money into it, a kind of monetary buffer in the amount of which Bank 2's clients can send payments to Bank 1's clients.
To understand how this works, let's look at an example. Let's say that Bank 2 has placed, say, 1 million rubles on a correspondent account in Bank 1.
The mechanism for making payments between two banks, which we just reviewed, is simple, but has a significant drawback in terms of scalability. With a large number of banks, it is difficult to establish and maintain correspondent relations between each bank and each other. Therefore, the main tool for interbank money transfers in the Russian Federation is the payment system of the Bank of Russia.
The main idea of this payment system is that the Bank of Russia acts as a single point to which all banks are connected, and through which payments pass from one bank to another.
Each credit institution, when registering and obtaining a banking license, opens a correspondent account with the Bank of Russia.
In order to be able to distinguish one bank from another, they are assigned bank identification codes (BIC). The Bank of Russia regularly updates and publishes the BIC directory on its website. If you know the BIC, you can also use this directory to determine the corresponding bank account number opened with the Bank of Russia. The combination of the BIC and current account number uniquely identifies the client's current account within the entire payment system of the Russian Federation.
Let's look at how an interbank payment will be made using the Bank of Russia's payment system. Let's take the interaction between customers and banks as a basis, illustrated in Figure 4.
If there are several options for the flow of funds, as, for example, between Client B and Client C in Figure 4, the sending bank independently decides on the routing of the payment: using direct correspondent relations or through the payment system of the Bank of Russia-depending on the payment parameters, its cost price and other conditions.
Money transfers in the payment system of the Bank of Russia are carried out:
Real-time payment processing is similar to using a taxi. The payment is sent to the Bank of Russia and processed immediately. In discrete mode, payment processing is similar to transporting passengers by regular bus. Payments are first accumulated, and then all of them are processed in a heap. The Bank of Russia operates several similar flights during the business day.
The schedule of flights accepted in the Moscow region is published on the website of the Bank of Russia and consists of five flights:
The Bank of Russia's tariffs for making payments via BESP are higher than in discrete mode.
Before that, we discussed how banks execute customer payments. Now let's look at how the bank makes its own payments, for example, buying paper, paying for electricity, communication services, etc.
By and large, everything is done exactly the same as in the case of customer payments, only the bank pays not from the current account, but from one of its correspondent accounts. This circumstance often puts inexperienced counterparties of the bank in a stupor, and they compulsively demand the bank's current account number, while banks usually do not have current accounts. Otherwise, everything is the same: a payment order is generated, then it is sent to the bank where the corresponding account is opened, that bank executes it and responds with an account statement.
In the 90-x years of the last century, the term "automated system" was often used in the state standards and regulatory documents of the FSTEC of Russia (then still the State Technical Commission under the President of the Russian Federation). "GOST 34.003-90 Information technology (IT). A set of standards for automated systems. Automated systems. Terms and Definitions " gives the following definition of this term:
After some time, a new term came into use — information system. In clause 3 of Article 2 of Federal Law No. 149-FZ of 27.07.2006 "On Information, Information Technologies and Information Protection", this term is defined as follows::
In this study, both terms will be used interchangeably.
The validity of this approach can be proved by the fact that in the Order of the FSTEC of Russia dated 11.02.2013 N 17 "On approval of Requirements for the protection of Information that does not Constitute a state secret contained in state information systems", the state regulator prescribes to be guided by State Standards on automated systems for the protection of information systems.
In addition to information systems, the bank's IT infrastructure also includes one more type of elements — information services, or, as they are often called, robots.
It is rather difficult to define the concept of an information service, so let's just list its main differences from an information system:
The core of any bank's information infrastructure is an automated banking system, or ABS for short.
Standard of the Bank of Russia STO BR IBBS-1.0-2014 " Ensuring information security of organizations of the banking system of the Russian Federation. General Provisions" defines ABS as follows:
This definition allows you to fit almost any IT system in a bank under it. At the same time, ordinary bank employees call ABS the system that deals with accounting for bank accounts, transactions between them (cash flow) and balances. The second definition does not contradict the first one and details it more clearly, and we will continue to use it.
In modern Russian banks, the most common ABS are the following:
Some particularly large banks do not use mass-produced ABS systems, but specially designed for them. But such cases are rare, just like especially large banks.
Sometimes banks use several ABS systems from different manufacturers in parallel. This often happens when a bank tries to switch from one ABS to another, but there may be less trivial reasons.
Despite the fact that ABS automates quite a large number of tasks, it does not cover all the bank's needs. There are tasks that the ABS does not do at all or does not do as the bank wants it to do. Therefore, other information systems that automate individual business processes are connected (integrated) to the ABS. In the future, such information systems will be called applied information systems.
Examples of applied information systems include:
Depending on the size of the bank and the services it provides, the number of applied information systems can range from units to hundreds.
In addition to ABS and applied information systems that automate basic business processes, banks also have a decent number of auxiliary infrastructure information systems. Examples of such systems can be:
Banks use a huge number of different information services that perform simple, routine functions, such as downloading BIC and FIAS reference books, publishing currency rates on the official website, etc.
Special mention should be made of the client parts of information systems external to the bank. As examples, I will give:
The following mechanisms are usually used to integrate information systems:
Under the integration module, we will understand a virtual element of the IT infrastructure that implements the integration of other elements of the IT infrastructure.
We called this element virtual, because its functionality can be implemented either as a separate specialized element of the IT infrastructure (for example, an information service), or as components of integrated information systems. Moreover, even a person who "manually" transfers information between integrated information systems can act as an integration module.
Shows a fragment of a typical bank information infrastructure containing the types of elements discussed above.
If you look at this scheme from the point of view of performing non-cash payments, you can see that the bank implements them using:
Technically, direct correspondent relations with partner banks can be organized using:
Connection to payment systems that serve plastic cards is made through standard modules that are part of processing systems.
For successful operation, the bank must ensure information security of all listed payment methods. It is very problematic to consider them within the framework of a single, even large-scale study, and therefore we will focus only on one area that is most critical from the point of view of possible losses — the bank's payment interaction with the Bank of Russia.
We will consider the IT infrastructure of the bank's payment interaction with the Bank of Russia as an example of the execution of a payment sent to a client of another bank.
As we remember from the first part, the client must first send a payment order to the bank. There are two ways to do this:
It is important to note here that RBS systems are only systems that provide legally significant electronic document flow between the client and the bank, and they do not make payments independently. That is why when a client opens a bank account, they usually enter into two contracts. The first is a contract for servicing a bank account, the second is a contract for electronic document management using the RBS ICB system. If the second agreement is not concluded, the client will still be able to use their account, but only during a personal visit to the bank's branch.
If the client has submitted a payment order in hard copy, the bank employee makes an electronic payment order based on it to the ABS. If the order was submitted via the RBS of the ICB, then it is automatically sent to the ABS via the integration module.
Proof that it was the client who made the order to transfer funds, in the first case, is a paper document personally signed by him, and in the second, an electronic document in the RBS of the ICB, certified in accordance with the agreement.
Usually, for certification of electronic documents of clients — legal entities, RBS ICB uses a cryptographic electronic signature, and for documents of clients — individuals, SMS confirmation codes are used. From a legal point of view, banks usually use the legal regime of a handwritten signature analog (TSA) to certify electronic documents in both cases.
Once in the ABS, the payment order is monitored in accordance with the bank's internal regulations and sent for execution to the Bank of Russia's payment system.
The technical means (software) used to interact with the Bank of Russia payment system may vary depending on the territorial institution of the Bank of Russia that serves the bank's correspondent account.
For banks served in the Moscow region, the following software applies:
APM KBR is software used by authorized employees of the bank to encrypt and electronically sign outgoing payment documents, as well as decrypt and verify the electronic signature of payment documents received from the Bank of Russia. But, to be more precise, the KBR Automated Control System operates not with payment documents, but with electronic messages (ES), which are of two types:
The list and formats of electronic messages are established by the Bank of Russia by issuing an Album of Unified Formats of Electronic Banking Messages (UFEBS).
In order for the KBR AWP to process the payment, it must be converted to a file containing an electronic payment message in the UFEBS format. The ABS integration module with the Bank of Russia payment system is responsible for this transformation. From a technical point of view, such conversions are quite simple, since the UFEBS format is based on XML.
Files of electronic messages leave the ABS integration module in open format and are placed in a special folder of the file system (usually a network folder), which is configured in the KBR WORKSTATION for electronic messages with the status "Entered". In the previous diagram, this folder is designated as "Folder 1".
Then, during processing, electronic messages change their statuses to "Controlled", "Sent" , etc., which is technically implemented by moving the file with the electronic message to the corresponding folders that are configured in the KBR AWP. In the diagram (Fig. 2), these folders are designated as "Folder 2".
At a certain moment of technological processing (established by the bank's internal regulations) of outgoing electronic messages, they are encrypted and signed with an electronic signature using SCAD Signature and private cryptographic keys of responsible employees.
SCAD Signature is a SCSI developed by Validata LLC on behalf of the Bank of Russia and designed to protect information in the Bank of Russia's payment system. This SCSI is not publicly available (except for the documentation posted on the CBR website), and it is distributed by the Bank of Russia only to participants of its payment system. The distinctive features of this SCSI include::
Encrypted and signed electronic messages are placed in a special folder, in the diagram this is "Folder 3". UTA continuously monitors this folder and, if it sees new files there, transmits them to the Central Bank of the Russian Federation in one of the following ways:
After reaching out to the Central Bank (in the first or second way), UTA transmits electronic messages through the API published by the Central Bank. During communication sessions, UTA also receives input electronic messages from the Central Bank.
It should be noted that all electronic messages that UTA works with are encrypted and signed with an electronic signature.
After receiving an encrypted email, UTA moves it to the folder with incoming encrypted messages. The authorized employee checks the electronic signature and decrypts the message with the help of their cryptographic keys and APM KBR.
Further processing is performed depending on the type of electronic message. If this is a payment message, it is transmitted to the ABS via the integration module, where accounting entries are generated based on it, which change the account balances. It is important to note that when the ABS (integration module) interacts with the KBR AWP, standard format files are used in open format.
During the operation of the automated control system, the KBR keeps a log of its work, which can be implemented in the form of text files or using databases running under the DBMS.
We have considered the "classic" scheme of the system operation. In reality, there are many varieties of it. Let's look at some of them.
Type 1. Separating message sending and receiving paths
The scheme is implemented with two AWP KBR. The first one works with human participation and performs only sending messages, the second one works in automatic mode and performs only receiving messages.
AWP KBR
Version 2. The full automatic is configured to work completely in automatic mode without human intervention
APM KBR
Version 3. Isolated APM KBR functions as a dedicated computer that is not connected to the bank's network. Electronic messages are transmitted to it by a human operator using OMNI.
The Bank of Russia plans to switch to a new technological payment processing scheme, in which electronic messages will be signed not in the KBR AWP, as was previously the case, but in the ABS (more precisely, in the ABS — KBR AWP integration module).
To implement this approach, a new version of the KBR AWP was released, which became known as the KBR-N AWP (new). All the main changes can be seen if you compare the schemes of information flows passing through the AWP of the CBD of the old and new versions.
Let's consider the scheme of information flows in the classic AWP KBR. The source of the scheme is the official documentation for the KBR AUTOMATED WORKSTATION " AUTOMATED WORKPLACE OF a BANK OF RUSSIA CLIENT. Programmer's guide. CBRF.61209-04 33 01".
Notes.
Now let's take a look at a similar scheme for the new KBR-N AWP. Source " AUTOMATED WORKPLACE OF A BANK OF RUSSIA CLIENT NEW. Programmer's guide. CBRF.61289-01 33 01"
From the cryptographic point of view, the KBR-N automated workplace is responsible for encrypting / decrypting electronic messages, as well as for verifying electronic signatures on them. Electronic signature generation has been moved to the ABS integration module.
It is logical to assume that this module will also have to check signatures for messages received from the KBR-N AWP. From a technical point of view, this is not mandatory, but from a security point of view, it is critical, since it ensures the integrity of messages transmitted between the ABS and the KBR-N AWP.
In addition to the file interface for interaction between the ABS, the KBR-N automated workstation and the UTA, the IBM WebSphere MQ interface has been added, which allows you to build a service-oriented IT infrastructure of the bank and solve the problem of the old scheme with the organization of simultaneous work of several operators responsible for sending payments.
Next, we'll look at:

In the modern Russian economic environment, there are many different types of organizations. These can be state-owned enterprises( FSUE, Municipal Unitary enterprise), public funds, and, finally, ordinary commercial organizations. The main difference between the latter and all others is that their main goal is to maximize profit, and everything they do is aimed at this.
A commercial organization can earn money in various ways, but the profit is always determined in the same way – it is income minus expenses. At the same time, if security is not the main activity of the company, then it does not generate revenue, and if so, then in order for this activity to make sense, it must reduce costs.
The economic effect of ensuring business security is to minimize or completely eliminate losses from threats. However, it should also be taken into account that implementing security measures also costs money, and therefore the true profit from security will be equal to the amount saved from implementing security threats, reduced by the cost of security measures.
One day, a conversation took place between the owner of a commercial bank and the head of the security service of his organization on the topic of the economic effect of security. The essence of this conversation most accurately reflects the role and place of security in the life of the organization:
- Security should not interfere with business.
— But you have to pay for security, and you have to pay for the lack of it.
The ideal security system is the golden mean between neutralized threats, resources spent on it, and business profitability.
The reasons for creating a SIB may vary. Let's highlight two main ones:
In relation to credit institutions, the need for the existence of an SIB is fixed in the following documents:
The functionality required from SIB is spelled out in the above-mentioned documents. The staff size is not strictly regulated, with the exception, perhaps, of the license requirements of the Federal Security Service of Russia for cryptography (at least 2 employees, but they may be in different divisions) and can be selected by the organization independently. To justify the size of the staff, it is recommended to use the document-Recommendations in the field of standardization of the Bank of Russia " Ensuring information security of organizations of the banking system of the Russian Federation. Resource support of information security "RS BR IBBS-2.7-2015"
From the point of view of the SIB's subordination, there is only one restriction prescribed in the above — mentioned provisions of the Central Bank of the Russian Federation - "The Information Security Service and the informatization (automation) service should not have a common supervisor", otherwise the organization remains free to choose. Let's consider typical options.
Table 1.
When interacting with other structural divisions and top management of the bank, the SIB of any organization has one common problem — proof of the need for its existence (financing).
The problem is that the amount of money saved from neutralized information security threats cannot be accurately determined. If the threat is not realized, then there is no damage from it, and if there are no problems, then there is no need to solve them.
To solve this problem, the SIB can act in two ways:

We will highlight the practical aspects of security that must be communicated to top management and other structural divisions, as well as taken into account when building an information security system:
Summing up the intermediate result of the above, we note that the created system of information security of non-cash payments should have a practical focus and be cost-effective. The best way to achieve these properties is to apply a risk-based approach.

Information security is just one of the areas of ensuring security (economic security, physical security, fire safety,...). In addition to information security threats, any organization is subject to other equally important threats, such as threats of theft, fires, fraud by unscrupulous customers, threats of violation of mandatory requirements (compliance), etc. etc.
Ultimately, an organization doesn't care what specific threat it suffers losses from, whether it's theft, fire, or computer hacking. The amount of losses (damage) is important.
In addition to the amount of damage, an important factor in assessing threats is the probability of their implementation, which depends on the specifics of the organization's business processes, its infrastructure, external malicious factors, and the countermeasures taken.
The characteristic that takes into account the damage and the probability of the threat being realized is called risk.
Note. A scientific definition of risk can be obtained in GOST R 51897-2011
Risk can be measured both quantitatively, for example, by multiplying damage by probability, and qualitatively. A qualitative assessment is made when neither the damage nor the probability is quantified. The risk in this case can be expressed as a set of values, for example, damage — "medium", probability - "high".
Assessing all threats as risks allows an organization to effectively use its available resources to neutralize exactly those threats that are most significant and dangerous for it.
Risk management is the main approach to building a comprehensive, cost-effective security system for an organization. Moreover, almost all banking regulations are based on the risk management recommendations of the Basel Committee on Banking Supervision.

We will highlight the main threats inherent in the activities of making bank non-cash payments, and determine the maximum possible damage from their implementation.
Table 2.
Here, the analyzed activity includes a set of business processes:
In the future, we will only consider issues related to ensuring the security of correspondent relations with the Bank of Russia. Nevertheless, the obtained results can be used to ensure security and other types of calculations.

When considering the main threats, we estimated their damage, but did not estimate the probability of their implementation. The fact is that if the maximum possible damage is the same for all banks, then the probability of implementing threats will differ from bank to bank and depend on the applied protective measures.
One of the main measures to reduce the likelihood of information security threats will be:
We will not talk about IT practices here, we will only touch on information security issues.
The main nuance that needs to be taken into account in ensuring information security is that this type of activity is rather tightly regulated by the state and the Central Bank. No matter how the risks are assessed, no matter how small the resources available to the bank, its protection must meet the established requirements. Otherwise, it will not be able to work.
Consider the information security requirements imposed on the business process of correspondent relations with the Bank of Russia.
Table 3.
We will also outline additional requirements for the organization of information security. These requirements will apply only to some banks and only in some cases:
The final results of applying all these requirements should be an information security system that meets any of the listed documents. In order to create such a system, requirements are summarized in a single table and in cases where there are several similar requirements, the most stringent ones are selected.
There is an important caveat here: the requirements set out in regulatory documents, as a rule, do not contain strict specifics. They indicate what the security system should look like, what tools it should consist of, and what tactical characteristics it should have. An exception will be requirements that come from the operational documentation for the information security tools used, for example, for the SCAD Signature SCSI.
Consider, for example, a fragment of the requirements of FSTEC Order No. 21
As we can see, the requirements of AVZ.1 and AVZ.2 indicate that there should be anti-virus protection. These requirements do not regulate exactly how to configure it, on which network nodes to install it (the Letter of the Bank of Russia dated 24.03.2014 N 49-T recommends that banks have antivirus products from various manufacturers on their ARMas, servers, and gateways).
The situation is similar with computer network segmentation-a VMS requirement.17. The document only prescribes the need to use this practice for protection, but does not say how the organization should do this.
You can find out exactly how information security tools are configured and how security mechanisms are implemented from a private technical specification for an information security system formed based on the results of modeling information security threats.
Thus, a comprehensive information security system should be a set of protective business processes (controls in the English – language literature), built taking into account the implementation of mandatory requirements, current threats, and information security practices.
To form a high-quality threat model, it is necessary to take into account existing practices and practices on this issue.
In this article, we will conduct a rapid review of about 40 sources describing the processes of threat modeling and information security risk management. We will consider both state standards and documents of Russian regulators (FSTEC of Russia, FSB of Russia, Central Bank of Russia), as well as international practices.
The end result of the threat modeling process should be a document-a threat model containing a list of significant (relevant) information security threats for the protected object.
When modeling threats, protected objects are usually considered as protected objects.:
By and large, the threat model does not need to be presented in the form of a list. It can be a tree (graph), a mind map, or any other form of recording that allows specialists to work with it conveniently.
The specific composition of threats will depend on the properties of the protected object and the business processes implemented using it. Accordingly, one of the source data for modeling will be a description of the protected object itself.
If a certain hypothetical object is considered, then a typical (basic) threat model is formed. If a real object is considered, then a private threat model is formed.
When modeling threats, in addition to describing the protected object, specialists must have knowledge about the threats themselves.
In practice, this knowledge can be gleaned from:
The initial stage of the modeling process will be threat identification, i.e. selecting the largest possible list of threats that can at least theoretically affect the protected object.
When implementing this stage, nature plays a cruel joke with information security specialists. The problem is that human memory is associative, and we can not take and extract all the contents from it, for example, to remember all possible threats.
In order to create a list of all possible threats, various tricks are used that allow specialists to ask themselves certain questions or use the principles by which threats will be extracted from memory and recorded. Examples of such techniques can include threat classifiers, threat trees, or patterns of typical computer attacks. We'll talk about these methods below.
Once the list of all possible threats is formed, it is filtered so that only threats that are relevant to the organization are left in the end. The filtering process is usually performed in several iterations, each of which discards threats based on one or another feature.
They start with a sign indicating that violators have the capabilities (resources) to implement threats. To determine it, first create a special document-a model of the violator, in which possible violators are identified and their capabilities are determined. Then they correlate the previously received threats with the intruder's model and discard all threats that are beyond the capabilities of potential intruders.
The next sign for filtering threats is the sign that the risk is insignificant. First, the organization determines the level of risk that it considers insignificant. Then it evaluates the risk from the implementation of each threat and, if it is less than or equal to this level, the threat is discarded.
Thus, after filtering is completed, a threat model will be obtained that contains information security threats that are significant (relevant) for the organization.
Take, for example, the problem of modeling threats to the security of personal data (PD) processed in personal data information systems (ISPDn).
The FSTEC of Russia in 2008 issued a methodological document for this purpose – the Basic Model of PD threats This document contains many classification schemes, of which we will consider the only one as an example — the classification of threats by "source of threat".
A specialist building a private threat model can use this scheme, ask yourself the question: "What threats to personal data will come from the actions of an internal intruder?" and record these threats. Then ask the following question: "How can an external intruder attack personal data?" and so on. Such a series of questions allows the specialist to describe all the threats known to him, without forgetting anything.
At the beginning, a high-level threat is formulated, which will be the root of the future tree.
Then the specialist begins to decompose this threat into low-level ones, the implementation of which can lead to the implementation of the threat in question. To do this, they may ask questions about how or how the threat under investigation can be implemented.
The threats received in this case are children of the one under consideration and are recorded in the tree as its descendants. Then they, in turn, are also decomposed, and so on until the required level of detail is reached.
This approach has long been known in engineering and is used to build fault trees, the formation of which is standardized in GOST R 51901.13-2005 (IEC 61025:1990) Risk management. Analysis of the fault tree.
To illustrate the use of "threat trees", we will consider the formation of a threat model for an informatization object, which is an isolated computer that is not connected to a computer network. Let's assume that this object processes important information that needs to be secured.
As a high-level threat, we define the following: violation of the security properties of protected information.
Generally accepted security properties are confidentiality, integrity, and availability. Thus, child threats will be:
We decompose the threat of "violation of the confidentiality of protected data".
Let's ask ourselves the question: "How can this threat be implemented?" and write down the following options as an answer::
We will do the same with the threat of "violation of the integrity of protected data". It can be decomposed into:
The decomposition of the threat "violation of the availability of protected data" can be represented by the following threats::
As a result, we get the following tree:
As we can see, even such a primitive model that we have just built is quite cumbersome when it is displayed graphically. Therefore, "threat trees" are mostly documented as hierarchical lists.
This technique is based on the idea that when performing computer attacks, attackers always perform a certain similar sequence of actions, which can be called a template for a typical attack.
One of the most well-known computer attack patterns at the moment is the kill chain pattern described by Lockheed Martin Corporation, which includes 7 stages:

Stage 1. Intelligence-collecting data about the attacked object.
Stage 2. Weaponization – development of tools (malicious code) for conducting an attack.
Stage 3. Delivery – delivery of malicious code to the target object.
Stage 4. Penetration (Exploitation) – using any vulnerability of the node of the attacked object to run malicious code.
Stage 5. Installation – installation of a hidden remote access system on a compromised node.
Stage 6. Obtaining control (C2) - organizing a remote access channel for intruders to the compromised node.
Stage 7. Actions – performing the actions for which the attack was carried out.
The research organization MITRE, slightly changing the names of the stages, called this template-Cyber Attack Lifecycle.

In addition, MITRE expanded the description of various stages and formed a matrix of typical tactics of attackers at each stage. This matrix was named ATT&CK.

(clickable)
Although the above matrix is not universal, it still allows you to describe the actions taken by attackers when committing a large number of real attacks.
From the point of view of threat modeling, the template of a typical attack can be considered as a threat classifier, and the matrix of typical tactics can be considered as a significant fragment of the threat model.
Only the last stage of the template – "Actions" - will require clarification, which is what the attack was carried out for, and the stages themselves can be supplemented with tactics that were not taken into account.
Both documents are methodological, that is, they are not required to be applied, but they reveal how, in the opinion of the FSTEC of Russia, the problem of modeling personal data security threats should be solved.
The FSTEC Basic Model of Personal Data Threats, 2008 contains unified source data on security threats to personal data processed in the ISPDn related to:
Sets a formal description of threats:
The following abbreviations were used to formally describe threats::
ISPDn – personal data information system.
NSD – unauthorized access.
PMV – software and mathematical impact (introduction of malicious programs).
The document contains classification criteria for threats and vulnerabilities, as well as malware. A small catalog of typical threats related to leaks through technical channels and unauthorized access is provided. A typical model of violators is given and their capabilities are determined.
The methodology for determining actual threats of the 2008 PD defines an algorithm that can be used to filter threats based on insignificant risk. To do this, the methodology provides methods for determining the possibility of implementing a threat (probability), an indicator of the threat's danger (damage), and rules for classifying a security threat as not relevant (having an insignificant risk).
Methodological document of the FSTEC of Russia. Information security measures in state information systems (approved by the FSTEC of Russia on 11.02.2014). Information security threats (UBI) are determined based on the results of assessing the capabilities (potential, equipment and motivation) of external and internal violators, analyzing possible vulnerabilities in the information system, possible ways to implement information security threats and the consequences of violating information security properties (confidentiality, integrity, availability).
Formal description of the threat to information security:
UBI: = [capabilities of the intruder; vulnerabilities of the information system; method of implementing the threat; consequences of implementing the threat].
The capabilities (potential) of violators are divided into three groups:
An explanation of the capabilities of violators is given in the draft methodological document of the FSTEC of Russia. Methodology for determining information security threats in information systems.
Vulnerabilities are described and classified using national standards:
The vulnerabilities themselves, how threats are implemented, and possible damage are listed in the threat database of the FSTEC of Russia.
The guidelines identify the main threats to personal data that can be neutralized only with the help of SCSI. These include:
The document also defines a classification of violators capabilities:
Letter of the Central Bank of the Russian Federation No. 197-T dated December 7, 2007 "On risks in remote banking services" contains a list of typical threats to remote banking systems and their clients, including:
The Bank of Russia's Directive No. 3889-U of December 10, 2015 "On determining threats to the security of personal data Relevant to the processing of personal data in personal data information systems" contains an industry-specific list of threats to the security of personal data, including the following threats:
Recommendations in the field of standardization of the Bank of Russia RS BR IBBS-2.2-2009. "Methodology for assessing information security breach risks"
The document suggests the following risk assessment procedures::
Procedure 1. Determination of the list of types of information assets for which the procedures for assessing the risks of an information security breach are performed (hereinafter referred to as the area of assessing the risks of an information security breach).
Procedure 2. Determining the list of types of environmental objects corresponding to each of the types of information assets in the field of information security risk assessment.
Procedure 3. Identify sources of threats for each of the types of environment objects defined in procedure 2.
Procedure 4. Determination of the information security threat SVR in relation to the types of environmental objects defined in the framework of the procedure 2.3.
Procedure 5. Determination of the STP of an information security breach for the types of information assets in the information security risk assessment area.
Procedure 6. Assessment of information security breach risks.
The degree of risk tolerance is proposed to be assessed using the "classical" risk assessment table, which takes into account the probability and possible damage.
Here SVR is the degree of possibility of implementing the threat, and STP is the severity of the consequences.
The recommendations also contain a small catalog of threats, divided by class.
Class 1. Sources of information security threats related to adverse events of natural, man-made, and social nature
Class 2. Sources of information security threats related to the activities of terrorists and persons committing crimes and offenses
Class 3. Sources of information security threats related to the activities of suppliers/providers/partners
Class 4. Sources of information security threats related to failures, failures, destruction/damage of software and hardware
Class 5. Sources of information security threats related to the activities of internal information security violators
Class 6. Sources of information security threats related to the activities of external information security violators
Class 7. Sources of information security threats related to non-compliance with the requirements of supervisory and regulatory authorities and current legislation.
GOST R 51275-2006. Information protection. An informatization object. Factors affecting the information. General provisions
This GOST is ideologically related to GOST R 50922-2006 Information security. Basic terms and definitions, the methodological document " Special requirements and recommendations for the protection of confidential information (STR-K) "(DSP) and current documents on certification of informatization objects. The document contains a classification of factors that affect information that can be interpreted as threats to information security.
GOST R ISO / TO 13569-2007. Financial services. Information Security Recommendations
Appendix " C " of this standard contains an example of information security risk assessment for a credit and financial institution. To do this, it is proposed to analyze among the main objects of malicious impacts, including personnel, hardware, business applications, communication systems, software tools and operating systems. Risk damage is assessed as financial losses, reduced productivity, reputational damage, and total damage.
GOST R 56545-2015 Information security. Vulnerabilities of information systems. Rules for describing vulnerabilities and GOST R 56546-2015 Information security. Vulnerabilities of information systems. Classification of information system vulnerabilities are used to describe vulnerabilities in information systems. The standards are applied in conjunction with the fundamental GOST R 50922-2006 Information Security. Basic terms and definitions.
The standards provide a classification of information system vulnerabilities, which contains three classification features:
The vulnerabilities themselves are proposed to be described in the form of a passport containing the following sections:
The standards suggest using OVAL as the language of vulnerability detection rules.
GOST R 53113.1-2008 Information Technology (IT): Protection of information technologies and automated systems from information security threats implemented using hidden channels. Part 1. General provisions
The standard describes threats associated with hidden channels, which are defined as communication channels that are unintended by the developer of information technology and automated systems and can be used to violate the security policy.
GOST R 52448-2005 Information security. Ensuring the security of telecommunication networks. General provisions
This document is a methodological document for telecom operators and contains a general scheme of actions to protect communication networks.
It is proposed to use GOST R 51275-2006 as the basis of the threat modeling process. Information protection. An informatization object. Factors affecting the information. General provisions. The standard provides a model of alleged violators.
A distinctive feature of this document is that in addition to the classical properties of information security, such as confidentiality, integrity, and availability, the standard also considers accountability.
Under accountability, the standard defines a property that provides unambiguous tracking of network activities of any object. Violation of accountability — denial of actions in the network (for example, participation in a perfect communication session) or forgery (for example, creating information and claims that were allegedly received from another object or sent to another object).
GOST R ISO / IEC 27005-2010. Information technology. Methods and tools for ensuring security. Information security risk management
This standard is part of a group of information security standards, often referred to as ISO 27K. The document focuses on management procedures for managing information security risks.
Appendix C provides examples of typical threats, and Appendix D provides typical vulnerabilities.
NIST SP 800-30. Guide for Conducting Risk Assessments
The document focuses on risk management issues at the organization's management level.
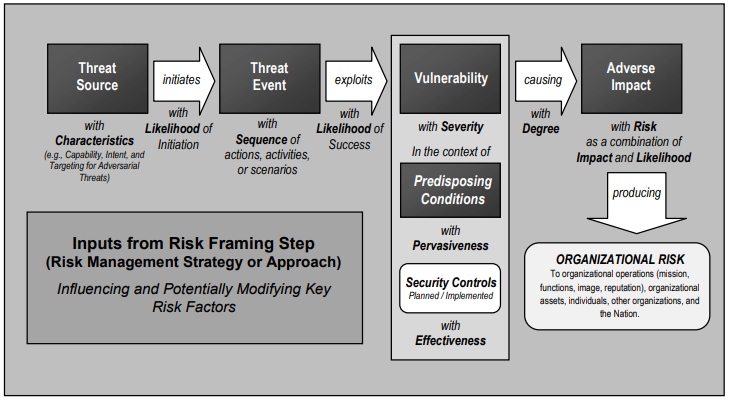
NIST SP 800-39. Managing Information Security Risk
This document describes the methodology for managing enterprise-level information security risks. The main goal of the methodology is to link the information security system with the mission and goals of the organization

The threat tree methodology is used to identify threats performed in step 5.
Distinctive features of this methodology are:
Microsoft uses the Security Development Lifecycle methodology to develop secure software. This methodology is an extension to the "classic" cascade model of software development ("waterfall"), which introduces additional security-related steps. At the "design" stage, it is proposed to conduct threat modeling.

We suggest using several approaches to identify threats:
The STRIDE methodology is a classification scheme for describing attacks based on the type of exploits used to implement them or the attacker's motivation.
STRIDE is an acronym for the first letters:
After identifying threats, SDL suggests evaluating the risks they generate. The DREAD method can be used for this purpose.
The name of the DREAD method is also an acronym for the first letters of the risk assessment categories:
The risk itself is estimated by the formula:
Risk_DREAD = (DAMAGE + REPRODUCIBILITY + EXPLOITABILITY + AFFECTED USERS + DISCOVERABILITY) / 5,
where the value of composite elements varies from 0 to 10. For example, the Damage Potential value can be defined as:
At some point in time, the number of selected materials has grown into quality, so this selection may be of interest in itself.
2. "Hackers from Moscow face 10 years for stealing 20 million rubles from a bank”, – sobesednik.ru, 2015
4. Plot: "Theft from the Russian International Bank (RMB)"
a) "Hackers stole more than half a billion rubles from the correspondent account in the Central Bank," — interfax.ru, 2016
b) "Russian International Bank named the amount of funds stolen by hackers”, — rbc.ru, 2016
5. Plot: "Theft from Metallinvestbank"
a) "Hackers withdrew 677 million rubles. from the accounts of Metallinvestbank", – rbc.ru, 2016
b) ” Due to a hacker attack, Metallinvestbank lost 200 million rubles, " — ria.ru, 2016
c) "Metallinvestbank press release on theft", — metallinvestbank.ru, 2016
d) "Hacker-style robbery”, — kommersant.ru, 2017
6. "ABS didn't work”, – kommersant.ru, 2016
7. "Hackers stole almost 2 billion rubles from banks with the help of" letters from the Central Bank " – RBC.ru, 2016
8. "A million in a couple of minutes. How hackers rob banks around the world”, — 21.by, 2016
9. "Hackers" accused of embezzling more than 2.6 million rubles from bank accounts in various regions of the country will appear in court in the Sverdlovsk region" - Prosecutor General's Office of the Russian Federation, 2016
10. Plot: Hacker group Lurk
) "Lurk Banking Trojan: specially designed for Russia", — Securelist.ru, 2016
b) "Employees of the Russian Ministry of Internal Affairs and the Federal Security Service of Russia detained Internet hackers”, - Ministry of Internal Affairs of Russia, 2016
c) "Hunting for Lurk”, — Securelist.ru, 2016
11. "The court recovered 470 million rubles from the processing company UCS”, — vedomosti.ru, 2016
13. "Group-IB assessed the scale of activity of Russian-speaking hackers MoneyTaker”, — rbc.ru,2017
14. "The co-founder of Group-IB spoke about those who committed a cyber attack on Russian banks”" — rbc.ru, 2017
15. Plot: "Theft from the bank "Globex"
a) "Hackers came running to SWIFT”, — kommersant.ru, 2017
b) "Hackers came to Globex, — kommersant.ru, 2017
c) "Hackers stole $1 million from a VEB subsidiary bank”, — vedomosti.ru, 2017
16. "Hacker attacks were grouped together”, — Коммерсант.ги, 2017
17. "Digital Security denies Zeronights member's connection to MoneyTaker", — anti-malware.ru, 2017
18. Plot: A group of 14 hackers robbing banks
a) "A boxer from Ukraine led a group of hackers who stole 1 billion rubles from banks”" — Life.ru, 2016
b) "The hacker's remorse program worked”" — kommersant.ru, 2017
c) "The court breaks into a hacker network”,- kommersant.ru, 2017
20. Plot: "Criminal group from Volzhsky"
a) "A hacker who stole funds from bank cards was detained in Volzhsky”" - SecurityLab.ru, 2018
b) "Hackers earned up to half a million a day”, — Коммерсант.ги, 2018
21. Plot: "Preparing for an attack on Russian payment systems"
a) "In Seversk, a hacker was convicted for preparing an attack on Russian payment systems”" — SecurityLab.ru, 2018
b) "A cyberattack on Russian electronic payment systems was prevented in Tomsk”, — ib-bank.ru, 2018
22. "In the Stavropol Territory, a hacker was detained for hacking ATMs and stealing funds”" - SecurityLab.ru, 2018
23. "In Saratov, a hacker stole more than 380 thousand rubles using a phishing site”, — SecurityLab.ru, 2018
24. "St. Petersburg hacker stole funds from bank cards”, — SecurityLab.ru, 2018
25. "Ghost hackers steal money from the Central Bank”, — dailystorm.ru, 2018
26. "Novice hackers have teachers on hacking ATMs," — dni24.com, 2018
27. Plot: "Arrest of the leader of the criminal group Carbanak / Anunak / Cobalt"
) “Mastermind behind eur 1 billion cyber bank robbery arrested in spain”, — Европол, 2018 + (here)
b) "A Ukrainian hacker, allegedly the leader of Carbanak, has been arrested," -SecurityLab.ru, 2018
c) "The leader of Carbanak got caught on unwillingness to pay for the car on time”, — SecurityLab.ru, 2018
28. Plot: "The continuation of the activity of the criminal group Cobalt after the arrest of its leader"
a) "Group-IB: Despite leader's arrest, Cobalt group continues attacks on banks” - Group-IB, 2018
b) "The arrest of the leader did not stop the activities of the Cobalt group: hackers attacked major banks in Russia and the CIS”" — xakep.ru, 2018
29. "Cybercriminals who stole funds from bank customers have been convicted in Moscow —" SecurityLab reports.Ru, 2018
30. "PIR Bank lost more than 58 million rubles as a result of a cyber attack —" - SecurityLab.Ru, 2018
31. "The investigative bodies of the Ministry of Internal Affairs of Russia sent to the court a case on embezzlement of funds from bank cards of citizens", - The Ministry of Internal Affairs of Russia, 2018
32. "Cyber fraudsters convicted in Moscow for stealing money through online banking accounts” - Interfax news agency, 2018
33. Plot: "Theft from the" PIR Bank "
a) "PIR for hackers", — kommersant.ru, 2018
b) "How do you like this, Carbanak?", — Gorup-ib.ru, 2018
34."The Prosecutor's Office of the Republic of Bashkortostan sent a criminal case to the court on the fact of theft by hackers of more than 8 million rubles”" - the Prosecutor General's Office of the Russian Federation, 2018
35. "In the US, a court has charged 3 members of the hacker group Carbanak", — SecurityLab.ru, 2018
36. "Yekaterinburg hackers stole 1.2 billion rubles from banks," — SecurityLab.ru, 2018
37. "In Rostov, a hacker stole more than 1 million rubles from an ATM", — SecurityLab.ru, 2018
38. "Hackers have withdrawn about $ 100,000 from the Housing Finance Bank," RIA Novosti, 2018
3. Report: "Attacks on brokerage and settlement systems”, - Group-IB, 2015
4. Big Bank Heist: The Carbanak APT campaign, – securelist.ru, 2015 (+ english report)
6. Report: "Buhtrap: Evolution of targeted attacks on banks”, - Group-IB, 2016
7. Отчет: “Cobalt snatch”, — Positive Technologies, 2016
9. "Following the trail of Cobalt: tactics of a logical attack on ATMs in the investigation of Group-IB”,-Group-IB company blog on habr.com, 2017
10. "Secrets of Cobalt As the Cobalt Group overcomes security measures”, - Group-IB, 2017
11. "MoneyTaker: Group-IB Stealth hunt declassifies hackers attacking banks in the US and Russia” - Group-IB, 2017
12. "Lazarus Technologies of espionage and targeted attacks by pro-government hackers from North Korea and unknown details of their operations in the Group-IB report "Lazarus: Architecture, Tools, attribution", - Group-IB, 2017
13. Attacks on ATMs on the example of GreenDispenser: organization and technology”, - Positive Technologies, 2017
14. "The Silence — a new targeted attack on financial institutions", — Securelist.ru, 2017
15. "TwoBee Financial Campaign", — Securelist.ru, 2017
17. "New attacks on banks” - Positive Technologies, 2018
18. Webinar: "Research on targeted attacks on financial institutions”, - Positive Technologies, 2018 (+ presentation)
19. "Attacks on industrial enterprises using RMS and TeamViewer", — Securelist.ru, 2018
20. "Hackers attack banks using Microsoft Publisher files", — SecurityLab.ru, 2018
3. "Report of the Center for Monitoring and Responding to Computer attacks in the Credit and Financial Sector of the Main Directorate for Information Security and Protection of the Bank of Russia: June 1, 2016-September 1, 2017", - FinCERT of the Central Bank of the Russian Federation, 2017
4. "The main types of attacks in the credit and financial sector in 2017”, - FinCERT of the Central Bank of the Russian Federation, 2017
5. "Review of unauthorized money transfers in 2017”, - FinCERT of the Central Bank of the Russian Federation, 2017
6. "Cybercriminals against Financial institutions: what to expect in 2018", — Securelist.ru, 2017
7. Webinar: "Current cyber threats-2017: trends and forecasts”, - Positive Technologies, 2018 (+ report)
1. "Materials of court proceedings between JSC Kemsotsinbank and other banks through which the money stolen from it was cashed" - Arbitration and Appeal Courts, 2017-18 (here and here)
2. "Archive securelist.ru, category "Attack on banks", — securelist.ru
3. FinCERT of the Bank of Russia, — Bank of Russia
4. "Investigations of high-tech crimes”, - Rubricator on the site Group-IB.ru
5. The story " Hacker attacks on Russian banks”, - RIA Novosti
6. Threat Actor Map
7. Category: "Burglary guards", — Komersant.ru
8. "Rubricator: Cybercrime on the official website of the Ministry of Internal Affairs of Russia" — - Ministry of Internal Affairs of Russia
9. Periodic reports: State of Crime — Ministry of Internal Affairs of Russia
3. "VM escape: 101", - Digital Security company blog on habr.com, 2014
7. "Automated Code Analysis: Web application vulnerability statistics for 2017”, - Positive Technologies, 2017
8. "Statistics of attacks on web applications: IV quarter of 2017”, - Positive Technologies, 2017
9. "Corporate information Systems: penetration testing attack scenarios”, - Positive Technologies, 2017
10. Webinar: "Typical scenarios of attacks on wireless networks”, - Positive Technologies, 2017 (+ presentation)
11. Webinar: "Typical scenarios of attacks on a corporate information system”, - Positive Technologies, 2017 (+ presentation)
13. Webinar: "Advanced attacks on Microsoft Active Directory: ways to detect and protect", - Positive Technologies, 2018 (+ presentation)
14. "Vulnerabilities of corporate information systems 2018", - Positive Technologies, 2018
15. "How Social Engineering opens doors to hackers in your organization” - Positive Technologies, 2018
16. Webinar: "ATM Security Analysis: logical attacks and vulnerabilities”, - Positive Technologies, 2018 (+ presentation)
17. "They got to the bills through the safe," — kommersant.ru, 2018
18. "Low-level hacking of NCR ATMs", - Positive Technologies company blog on habr.com, 2018
2014
2. "Attacks on automated banking systems”, BIS-journal, 2014
4. "21st Century Heist: Hackers managed to steal $1 billion” - Kaspersky Lab, 2015
5. “Russian financial cybercrime: how it works”, — securelist.com, 2015
7. "A banker who can steal everything” – securelist.com, 2016
8. "Hackers against banks: the most high-profile crimes of recent years", — Rbc.ru, 2016
10. "Targeted attacks on banks Russia as a testing ground”, - Group-IB, 2017
11. "Hacker-style robbery”, — Kommersant.ru, 2017
13. "$3,000 per night. How do cybercriminals who can rob anyone work? " — tut.by, 2018
14. "Cyber attacks are our daily routine. Hackers targeted mobile banks and industry”, — 360tv.ru, 2018
15. "Attacks on banks”, - Positive Technologie, 2018
16. "Theft schemes in RBS systems and five levels of countering them",-Group-IB company blog on habr.com, 2018
17. "Pegasus crept up unnoticed", — Kommersant.ru, 2018
18. "Criminal Cyber Services Market 2018", - Positive Technology, 2018
19. "Trojans are multiplying in mobile banking", — Kommersant.ru, 2018
20. «APT Trends Report Q2 2018», — Securelist.com, 2018
21. "On crimes committed using modern information and communication technologies" — Prosecutor General's Office of the Russian Federation, 2018

(c) The Ministry of Internal Affairs of Russia. A fragment of surveillance footage from the moment when money was stolen from an ATM
Further in the article we will present a sample of more than one hundred real crimes of recent years. All considered crimes will be classified and provided with a brief description. Then a comprehensive analysis will be conducted, which will provide answers to the main questions of banking security, in particular:
The sources of data on crimes included in the sample were articles on news resources and press releases of law enforcement agencies: the Ministry of Internal Affairs of the Russian Federation, the Prosecutor General's Office of the Russian Federation, the Investigative Committee of the Russian Federation, etc.
Given the huge number of" ordinary " crimes, the sample size for them was limited to the last year — approximately from 07.2017 to 07.2018. The time range of the analyzed "computer" crimes is wider — from 2015 to 2018.
From the point of view of banking security, the most important factors in the analysis of crimes will be:
Based on the above, all the crimes under consideration were classified as follows::
In the beginning, they were divided into two types:
Then crimes of each type were divided into two categories:
Each of the resulting categories, in turn, was divided into two more types:
The generalized classification scheme is as follows:
The description of each crime includes the name and reference of the original article, followed by a summary description of the crime as a table.
Example.
"In Krasnoyarsk, the police detained suspects in the theft of 15 million rubles from ATMs," - Banks. <url>, 2018
Here:
Crime type-contains a brief description of the crime.
Articles of the Criminal Code of the Russian Federation — contains a list of articles of the Criminal Code of the Russian Federation, according to which law enforcement agencies have qualified this crime.
Damage (million rubles — - contains the amount of total damage caused by the crime, expressed in millions of rubles. If the crime involved amounts in foreign currency, they were converted into rubles at the rate of 60 rubles per US dollar and 70 rubles per euro. In cases where the amount of the attempted theft differs from the amount of actual losses, the first amount is indicated.
Maximum penalty (years of imprisonment) - contains information about the maximum penalty that was imposed on criminals for committing this crime.
Information about criminals-contains a description of the persons who committed the crime.
If the source does not contain the required data, then “- ”is indicated in the corresponding column of the description.
Given the huge amount of data, descriptions of all crimes are hidden under spoilers.
For an adequate interpretation of the results obtained in this article, it is necessary to take into account the following facts:
List of “ordinary " crimes committed by individuals who are not employees of the bank
1. "A resident of Izhevsk received more than eight years in a high-security penal colony for a raid on a bank," - Banks.<url>, 2018
2. "In the Krasnoyarsk Territory, employees of the Ministry of Internal Affairs of Russia detained a suspect during the day in an attempt to steal more than 2 million rubles from an ATM," - the Ministry of Internal Affairs of Russia, 2018
3. "6.5 million rubles were stolen from an ATM in Moscow," — Banks.<url>, 2017
4. "A man who tried to steal more than a million rubles from an ATM was sentenced in Udmurtia" - Russian Interior Ministry, 2017
5. "A person accused of robbing a bank branch in Primorsky Krai will appear in court," the Russian Ministry of Internal Affairs, 2017
6. "An unknown person robbed a bank in Yekaterinburg" - RIA Novosti, 2017
7. "In Udmurtia, a suspect in a robbery attack on a bank was detained," - Banks.<url>, 2017
8. "Krasnoyarsk police sent a criminal case to the court on the fact of a robbery attack on a bank branch", - The Ministry of Internal Affairs of Russia, 2017
9. "In the Kostroma region, a criminal with a hunting rifle tried to rob the mobile office of Sberbank," - Banks.<url>, 2017
10. "In the Tula region, a court issued a verdict in a criminal case on embezzlement of about 3 million rubles from commercial banks through the conclusion of fictitious loan agreements," the Prosecutor General's Office of the Russian Federation, 2018
11. The plot "Robber from the Federal Penitentiary Service":
a) "Ex-employee of the Federal Penitentiary Service of the Samara region was sentenced for bank robbery" - Volga News, 2017
b) "Victims of the Solidarity Bank robbery demand a million rubles from the offender," Volga News, 2017
12. The plot of "Robber fitness trainer":
a) "Kazan fitness trainer was given 10 years for robbery in Bystrobank", - Realnoe vremya, 2017
b) "Fast robbery: "gangster" stole almost 5 million rubles from the Kazan "Bystrobank", - Realnoe vremya, 2016
The number of crimes considered is 12.
The minimum damage caused by a crime is 624 thousand rubles.
The maximum damage caused by a crime is 8 million rubles.
The minimum penalty for a crime is 3 years in prison.
The maximum penalty for the crime is 10 years in prison.
Crimes committed by women:
Crimes committed by men:
The main crimes in this group are crimes related to the manifestation of violence, namely robberies on bank branches and physical hacking of ATMs. These crimes were usually committed by men in their 30s and 40s, and two cases deserve special attention. The first is a crime committed by a former employee of the Federal Penitentiary Service, and the second is a robbery committed by a former fitness trainer. If the first case is indicative of the fact that the crimes were committed by a person who was called upon to protect the law, then the second case partly resembles the plot of the film "Blood and Sweat: Anabolics", where the main criminal was also a fitness trainer, although he robbed not a bank, but his client.
Female offenders, unlike men, generally do not commit violent crimes. Instead, they use cunning and guile. So the only crime in this group committed by a woman is fraud in the field of lending, namely, the registration of fictitious loans using stolen personal data of individuals.
List of “ordinary " crimes committed by lone employees of the bank
1. "In Orenburg, the former manager of a bank branch was sent to a penal colony for embezzlement of 16 million rubles," - Banks.<url>, 2018
2. "An employee of one of the banks was detained by police in Balashikha, Moscow region, on suspicion of fraud," the Ministry of Internal Affairs of Russia, 2018
3. "In the city of Sharya, Kostroma region, the former director of a branch of a commercial bank is accused of fraud and embezzlement of funds", - the Ministry of Internal Affairs of Russia, 2018
4. "A businessman suspected of fraud in the amount of 150 million rubles was arrested in St. Petersburg", - Russian Interior Ministry, 2018
5. "In the Sverdlovsk region, according to police materials, a former bank employee was convicted of embezzling securities worth 20 million rubles", - the Ministry of Internal Affairs of Russia, 2017
6. "In Khabarovsk, a bank employee is suspected of embezzling three million rubles from pensioners," - Russian Interior Ministry, 2017
7. "The ex-head of Ergobank is accused of embezzlement of money," - Banks.<url>, 2017
8. "In the Novosibirsk region, a cashier who robbed a bank received 3 years of probation" - Prosecutor's Office of the Novosibirsk region, 2017
9. "A criminal case was sent to the court in Nizhny Tagil on charges of fraud against a former manager of a financial and credit institution," the Ministry of Internal Affairs of Russia, 2017
10. "A suspect in especially large-scale fraud was detained in St. Petersburg," - Russian Interior Ministry, 2017
11. "Police officers in Udmurtia detained a bank employee suspected of embezzling almost two million rubles," - Russian Interior Ministry, 2017
12. "An employee of a bank faces up to ten years for embezzlement of money from clients and financial institutions", — Banks.<url>, 2017
13. "In the Kirov region, an ex-employee of a bank stole almost 1 million rubles from depositors," — Banks.<url>, 2017
14. " The ex - manager of Sberbank is accused of stealing 1 billion rubles. from the accounts of VIP clients", - Volga News, 2017
15. "The duty officer of the collection station stole 4.2 million rubles," - Prosecutor General's Office of the Russian Federation, 2017
16. "In Khakassia, a bank cashier embezzled money and went on a trip" - Banks.<url>, 2017
17. "Deputy Chairman of the South-Western Bank of Sberbank detained in Rostov-on-Don", - TASS news agency, 2017
18. "A criminal case has been opened in the Penza Region against a cash collector who embezzled about two million rubles," the Ministry of Internal Affairs of Russia, 2017
19. "In Volgograd, a bank teller stole more than 13 million rubles and disappeared with her family," - Russian Interior Ministry, 2017
20. "In the Samara region, a criminal case was sent to the court against a bank manager accused of fraud", - the Ministry of Internal Affairs of Russia, 2017
21. "In the Republic of Crimea, police officers exposed the illegal scheme of a former bank employee," - Russian Interior Ministry, 2017
22. "GSU of the Metropolitan Police sent to the court a criminal case on an attempt to disclose information constituting a bank secret", - Ministry of Internal Affairs of Russia, 2017
The number of crimes considered is 22.
The minimum damage caused by a crime is 172 thousand rubles.
The maximum damage caused by a crime is 1 billion rubles.
The minimum penalty for a crime is 2 years in prison.
The maximum penalty for the crime is 4 years in prison.
Crimes committed by women:
Crimes committed by men:
Positions of criminals:
The following typical scenarios can be distinguished in crimes of this group:
An interesting fact is that in this group, the overwhelming majority of criminals are women, and their behavior can be divided into two archetypes:
In the list of crimes of this group, there is a case that is not related to the analyzed banking crimes, but still quite interesting. This is a case in which a bank employee "leaked" a customer database and then tried to sell it. However, he was caught red-handed.
List of “ordinary " crimes committed by groups of individuals without the participation of bank employees
1. "The Prosecutor's Office of the Kabardino-Balkar Republic approved an indictment in a criminal case on six episodes of fraud in the amount of more than 16 million rubles" — - Prosecutor General's Office of the Russian Federation, 2018
2. "A bank was robbed in Moscow in two minutes," Lenta reports.<url>, 2018
3. "Employees of the Ministry of Internal Affairs of Russia detained suspects in a robbery committed in a credit institution", - Ministry of Internal Affairs of Russia, 2018
4. "The court sent robbers to the Moscow bank office in a penal colony," - Banks.<url>, 2017
5. "Participants of bank robberies convicted in Sverdlovsk and Rostov regions" — Prosecutor General's Office of the Russian Federation, 2017
6. "Employees of the Ministry of Internal Affairs of Russia revealed a scheme of embezzlement of 500 million rubles", - Ministry of Internal Affairs of Russia, 2017
7. "In the Angara region, a sentence was passed to members of an organized group accused of robberies on financial institutions", - the Ministry of Internal Affairs of Russia, 2017
8. "Moscow found guilty of members of an organized group who stole over 98 million rubles from clients of the capital's banks," - Russian Interior Ministry, 2017
9. "Two unknown people stole 4.5 million rubles from an ATM in St. Petersburg", - Channel 5, 2017
10. "The Prosecutor's Office of the Volgograd region sent to the court a criminal case on fraud in the amount of more than 739 million rubles," - Prosecutor General's Office of the Russian Federation, 2017
11. "The case of embezzlement of more than 4 billion rubles from Otkritie Bank is divided into episodes," Kommersant, 2017
12. "Three citizens stole more than 52 million rubles from three large banks under the guise of consumer loans," — Banks.<url>, 2017
13. "In the Voronezh Region, a criminal case was sent to the court against three citizens who committed a series of bank robberies", - The Ministry of Internal Affairs of Russia, 2017
14. "A person involved in a criminal case on embezzlement of 132 million rubles from one of the capital's banks was found guilty in Moscow," the Ministry of Internal Affairs of Russia, 2017
15. "The court will consider the case of embezzlement of more than 134 million rubles from one of the capital's banks —" - Banks.<url>, 2017
16. "The case of embezzlement of 160 million rubles from banks was transferred to the court", - Banks.<url>, 2017
17. "In Chuvashia, a criminal case was sent to the court on charges of fraud", - The Ministry of Internal Affairs of Russia, 2017
18. "Members of an organized group who stole more than 98 million rubles from clients of Moscow banks will be brought to trial", - Ministry of Internal Affairs of Russia, 2017
19. "Employees of the Russian Ministry of Internal Affairs detained suspects of attempted fraud", - Ministry of Internal Affairs of Russia, 2018
The number of crimes considered is 19.
The minimum damage caused by a crime is 1 million 100 thousand rubles.
The maximum damage caused by the crime is 4.5 billion rubles.
The minimum penalty for a crime is 4.5 years in prison.
The maximum penalty for the crime is 14 years in prison.
Crimes committed by women:
Crimes committed by men:
The maximum size of a criminal group is 7 members.
If we compare the structure of crimes in this group with the structure of similar crimes committed by individuals, we can see a significant shift from violent crimes to intellectual crimes related to fraud. In addition to changes in the structure, the damage caused by crimes has also increased. The group under consideration contains:
Interesting crimes in this group include fraud committed in Chuvashia. Here, the criminals used the classic "lost wallet" wiring, during which they physically stole the victims ' bank cards and, using previously spied PIN codes, withdrew money from them at ATMs. To prevent the victim from suspecting theft, the criminals slipped a plastic blank instead of a real card.
List of "ordinary" crimes committed by groups of individuals with the participation of bank employees
The number of crimes considered is 20.
The minimum damage caused by a crime is 1 million 600 thousand rubles.
The maximum damage caused by a crime is 2 billion rubles. 100 million rubles.
The minimum penalty for a crime is 2.5 years in prison.
The maximum penalty for the crime is 12 years in prison.
Crimes committed by women:
Crimes committed by men:
The maximum size of a criminal group is 8 members.
Positions of criminals:
The main difference between crimes of this group and those previously considered is that in the vast majority of cases, the affected party is the bank, and the main method of causing damage is the issuance of deliberately non — repayable loans. In addition to credit fraud, the attackers also engaged in the theft of customers ' money committed in various ways. The cadre of criminals is quite remarkable: among them there are many middle-and senior-level managers, as well as bank owners.
The most interesting crime in this group can be considered a combination in which the attackers first gained control of the bank, and then by issuing non-repayable loans withdrew funds from it, which eventually caused damage in more than 2 billion rubles.
List of "computer" crimes committed by individuals who are not employees of the bank
1. "A suspect was detained in Izhevsk in an attempt to steal money from an ATM", - The Ministry of Internal Affairs of Russia, 2018
2. "In Khabarovsk, police officers revealed the fact of illegal turnover of payment orders in the amount of more than 900 million rubles", - the Ministry of Internal Affairs of Russia, 2018
3. "In the Republic of Mari El, the police stopped the theft of money from bank cards from citizens", - The Ministry of Internal Affairs of Russia, 2017
4. "Rosgvardiya employees prevented theft of a large amount of cash from an ATM in Budyonnovsk" - Rosgvardiya, 2018
5. "A Saratov hacker stole money through a bank's phishing site," SarBC, 2018
6. The story " Theft from Texbank”:
a) "After a failure in the operating system, 27 million rubles disappeared from the Moscow bank", - Kommersant, 2017
b) "An actor from St. Petersburg stole 27 million rubles from Texbank", - Channel 5, 2017
The number of crimes considered is 6.
The minimum damage caused by a crime is 120 thousand rubles.
The maximum damage caused by the crime is 27 million rubles.
Minimum penalty for a crime-no data available.
Maximum penalty for a crime-no data available.
Crimes committed by women are not recorded.
Crimes committed by men:
"Computer" crimes committed by lone individuals are mainly directed against bank customers and consist in stealing victims ' money through the Client-Bank Internet systems and performing unauthorized operations on their payment cards.
In addition to attacks on customers, lone hackers stole money from ATMs, and just as in the case of Texbank, they tried to steal money by hacking into the bank's IT systems.
It is noteworthy that among the criminals there is not a single representative of the fair sex.
List of "computer" crimes committed by a group of individuals that included bank employees
1. "A case on fraud in the field of computer information was submitted to the court in the Central District", - The Ministry of Internal Affairs of Russia, 2017
2. "Hackers from Moscow face 10 years for stealing 20 million rubles from a bank," the source said.<url>, 2015
The number of crimes considered is 2.
The minimum damage caused by a crime is 6 million rubles.
The maximum damage caused by a crime is 20 million rubles.
Minimum penalty for a crime-no data available.
Maximum penalty for a crime-no data available.
Crimes committed by women:
Crimes committed by men:
The maximum size of a criminal group is 10 members.
Positions of criminals:
Types of crimes — unauthorized transfers (debits) from bank clients ' accounts.
"Computer" crimes committed with the participation of bank employees are quite rare. There are only two of them in our sample. And all these are actions of criminal groups. There are no" computer " crimes committed by lone individuals at all.
In all the crimes of this group, the attackers tried to steal customer funds. Both men and women were involved in the crimes. Also, the fact that there are no banking IT specialists among the criminals is striking.
List of "computer" crimes committed by groups of individuals without the participation of bank employees
1. "In Krasnoyarsk, the police detained suspects in the theft of 15 million rubles from ATMs," — Banks.<url>, 2018
2. "A fraudster tried to steal 1.4 billion rubles from a Russian bank," Kommersant, 2018
3. "Suspects in a series of ATM thefts worth more than 6 million rubles were detained in Dagestan" - Russian Interior Ministry, 2017
4. "The verdict against a resident of the Moscow region who was found guilty of stealing more than 600 thousand rubles from bank accounts of residents of Belgorod has entered into legal force," Belgorod Regional Court, 2017
5. "Employees of the Department" K "of the Ministry of Internal Affairs of Russia together with operatives of the department" K "of the Ministry of Internal Affairs of the Republic of Tatarstan stopped the activities of persons who carried out embezzlement of money from bank accounts of citizens", - Ministry of Internal Affairs of Russia, 2017
6. "Employees of the Ministry of Internal Affairs of Russia detained members of the group suspected of stealing money from ATMs in Yakutsk", - Ministry of Internal Affairs of Russia, 2017
7. "Department" K "of the Ministry of Internal Affairs of Russia suppressed the activities of an organized group suspected of embezzling funds from bank accounts using a Trojan program", - Ministry of Internal Affairs of Russia, 2017
8. "In Bryansk, police officers and Rosgvardiya detained suspects in an attempt to steal money from ATMs", - the Ministry of Internal Affairs of Russia, 2017
9. "In Kuban, the police detained suspects of embezzlement of funds from ATMs", - the Ministry of Internal Affairs of Russia, 2017
10. "Hackers from Gorny Altai stole tens of millions from the bank" - <url>, 2015
11. "Hackers stole a billion rubles from four banks using a bot" — <url>, 2016
12. "ABS didn't work" - Kommersant, 2016
13. "Hackers stole almost 2 billion rubles from banks using 'letters from the Central Bank'", — RBC, 2016
14. "The investigative bodies of the Ministry of Internal Affairs of Russia sent to the court a case on embezzlement of funds from bank cards of citizens", - The Ministry of Internal Affairs of Russia, 2018
15. "The Prosecutor's Office of the Republic of Bashkortostan sent a criminal case to the court on the fact of theft by hackers of more than 8 million rubles," - Prosecutor General's Office of the Russian Federation, 2018
16. "Hackers" accused of embezzling more than 2.6 million rubles from bank accounts in various regions of the country will appear in court in the Sverdlovsk region" — - Prosecutor General's Office of the Russian Federation, 2016
17. "The court recovered 470 million rubles from the processing company UCS", - Vedomosti, 2016
18. "Five residents of Buryatia will stand trial for embezzlement of money from bank accounts of Trans-Baikal residents", - The Ministry of Internal Affairs of Russia, 2018
19. "The Investigation Department has completed the investigation of the criminal case on illegal access to computer information", - Ministry of Internal Affairs of Russia, 2017
20. "In the Volgograd region, employees of the K department detained a suspect in embezzlement of money from citizens 'accounts", - The Ministry of Internal Affairs of Russia, 2018
21. "TwoBee Financial Campaign", — Securelist.ru, 2017
22. The story " Theft from the Russian International Bank”:
a) "Hackers stole more than half a billion rubles from the correspondent account in the Central Bank", - Interfax, 2016
b) "Russian International Bank named the amount of funds stolen by hackers", - RBC, 2016
c) "Hackers stole almost 2 billion rubles from banks using "letters from the Central Bank", - RBC, 2016
23. The story "Theft from Metallinvestbank":
a) " Hackers withdrew 677 million rubles. from Metallinvestbank's accounts", - RBC, 2016
b) "Metallinvestbank lost 200 million rubles due to a hacker attack", - RIA Novosti, 2016
c) "Metallinvestbank press release on theft" — - Metalinvestbank, 2016
d) "Hacker-style robbery", - Kommersant, 2017
24. The plot "Theft from the bank "Globex"":
a) "Hackers came running to SWIFT", - Kommersant, 2017
b) "Hackers came to Globex", - Kommersant, 2017
c) "Hackers stole $1 million from a subsidiary bank of VEB", - Vedomosti, 2017
25. The plot "Theft from the PIR Bank":
a) "A feast for hackers", - Kommersant, 2018
b) " How do you like this, Carbanak?", - Group-IB, 2018
26. The plot "A group of 14 hackers robbing banks":
a) "The hacker's remorse program worked", - Kommersant, 2017
b) "A boxer from Ukraine led a group of hackers who stole 1 billion rubles from banks," - <url>, 2016
c) "The court breaks into a hacker network," - Kommersant, 2017
27. The story "Hacker group Lurk":
a) "Lurk Banking Trojan: specially designed for Russia", — Securelist.ru, 2016
b) "Employees of the Ministry of Internal Affairs of Russia and the Federal Security Service of Russia detained Internet hackers", - The Ministry of Internal Affairs of Russia, 2016
c) "Hunting for Lurk", — Securelist.ru, 2016
28. The plot "Hackers of Popelsha":
a) "Cyber fraudsters convicted in Moscow for stealing money through online bank accounts", - Interfax, 2018
b) "The court found members of the group guilty of stealing 12.5 million rubles from 7,000 Russian bank accounts", - Group-IB, 2018
The number of crimes considered is 28.
The minimum damage caused by a crime is 660 thousand rubles.
The maximum damage caused by the crime is 2 billion rubles.
The minimum penalty for a crime is 5 years in prison.
The maximum penalty for the crime is 8 years in prison.
Crimes committed by women:
Crimes committed by men:
The maximum size of a criminal group is 50 members.
Crimes of this group are classic hacker crimes, among which the following typical scenarios can be distinguished::
The type of crimes and the damage they cause depends to a greater extent on the qualifications and to a lesser extent on the number of groups that committed them.
For example, there are crimes committed by a group of 5 participants, as a result of which 3 million rubles were stolen, and there are crimes committed by 2 bandits, but caused damage of 60 million rubles. At the same time, the maximum damage was caused by the actions of professional criminal groups with dozens of participants. These gangs can safely be called "hacker enterprises", since they committed so many crimes that they even posted job vacancies to fulfill all their plans.
Among all the crimes considered, we can single out the actions of a criminal group consisting of two women and their male accomplice who robbed Sberbank customers. Of interest is the fact that the criminals were not particularly gifted hackers who developed clever Trojans or used 0-day exploits, instead they rummaged in the trash cans next to Sberbank ATMs, found checks containing bank account details, and then made unauthorized transfers using regular Sberbank funds.Online".
Up to this point, we have analyzed crimes by groups. Now we will conduct a generalized analysis of all crimes in the sample.
Note. When calculating damages from crimes involving several types of illegal actions (for example, fraud in the field of lending and unauthorized transfers from bank accounts), the total damage is evenly distributed among all types.
In terms of the total number of crimes, the TOP 3 types of crimes will be:
In terms of the total amount of damage, the TOP 3 types of crimes will be:
The most dangerous type of crime is recognized as "fraud in the field of lending", since it occupies the first place in terms of damage and the second in terms of the number of crimes committed.
The crime that caused the maximum damage is securities fraud, which caused losses of 4.5 billion rubles to Otkritie Bank.
The crime for which the maximum penalty is imposed is robberies on bank branches in the Sverdlovsk region, for which one of the bandits was imprisoned for 14 years.
The maximum amount of cash that criminals stole is 780 million rubles (stolen from the cash register by the former owner of Ergobank).
The maximum amount of cash stolen by criminals who are not employees of the bank is 23 million rubles (assault on a branch of a Moscow bank).
The maximum amount of money stolen by hackers due to hacking into the bank's IT systems is quite difficult to reliably determine, since the size of the theft attempt and the size of the actual stolen money are always different. The maximum theft attempt is 1 billion rubles. 400 million rubles (attempted theft from the bank "Ring of the Urals"). There is no reliable information about the amount of money actually stolen.
Positions of criminals who are employees (or owners) of the bank:
It is definitely impossible to answer the question of which employee is the most dangerous for the bank. In this case, the following patterns can be distinguished:
Crimes committed by women:
Crimes committed by men:
The age of the perpetrators is from 19 to 62 years.
The maximum size of criminal groups is 50 participants.
The analysis of crimes revealed the following patterns:

This article presents a basic model of threats to the information security of bank wire transfers made through the payment system of the Bank of Russia.
The threats presented here are valid for almost any bank in the Russian Federation, as well as for any other organizations that use thick clients with cryptographic payment confirmation for settlements.
This threat model is designed to ensure practical security and generate internal bank documentation in accordance with the requirements of Bank of Russia Regulations No. 552-P of August 24, 2016 and No. 382-P of June 9, 2012.
One of the most successful ways to simulate computer attacks today is Kill chain. This method represents a computer attack as a sequence of steps performed by attackers to achieve their goals.
Most of the stages are described in the MITRE ATT&CK Matrix, but there is no decoding of the final actions — "Actions" (the last stage of the Kill chain), for which the attackers carried out the attack and which, in fact, are stealing money from the bank. Another problem with using the classic Kill chain for threat modeling is the lack of a description of availability-related threats.
This threat model is designed to compensate for these shortcomings. To do this, it will formally consist of two parts:
The main requirements for the created threat model were:
To achieve these goals, the model was built on the basis of the "threat tree" methodology, which was slightly improved:
The procedure for updating threats described in the model should be carried out in accordance with the organization's internal documents. In the absence of such documents, they can be developed on the basis of the methods discussed in the previous article of the study.
This threat model uses the following design rules:
The scope of this threat model applies to the process of non-cash money transfers through the Bank of Russia payment system.
Architecture
The model's coverage area includes the following information infrastructure::
Here:
"Bank of Russia Payment System Section" means a section of information infrastructure that is subject to the requirements of Bank of Russia Regulation No. 552-P of August 24, 2016. The criterion for classifying an information infrastructure as a BR substation site is processing of electronic messages in the UFEBS format at information infrastructure facilities.
"Electronic message transmission channel" includes the bank's communication channel with the Central Bank of the Russian Federation, built through a specialized telecom operator or modem connection, as well as an electronic message exchange mechanism that operates using a courier and alienable machine data carriers (OMNI).
The list of premises that fall within the threat model's coverage area is determined by the criterion of whether they contain information infrastructure facilities that are involved in money transfers.
Model Restrictions
This threat model applies only to the option of organizing a payment infrastructure with the KBR APM, which combines encryption and electronic signature functions, and does not consider the case of using the KBR-N APM, where the electronic signature is performed "on the ABS side".
Decomposition
Y1. Termination of the non-cash transfer system.
Y2. Theft of funds during the operation of the non-cash transfer system.
Explanations
Potential damage from the implementation of this threat can be estimated based on the following assumptions:
In general, the maximum allowable delay in payment execution can be considered one flight during a business day. A further increase in the delay will lead to more and more damage to the bank.
When decomposing this threat, the following documents were taken into account:
Decomposition
Y1. 1. Problems with the equipment or data carriers used in making transfers:
Y1. 1. 1. Failures and failures.
Y1. 1. 2. Theft.
Y1. 1. 3. Loss.
Y1. 2. Destruction of programs or data necessary for making transfers.
Y1. 3. Malicious actors perform denial-of-service (DoS, DDoS) attacks on technical means and communication channels used for making transfers.
Y1. 4. Inability to exchange electronic messages with the payment system of the Central Bank of the Russian Federation (S):
Y1.4.1.<...>, carried out through network connections:
Y1. 4. 1. 1. Inoperable communication channels with the Central Bank of the Russian Federation (S):
Y1. 4. 1. 1. 1. < ... > provided by a specialized telecom operator.
Y1.4.1.1.2. <...>, organized as a modem connection.
U1. 4. 1. 2. Termination of information used to authenticate a network connection with the Central Bank of the Russian Federation.
Y1. 4. 2.<...>, carried out by courier on alienated machine information carriers (OMNI):
Y1. 4. 2. 1. Lack of properly executed documents:
Y1.4.2.1.1 <...>, confirming the courier's credentials.
Y1.4.2.1.2 <...>, accompanying payments on OMNI.
Y1. 5. Termination of cryptographic keys used to protect electronic messages:
Y1. 5. 1. Expiration of cryptographic keys.
Y1. 5. 2. Compromise of cryptographic keys.
U1. 5. 3. Provocation by intruders of the Central Bank of the Russian Federation certification center to block the operation of the bank's cryptographic keys.
Y1. 6. Absence at the workplace of persons involved in making non-cash payments.
Y1. 7. Use of outdated versions of the software used for making non-cash transfers.
Y1. 8. The occurrence of conditions in the premises under which it is impossible for the normal functioning of technical means, communication channels and personnel involved in transfers:
Y1. 8. 1. Lack of power supply.
Y1. 8. 2. Significant violations of the temperature regime (overheating, hypothermia).
Y1. 8. 3. Fire.
Y1. 8. 4. Flooding of the room.
Y1. 8. 5. Collapse or threat of collapse of premises.
Y1. 8. 6. Armed attack.
Y1. 8. 7. Radioactive or chemical contamination.
Y1. 8. 8. Strong electromagnetic interference.
Y1. 8. 9. Epidemics.
Y1. 9. Administrative termination of access to buildings or premises where the information infrastructure used for making payments is located:
U1. 9. 1. Blocking access by the authorities:
U1. 9. 1. 1. Conducting searches or other operational investigative measures.
Y1. 9. 1. 2. Holding cultural events, religious holidays, etc.
Y1. 9. 2. Blocking access by the owner:
Y1. 9. 2. 1. Conflict of economic entities.
У1.10. The effect of force majeure circumstances (natural disasters, catastrophes, mass riots, terrorist attacks, military operations, zombie apocalypse,...).
Explanations
Theft of funds during the operation of a non-cash transfer system is the theft of non-cash funds with their subsequent or simultaneous withdrawal from the victim bank.
Theft of non-cash funds is an unauthorized change in the customer's or bank's account balance. These changes may occur as a result of:
We will call an abnormal change in the account balance actions that are not regulated by the bank's internal documentation, as a result of which an unauthorized decrease or increase in the bank account balance occurred. Examples of such actions can be: making a fictitious bank transaction, directly changing the balance in a storage location (for example, in a database), and other actions.
An abnormal change in the account balance is usually accompanied by regular operations to spend stolen funds. Such operations include:
An unauthorized transfer of funds is a transfer made without the consent of persons who have the right to dispose of funds and, as a rule, made by executing a forged order for the transfer of funds by the bank.
Fake money transfer orders can be generated either through the fault of customers or the bank. In this threat model, only threats that are within the bank's area of responsibility will be considered. In this model, only payment orders will be considered as money transfer orders.
In general, it can be assumed that the bank's processing of intrabank transfers is a special case of processing interbank transfers, so to preserve the compactness of the model, only interbank transfers will be considered in the future.
Theft of non-cash funds can be performed both in the execution of outgoing payment orders and in the execution of incoming payment orders. At the same time, we will refer to the outgoing payment order as a payment order sent by the bank to the Bank of Russia payment system, and we will refer to the incoming payment order as a payment order received by the bank from the Bank of Russia payment system.
Decomposition
Y2. 1. Execution of fake outgoing payment orders by the bank.
Y2. 2. Execution of fake incoming payment orders by the bank.
Y2. 3. Abnormal changes in account balances.
Explanations
The main reason why a bank can execute a fake payment order is due to its introduction by intruders into the business process of payment processing.
Decomposition
Y2. 1. 1. Introduction of a fake outgoing payment order into the business process of payment processing by intruders.
Explanations
Decomposition of this threat will be performed by elements of the information infrastructure in which a fake payment order may be introduced.
Decomposition
Y2. 1. 1. 1.<...> in the "Bank Operator" element.
Y2. 1. 1. 2.<...> in the "RBS Server" element.
Y2. 1. 1. 3.<...> in the "DBO-ABS Integration Module" element.
Y2. 1. 1. 4.<...> in the " ABS " element.
Y2. 1. 1. 5.<...> in the "ABS-CBD Integration Module" element.
Y2.1.1.6 .<...> in the "APM KBR" element.
Y2.1.1.7 .<...> in the "CBD-UTA Integration Module" element.
Y2. 1. 1. 8.<...> in the "UTA" element.
Y2. 1. 1. 9.<...> in the "Email transmission channel" element.
Explanations
When accepting a paper payment order from the client, the operator enters an electronic document based on it in the ABS. The vast majority of modern ABS systems are based on the client-server architecture, which makes it possible to analyze this threat based on a typical threat model of client-server information systems.
Decomposition
Y2. 1. 1.1. 1.The bank's operator accepted a forged paper payment order from an attacker who introduced himself as a bank customer.
U2. 1. 1. 1. 2.A fake electronic payment order was entered in the ABS on behalf of the bank's operator.
Y2.1.1.1.2.1. The operator acted with malicious intent or made an unintentional mistake.
Y2.1.1.1.2.2. Malefactors acted on behalf of the operator:
Y2.1.1.1.2.2.1. Link: "Standard threat model. An information system based on the client-server architecture. Y1. Performing unauthorized actions by intruders on behalf of a legitimate user".
Note. Typical threat models will be discussed in the following articles.
Decomposition
Y2. 1. 1. 2. 1. The RBS server accepted a duly certified payment order on behalf of the client, but it was drawn up by intruders without the client's consent:
Y2.1.1.2.1.1. Link: "Standard threat model. An information system based on the client-server architecture. Y1. Performing unauthorized actions by intruders on behalf of a legitimate user".
Y2. 1. 1. 2. 2. Attackers introduced a fake payment order into the RBS server:
Y2.1.1.2.2.1. Link: "Standard threat model. An information system based on the client-server architecture. Y2. Unauthorized modification of protected information during its processing by the server part of the information system".
Decomposition
Y2. 1. 1. 3. 1. Link: "Standard threat model. Integration module. Y1. Introduction of fake information by intruders through the integration module".
Decomposition
Y2. 1. 1. 4. 1. Link: "Standard threat model. An information system based on the client-server architecture. Y2. Unauthorized modification of protected information during its processing by the server part of the information system".
Decomposition
Y2. 1. 1. 5. 1. Link: "Standard threat model. Integration module. Y1. Introduction of fake information by intruders through the integration module".
Explanations
The main function of the KBR automated control system in terms of information security is cryptographic protection of electronic messages exchanged by the bank with the payment system of the Bank of Russia. All outgoing payment documents are encrypted using the Bank of Russia's public keys and the bank's private electronic signature keys.
Decomposition (S):
Y2. 1. 1. 6. 1. Encryption of a fake payment order using the Bank of Russia's public keys:
Y2.1.1.6.1.1. Link: "Standard threat model. Cryptographic information protection system. Y2. Encryption of forged data on behalf of a legitimate sender".
Y2. 1. 1. 6. 2. Electronic signature of a forged payment order on the bank's private keys:
Y2.1.1.6.2.1. Link: "Standard threat model. Cryptographic information protection system. Y4. Creating an electronic signature of a legitimate signatory under forged data".
Explanations
In accordance with the technological process of payment processing, electronic messages on the KBR — CBR AWP section are signed with an electronic signature and encrypted. Accordingly, the introduction of a fake payment order at this stage is possible only if the attackers managed to bypass the standard cryptographic protection procedure to encrypt and sign the fake payment order.
Decomposition (S):
Y2. 1. 1. 7. 1. Link: "Current threat model. Y2. 1. 1. 6.<...> in the "APM KBR" element.
Y2. 1. 1. 7. 2. Link: "Typical threat model. Integration module. Y1. Introduction of fake information by intruders through the integration module".
Explanations
UTA is essentially an information robot that exchanges cryptographically secure electronic messages with the Central Bank of the Russian Federation. Threats to the information security of this element correspond to the threats of integration modules.
Decomposition (S):
Y2. 1. 1. 8. 1. Link: "Current threat model. Y2. 1. 1. 6.<...> in the "APM KBR" element.
Y2. 1. 1. 8. 2. Link: "Typical threat model. Integration module. Y1. Introduction of fake information by intruders through the integration module".
Decomposition (S):
Y2. 1. 1. 9. 1. Link: "Current threat model. Y2. 1. 1. 6.<...> in the "APM KBR" element.
U2. 1. 1. 9. 2. Transfer of a fake payment order to the Bank of Russia by intruders:
Y2.1.1.9.2.1. <...> during a communication session with the Bank of Russia established on behalf of the bank.
Y2.1.1.9.2.2. <...> with the help of an OMNI courier.
Decomposition
Y2. 2. 1. Introduction of a fake incoming payment order into the business process of payment processing by intruders.
Explanations
Payment orders are encrypted and signed with an electronic signature in the KBR — Bank of Russia Automated Payment System section. In general, payment orders are not cryptographically secure in the KBR — ABS AWP section.
Payment orders received by the bank are encrypted on the bank's public keys and signed with the Bank of Russia's private keys. The key cryptographic protection system is based on the private public key infrastructure (private PKI), implemented on the basis of the SCAD Signature SCSI and includes: The certification center of the Bank of Russia and its users is credit organizations. All participants in the public key infrastructure trust certificates issued by the Central Bank of the Russian Federation certification center.
Thus, in order to implement a fake incoming payment order, attackers need to compromise the recipient bank's public encryption keys and electronic signature keys, whose certificates are trusted by the recipient bank.
Decomposition of this threat will be performed based on infrastructure elements where fake incoming payment orders may be introduced.
Decomposition
Y2. 2. 1. 1.<...> in the " ABS " element.
Y2. 2. 1. 2.<...> in the "ABS-CBD Integration Module" element.
Y2.2.1.3 .<...> in the "APM KBR" element.
Y2.2.1.4 .<...> in the "CBD-UTA Integration Module" element.
Y2. 2. 1. 5.<...> in the "UTA" element.
Y2. 2. 1. 6.<...> in the "Email transmission channel" element.
Decomposition
Y2. 2. 1. 1. 1. Link: "Standard threat model. An information system based on the client-server architecture. Y2. Unauthorized modification of protected information during its processing by the server part of the information system".
Decomposition
Y2. 2. 1. 2. 1. Link: "Standard threat model. Integration module. Y1. Introduction of fake information by intruders through the integration module".
Explanations
When processing incoming payment documents, the AWP KBR is the last line of defense, whose task is to decrypt and verify the integrity of incoming cryptographically protected electronic messages. The protection of this stage will be neutralized if the Automated Control System of the KBR, after receiving a fake payment order at the entrance, informs that the electronic signature under it is correct.
Decomposition
Y2. 2. 1. 3. 1. Successful verification of the electronic signature of a fake incoming payment order:
Y2.2.1.3.1.1 Link: "Standard threat model. Cryptographic information protection system. Y5. Getting a positive result of checking the electronic signature of forged data".
Explanations
Starting from this element and continuing to the Bank of Russia payment system, attackers lose the possibility of unauthorized access to the cryptographic information protection system (ICSI). Therefore, all data coming from the Integration Module to the KBR AWP must be correctly encrypted and signed. For encryption, attackers must use the bank's public keys, and for electronic signatures, private keys that the bank trusts with certificates.
Decomposition (S):
Y2. 2. 1. 4. 1. Neutralizing the cryptographic protection of incoming electronic messages (S):
Y2.2.1.4.1.1. Encryption of a fake payment order using the bank's public keys:
Y2.2.1.4.1.1.1. Link: "Standard model threats. Cryptographic information protection system. Y2. Encryption of forged data on behalf of a legitimate sender".
Y2.2.1.4.1.2. Electronic signature of a fake payment order based on private keys trusted by the bank:
Y2.2.1.4.1.2.1. Link: "Standard threat model. Cryptographic information protection system. Y4. Creating an electronic signature of a legitimate signer under forged data".
Y2. 2. 1. 4. 2. Link: "Standard threat model. Integration module. Y1. Introduction of fake information by intruders through the integration module".
Decomposition:
Y2. 2. 1. 5. 1. Link: "Current threat model. Y2. 2. 1. 4.<...> in the "CBD-UTA Integration Module" element.
Decomposition (S):
Y2. 2. 1. 6. 1. Link: "Current threat model.Y2. 2. 1. 4. 1. Neutralizing the cryptographic protection of incoming electronic messages".
Y2. 2. 1. 6. 2. Receiving a fake payment order from the Central Bank of the Russian Federation:
Y2.2.1.6.2.1. <...> during a communication session with the Bank of Russia established by the Bank of on behalf of the bank.
Y2.2.1.6.2.2. <...> with the help of an OMNI courier.
The object of protection is data transmitted over a network connection that operates in data transmission networks built on the basis of the TCP/IP stack.
Architecture
Description of the architecture elements:
Decomposition
Y1. Unauthorized access to the transmitted data.
Y2. Unauthorized modification of the transmitted data.
Y3. Violation of the authorship of the transmitted data.
Decomposition
Y1. 1. < ... > performed on end or intermediate nodes:
Y1. 1. 1. < ... > by reading data while they are in the node's storage devices:
Y1.1.1.1. <...> in RAM.
Explanation of Y1. 1. 1. 1.
For example, during data processing by the node's network stack.
У1.1.1.2. <...> in non-volatile memory.
Explanation of Y1. 1. 1. 2.
For example, when storing transmitted data in a cache, temporary files, or paging files.
Y1. 2. < ... > performed on third-party nodes of the data transmission network:
Y1. 2. 1. < ... > by capturing all packets that reach the node's network interface:
Explanation of Y1. 2. 1.
All packets are captured by switching the network card to promiscuous mode (promiscuous mode for wired adapters or monitor mode for wi-fi adapters).
Y1. 2. 2. < ... > by performing man-in-the-middle (MiTM) attacks, but without modifying the transmitted data (not counting network protocol overhead).
Y1. 2. 2. 1. Link: "Standard threat model. Network connection. Y2. Unauthorized modification of the transmitted data".
U1. 3.<...>, carried out due to information leakage through technical channels (TCUI) from physical nodes or communication lines.
U1. 4.<...>, carried out by installing special technical means (STS) at the end or intermediate nodes intended for secret information retrieval.
Decomposition
Y2. 1. < ... > performed on end or intermediate nodes:
Y2. 1. 1. < ... > by reading and modifying data while it is in the storage devices of nodes:
Y2.1.1.1. <...> in RAM:
Y2. 1. 1.2.<...> in non-volatile memory:
Y2. 2. < ... > performed on third-party nodes of the data transmission network:
Y2. 2. 1. < ... > by performing man-in-the-middle (MiTM) attacks and redirecting traffic to the attackers 'node:
Y2.2.1.1. Physically connecting the attackers' equipment when the network connection is broken.
Y2. 2. 1. 2. Attacks on network protocols:
Y2.2.1.2.1. <...> management of virtual local area networks (VLANs):
Y2.2.1.2.1.1. VLAN hopping.
Y2.2.1.2.1.2. Unauthorized modification of VLAN settings on switches or routers.
У2.2.1.2.2. <...> traffic routing:
Y2.2.1.2.2.1. Unauthorized modification of static routing tables for routers.
Y2.2.1.2.2.2. Attackers announce fake routes via dynamic routing protocols.
Y2.2.1.2.3. <...> Automatic configuration:
Y2.2.1.2.3.1. Rogue DHCP.
У2.2.1.2.3.2. Rogue WPAD.
Y2.2.1.2.4. <...> addressing and name resolution:
Y2.2.1.2.4.1. ARP spoofing.
У2.2.1.2.4.2. DNS spoofing.
Y2.2.1.2.4.3. Making unauthorized changes to local hostname files (hosts, lmhosts, etc.)
Decomposition
Y3. 1. Neutralizing the mechanisms for determining the authorship of information by specifying false information about the author or data source:
Y3. 1. 1. Changing the information about the author contained in the transmitted information.
Y3. 1. 1. 1. Neutralization of cryptographic protection of integrity and authorship of transmitted data:
Y3. 1. 1. 1. 1. Reference: "Standard threat model. Cryptographic information protection system.
Y4. Creation of an electronic signature of a legitimate signatory under forged data".
Y3. 1. 1. 2. Neutralization of copyright protection of transmitted data, implemented using one-time confirmation codes:
Y3. 1. 1. 2. 1. SIM swap.
Y3. 1. 2. Changing information about the source of transmitted information:
Y3. 1. 2. 1. IP spoofing.
У3.1.2.2. MAC spoofing.
The object of protection is an information system built on the basis of the client-server architecture.
Architecture
Description of the architecture elements:
Limitations
When modeling an object, the following restrictions are set::
Decomposition
Y1. Attackers perform unauthorized actions on behalf of a legitimate user.
Y2. Unauthorized modification of protected information during its processing by the server part of the information system.
Explanations
Usually, in information systems, actions are associated with the user who performed them using:
In relation to the work session, this threat can be decomposed into:
A user session can be initiated:
At this stage, the intermediate decomposition of this threat will look like this:
Y1. 1. Unauthorized actions were performed within the user's session:
Y1. 1. 1.<...>, installed by the attacked user.
Y1. 1. 2. < ... > installed by intruders.
Y1. 2. Unauthorized actions were performed outside the user's session.
From the point of view of information infrastructure objects that can be affected by intruders, the decomposition of intermediate threats will look like this::
Decomposition
Y1. 1. Unauthorized actions were performed within the user's session:
Y1. 1. 1.<...>, installed by the attacked user:
Y1. 1. 1. 1. Attackers independently operated from the Client:
Y1. 1. 1. 1. 1 Attackers used standard access tools of the information system:
Y1.1.1.1.1.1. The attackers used the Client's physical I / O facilities (keyboard, mouse, monitor, or touch screen). mobile device):
Y1.1.1.1.1.1.1. The attackers operated during periods of time when the session is active, I / O facilities are available, and the user is not in place.
Y1.1.1.1.1.2. Attackers used remote administration tools (either standard or provided by malicious code) to manage the Client:
Y1.1.1.1.1.2.1. The attackers operated during periods of time when the session is active, I / O tools are available, and the user is unable to use them. out of place.
Y1.1.1.1.1.2.2. The attackers used remote administration tools that are invisible to the attacked user.
Y1. 1. 1. 2. Attackers substituted data in the network connection between the Client and Server, modifying it so that it was perceived as the actions of a legitimate user:
Y1. 1.1.2. 1.Link: "Typical threat model. Network connection. Y2. Unauthorized modification of the transmitted data".
Y1. 1. 1. 3. Attackers forced the user to perform their specified actions using social engineering methods.
Y1. 1. 2 < ... > installed by the attackers:
Y1. 1. 2. 1. The attackers acted from the Client (S):
Y1. 1. 2. 1. 1. The attackers neutralized the access control system of the information system:
Y1.1.2.1.1.1. Link: "Typical threat model. Access control system. Y1. Unauthorized establishment of a work session on behalf of a legitimate user".
Y1. 1. 2. 1. 2. The attackers used the standard access tools of the information system
Y1. 1. 2. 2. The attackers operated from other nodes of the data transmission network from which a network connection can be established with the Server (S):
Y1. 1. 2. 2. 1. The attackers neutralized the differentiation system Information system access number:
U1.1.2.2.1.1. Link: "Standard threat model. Access control system. Y1. Unauthorized establishment of a work session on behalf of a legitimate user".
Y1. 1. 2. 2. 2. The attackers used non-standard means of accessing the information system.
Explanation of Y1. 1. 2. 2. 2.
Attackers could install a standard client of the information system on a third-party node, or they could use non-standard software that implements standard exchange protocols between the Client and the Server.
Y1. 2 Unauthorized actions were performed outside the user's session.
Y1. 2. 1 Attackers performed unauthorized actions, and then made unauthorized changes to the logs of the information system or special attributes of data objects, indicating that the actions performed by them were performed by a legitimate user.
Decomposition
Y2. 1. Attackers modify the protected information using standard information system tools and do this on behalf of a legitimate user.
Y2. 1. 1. Link: "Standard threat model. An information system based on the client-server architecture. Y1. Performing unauthorized actions by intruders on behalf of a legitimate user".
Y2. 2. Attackers modify protected information by using data access mechanisms that are not provided for in the normal mode of operation of the information system.
Y2. 2. 1. Attackers modify files containing protected information:
Y2.2.1.1. <...>, using the file management mechanisms provided by the operating system.
Y2.2.1.2. <...> by provoking the recovery of files from an unauthorized modified backup.
Y2. 2. 2. Attackers modify the protected information stored in the database (S):
Y2. 2. 2. 1. Attackers neutralize the DBMS access control system:
Y2. 2. 2. 1. 1. Link: "Standard threat model. Access control system. Y1. Unauthorized establishment of a work session on behalf of a legitimate user".
Y2. 2. 2. 2. Attackers modify information using standard DBMS interfaces to access data.
Y2. 3. Attackers modify the protected information by unauthorized modification of the algorithms of the software processing it.
Y2. 3. 1. The source code of the software is modified.
Y2.3. 1.The machine code of the software is modified.
Y2. 4. Attackers modify protected information by exploiting vulnerabilities in the information system software.
Y2. 5. Attackers modify protected information when it is transmitted between components of the back-end of an information system (for example, a database server and an application server):
Y2. 5. 1. Reference: "Typical threat model. Network connection. Y2. Unauthorized modification of the transmitted data".
The security object for which this threat model is applied corresponds to the security object of the threat model: "Typical Threat Model. An information system based on the client-server architecture."
In this threat model, a user access control system is understood as an information system component that implements the following functions:
Decomposition
Y1. Unauthorized establishment of a work session on behalf of a legitimate user.
Y2. Unauthorized elevation of user privileges in the information system.
Explanations
The breakdown of this threat will generally depend on the type of user identification and authentication systems used.
This model will only consider a user identification and authentication system that uses a text-based username and password. At the same time, we assume that the user's login is publicly available information known to attackers.
Decomposition
Y1. 1. < ... > by compromising credentials:
Y1.1. 1. Attackers compromised the user's credentials while storing them.
Explanation of Y1. 1. 1.
For example, credentials could be written on a sticker attached to the monitor.
Y1. 1. 2. The user accidentally or maliciously transferred access details to intruders.
Y1. 1. 2. 1. The user spoke the credentials out loud when entering them.
Y1. 1. 2. 2. The user intentionally passed their credentials:
Y1.1.2.2.1. <...> to your work colleagues.
Explanation of Y1. 1. 2. 2. 1.
For example, so that they can replace it during the period of illness.
У1.1.2.2.2. <...> contractors of the employer performing work on information infrastructure objects.
У1.1.2.2.3. <...> to third parties.
Explanation of Y1. 1. 2. 2. 3.
One, but not the only option for implementing this threat is the use of social engineering methods by attackers.
Y1. 1. 3. Attackers picked up credentials by brute force:
Y1.1.3.1. <...> using standard access mechanisms.
Y1.1.3.2. <...> by previously intercepted codes (for example, password hashes) for storing credentials.
Y1. 1. 4. Attackers used malicious code to intercept user credentials.
Y1. 1. 5. Attackers extracted credentials from the network connection between the Client and Server:
Y1. 1.5. 1.Link: "Typical threat model. Network connection. Y1. Unauthorized access to the transmitted data".
Y1. 1. 6. Attackers extracted credentials from the records of monitoring systems:
Y1. 1. 6. 1.<...> video surveillance systems (if keystrokes on the keyboard were recorded during operation).
У1.1.6.2. <...> systems for monitoring employee actions at the computer
Explanation of Y1. 1. 6. 2.
An example of such a system is StuffCop.
Y1. 1. 7. Attackers compromised the user's credentials due to shortcomings in the process of transmitting them.
Explanation of Y1. 1. 7.
For example, transmitting passwords in clear text via email.
Y1. 1. 8. Attackers found out the credentials by monitoring the user's session using remote administration systems.
Y1. 1. 9. Attackers extracted credentials as a result of their leakage through technical channels (TCUI):
Y1. 1. 9. 1. Attackers spied on the user entering credentials from the keyboard:
Y1. 1. 9. 1. 1 Attackers were located in close proximity to the user and saw the user entering credentials data with your own eyes.
Explanation Y1. 1. 9. 1. 1
Such cases can include actions of colleagues at work or when the user's keyboard is visible to visitors of the organization.
Y1. 1. 9. 1. 2 Attackers used additional technical means, such as binoculars or an unmanned aerial vehicle, and saw the login data being entered through a window.
Y1. 1. 9. 2. Attackers extracted credentials from records of radio communication between the keyboard and the computer's system unit if they were connected via a radio interface (for example, Bluetooth).
Y1. 1. 9. 3. The attackers intercepted the credentials due to their leakage through the channel of spurious electromagnetic radiation and interference (PEMIN).
Explanation of Y1. 1. 9. 3.
Examples of the attack are here and here.
Y1. 1. 9. 4. The attacker intercepted the input of credentials from the keyboard by using special technical means (STS) designed to secretly remove information.
Explanation of Y1. 1. 9. 4.
Examples of devices.
Y1. 1. 9. 5. Attackers intercepted the input of credentials from the keyboard by
analyzing the Wi-Fi signal modulated by the user's keystroke process.
Explanation of Y1. 1. 9. 5.
Example of an attack.
Y1. 1. 9. 6. Attackers intercepted the input of credentials from the keyboard by analyzing the sounds of keystrokes.
Explanation of Y1. 1. 9. 6.
Y1. 1. 9. 7. Attackers intercepted the input of credentials from the keyboard of a mobile device by analyzing the accelerometer readings.
Explanation of Y1. 1. 9. 7.
Y1. 1. 10. < ... > previously saved on the Client.
Explanation of Y1. 1. 10.
For example, a user could save a username and password in the browser to access a specific site.
Y1. 1. 11. Attackers compromised credentials due to shortcomings in the process of revoking user access.
Explanation of Y1. 1. 11.
For example, after a user was dismissed, their accounts were not blocked.
Y1. 2. < ... > by exploiting vulnerabilities in the access control system.
Decomposition
Y2. 1 <...> by making unauthorized changes to data containing information about user privileges.
Y2. 2 <...> by exploiting vulnerabilities in the access control system.
Y2. 3. < ... > due to shortcomings in the user access control process.
Explanation of Y2. 3.
Example 1. The user was granted more access to work than he needed for official reasons.
Example 2. After the user was transferred to another position, the previously granted access rights were not revoked.
Integration module – a set of information infrastructure objects designed to organize information exchange between information systems.
Given the fact that in corporate networks it is not always possible to clearly separate one information system from another, the integration module can also be considered as a link between components within one information system.
Architecture
The generalized scheme of the integration module looks like this:
Description of the architecture elements:
Examples of integration modules
Scheme 1. Integration of ABS and AWP KBR via a third-party file server
To execute payments, an authorized bank employee unloads electronic payment documents from the ABS and saves them to a file (in its own format, for example, an SQL dump) on the network folder (\\...\SHARE\) of the file server. Then this file is converted to a set of files in the UFEBS format using a converter script, which is then read by the KBR APM.
After that, an authorized employee — a user of the KBR automated Control System-encrypts and signs the received files and sends them to the Bank of Russia payment system.
When payments are received from the Bank of Russia, the KBR Automated Control System performs their decryption and verification of the electronic signature, and then writes them to the file server as a set of files in the UFEBS format. Before importing payment documents to ABS, they are converted using a converter script from the UFEBS format to the ABS format.
We will assume that in this scheme, the ABS operates on one physical server, the KBR AWP operates on a dedicated computer, and the converter script operates on a file server.
Correspondence of objects of the considered schema to the elements of the integration module model:
"Exchange servers on the ABS side" – the ABS server.
"Exchange servers from the KBR AWP" – the KBR AWP computer.
Intermediary – a third-party file server.
Data Processing Software – a script converter.
Scheme 2. Integration of ABS and AWS KBR when placing a shared network folder with payments on AWS KBR
Everything is similar to Scheme 1, but a separate file server is not used, instead a network folder (\\...\SHARE\) with electronic payment documents is placed on a computer with the KBR APM. The script converter also works on the KBR WORKSTATION.
Correspondence of objects of the considered scheme to the elements of the integration module model:
Similar to Scheme 1, but the "Intermediary" is not used.
Scheme 3. Integration of ABS and AWP KBR-N via IBM WebSphera MQ and implementation of electronic document signing "on the ABS side"
ABS runs on a platform that is not supported by the SCAD Signature SCSI. Outgoing electronic documents are signed on a special electronic signature server (EP Server). The same server verifies the electronic signature of incoming documents from the Bank of Russia.
ABS uploads a file with payment documents in its own format to the Item Instance Server.
The EP server uses a converter script to convert the file to e-mail messages in the UFEBS format. After that, the e-mail messages are signed and transmitted to IBM WebSphere MQ.
The KBR-N AWP accesses IBM WebSphere MQ and receives signed payment messages from there, after which an authorized employee — a user of the KBR AWP — encrypts them and sends them to the payment system of the Bank of Russia.
When payments are received from the Bank of Russia, the KBR-N automated Payment System decrypts them and verifies the electronic signature. Successfully processed payments in the form of decrypted and signed e-mail messages in the UFEBS format are transmitted to IBM WebSphere MQ, from where they are received by the EP Server.
The Item instance server verifies the electronic signature of received payments and saves them to an ABS file. After that, an authorized employee — an ABS user-uploads the resulting file to the ABS in accordance with the established procedure.
Correspondence of objects of the considered schema to the elements of the integration module model:
"Exchange server on the ABS side" – the ABS server.
"Exchange server from the KBR AWP" — the computer of the KBR AWP.
"Intermediary" – the EP Server and IBM WebSphere MQ.
"Data processing software" – a script converter, SCSI SCAD Signature on the Instance Server.
Scheme 4. Integration of the RBS and ABS Server via the API provided by the dedicated exchange server
We will assume that the bank uses several remote banking systems(RBS):
In order to ensure information security, all ABS interaction with RBS systems is carried out through a dedicated exchange server operating within the framework of the ABS information system.
Next, we will consider the process of interaction of the RBS system of the ICB of the legal entity with the ABS.
The RBS server, having received a duly certified payment order from the client, must create a corresponding document in the ABS based on it. To do this, it uses the API to transmit information to the exchange server, which, in turn, enters data into the ABS.
When the client's account balances change, the ABS generates electronic notifications, which are transmitted to the RBS server via the exchange server.
Correspondence of objects of the considered schema to the elements of the integration module model:
"Exchange server on the part of RBS" – the RBS server of IKB YUL.
"Exchange server on the ABS side" – the exchange server.
"Intermediary" – missing.
"Data processing software" – components of the RBS Server responsible for using the exchange server API, components of the exchange server responsible for using the ABS API.
Decomposition
Y1. Introduction of fake information by intruders through the integration module.
Decomposition
Y1. 1. Unauthorized modification of legitimate data when it is transmitted over network connections:
Y1.1.1 Link: "Typical threat model. Network connection. Y2. Unauthorized modification of the transmitted data".
Y1. 2. Transmission of forged data via communication channels on behalf of a legitimate exchange participant:
Y1. 1. 2 Link: "Standard threat model. Network connection. Y3. Violation of the authorship of the transmitted data".
Y1. 3. Unauthorized modification of legitimate data during their processing on Exchange Servers or Intermediaries:
Y1. 3. 1. Link: "Typical threat model. An information system based on the client-server architecture. Y2. Unauthorized modification of protected information during its processing by the server part of the information system".
Y1. 4. Creating fake data on Exchange Servers or Intermediaries on behalf of a legitimate exchange participant:
Y1. 4. 1. Link: "Standard threat model. An information system based on the client-server architecture. Y1. Performing unauthorized actions by intruders on behalf of a legitimate user".
Y1. 5. Unauthorized modification of data during their processing using data processing software:
Y1. 5. 1. < ... > due to unauthorized changes made by intruders to the settings (configuration) of the data processing software.
Y1. 5. 2. < ... > due to unauthorized changes made by intruders to the executable files of the data processing software.
Y1. 5. 3. < ... > due to interactive management of data processing work by intruders.
The object of protection is the cryptographic information protection system used to ensure the security of the information system.
Architecture
The basis of any information system is the application software (software) that implements its target functionality.
Cryptographic protection is usually implemented by calling cryptographic primitives from the business logic of the application software, which are placed in specialized libraries – cryptokernels.
Cryptographic primitives include low-level cryptographic functions, such as:
The business logic of application software uses cryptographic primitives to implement higher-level functionality:
The interaction of business logic and the cryptokernel can be performed:
There are two typical schemes for organizing a cryptokernel:
The elements in these diagrams can be either separate software modules running on the same computer, or network services interacting within a computer network.
When using systems built according to Scheme 1, the application software and the cryptokernel work within a single cryptographic tool operating environment (SPS), for example, on the same computer running the same operating system. As a rule, the user of the system can run other programs within the same operating environment, including those containing malicious code. In such circumstances, there is a serious risk of leakage of private cryptographic keys.
To minimize the risk, scheme 2 is used, in which the cryptokernel is divided into two parts:
The division of a cryptokernel into software and hardware parts is very conditional. There are systems on the market that are built according to the scheme with a shared cryptokernel, but the" hardware " part of which is represented as a virtual machine image-virtual HSM (example).
The interaction of both parts of the cryptokernel occurs in such a way that private cryptographic keys are never transmitted to the software part and, accordingly, cannot be stolen using malicious code.
The interaction interface (API) and the set of cryptographic primitives provided to the application software by the cryptokernel are the same in both cases. The difference lies in the way they are implemented.
So, when using a scheme with a split cryptonuclear, the interaction of software and hardware is performed according to the following principle:
Let's illustrate the operation of a split cryptonuclear using the example of creating an electronic signature:
Features of checking the correctness of an electronic signature
When the receiving party receives data signed with an electronic signature, it must perform several verification steps. A positive result of checking the electronic signature is achieved only if all the verification stages are successfully completed.
Stage 1. Control of data integrity and data authorship.
Content of the stage. The electronic signature of the data is checked using the appropriate cryptographic algorithm. Successful completion of this stage indicates that the data has not been modified since it was signed, as well as that the signature was made with a private key corresponding to the public key of electronic signature verification.
Stage execution location: cryptokernel.
Stage 2. Control of trust in the public key of the signer and control of the validity period of the private key of the electronic signature.
Content of the stage. The stage consists of two intermediate sub-stages. At the first stage, it is determined whether the public key for verifying the electronic signature was trusted at the time of signing the data. The second stage determines whether the private key of the electronic signature was valid at the time of signing the data. In general, the validity periods of these keys may not coincide (for example, for qualified certificates of electronic signature verification keys). Methods for establishing trust in the signer's public key are determined by the rules of electronic document management adopted by the interacting parties.
Stage execution location: application software / cryptokernel.
Stage 3. Control of the signatory's authority.
Content of the stage. In accordance with the established rules of electronic document management, it is checked whether the signatory had the right to certify the protected data. For an example, here is a situation of violation of authority. Suppose there is an organization where all employees have an electronic signature. The internal electronic document management system receives an order from the manager, but signed with the electronic signature of the warehouse manager. Accordingly, such a document cannot be considered legitimate.
Stage execution location: application software.
Assumptions made when describing the security object
Description of the information system
Two organizations decided to introduce legally significant electronic document management (EDI) between them. To do this, they entered into an agreement in which they prescribed that documents will be transmitted by e-mail, and at the same time they must be encrypted and signed with a qualified electronic signature. Office programs from the Microsoft Office 2016 package should be used as tools for creating and processing documents, and cryptographic protection tools should be used for CryptoPro SCSI and CryptoARM encryption software.
Description of the organization's infrastructure 1
Organization 1 has decided that it will install CryptoPro's SCSI and CryptoARM software on the user's WORKSTATION-a physical computer. Encryption and electronic signature keys will be stored on the ruToken key carrier, which operates in the extracted key mode. The user will prepare electronic documents locally on their computer, then encrypt them, sign them, and send them using a locally installed email client.
Description of the organization's infrastructure 2
Organization 2 decided to move the encryption and electronic signature functions to a dedicated VM. In this case, all cryptographic operations will be performed automatically.
To do this, two network folders are organized on the dedicated VM:"\\...\In\", "\\...\Out\". To the network folder"\\...\In\ " files received from the counterparty will be automatically placed in plain text. These files will be decrypted and the electronic signature will be verified.
In the "\\...\Out\" folder, the user will place files that need to be encrypted, signed,and sent to the counterparty. The user will prepare the files themselves on their own ARM.
To perform the encryption and electronic signature functions, CryptoPro SCSI, CryptoARM software, and an email client are installed on the VM. All VM elements will be automatically managed using scripts developed by system administrators. Scripts are logged in log files (logs).
Cryptographic keys of the electronic signature will be placed on a token with an unrecoverable JaCarta GOST key, which the user will connect to their local computer.
The token will be forwarded to the VM using specialized USB-over-IP software installed on the user's ARM and on the VM.
The system clock on the user's ARM in organization 1 will be adjusted manually. The system clock of a specialized VM in organization 2 will be synchronized with the system clock of the hypervisor, which, in turn, will be synchronized over the Internet with public time servers.
Selection of SCSI structural elements
Based on the above description of the IT infrastructure, we will select the structural elements of the SCSI and write them down in a table.
Table-Correspondence of elements of the SCSI model to elements of information systems
Explanations
Assumptions used in threat decomposition:
Decomposition
Y1. Compromise of private cryptographic keys.
Y2. Encryption of forged data on behalf of a legitimate sender.
Y3. Decryption of encrypted data by persons who are not legitimate recipients of the data (intruders).
Y4. Creating an electronic signature of a legitimate signatory under forged data.
Y5. Getting a positive result of checking the electronic signature of forged data.
Y6. Erroneous acceptance of electronic documents for execution due to problems in the organization of electronic document management.
U7. Unauthorized access to protected data during their processing by the SCSI.
Y1. 1. Getting a private key from the private key store.
Y1. 2. Obtaining a private key from objects of the cryptographic medium functioning environment, in which it can temporarily reside.
Explanation of Y1. 2.
Objects that can temporarily store a private key include:
Y1. 2. 1. Extracting private keys from working RAM by freezing RAM modules, extracting them and then reading the data (freeze attack).
Explanation of Y1. 2. 1.
Example of an attack.
Y1. 3. Getting a private key from the private key exchange channel.
Explanation of Y1. 3.
An example of the implementation of this threat will be given below.
Y1. 4. Unauthorized modification of the cryptokernel, as a result of which private keys become known to intruders.
Y1. 5. Compromise of the private key as a result of using technical channels of information leakage.
Explanation of Y1. 5.
Example of an attack.
Y1. 6. Compromise of the private key as a result of the use of special technical means (STS) intended for secret removal of information ("bugs").
Y1. 7. Compromise of private keys in the process of storing them outside the SCSI.
Explanation of Y1. 7.
For example, a user stores their key media in a desktop mailbox, from which they can easily be extracted by intruders.
Explanations
This threat is considered only for data encryption schemes with sender authentication. Examples of such schemes are given in the recommendations for standardization R 1323565.1.004-2017 " Information technology. Cryptographic protection of information. Shared key generation schemes with public key authentication". For other cryptographic schemes, this threat does not exist, since encryption is performed on the recipient's public keys, and they are generally known to attackers.
Decomposition
Y2. 1. Compromise of the sender's private key:
Y2. 1. 1. Link: "Typical threat model. Cryptographic information protection system.Y1. Compromise of private cryptographic keys".
Y2. 2. Substitution of input data in the open data exchange channel.
Notes Y2. 2.
Decomposition
Y3. 1. Compromise of private keys of the recipient of encrypted data.
Y3. 1. 1 Link: "Typical threat model. Cryptographic information protection system. Y1. Compromise of private cryptographic keys".
Y3. 2. Substitution of encrypted data in the secure data exchange channel.
Decomposition
Y4. 1. Compromise of the private keys of the electronic signature of a legitimate signer.
Y4. 1. 1 Link: "Standard threat model. Cryptographic information protection system. Y1. Compromise of private cryptographic keys".
Y4. 2. Substitution of signed data in the open data exchange channel.
Note U4. 2.
Decomposition
Y5. 1. Attackers intercept a message about a negative result of checking an electronic signature in the work results transmission channel and replace it with a message with a positive result.
Y5. 2. Attackers carry out an attack on the trust of signature certificates (SCENARIO — all elements are required):
Y5. 2. 1. Attackers generate a public and private key of an electronic signature. If the system uses electronic signature key certificates, they generate an electronic signature certificate that is as similar as possible to the certificate of the intended sender of the data whose message they want to forge.
U5. 2. 2. Attackers make unauthorized changes to the public key store, giving the generated public key the necessary level of trust and authority.
U5. 2. 3. Attackers sign fake data with a previously generated electronic signature key and embed it in the secure data exchange channel.
Y5. 3. Attackers carry out an attack using expired electronic signature keys of a legal signer (SCENARIO — all elements are required):
Y5.3.1. Attackers compromise expired (not currently valid)ones private keys of the legitimate sender's electronic signature.
Y5. 3. 2. Attackers substitute the time in the time transfer channel for the time when the compromised keys were still valid.
U5. 3. 3. Attackers sign fake data with a previously compromised electronic signature key and embed it in the secure data exchange channel.
Y5. 4. Attackers carry out an attack using compromised electronic signature keys of a legal signer (SCENARIO — all elements are required):
Y5. 4. 1. Attackers make a copy of the public key store.
U5. 4. 2. Attackers compromise the private keys of one of the legitimate senders. The latter notices a compromise, revokes the keys, and information about revoking the key is placed in the public key store.
Y5. 4. 3. Attackers replace the public key store with a previously copied one.
U5. 4. 4. Attackers sign fake data with a previously compromised electronic signature key and embed it in the secure data exchange channel.
U5. 5. < ... > due to the presence of errors in the implementation of the 2nd and 3rd stages of electronic signature verification:
Explanation of Y5. 5.
Y5. 5. 1. Verification of trust in the certificate of the electronic signature key only by the presence of trust in the certificate with which it is signed, without CRL or OCSP checks.
Explanation of Y5. 5. 1.
Y5. 5. 2. When building a chain of trust for a certificate, the authority of issuing certificates is not analyzed
Explanation of Y5. 5. 2.
Example of an attack against SSL / TLS certificates.
The attackers bought a legitimate certificate for their email address. They then made a fraudulent site certificate and signed it with their certificate. If the authorization check is not performed, then when checking the chain of trust, it will be correct, and, accordingly, the fraudulent certificate will also be correct.
Y5. 5. 3. When building a chain of trust for a certificate, intermediate certificates are not checked for revocation.
Y5. 5. 4. CRLs are updated less frequently than they are issued by the certification authority.
U5. 5. 5. The decision to trust the electronic signature is made before the OCSP response about the certificate status is received, sent for a request made later than the time of signature formation or earlier than the next CRL is received after the signature formation.
Explanation of U5. 5. 5.
In the regulations of most CA, the time of revocation of a certificate is considered to be the time when the nearest CRL containing information about the revocation of the certificate is issued.
Y5. 5. 6. When receiving signed data, the identity of the certificate to the sender is not checked.
Explanation of Y5. 5. 6.
Example of an attack. For SSL certificates: the address of the called server may not match the value of the CN field in the certificate.
Example of an attack. Attackers compromised the electronic signature keys of one of the payment system participants. After that, they hacked the network of another participant and sent payment documents signed with compromised keys to the settlement server of the payment system on their behalf. If the server analyzes only trust and does not check compliance, then fraudulent documents will be considered legitimate.
Decomposition
Y6. 1. The receiving party does not detect duplication of the received documents.
Explanation of U6. 1.
Example of an attack. Attackers can intercept a document sent to the recipient, even if it is cryptographically secure, and then repeatedly send it to the secure data transmission channel. If the recipient does not detect duplicates, then all received documents will be perceived and processed as different documents.
Decomposition
Y7. 1.<...> due to information leakage through third-party channels (side channel attack).
Explanation of U7. 1.
Example of an attack.
Y7. 2.<...> due to the neutralization of protection against unauthorized access to information processed on the SCSI:
U7. 2. 1. Operation of the SCSI in violation of the requirements described in the SCSI documentation.
Y7. 2. 2. < ... > implemented in due to the presence of vulnerabilities in:
Y7. 2. 2. 1.<...> anti-unauthorized access tools.
U7. 2. 2. 2.<...> the SCSI itself.
U7. 2. 2. 3.<...> the operating environment of the cryptographic tool.
Item Description
The KBR AWP software and SCAD Signature SCSI are installed on a physical computer that is not connected to the computer network. As a key carrier, the vdToken FCN is used in the mode of operation with an unrecoverable key.
The settlement procedure assumes that the settlement specialist downloads electronic messages in clear text from his work computer (the scheme of the old KBR WORKSTATION) from a special secure file server, then writes them to an alienable USB flash drive and transfers them to the KBR workstation, where he encrypts and signs them. After that, the specialist transfers protected electronic messages to the alienated medium, and then writes them to the file server via his work computer, from where they get to the UTA and then to the payment system of the Bank of Russia.
In this case, the channels for exchanging open and protected data will include: the file server, the specialist's work computer, and the media to be disposed of.
Attack
Unauthorized intruders install a remote control system on the specialist's work computer and, at the time of recording payment orders (electronic messages) in plain text on the alienated medium, replace the contents of one of them. The specialist transfers payment orders to the KBR APM, signs and encrypts them without noticing the substitution (for example, due to a large number of payment orders on a flight, fatigue, etc.). After that, the fake payment order passes through the technological chain and enters the payment system of the Bank of Russia.
Item Description
The computer with installed AWP KBR, SCAD Signature and connected key carrier FCN vdToken functions in a dedicated room without access from the staff.
The calculation specialist connects to the KBR workstation in remote access mode via the RDP protocol.
Attack
Attackers intercept banking details used by the settlement specialist to connect and work with the KBR automated control system (for example, by using malicious code on their computer). Then they connect on their behalf and send a fake payment order to the Bank of Russia's payment system.
Item Description
Let's consider one of the hypothetical options for implementing the ABS-KBR integration modules for a new scheme (AWP KBR-N), in which the electronic signature of outgoing documents occurs on the ABS side. At the same time, we will assume that ABS operates on the basis of an operating system that is not supported by the SCAD Signature SCSI, and, accordingly, the cryptographic functionality is transferred to a separate virtual machine — the ABS-KBR integration module.
The key storage medium is a regular USB token that works in the extracted key mode. When connecting the key media to the hypervisor, it turned out that there were no free USB ports in the system, so we decided to connect the USB token via a network USB hub, and install a USB-over-IP client on the VM that will communicate with the hub.
Attack
Attackers intercepted the private key of an electronic signature from the communication channel between the USB hub and the hypervisor (data was transmitted in clear form). Having the private key, the attackers created a fake payment order, signed it with an electronic signature, and sent it to the KBR-N ARM for execution.
Item Description
Let's consider the same scheme as in the previous scenario. We assume that e-mail messages coming from the KBR-N AWP fall into the \ \ folder...\SHARE\In, and those that are sent to the KBR-N ARM and then to the Bank of Russia payment system are sent to \\...\SHARE\out.
We will also assume that when implementing the integration module, the lists of revoked certificates are updated only when cryptographic keys are reissued, and also that electronic messages received in the \\folder are updated...\SHARE\In is checked only for integrity control and control of trust in the public key of the electronic signature.
Attack
The attackers, using the keys stolen in the previous scenario, signed a fake payment order containing information about the receipt of money to the account of a fraudulent client and embedded it in the secure data exchange channel. Since there is no verification that the payment order was signed by the Bank of Russia, it is accepted for execution.
Other parts of the study
- Information security of bank non-cash payments. Part 1 - Economic fundamentals.
- Information security of bank non-cash payments. Part 2 - Typical IT infrastructure of the bank.
- Information security of bank non-cash payments. Part 3 - Creating requirements for the security system.
- Information security of bank non-cash payments. Part 4 - Overview of threat modeling standards.
- Information security of bank non-cash payments. Part 5 - 100 + thematic links about bank hacks.
- Information security of bank non-cash payments. Part 6 - Analysis of banking crimes.
- Information security of bank non-cash payments. Part 7 - Basic Threat Model.
- Information security of bank non-cash payments. Part 8 - Typical threat models.
Part 1 - Economic fundamentals
Information security of banks is one of the most interesting tasks for ensuring practical security. The large amounts of money held by banks, the ubiquity of online technologies and online payments make banks a welcome target for the bad guys from the dark side. And if there are problems, then there must be solutions.We present to your attention the results of a study on ensuring information security of one of the most vulnerable areas of the bank — the process of making non-cash payments.
The study turned out to be quite extensive, so it will be published in parts. And we will start with the first part, which will tell you what non-cash payments are from an economic point of view.
Terms, definitions, assumptions and conventions
The purpose of the study is to systematize knowledge, solutions and experience in ensuring information security of bank wire transfers.
Information sources:
- open materials from the Bank of Russia website,
- legal information and reference systems,
- materials and publications in mass media,
- reports from security companies,
- own experience and personal communication with colleagues.
Assumptions:
The standard scheme of organizational and technical interaction between credit institutions and the Bank of Russia adopted in the Moscow region is taken as a basis.
When considering the economic fundamentals, issues related to the collection of commissions and accounting will be omitted.
Terms and conditions:
The study will use terms and definitions in the sense in which they are used in the current legislation of the Russian Federation.
Synonyms:
Bank = credit institution.
Non-cash payment = transfer of funds.
Payments = settlements.
Cash payments vs. cashless payments
Historically, the first types of payments were made in cash. The buyer handed over banknotes to the seller, and in return received a product or service.

Let's analyze the pros and cons of this form of settlement from the point of view of the buyer and seller, as well as from the point of view of the state economy as a whole.
| Cash settlement analysis from the point of view of the seller and buyer | |
|---|---|
| Positive | Minuses |
| Provides the buyer and seller with maximum freedom and independence from third parties. The main thing is that the banknotes are well protected from forgery, and there is a sufficient number of them | Significant inconvenience, and sometimes the inability to make purchases without personal contact of settlement participants. Ensuring the security of cash storage. |
| Analysis of cash payments from the state's point of view | |
|---|---|
| Positive | Minuses |
| A historically formed form of payment that the population is used to. | With cash payments, money "settles" from sellers and stops "working" until the seller makes a purchase with it. |
| The state bears the infrastructure costs for the production of banknotes, their logistics and disposal. | |
| Cash payments are practically beyond the control of the fiscal authorities (tax inspectorate) and create conditions for the development of the shadow economy and tax evasion. |
Thus, it is clear that cash payments for the state are an evil that it would gladly prohibit if it did not cause a sharp protest of the population. And if it is impossible to completely ban it, then restrictive measures are applied.
In Russia, in particular, legislation (Civil Code of the Russian Federation, Article 861, Bank of Russia Directive 3073-U of 07.10.2013) establishes that only citizens and only for personal purposes can use cash without restrictions, while the rest (sole proprietors, legal entities,...) are strictly limited in the use of cash.
Non-cash payments, in contrast to cash payments, imply the presence of a third trusted party between the seller and the buyer — an intermediary who, on behalf of the parties, performs settlements between them.
Cryptocurrencies such as Bitcoin, Ethereum, and others allow payments to be made without intermediaries (not counting miners), but so far the status of these systems is not legally defined, and their description is beyond the scope of this article. Here we will consider only "classic" non-cash payments, where credit organizations (banks) act as the third trusted party.
Bank accounts and money in non-cash form
For making non-cash payments, money is used in a non-cash form. Consider the mechanisms for converting money from cash to non-cash and back.
It all starts with the fact that the client, whether an individual, a legal entity or an individual entrepreneur, enters into a contractual relationship with a credit institution that has a banking license from the Bank of Russia.
The Client transfers cash funds to the bank, the bank accepts them and reflects them on a bank account specially established for accounting for settlements with the client. If the client deposits money in the bank, the balance on this account increases, if he withdraws, it decreases.
After the client has deposited cash in the bank, it turns into non-cash money, which, if much simplified, is not even money, but the bank's obligations to do certain services for the client, which can include issuing cash to the client, transferring funds, and so on.
In addition to receiving and withdrawing cash, the client's bank account may increase or decrease due to receiving non-cash transfers from third parties and making transfers to third parties, respectively. It is important to note that non-cash money is not the obligations of the entire banking system, but the obligations of the bank where the corresponding bank account is opened. This realization comes especially vividly if the bank that serves this account goes bankrupt. Then the money (the balance on the account) seems to be there, but it is impossible to use it.
There are different types of bank accounts. Customers — individuals-open current or special card accounts with the bank. Clients — legal entities-open current accounts with banks. Banks open correspondent accounts with other banks to make payments. Without going into details, the functioning of all these accounts looks approximately the same: an increase in the account balance leads to an increase in the obligations of the bank in which it is opened, and vice versa, a decrease in the balance reduces the bank's obligations. For the sake of simplicity, in the future we will consider only work on settlement and correspondent accounts.
At this stage, the bank will consist of two main parts for us:
- a bank account register containing the values of customer account balances;
- funds of the bank, consisting of all customers ' money and the bank's own funds.
One of the main sources of income for banks is lending. The bank transfers the money for temporary use to the client, who returns it with interest. To support this type of business, the bank needs money that it will give on credit. And this is where customer money stored in non-cash accounts comes into play.
The basic idea is that the bank never holds all the money of its customers. Instead, the bank keeps statistical records of customers ' activities and "very accurately guesses" how much money they may need for current payments. The rest of the money is used by the bank for lending.
Payment mechanisms
Let's look at how a non-cash payment is made between a payer and a recipient (hereinafter referred to as clients) who are served in the same bank.
Transaction 1.
Client A makes a transfer to Client B's address. For its execution, the Bank reduces the balance of funds on the current account of Client A by the amount of the transfer and increases the balance on the account of Client B. The total amount of money in the bank does not change.
When paying in cash, payments are always of the same type: the payer voluntarily transfers the required amount of money to the recipient. When using non-cash payments, the payment schemes may be different:
- the payer can order the bank to make a payment to the recipient at the expense of funds in their bank account at their own will-settlements on payment orders;
- the recipient may request the bank with which the payer's account is opened to make a payment to their address if there is a corresponding agreement with the payer or in cases stipulated in the legislation. In this case, the payment can be made with the payer's acceptance – settlement of payment claims, or in a non-acceptance manner-settlement of collection orders;
- the payer and the recipient can agree that the bank will make a payment to the recipient, provided that the latter submits to the bank pre-agreed documents confirming the fact of the transaction-settlement under letters of credit;
- and other forms that can be found in clause 1.1 of the Bank of Russia Regulation No. 383-P of 19.06.2012 "On the Rules for Making Money Transfers".
The most common form of settlement is based on payment orders.
Regardless of the settlement forms used, the Bank reports to the client for all transactions made on its account by providing a special document – an account statement.
The payment order and account statement are the main legally significant documents used by the client and the bank for accounting purposes and conflict resolution proceedings in court.
It is important to note that if a payment was received to the client's current account and it was reflected in the account statement, the bank does not have the right to return the payment to the sender, even if it was made by mistake or maliciously. Refund of payment is possible only by agreement with the recipient or by a court decision. The maximum that a bank can do is, in accordance with the legislation on countering the legalization of proceeds from crime, to block funds in the recipient's account.
Note
The Civil Code of the Russian Federation (Civil Code of the Russian Federation Article 1102. Obligation to return unjust enrichment) requires the recipient to return funds to the sender if they were sent without justification or by mistake.
Direct correspondent relations
Earlier, we looked at how transfers are made between clients served in the same bank. Now let's complicate the task and look at how settlements are made between clients served in two different banks.
For interbank settlements, banks must establish correspondent relations with each other. The essence of this relationship is that one bank, Bank 2 in the diagram below (Figure 3), becomes a client of Bank 1 and opens a special bank account called a correspondent account. After opening a correspondent account, Bank 2 deposits a certain amount of money into it, a kind of monetary buffer in the amount of which Bank 2's clients can send payments to Bank 1's clients.
To understand how this works, let's look at an example. Let's say that Bank 2 has placed, say, 1 million rubles on a correspondent account in Bank 1.
Transaction 2.
Customer B, served at Bank 2, wants to send Customer A, served at Bank 1, for example, 500 thousand rubles. To do this, it forms and sends a payment order to Bank 2, in which it specifies Client A as the recipient, and specifies 500 thousand rubles as the payment amounts. Bank 2, having received the order from Client B, sees that the payment recipient is Client A, served by Bank 1. Then Bank 2 sends an order to Bank 1 to write off 500 thousand rubles from its correspondent account and transfer them to Client A's current account, and after that Bank 2 reduces the balance on Client B's current account by 500 thousand rubles.
Transaction 3.
Now let's look at an example where Client B sends 2 million rubles to Client B. To do this, Client B sends the corresponding payment order to Bank 1. Bank 1 debits 2 million rubles from Client B's current account and deposits them to Bank 2's correspondent account, after which it transfers a payment order from Client B to Bank 2. Upon receiving it, Bank 2 increases the balance on Client B's current account by 2 million rubles.
After transactions 2 and 3, the corresponding Bank account 2 will have 2.5 million rubles.
Transaction 4.
What happens if Client B sends 3 million rubles to Client A? Everything will be the same as when considering transactions 2 and 3, except that the payment will not be executed until Bank 2 increases the corresponding account balance by the missing 500 thousand rubles.
Bank of Russia payment System
The mechanism for making payments between two banks, which we just reviewed, is simple, but has a significant drawback in terms of scalability. With a large number of banks, it is difficult to establish and maintain correspondent relations between each bank and each other. Therefore, the main tool for interbank money transfers in the Russian Federation is the payment system of the Bank of Russia.
The main idea of this payment system is that the Bank of Russia acts as a single point to which all banks are connected, and through which payments pass from one bank to another.
Each credit institution, when registering and obtaining a banking license, opens a correspondent account with the Bank of Russia.
In order to be able to distinguish one bank from another, they are assigned bank identification codes (BIC). The Bank of Russia regularly updates and publishes the BIC directory on its website. If you know the BIC, you can also use this directory to determine the corresponding bank account number opened with the Bank of Russia. The combination of the BIC and current account number uniquely identifies the client's current account within the entire payment system of the Russian Federation.
Let's look at how an interbank payment will be made using the Bank of Russia's payment system. Let's take the interaction between customers and banks as a basis, illustrated in Figure 4.
Transaction 5.
Customer D makes a payment to Customer B. To do this, he sends a payment order to his bank (Bank 3), in which he specifies Client B as the payee.
Bank 3, after receiving a payment order from Client D, sees that the recipient of the payment (Client C) is not its client, and forwards the payment order to the Bank of Russia.
The Bank of Russia reduces the balance on the correspondent account of Bank 3 by the payment amount and increases the balance on the correspondent account of Bank 2 (recipient bank) by the same amount. After that, the Bank of Russia sends the payment order to Bank 2 and sends a notification to Bank 3 about the payment, which in turn reduces the balance on the Client's current account.
Bank 2, having received a notification from the Bank of Russia, increases the balance on Client B's current account. Both banks-Bank 2 and Bank 3-reflect cash flows on current accounts in statements and provide them to customers.
If there are several options for the flow of funds, as, for example, between Client B and Client C in Figure 4, the sending bank independently decides on the routing of the payment: using direct correspondent relations or through the payment system of the Bank of Russia-depending on the payment parameters, its cost price and other conditions.
Money transfers in the payment system of the Bank of Russia are carried out:
- in real-time mode using the bank's Electronic urgent payments (BESP)service;
- in discrete mode, using the mechanisms of intraregional electronic settlements (VER) or interregional electronic settlements (MEA).
Real-time payment processing is similar to using a taxi. The payment is sent to the Bank of Russia and processed immediately. In discrete mode, payment processing is similar to transporting passengers by regular bus. Payments are first accumulated, and then all of them are processed in a heap. The Bank of Russia operates several similar flights during the business day.
The schedule of flights accepted in the Moscow region is published on the website of the Bank of Russia and consists of five flights:
| Flight number | Electronic document acceptance period | Electronic document processing period | Time when processing results were issued |
| First flight | 10:00 – 11:00 | 11:00 – 12:00 | from 12: 00 |
| Second flight | 11:15 – 14:00 | 14:00 – 15:00 | from 15: 00 |
| Third flight | 14:15 – 16:00 | 16:00 – 17:00 | from 17: 00 |
| Fourth flight | 16:16 – 18:00 | 18:00 – 20:00 | from 20: 00 |
| Final flight | 19:00 – 21L00 | 21:00 – 22:00 | from 22: 00 |
The Bank of Russia's tariffs for making payments via BESP are higher than in discrete mode.
Transfers at the expense of banks ' own funds
Before that, we discussed how banks execute customer payments. Now let's look at how the bank makes its own payments, for example, buying paper, paying for electricity, communication services, etc.
By and large, everything is done exactly the same as in the case of customer payments, only the bank pays not from the current account, but from one of its correspondent accounts. This circumstance often puts inexperienced counterparties of the bank in a stupor, and they compulsively demand the bank's current account number, while banks usually do not have current accounts. Otherwise, everything is the same: a payment order is generated, then it is sent to the bank where the corresponding account is opened, that bank executes it and responds with an account statement.
Conclusion
In this section, we have introduced the basic principles and mechanisms related to the implementation of non-cash money transfers in the Russian Federation. In the next part, we will look at the bank's IT infrastructure used for making transfers, and especially the part that is responsible for implementing correspondent relations with the Bank of Russia.Part 2 - Typical IT infrastructure of the bank
In the first part of our research, we examined the operation of the bank's non-cash payment system from an economic point of view. Now it is time to look at the internal structure of the bank's IT infrastructure, through which these payments are implemented.Disclaimer
This article does not contain confidential information. All materials used are publicly available on the Internet, including on the Bank of Russia website.
Chapter 1. General description of the IT infrastructure
Basic terms
In the 90-x years of the last century, the term "automated system" was often used in the state standards and regulatory documents of the FSTEC of Russia (then still the State Technical Commission under the President of the Russian Federation). "GOST 34.003-90 Information technology (IT). A set of standards for automated systems. Automated systems. Terms and Definitions " gives the following definition of this term:
automated system; AC: A system consisting of personnel and a set of automation tools for their activities, which implements information technology for performing established functions.
After some time, a new term came into use — information system. In clause 3 of Article 2 of Federal Law No. 149-FZ of 27.07.2006 "On Information, Information Technologies and Information Protection", this term is defined as follows::
information system — a set of information contained in databases and information technologies and technical means that ensure its processing;
In this study, both terms will be used interchangeably.
The validity of this approach can be proved by the fact that in the Order of the FSTEC of Russia dated 11.02.2013 N 17 "On approval of Requirements for the protection of Information that does not Constitute a state secret contained in state information systems", the state regulator prescribes to be guided by State Standards on automated systems for the protection of information systems.
In addition to information systems, the bank's IT infrastructure also includes one more type of elements — information services, or, as they are often called, robots.
It is rather difficult to define the concept of an information service, so let's just list its main differences from an information system:
- An information service is much simpler than an information system, but at the same time it cannot be called a component of the latter, since the results of its work can be used simultaneously by several information systems.
- Information services are designed to automate simple, routine tasks.
- Information services do not contain databases.
- Information services operate automatically without human involvement (or with minimal involvement).
Automated banking system
The core of any bank's information infrastructure is an automated banking system, or ABS for short.
Standard of the Bank of Russia STO BR IBBS-1.0-2014 " Ensuring information security of organizations of the banking system of the Russian Federation. General Provisions" defines ABS as follows:
automated system that implements the banking technological process.
This definition allows you to fit almost any IT system in a bank under it. At the same time, ordinary bank employees call ABS the system that deals with accounting for bank accounts, transactions between them (cash flow) and balances. The second definition does not contradict the first one and details it more clearly, and we will continue to use it.
In modern Russian banks, the most common ABS are the following:
- Diasoft FA#,
- Inversion of the XXI century,
- RS-Bank,
- CFT-Bank.
Some particularly large banks do not use mass-produced ABS systems, but specially designed for them. But such cases are rare, just like especially large banks.
Sometimes banks use several ABS systems from different manufacturers in parallel. This often happens when a bank tries to switch from one ABS to another, but there may be less trivial reasons.
Applied information systems
Despite the fact that ABS automates quite a large number of tasks, it does not cover all the bank's needs. There are tasks that the ABS does not do at all or does not do as the bank wants it to do. Therefore, other information systems that automate individual business processes are connected (integrated) to the ABS. In the future, such information systems will be called applied information systems.
Examples of applied information systems include:
- remote banking systems of the Internet Client-Bank (RBS ICB, for example, iBank2, BS-Client, InterBank),
- payment card processing (for example, TranzWare, SmartVista, Way4),
- contact center automation systems (for example, Avaya Call Center, Cisco Unified Contact Center),
- automatic scoring systems for borrowers (for example, FICO),
- etc.
Depending on the size of the bank and the services it provides, the number of applied information systems can range from units to hundreds.
Infrastructure information systems
In addition to ABS and applied information systems that automate basic business processes, banks also have a decent number of auxiliary infrastructure information systems. Examples of such systems can be:
- Active Directory Service,
- domain Name Service (DNS),
- corporate email,
- services for providing employees with Internet access;
- access control systems (ACS) to premises;
- IP video surveillance;
- IP telephony services;
- and much more.
Information services
Banks use a huge number of different information services that perform simple, routine functions, such as downloading BIC and FIAS reference books, publishing currency rates on the official website, etc.
Client parts of third-party information systems
Special mention should be made of the client parts of information systems external to the bank. As examples, I will give:
- integration modules with state information systems: GIS GMP, GIS HOUSING AND UTILITIES;
- client parts of external payment systems;
- exchange trading terminals;
- etc.
Typical ways to integrate information systems
The following mechanisms are usually used to integrate information systems:
- Integration via an API (for example, Web services).
- Integration via DBMS:
- by granting access only to stored procedures;
- by providing access to stored procedures and database tables.
- File sharing:
- via a computer network;
- via alienated machine storage media (OMNI, for example, flash drives).
- Implementation of a service-oriented architecture (SoA).
Integration modules
Under the integration module, we will understand a virtual element of the IT infrastructure that implements the integration of other elements of the IT infrastructure.
We called this element virtual, because its functionality can be implemented either as a separate specialized element of the IT infrastructure (for example, an information service), or as components of integrated information systems. Moreover, even a person who "manually" transfers information between integrated information systems can act as an integration module.
Example of a bank's IT infrastructure
Shows a fragment of a typical bank information infrastructure containing the types of elements discussed above.
Chapter 2. Cashless payment infrastructure
If you look at this scheme from the point of view of performing non-cash payments, you can see that the bank implements them using:
- direct correspondent relations with the partner bank,
- an international payment system (IMS) (for example, VISA, MasterCard).
- correspondent relations with the Bank of Russia.
Technically, direct correspondent relations with partner banks can be organized using:
- conventional RBS & B systems used by banks for servicing legal entities (in the example under consideration (Fig. 1), this method is used);
- interbank payment systems (for example, SWIFT);
- specialized payment messaging systems (for example, REX400, TELEX);
- specialized software developed by one of the interacting banks.
Connection to payment systems that serve plastic cards is made through standard modules that are part of processing systems.
For successful operation, the bank must ensure information security of all listed payment methods. It is very problematic to consider them within the framework of a single, even large-scale study, and therefore we will focus only on one area that is most critical from the point of view of possible losses — the bank's payment interaction with the Bank of Russia.
Infrastructure for ensuring payment interaction with the Bank of Russia
We will consider the IT infrastructure of the bank's payment interaction with the Bank of Russia as an example of the execution of a payment sent to a client of another bank.
As we remember from the first part, the client must first send a payment order to the bank. There are two ways to do this:
- Show up in person at the bank's branch and hand over a certified payment order in hard copy.
- Send the payment order via the RBS ICB system.
It is important to note here that RBS systems are only systems that provide legally significant electronic document flow between the client and the bank, and they do not make payments independently. That is why when a client opens a bank account, they usually enter into two contracts. The first is a contract for servicing a bank account, the second is a contract for electronic document management using the RBS ICB system. If the second agreement is not concluded, the client will still be able to use their account, but only during a personal visit to the bank's branch.
If the client has submitted a payment order in hard copy, the bank employee makes an electronic payment order based on it to the ABS. If the order was submitted via the RBS of the ICB, then it is automatically sent to the ABS via the integration module.
Proof that it was the client who made the order to transfer funds, in the first case, is a paper document personally signed by him, and in the second, an electronic document in the RBS of the ICB, certified in accordance with the agreement.
Usually, for certification of electronic documents of clients — legal entities, RBS ICB uses a cryptographic electronic signature, and for documents of clients — individuals, SMS confirmation codes are used. From a legal point of view, banks usually use the legal regime of a handwritten signature analog (TSA) to certify electronic documents in both cases.
Once in the ABS, the payment order is monitored in accordance with the bank's internal regulations and sent for execution to the Bank of Russia's payment system.
Technical means of interaction with the Bank of Russia payment system
The technical means (software) used to interact with the Bank of Russia payment system may vary depending on the territorial institution of the Bank of Russia that serves the bank's correspondent account.
For banks served in the Moscow region, the following software applies:
- APM KBR-automated workplace of a Bank of Russia client;
- UTA – special software for file interaction of the Bank of Russia client (universal transport adapter);
- SCAD Signature-a cryptographic information protection tool (SCSI) "Hardware and software complex Signature-client" version 5, certificates of the Federal Security Service of Russia-SF/114-2680 (cryptographic protection level KC1), for the cryptographic protection level KC2 – SF/124-2681 (cryptographic protection level KC2). SCUD stands for cryptographic document authentication system.
ARM OF the CBD
APM KBR is software used by authorized employees of the bank to encrypt and electronically sign outgoing payment documents, as well as decrypt and verify the electronic signature of payment documents received from the Bank of Russia. But, to be more precise, the KBR Automated Control System operates not with payment documents, but with electronic messages (ES), which are of two types:
- electronic payment messages (EPS), for example, ED101 "Payment order";
- electronic service information messages (ESIS), for example, ED201 "Notification of the results of ES control".
The list and formats of electronic messages are established by the Bank of Russia by issuing an Album of Unified Formats of Electronic Banking Messages (UFEBS).
In order for the KBR AWP to process the payment, it must be converted to a file containing an electronic payment message in the UFEBS format. The ABS integration module with the Bank of Russia payment system is responsible for this transformation. From a technical point of view, such conversions are quite simple, since the UFEBS format is based on XML.
Files of electronic messages leave the ABS integration module in open format and are placed in a special folder of the file system (usually a network folder), which is configured in the KBR WORKSTATION for electronic messages with the status "Entered". In the previous diagram, this folder is designated as "Folder 1".
Then, during processing, electronic messages change their statuses to "Controlled", "Sent" , etc., which is technically implemented by moving the file with the electronic message to the corresponding folders that are configured in the KBR AWP. In the diagram (Fig. 2), these folders are designated as "Folder 2".
At a certain moment of technological processing (established by the bank's internal regulations) of outgoing electronic messages, they are encrypted and signed with an electronic signature using SCAD Signature and private cryptographic keys of responsible employees.
SCUD Signature
SCAD Signature is a SCSI developed by Validata LLC on behalf of the Bank of Russia and designed to protect information in the Bank of Russia's payment system. This SCSI is not publicly available (except for the documentation posted on the CBR website), and it is distributed by the Bank of Russia only to participants of its payment system. The distinctive features of this SCSI include::
- This SCSI, unlike other common SCSI in Russian business circles (for example, such as Crypto-PRO CSP, VIPNET CSP, etc.), implements its own public key infrastructure (PKI) isolated from the operating system. This is manifested in the fact that the public key directory containing certificates, a list of trusted certificates, a list of revoked certificates, etc. is cryptographically protected on the user's private key, which prevents an attacker from making changes to it, for example, installing a trusted certificate without the user's knowledge.
Note. Verba-OW implements a similar key model. - The next feature follows from the previous one. In the SCSI, to make working keys, you must first create a certificate directory using special registration keys. After the working keys expire, new ones are generated, but in order to generate them, you need to have the previous working keys that are valid. Keys are created using a decentralized scheme with the participation of the Bank of Russia as a Certification Authority.
- SCSI supports working with functional key carriers (vdToken) that perform electronic signature and encryption functions on board, without transferring private keys to computer memory.
- There are two types of cryptographic keys used to interact with the Bank of Russia's payment system::
- "Encryption only" – allows you to encrypt / decrypt electronic messages.
- "Encryption and signature – - do the same thing as in the first case, and also allow you to sign electronic messages.
UTA
Encrypted and signed electronic messages are placed in a special folder, in the diagram this is "Folder 3". UTA continuously monitors this folder and, if it sees new files there, transmits them to the Central Bank of the Russian Federation in one of the following ways:
- "On the Internet", although in fact this is not entirely true. Instead of the Internet, a specialized telecom operator is used that provides dedicated communication channels to the Central Bank of the Russian Federation, but since the network is IP-addressable, they say that sending goes through the Internet.
- "Via modem". In case of an accident of the first type of communication, there is a reserve in the form of a modem connection over the public telephone network.
- In case of failure of all communication channels, delivery of electronic messages to OMNI (alienated machine data carrier) by courier is provided. By the way, this is one of the ways that banks with revoked licenses make payments during their liquidation.
After reaching out to the Central Bank (in the first or second way), UTA transmits electronic messages through the API published by the Central Bank. During communication sessions, UTA also receives input electronic messages from the Central Bank.
It should be noted that all electronic messages that UTA works with are encrypted and signed with an electronic signature.
After receiving an encrypted email, UTA moves it to the folder with incoming encrypted messages. The authorized employee checks the electronic signature and decrypts the message with the help of their cryptographic keys and APM KBR.
Further processing is performed depending on the type of electronic message. If this is a payment message, it is transmitted to the ABS via the integration module, where accounting entries are generated based on it, which change the account balances. It is important to note that when the ABS (integration module) interacts with the KBR AWP, standard format files are used in open format.
During the operation of the automated control system, the KBR keeps a log of its work, which can be implemented in the form of text files or using databases running under the DBMS.
Alternative processing schemes
We have considered the "classic" scheme of the system operation. In reality, there are many varieties of it. Let's look at some of them.
Type 1. Separating message sending and receiving paths
The scheme is implemented with two AWP KBR. The first one works with human participation and performs only sending messages, the second one works in automatic mode and performs only receiving messages.
AWP KBR
Version 2. The full automatic is configured to work completely in automatic mode without human intervention
APM KBR
Version 3. Isolated APM KBR functions as a dedicated computer that is not connected to the bank's network. Electronic messages are transmitted to it by a human operator using OMNI.
Transfer of an electronic signature from the APM of the KBR to the ABS
The Bank of Russia plans to switch to a new technological payment processing scheme, in which electronic messages will be signed not in the KBR AWP, as was previously the case, but in the ABS (more precisely, in the ABS — KBR AWP integration module).
To implement this approach, a new version of the KBR AWP was released, which became known as the KBR-N AWP (new). All the main changes can be seen if you compare the schemes of information flows passing through the AWP of the CBD of the old and new versions.
Let's consider the scheme of information flows in the classic AWP KBR. The source of the scheme is the official documentation for the KBR AUTOMATED WORKSTATION " AUTOMATED WORKPLACE OF a BANK OF RUSSIA CLIENT. Programmer's guide. CBRF.61209-04 33 01".
Notes.
- Symbol "AS KBR" (automated customer system of the Bank of Russia) corresponds to the ABS symbol in the previous diagrams.
- The symbol "SVK open source" corresponds to the UTA symbol in the previous diagrams.
- KA – authentication code (electronic signature) of the electronic message.
- ZK-security code is another type of electronic signature, but unlike the CA, which is formed by the original message without changes, the ZK is formed only under meaningful data without markup. You can read more about the technical nuances of the SC and ZK in the documentation of the Federal Security Service " Protection of electronic messages (ES packets)". From a legal point of view, the ZK is a technological measure to protect information, while the KA, according to the agreements and rules of the payment system of the Bank of Russia, is recognized as an electronic signature.
Now let's take a look at a similar scheme for the new KBR-N AWP. Source " AUTOMATED WORKPLACE OF A BANK OF RUSSIA CLIENT NEW. Programmer's guide. CBRF.61289-01 33 01"
From the cryptographic point of view, the KBR-N automated workplace is responsible for encrypting / decrypting electronic messages, as well as for verifying electronic signatures on them. Electronic signature generation has been moved to the ABS integration module.
It is logical to assume that this module will also have to check signatures for messages received from the KBR-N AWP. From a technical point of view, this is not mandatory, but from a security point of view, it is critical, since it ensures the integrity of messages transmitted between the ABS and the KBR-N AWP.
In addition to the file interface for interaction between the ABS, the KBR-N automated workstation and the UTA, the IBM WebSphere MQ interface has been added, which allows you to build a service-oriented IT infrastructure of the bank and solve the problem of the old scheme with the organization of simultaneous work of several operators responsible for sending payments.
Conclusion
We reviewed the internal structure of the bank's payment IT infrastructure. In the following parts, we will look at the information security threats that arise here.Part 3 - Creating requirements for the security system
In the previous parts of the study, we discussed the economic foundations and IT infrastructure of bank non-cash payments. In this part, we will discuss the formation of requirements for the information security system (IS) being created.Next, we'll look at:
- the role of security in the life of a commercial organization;
- place of the information security service in the organization's management structure;
- practical aspects of ensuring security;
- applying the theory of risk management in information security;
- main threats and potential damage from their implementation;
- composition of mandatory requirements for the information security system of bank non-cash payments.
The role of security in the life of a commercial organization

In the modern Russian economic environment, there are many different types of organizations. These can be state-owned enterprises( FSUE, Municipal Unitary enterprise), public funds, and, finally, ordinary commercial organizations. The main difference between the latter and all others is that their main goal is to maximize profit, and everything they do is aimed at this.
A commercial organization can earn money in various ways, but the profit is always determined in the same way – it is income minus expenses. At the same time, if security is not the main activity of the company, then it does not generate revenue, and if so, then in order for this activity to make sense, it must reduce costs.
The economic effect of ensuring business security is to minimize or completely eliminate losses from threats. However, it should also be taken into account that implementing security measures also costs money, and therefore the true profit from security will be equal to the amount saved from implementing security threats, reduced by the cost of security measures.
One day, a conversation took place between the owner of a commercial bank and the head of the security service of his organization on the topic of the economic effect of security. The essence of this conversation most accurately reflects the role and place of security in the life of the organization:
- Security should not interfere with business.
— But you have to pay for security, and you have to pay for the lack of it.
The ideal security system is the golden mean between neutralized threats, resources spent on it, and business profitability.
Place of the information security service in the organization's management structure
The structural division responsible for ensuring information security may have different names. This can be a department, department, or even an information security department. Further, for the sake of unification, this structural division will simply be called the Information Security Service (SIB).The reasons for creating a SIB may vary. Let's highlight two main ones:
- Fear.
The company's management is aware that computer attacks or information leaks can lead to disastrous consequences, and makes efforts to neutralize them. - Ensuring compliance with legal requirements.
The current legal requirements impose obligations on the company to form an SIB, and top management makes efforts to comply with them.
In relation to credit institutions, the need for the existence of an SIB is fixed in the following documents:
- Decree of the Government of the Russian Federation No. 1119 of 01.11.2012 "On Approval of requirements for the protection of personal data when Processing them in Personal data Information systems".
- "Regulation on Information Security Requirements for Money Transfers and on the Procedure for the Bank of Russia to Monitor Compliance with Information Security Requirements for Money Transfers" (approved by the Bank of Russia on 09.06.2012 N 382-P) (as amended on 14.08.2014) (Registered with the Ministry of Justice of Russia on 14.06.2012 N 24575).
- "Regulation on Information security requirements in the payment system of the Bank of Russia "(approved by the Bank of Russia on 24.08.2016 N 552-P) (Registered with the Ministry of Justice of Russia on 06.12.2016 N 44582).
- Requirements for the cryptography license of the Federal Security Service of Russia: Decree of the Government of the Russian Federation No. 313 of 16.04.2012, Order of the FAPSI No. 152 of 13.06.2001 (SIB, as a cryptographic protection body).
- For banks with significant objects of key information infrastructure — FSTEC Order No. 235 of 21.12.2017 " On Approval of Requirements for Creating Security Systems for Significant Objects of Critical Information Infrastructure of the Russian Federation and Ensuring their Functioning "(Registered with the Ministry of Justice of the Russian Federation No. 50118 on 22.02.2018).
The functionality required from SIB is spelled out in the above-mentioned documents. The staff size is not strictly regulated, with the exception, perhaps, of the license requirements of the Federal Security Service of Russia for cryptography (at least 2 employees, but they may be in different divisions) and can be selected by the organization independently. To justify the size of the staff, it is recommended to use the document-Recommendations in the field of standardization of the Bank of Russia " Ensuring information security of organizations of the banking system of the Russian Federation. Resource support of information security "RS BR IBBS-2.7-2015"
From the point of view of the SIB's subordination, there is only one restriction prescribed in the above — mentioned provisions of the Central Bank of the Russian Federation - "The Information Security Service and the informatization (automation) service should not have a common supervisor", otherwise the organization remains free to choose. Let's consider typical options.
Table 1.
| Subordination | Features |
|---|---|
| SIB as part of IT | 1. The organization of protection is possible only against an external attacker. The main likely internal attacker is an IT employee. It is impossible to fight IT as part of an IT team. 2. Violation of the requirements of the Bank of Russia. 3. Direct dialogue with IT, easy implementation of information security systems |
| SIB as part of the security service | 1. Protection from both internal and external intruders. 2. SB — a single point of interaction between top management on any security issues. 3. The complexity of interaction with IT, since communication takes place at the level of the heads of IT and SAT, and the latter, as a rule, has minimal knowledge in IT. |
| SIB reports to the Chairman of the Management Board | 1. The SIB has maximum authority and its own budget. 2. An additional point of control and interaction is created for the Chairman of the Management Board, which requires a certain amount of attention. 3. Possible conflicts between the Security Service and the Security Service by areas of responsibility in the investigation of incidents. 4. A separate SIB can "politically" balance the powers of the Security Council. |
When interacting with other structural divisions and top management of the bank, the SIB of any organization has one common problem — proof of the need for its existence (financing).
The problem is that the amount of money saved from neutralized information security threats cannot be accurately determined. If the threat is not realized, then there is no damage from it, and if there are no problems, then there is no need to solve them.
To solve this problem, the SIB can act in two ways:
- Show economic significance
To do this, it needs to keep records of incidents and assess potential damage from their implementation. The total amount of potential damage can be considered saved money. In order to resolve disagreements on the amount of estimated damage, it is recommended to develop and approve a methodology for its assessment in advance. - Engage in internal PR
Ordinary employees of the organization usually do not know what the SIB does, and consider its employees to be idlers and charlatans who interfere with their work, which leads to unnecessary conflicts. Therefore, the SIB should periodically inform its colleagues about the results of its activities, talk about current threats to information security, conduct training and raise their awareness. Any employee of the company should feel that if they have a problem related to information security, they can contact the Information Security Service, and they will be helped there.
Practical aspects of ensuring security

We will highlight the practical aspects of security that must be communicated to top management and other structural divisions, as well as taken into account when building an information security system:
- Security is a continuous, never-ending process. The degree of security achieved with its help will fluctuate over time, depending on the harmful factors affecting it and the efforts aimed at neutralizing them.
- Security cannot be guaranteed after the fact, i.e. at the moment when the threat has already been realized. To neutralize a threat, the security process must begin before it is attempted.
- Most of the threats are anthropogenic in nature, meaning that organizations are threatened in one way or another by people. As computer forensics experts say: "It's not programs that steal, it's people who steal."
- Neutralizing threats should involve people whose security is ensured,
whether they are business owners or customers. - Security is derived from the corporate culture. The discipline required for implementing protective measures cannot be higher than the general discipline of the organization's work.
Summing up the intermediate result of the above, we note that the created system of information security of non-cash payments should have a practical focus and be cost-effective. The best way to achieve these properties is to apply a risk-based approach.
Risk management

Information security is just one of the areas of ensuring security (economic security, physical security, fire safety,...). In addition to information security threats, any organization is subject to other equally important threats, such as threats of theft, fires, fraud by unscrupulous customers, threats of violation of mandatory requirements (compliance), etc. etc.
Ultimately, an organization doesn't care what specific threat it suffers losses from, whether it's theft, fire, or computer hacking. The amount of losses (damage) is important.
In addition to the amount of damage, an important factor in assessing threats is the probability of their implementation, which depends on the specifics of the organization's business processes, its infrastructure, external malicious factors, and the countermeasures taken.
The characteristic that takes into account the damage and the probability of the threat being realized is called risk.
Note. A scientific definition of risk can be obtained in GOST R 51897-2011
Risk can be measured both quantitatively, for example, by multiplying damage by probability, and qualitatively. A qualitative assessment is made when neither the damage nor the probability is quantified. The risk in this case can be expressed as a set of values, for example, damage — "medium", probability - "high".
Assessing all threats as risks allows an organization to effectively use its available resources to neutralize exactly those threats that are most significant and dangerous for it.
Risk management is the main approach to building a comprehensive, cost-effective security system for an organization. Moreover, almost all banking regulations are based on the risk management recommendations of the Basel Committee on Banking Supervision.
Main threats and assessment of potential damage from their implementation

We will highlight the main threats inherent in the activities of making bank non-cash payments, and determine the maximum possible damage from their implementation.
Table 2.
| № | Threat | Maximum possible damage |
| 1 | Termination (prolonged shutdown) of an activity | Revocation of a banking license |
| 2 | Theft of funds | In the amount of the balance of funds on the accounts |
| 3 | Violation of mandatory business requirements established by the current legislation and agreements with the Bank of Russia | Revocation of a banking license |
Here, the analyzed activity includes a set of business processes:
- implementation of correspondent relations with partner banks and the Central Bank of the Russian Federation;
- making settlements with clients.
In the future, we will only consider issues related to ensuring the security of correspondent relations with the Bank of Russia. Nevertheless, the obtained results can be used to ensure security and other types of calculations.
Mandatory requirements for the IS system of non-cash payments

When considering the main threats, we estimated their damage, but did not estimate the probability of their implementation. The fact is that if the maximum possible damage is the same for all banks, then the probability of implementing threats will differ from bank to bank and depend on the applied protective measures.
One of the main measures to reduce the likelihood of information security threats will be:
- implementation of best practices in IT and infrastructure management;
- creation of a comprehensive information security system.
We will not talk about IT practices here, we will only touch on information security issues.
The main nuance that needs to be taken into account in ensuring information security is that this type of activity is rather tightly regulated by the state and the Central Bank. No matter how the risks are assessed, no matter how small the resources available to the bank, its protection must meet the established requirements. Otherwise, it will not be able to work.
Consider the information security requirements imposed on the business process of correspondent relations with the Bank of Russia.
Table 3.
Documents setting out the requirements | Penalty for non-compliance |
|---|---|
| Protection of personal data. Basis – payment documents contain personal data (full name of the payer / recipient, their address, details of the identity document) | |
| Federal Law No. 152-FZ of 27.07.2006 "On Personal Data" | Administrative Code of the Russian Federation Article 13.11, Administrative Code of the Russian Federation Article 13.12-up to 75 thousand rubles fine., Article 137 of the Criminal Code of the Russian Federation – up to 2 years of imprisonment |
| Decree of the Government of the Russian Federation No. 1119 of 01.11.2012 "On Approval of Requirements for the protection of personal data when Processing them in Personal Data Information Systems" | |
| Order of the FSTEC of Russia No. 21 of 18.02.2013 " On approval of the Composition and Content of organizational and technical measures to ensure the security of personal data when processing them in Personal data Information Systems "(Registered with the Ministry of Justice of Russia No. 28375 on 14.05.2013) | |
| Order of the Federal Security Service of Russia No. 378 of 10.07.2014 " On approval of the Composition and Content of Organizational and Technical measures to ensure the security of personal data when Processing them in Personal data information Systems using Cryptographic Information protection Tools Necessary to Meet the Requirements for Personal Data Protection established by the Government of the Russian Federation for each of the Security levels "(Registered with the Ministry of Justice of the Russian Federation 18.08.2014 N 33620) | |
| Bank of Russia Directive No. 3889-U of December 10, 2015 "On Identifying threats to the security of personal data Relevant to the processing of personal data in Personal data Information Systems" | |
| Ensuring information security in the national payment system. Foundation – a credit institution that performs money transfers is part of the national payment system. | |
| Federal Law No. 161-FZ of 27.06.2011 "On the National Payment System" | Clause 6 of Article 20 of Federal Law No. 395-1 of 02.12.1990 "On Banks and Banking Activities" – license revocation |
| Decree of the Government of the Russian Federation No. 584 of 13.06.2012 "On Approval of the Regulation on Information Protection in the Payment System" | |
| Regulation of the Bank of Russia No. 382-P of June 9, 2012 "On Information Security Requirements for Money Transfers and on the Procedure for the Bank of Russia to Monitor Compliance with Information Security Requirements for Money Transfers" | |
| Regulation of the Bank of Russia No. 552-P of August 24, 2016 "On Information Security Requirements in the Bank of Russia Payment System" | |
| Operational documentation for SCAD Signature SCSI | |
| Ensuring the security of the critical information infrastructure of the Russian Federation. Foundation – by virtue of Clause 8 of Article 2 of Federal Law No. 187-FZ of 26.07.2017, the bank is a subject of critical information infrastructure | |
| Federal Law No. 187-FZ of 26.07.2017 "On Security of Critical Information Infrastructure of the Russian Federation" | Criminal Code of the Russian Federation Article 274.1-up to 8 years of imprisonment |
| Decree of the Government of the Russian Federation No. 127 of 08.02.2018 "On Approval of the Rules for Categorizing Objects of Critical Information Infrastructure of the Russian Federation, as well as the list of indicators of criteria for the significance of objects of critical Information Infrastructure of the Russian Federation and their values" | |
| FSTEC Order No. 235 of 21.12.2017 " On Approval of Requirements for Creating Security Systems for Significant Critical Information Infrastructure Facilities in the Russian Federation and Ensuring their Functioning "(Registered with the Ministry of Justice of the Russian Federation No. 50118 on 22.02.2018) | |
| FSTEC Order No. 227 of 06.12.2017 " On Approval of the Procedure for Maintaining the Register of Significant Objects of Critical Information Infrastructure of the Russian Federation "(Registered with the Ministry of Justice of the Russian Federation No. 49966 on 08.02.2018) | |
| Decree of the President of the Russian Federation No. 620 of 22.12.2017 "On Improving the State System for Detecting, preventing and eliminating the consequences of computer attacks on Information Resources of the Russian Federation" | |
| Information security requirements established by the agreement on the exchange of electronic messages when transferring funds within the payment system of the Bank of Russia. Basis – this agreement is concluded by all credit institutions for electronic exchange of payment documents with the Bank of Russia. | |
| Standard E-mail exchange agreement with appendices. Documentation for AWP KBR, UTA (requirements for their use are reflected in clause 1. of Annex 3 to the Agreement) | Clause 9.5.4 of the Agreement – unilateral termination of the Agreement at the initiative of the Bank of Russia. |
We will also outline additional requirements for the organization of information security. These requirements will apply only to some banks and only in some cases:
- ONE HUNDRED BR IBBS. The standard and a set of accompanying documents are valid only if it is voluntarily accepted by the credit institution.
- PCI DSS. This standard will only apply if payment documents contain full non-masked payment card numbers (PAN).
- Corporate Information Security Policy. The requirements are relevant for large banking groups, where a single information security policy is established for all banks in the group and where each bank must develop internal documents based on it.
The final results of applying all these requirements should be an information security system that meets any of the listed documents. In order to create such a system, requirements are summarized in a single table and in cases where there are several similar requirements, the most stringent ones are selected.
There is an important caveat here: the requirements set out in regulatory documents, as a rule, do not contain strict specifics. They indicate what the security system should look like, what tools it should consist of, and what tactical characteristics it should have. An exception will be requirements that come from the operational documentation for the information security tools used, for example, for the SCAD Signature SCSI.
Consider, for example, a fragment of the requirements of FSTEC Order No. 21
As we can see, the requirements of AVZ.1 and AVZ.2 indicate that there should be anti-virus protection. These requirements do not regulate exactly how to configure it, on which network nodes to install it (the Letter of the Bank of Russia dated 24.03.2014 N 49-T recommends that banks have antivirus products from various manufacturers on their ARMas, servers, and gateways).
The situation is similar with computer network segmentation-a VMS requirement.17. The document only prescribes the need to use this practice for protection, but does not say how the organization should do this.
You can find out exactly how information security tools are configured and how security mechanisms are implemented from a private technical specification for an information security system formed based on the results of modeling information security threats.
Thus, a comprehensive information security system should be a set of protective business processes (controls in the English – language literature), built taking into account the implementation of mandatory requirements, current threats, and information security practices.
Part 4 - Overview of Threat Modeling Standards
In the previous publication of the series, we formed the basic requirements for the information security system for non-cash payments and said that the specific content of security measures will depend on the threat model.To form a high-quality threat model, it is necessary to take into account existing practices and practices on this issue.
In this article, we will conduct a rapid review of about 40 sources describing the processes of threat modeling and information security risk management. We will consider both state standards and documents of Russian regulators (FSTEC of Russia, FSB of Russia, Central Bank of Russia), as well as international practices.
Brief description of the threat modeling process
The end result of the threat modeling process should be a document-a threat model containing a list of significant (relevant) information security threats for the protected object.
When modeling threats, protected objects are usually considered as protected objects.:
- information systems;
- automated systems;
- informatization objects;
- business processes.
By and large, the threat model does not need to be presented in the form of a list. It can be a tree (graph), a mind map, or any other form of recording that allows specialists to work with it conveniently.
The specific composition of threats will depend on the properties of the protected object and the business processes implemented using it. Accordingly, one of the source data for modeling will be a description of the protected object itself.
If a certain hypothetical object is considered, then a typical (basic) threat model is formed. If a real object is considered, then a private threat model is formed.
When modeling threats, in addition to describing the protected object, specialists must have knowledge about the threats themselves.
In practice, this knowledge can be gleaned from:
- researchers reports on detected vulnerabilities that can be used to implement threats;
- computer forensics reports on investigations of real-world computer attacks;
- reports of companies specializing in information security that analyze the current situation in the field of computer security;
- publications in the media devoted to computer crimes;
- databases or threat catalogs that list threats grouped by one or another principle.
The initial stage of the modeling process will be threat identification, i.e. selecting the largest possible list of threats that can at least theoretically affect the protected object.
When implementing this stage, nature plays a cruel joke with information security specialists. The problem is that human memory is associative, and we can not take and extract all the contents from it, for example, to remember all possible threats.
In order to create a list of all possible threats, various tricks are used that allow specialists to ask themselves certain questions or use the principles by which threats will be extracted from memory and recorded. Examples of such techniques can include threat classifiers, threat trees, or patterns of typical computer attacks. We'll talk about these methods below.
Once the list of all possible threats is formed, it is filtered so that only threats that are relevant to the organization are left in the end. The filtering process is usually performed in several iterations, each of which discards threats based on one or another feature.
They start with a sign indicating that violators have the capabilities (resources) to implement threats. To determine it, first create a special document-a model of the violator, in which possible violators are identified and their capabilities are determined. Then they correlate the previously received threats with the intruder's model and discard all threats that are beyond the capabilities of potential intruders.
The next sign for filtering threats is the sign that the risk is insignificant. First, the organization determines the level of risk that it considers insignificant. Then it evaluates the risk from the implementation of each threat and, if it is less than or equal to this level, the threat is discarded.
Thus, after filtering is completed, a threat model will be obtained that contains information security threats that are significant (relevant) for the organization.
Threat identification methodology – "threat classifiers"
Most information security threats can be grouped (classified) by one or another attribute. The resulting classification schemes can be used by specialists as questionnaires to their memory, from which they will extract threats.Take, for example, the problem of modeling threats to the security of personal data (PD) processed in personal data information systems (ISPDn).
The FSTEC of Russia in 2008 issued a methodological document for this purpose – the Basic Model of PD threats This document contains many classification schemes, of which we will consider the only one as an example — the classification of threats by "source of threat".
A specialist building a private threat model can use this scheme, ask yourself the question: "What threats to personal data will come from the actions of an internal intruder?" and record these threats. Then ask the following question: "How can an external intruder attack personal data?" and so on. Such a series of questions allows the specialist to describe all the threats known to him, without forgetting anything.
Threat identification methodology – "threat tree"
When using this technique, an information security specialist puts himself in the place of the intruder and begins to think about how he would attack the protected object.At the beginning, a high-level threat is formulated, which will be the root of the future tree.
Then the specialist begins to decompose this threat into low-level ones, the implementation of which can lead to the implementation of the threat in question. To do this, they may ask questions about how or how the threat under investigation can be implemented.
The threats received in this case are children of the one under consideration and are recorded in the tree as its descendants. Then they, in turn, are also decomposed, and so on until the required level of detail is reached.
This approach has long been known in engineering and is used to build fault trees, the formation of which is standardized in GOST R 51901.13-2005 (IEC 61025:1990) Risk management. Analysis of the fault tree.
To illustrate the use of "threat trees", we will consider the formation of a threat model for an informatization object, which is an isolated computer that is not connected to a computer network. Let's assume that this object processes important information that needs to be secured.
As a high-level threat, we define the following: violation of the security properties of protected information.
Generally accepted security properties are confidentiality, integrity, and availability. Thus, child threats will be:
- violation of the confidentiality of protected data;
- violation of the integrity of protected data;
- violation of the availability of protected data.
We decompose the threat of "violation of the confidentiality of protected data".
Let's ask ourselves the question: "How can this threat be implemented?" and write down the following options as an answer::
- disclosure of protected data by persons authorized to process it;
- unauthorized access to protected data by unauthorized persons;
- leakage of protected data through technical channels.
We will do the same with the threat of "violation of the integrity of protected data". It can be decomposed into:
- damage to protected data due to actions of persons authorized to process it;
- damage to protected data due to malicious code;
- damage to protected data due to failures and failures of the computer on which it is processed.
The decomposition of the threat "violation of the availability of protected data" can be represented by the following threats::
- destruction of protected data due to malicious code (cryptolockers);
- destruction of protected data due to failure of the hard disk of the computer on which it is stored;
- violation of the operating conditions of an informatization object, which makes it impossible for personnel to work with it.
As a result, we get the following tree:
As we can see, even such a primitive model that we have just built is quite cumbersome when it is displayed graphically. Therefore, "threat trees" are mostly documented as hierarchical lists.
Threat identification methodology "templates of typical attacks"
This technique is based on the idea that when performing computer attacks, attackers always perform a certain similar sequence of actions, which can be called a template for a typical attack.
One of the most well-known computer attack patterns at the moment is the kill chain pattern described by Lockheed Martin Corporation, which includes 7 stages:

Stage 1. Intelligence-collecting data about the attacked object.
Stage 2. Weaponization – development of tools (malicious code) for conducting an attack.
Stage 3. Delivery – delivery of malicious code to the target object.
Stage 4. Penetration (Exploitation) – using any vulnerability of the node of the attacked object to run malicious code.
Stage 5. Installation – installation of a hidden remote access system on a compromised node.
Stage 6. Obtaining control (C2) - organizing a remote access channel for intruders to the compromised node.
Stage 7. Actions – performing the actions for which the attack was carried out.
The research organization MITRE, slightly changing the names of the stages, called this template-Cyber Attack Lifecycle.

In addition, MITRE expanded the description of various stages and formed a matrix of typical tactics of attackers at each stage. This matrix was named ATT&CK.

(clickable)
Although the above matrix is not universal, it still allows you to describe the actions taken by attackers when committing a large number of real attacks.
From the point of view of threat modeling, the template of a typical attack can be considered as a threat classifier, and the matrix of typical tactics can be considered as a significant fragment of the threat model.
Only the last stage of the template – "Actions" - will require clarification, which is what the attack was carried out for, and the stages themselves can be supplemented with tactics that were not taken into account.
Documents of the FSTEC of Russia on modeling threats to personal data in 2008.
- FSTEC's Basic PD Threat Model, 2008
- Methodology for determining actual personal data threats in 2008
Both documents are methodological, that is, they are not required to be applied, but they reveal how, in the opinion of the FSTEC of Russia, the problem of modeling personal data security threats should be solved.
The FSTEC Basic Model of Personal Data Threats, 2008 contains unified source data on security threats to personal data processed in the ISPDn related to:
- with the interception (removal) of personal data through technical channels for the purpose of copying or illegal distribution;
- with unauthorized, including accidental, access to the ISPDN for the purpose of modifying, copying, illegally distributing personal data or destructive effects on the elements of the ISPDn and the personal data processed in them using software and hardware for the purpose of destroying or blocking personal data.
Sets a formal description of threats:
- threat of leaks through technical channels := < source of threat>, < medium of distribution of PD and impacts / receiver of an informative signal / transmitter of an impacting signal>, <carrier of PD>
- the threat of NSD := < threat source>, <software or hardware vulnerability>, <method of threat implementation>, <target of impact>, <unauthorized access>.
- NSD threat in ISPDn: = < threat source>, <ISPDn vulnerability>, <method of threat implementation>, <object of influence (program, protocol, data, etc.)>, <destructive action>.
- Denial of service threat: = <threat source>, <ISPDn vulnerability>, <method of threat implementation>, <object of impact (PD carrier)> , <immediate result of the threat implementation (buffer overflow, blocking of the processing procedure," looping " of processing, etc.)>;
- PMV threat in ISPDn: = < malware class (indicating the environment)>, <threat source (malware carrier)> , <infection method>, <target of impact (boot sector, file, etc.)>, <description of possible destructive actions>, <additional information about the threat (residency, speed of distribution, polymorphism, etc.)>.
The following abbreviations were used to formally describe threats::
ISPDn – personal data information system.
NSD – unauthorized access.
PMV – software and mathematical impact (introduction of malicious programs).
The document contains classification criteria for threats and vulnerabilities, as well as malware. A small catalog of typical threats related to leaks through technical channels and unauthorized access is provided. A typical model of violators is given and their capabilities are determined.
The methodology for determining actual threats of the 2008 PD defines an algorithm that can be used to filter threats based on insignificant risk. To do this, the methodology provides methods for determining the possibility of implementing a threat (probability), an indicator of the threat's danger (damage), and rules for classifying a security threat as not relevant (having an insignificant risk).
FSTEC documents on threat modeling in State Information Systems (GIS) and the FSTEC Threat Database.
- Methodological document of the FSTEC of Russia. Information security measures in state information systems (approved by the FSTEC of Russia on 11.02.2014)
- Draft methodological document of the FSTEC of Russia. Methodology for determining information security threats in information systems
- Threat Database of the FSTEC of Russia (bdu.fstec.ru).
Methodological document of the FSTEC of Russia. Information security measures in state information systems (approved by the FSTEC of Russia on 11.02.2014). Information security threats (UBI) are determined based on the results of assessing the capabilities (potential, equipment and motivation) of external and internal violators, analyzing possible vulnerabilities in the information system, possible ways to implement information security threats and the consequences of violating information security properties (confidentiality, integrity, availability).
Formal description of the threat to information security:
UBI: = [capabilities of the intruder; vulnerabilities of the information system; method of implementing the threat; consequences of implementing the threat].
The capabilities (potential) of violators are divided into three groups:
- An intruder with a basic potential.
- Intruder with basic enhanced potential
- High-potential intruder
An explanation of the capabilities of violators is given in the draft methodological document of the FSTEC of Russia. Methodology for determining information security threats in information systems.
Vulnerabilities are described and classified using national standards:
- GOST R 56545-2015 Information security. Vulnerabilities of information systems. Rules for describing vulnerabilities
- GOST R 56546-2015 Information security. Vulnerabilities of information systems. Classification of information system vulnerabilities
The vulnerabilities themselves, how threats are implemented, and possible damage are listed in the threat database of the FSTEC of Russia.
Methodological recommendations of the Federal Security Service of Russia on modeling personal data security threats
- "Methodological recommendations for the development of regulatory legal acts defining threats to personal data security that are relevant when processing personal data in personal data information systems used in the implementation of relevant types of activities" (approved by the Federal Security Service of Russia on 31.03.2015 N 149/7/2/6-432).
The guidelines identify the main threats to personal data that can be neutralized only with the help of SCSI. These include:
- transfer of personal data through communication channels that are not protected from interception of the information transmitted by the violator or from unauthorized actions on this information (for example, when transmitting personal data over public information and telecommunications networks);
- storage of personal data on data carriers, unauthorized access to which by the violator cannot be excluded using non-cryptographic methods and methods.
The document also defines a classification of violators capabilities:
| N | Generalized capabilities of attack sources |
|---|---|
| 1 | Ability to independently create attack methods, prepare and conduct attacks only outside the controlled zone |
| 2 | The ability to independently create attack methods, prepare and conduct attacks within the controlled zone, but without physical access to the hardware (hereinafter referred to as AS) on which the SCSI and their operating environment are implemented |
| 3 | The ability to independently create attack methods, prepare and conduct attacks within a controlled zone with physical access to the automated control systems where the SCSI and their operating environment are implemented |
| 4 | Ability to attract specialists who have experience in the development and analysis of SCSI (including specialists in the analysis of linear transmission signals and signals of spurious electromagnetic radiation and SCSI crosstalk) |
| 5 | Ability to attract specialists with experience in the development and analysis of SCSI (including specialists in the use of undocumented application software capabilities to implement attacks) |
| 6 | Ability to attract specialists with experience in the development and analysis of SCSI (including specialists in the use of undocumented capabilities of the hardware and software components of the SCSI operating environment for attacks) |
Bank of Russia documents on information security risks
- Letter of the Central Bank of the Russian Federation No. 197-T dated December 7, 2007 " On risks in remote banking services”
- Bank of Russia Directive No. 3889-U of December 10, 2015 "On Identifying threats to the security of personal data Relevant to the processing of personal data in Personal data Information Systems"
- Recommendations in the field of standardization of the Bank of Russia RS BR IBBS-2.2-2009. "Methodology for assessing information security breach risks"
Letter of the Central Bank of the Russian Federation No. 197-T dated December 7, 2007 "On risks in remote banking services" contains a list of typical threats to remote banking systems and their clients, including:
- Implementation of DoS / DDoS attacks against RBS servers.
- Theft of personal information of bank customers through phishing via email.
- Theft of payment card details using skimming attacks and fake ATMs.
- Theft of customer access details to RBS systems using social engineering and telephone fraud.
The Bank of Russia's Directive No. 3889-U of December 10, 2015 "On determining threats to the security of personal data Relevant to the processing of personal data in personal data information systems" contains an industry-specific list of threats to the security of personal data, including the following threats:
- threat of unauthorized access to personal data by persons with authority in the personal data information system, including during the creation, operation, maintenance and (or) repair, modernization, decommissioning of the personal data information system;
- threat of exposure to malicious code external to the personal data information system;
- threat of using social engineering methods to persons with authority in the personal data information system;
- threat of unauthorized access to alienated personal data carriers;
- threat of loss (loss) of personal data carriers, including portable personal computers of users of the personal data information system;
- threat of unauthorized access to personal data by persons who do not have authority in the personal data information system, using vulnerabilities in the organization of personal data protection;
- threat of unauthorized access to personal data by persons who do not have authority in the personal data information system, using vulnerabilities in the software of the personal data information system;
- threat of unauthorized access to personal data by persons who do not have authority in the personal data information system, using vulnerabilities in ensuring the protection of network interaction and data transmission channels;
- threat of unauthorized access to personal data by persons who do not have authority in the personal data information system, using vulnerabilities in ensuring the protection of computer networks of the personal data information system;
- threat of unauthorized access to personal data by persons who do not have authority in the personal data information system, using vulnerabilities caused by non-compliance with the requirements for the operation of cryptographic information protection tools.
Recommendations in the field of standardization of the Bank of Russia RS BR IBBS-2.2-2009. "Methodology for assessing information security breach risks"
The document suggests the following risk assessment procedures::
Procedure 1. Determination of the list of types of information assets for which the procedures for assessing the risks of an information security breach are performed (hereinafter referred to as the area of assessing the risks of an information security breach).
Procedure 2. Determining the list of types of environmental objects corresponding to each of the types of information assets in the field of information security risk assessment.
Procedure 3. Identify sources of threats for each of the types of environment objects defined in procedure 2.
Procedure 4. Determination of the information security threat SVR in relation to the types of environmental objects defined in the framework of the procedure 2.3.
Procedure 5. Determination of the STP of an information security breach for the types of information assets in the information security risk assessment area.
Procedure 6. Assessment of information security breach risks.
The degree of risk tolerance is proposed to be assessed using the "classical" risk assessment table, which takes into account the probability and possible damage.
Here SVR is the degree of possibility of implementing the threat, and STP is the severity of the consequences.
The recommendations also contain a small catalog of threats, divided by class.
Class 1. Sources of information security threats related to adverse events of natural, man-made, and social nature
Class 2. Sources of information security threats related to the activities of terrorists and persons committing crimes and offenses
Class 3. Sources of information security threats related to the activities of suppliers/providers/partners
Class 4. Sources of information security threats related to failures, failures, destruction/damage of software and hardware
Class 5. Sources of information security threats related to the activities of internal information security violators
Class 6. Sources of information security threats related to the activities of external information security violators
Class 7. Sources of information security threats related to non-compliance with the requirements of supervisory and regulatory authorities and current legislation.
National standards of the Russian Federation (GOST)
- GOST R 51275-2006. Information protection. An informatization object. Factors affecting the information. General provisions
- GOST R ISO / TO 13569-2007. Financial services. Recommendations for information security
- GOST R 56545-2015 Information security. Vulnerabilities of information systems. Rules for describing vulnerabilities
- GOST R 56546-2015 Information security. Vulnerabilities of information systems. Classification of information system vulnerabilities
- GOST R 53113.1-2008 Information Technology (IT): Protection of information technologies and automated systems from information security threats implemented using hidden channels. Part 1. General provisions
- GOST R 52448-2005 Information security. Ensuring the security of telecommunication networks. General provisions
- GOST R ISO / IEC 27005-2010. Information technology. Methods and tools for ensuring security. Information security risk management
GOST R 51275-2006. Information protection. An informatization object. Factors affecting the information. General provisions
This GOST is ideologically related to GOST R 50922-2006 Information security. Basic terms and definitions, the methodological document " Special requirements and recommendations for the protection of confidential information (STR-K) "(DSP) and current documents on certification of informatization objects. The document contains a classification of factors that affect information that can be interpreted as threats to information security.
GOST R ISO / TO 13569-2007. Financial services. Information Security Recommendations
Appendix " C " of this standard contains an example of information security risk assessment for a credit and financial institution. To do this, it is proposed to analyze among the main objects of malicious impacts, including personnel, hardware, business applications, communication systems, software tools and operating systems. Risk damage is assessed as financial losses, reduced productivity, reputational damage, and total damage.
GOST R 56545-2015 Information security. Vulnerabilities of information systems. Rules for describing vulnerabilities and GOST R 56546-2015 Information security. Vulnerabilities of information systems. Classification of information system vulnerabilities are used to describe vulnerabilities in information systems. The standards are applied in conjunction with the fundamental GOST R 50922-2006 Information Security. Basic terms and definitions.
The standards provide a classification of information system vulnerabilities, which contains three classification features:
- by region of origin;
- by types of IP deficiencies;
- at the place of occurrence (manifestation).
The vulnerabilities themselves are proposed to be described in the form of a passport containing the following sections:
- Name of the vulnerability.
- ID of the vulnerability.
- Ids of other vulnerability description systems.
- A brief description of the vulnerability.
- Vulnerability class.
- Name of the software and its version.
- The service (port) that is used for software operation.
- Software programming language.
- Type of fault.
- Location of vulnerability occurrence (manifestation).
- ID of the fault type.
- Name of the operating system and type of hardware platform.
- Date when the vulnerability was detected.
- The author who published information about the identified vulnerability.
- Method (rule) for detecting the vulnerability.
The standards suggest using OVAL as the language of vulnerability detection rules.
GOST R 53113.1-2008 Information Technology (IT): Protection of information technologies and automated systems from information security threats implemented using hidden channels. Part 1. General provisions
The standard describes threats associated with hidden channels, which are defined as communication channels that are unintended by the developer of information technology and automated systems and can be used to violate the security policy.
GOST R 52448-2005 Information security. Ensuring the security of telecommunication networks. General provisions
This document is a methodological document for telecom operators and contains a general scheme of actions to protect communication networks.
It is proposed to use GOST R 51275-2006 as the basis of the threat modeling process. Information protection. An informatization object. Factors affecting the information. General provisions. The standard provides a model of alleged violators.
A distinctive feature of this document is that in addition to the classical properties of information security, such as confidentiality, integrity, and availability, the standard also considers accountability.
Under accountability, the standard defines a property that provides unambiguous tracking of network activities of any object. Violation of accountability — denial of actions in the network (for example, participation in a perfect communication session) or forgery (for example, creating information and claims that were allegedly received from another object or sent to another object).
GOST R ISO / IEC 27005-2010. Information technology. Methods and tools for ensuring security. Information security risk management
This standard is part of a group of information security standards, often referred to as ISO 27K. The document focuses on management procedures for managing information security risks.
Appendix C provides examples of typical threats, and Appendix D provides typical vulnerabilities.
NIST Special Publications
- NIST SP 800-30. Guide for Conducting Risk Assessments
- NIST SP 800-39. Managing Information Security Risk
NIST SP 800-30. Guide for Conducting Risk Assessments
The document focuses on risk management issues at the organization's management level.

NIST SP 800-39. Managing Information Security Risk
This document describes the methodology for managing enterprise-level information security risks. The main goal of the methodology is to link the information security system with the mission and goals of the organization

OCTAVE (Operationally Critical Threat, Asset, and Vulnerability Evaluation)
OCTAVE is an information security risk management methodology, the main purpose of which is to ensure that the goals of information security processes meet the goals and objectives of the organization. The methodology consists of 8 main steps:
- Definition of risk measurement criteria (Establish Risk Measurement Criteria).
- Develop an Information Asset Profile.
- Identification of storage / processing / transfer locations for information assets (Identify Information Asset Containers).
- Identifying groups of high-level information security threats (Identify Areas of Concern)
- Identification of information security threats (Identify Threat Scenarios)
- Identification of information security risks
- Information Security Risk Analysis (Analyze Risks)
- Selection of measures for information security risk management (Select Mitigation Approach)
The threat tree methodology is used to identify threats performed in step 5.
Trike Methodology
Trike is based on a risk-based approach to building information security and is designed for conducting information security audits and building threat models.Distinctive features of this methodology are:
- its initial focus is on using specialized software to build threat models;
- using "attack trees" to describe security threats;
- using standard attack libraries.
Microsoft Threat Modeling techniques and publications
Microsoft uses the Security Development Lifecycle methodology to develop secure software. This methodology is an extension to the "classic" cascade model of software development ("waterfall"), which introduces additional security-related steps. At the "design" stage, it is proposed to conduct threat modeling.

We suggest using several approaches to identify threats:
- STRIDE methodology;
- using threat classifiers;
- using threat trees and attack patterns.
The STRIDE methodology is a classification scheme for describing attacks based on the type of exploits used to implement them or the attacker's motivation.
STRIDE is an acronym for the first letters:
- S poofing Identity – "identity substitution". The intruder pretends to be a legitimate user (for example, stole the username/password) and performs malicious actions on their behalf.
- Tampering with Data – "data forgery". The intruder fakes data that is available to them when the Web application is running. These can be cookies, elements of HTTP requests, and so on.
- Renaudiation – "refusing transactions". An intruder can reject transactions when the Web application does not conduct sufficient audit of user actions.
- Information Disclosure – "disclosure of sensitive information". The violator tries to disclose personal data of other users, authentication information, etc.
- D enial of Service – "denial of service".
- E level of Privilege – "increase of privileges".
After identifying threats, SDL suggests evaluating the risks they generate. The DREAD method can be used for this purpose.
The name of the DREAD method is also an acronym for the first letters of the risk assessment categories:
- Damage Potential – how much damage will be done if the threat is realized?
- R eproducibility – how easy is it to implement a threat?
- E xploitability – what is required to perform an attack?
- A perfect Users – how many users can be affected by the attack?
- D iscoverability – how easy is it for an attacker to detect a threat?
The risk itself is estimated by the formula:
Risk_DREAD = (DAMAGE + REPRODUCIBILITY + EXPLOITABILITY + AFFECTED USERS + DISCOVERABILITY) / 5,
where the value of composite elements varies from 0 to 10. For example, the Damage Potential value can be defined as:
- 0 = no damage will occur;
- 5 = only some part of the system or a limited amount of data will be damaged;
- 10 = the entire system will be affected or all data will be destroyed.
Threat directories
- OWASP Top10
Contains a description of the main threats to Web applications. - The OWASP Testing project
provides recommendations for testing Web application security. - WASC Threat Classification
Another source that describes typical attacks on Web applications. - Bluetooth Threat Taxonomy
Contains data on vulnerabilities in the Bluetooth protocol. - ENISA Threat Landscape
Annual report of the European Union Cybersecurity Agency, containing information on the main threats. - ENISA Threat Taxonomy
Another document of the EU cybersecurity agency, containing a classification and description of the main information security threats. - BSI Threat catalogue
Catalog of the German Federal Information Security Agency, which contains descriptions of mostly physical threats (fires, theft, ionizing radiation, etc.). - Open Threat Taxonomy
An open source project that includes software and various classification schemes in JSON format used for exchanging data on information security threats. - US DoD Comprehensive Military Unmanned Aerial Vehicle smart device ground control station threat model
A document of the US Department of Defense containing a threat model for ground-based unmanned aerial vehicle control stations. - VoIP Security and Privacy Threat Taxonomy
A document containing a description of VoIP threats. - Mobile Threat Catalogue
NIST information resource, which includes an extensive catalog of threats related to the use of mobile devices and technologies. - ATT&CK
Matrix of techniques and tactics used by real violators in hacking information systems. - Recommendations in the field of standardization of the Bank of Russia RS BR IBBS-2.2-2009. "Methodology for assessing information security breach risks"
A Bank of Russia risk management document containing a description of typical threats in the appendix. - Database of Information Security Threats of the FSTEC of Russia
The main catalog of threats and vulnerabilities of the FSTEC of Russia. It is used for modeling threats in state and municipal information systems. - GOST R 51275-2006. Information protection. An informatization object. Factors affecting the information. General provisions
A standard describing typical information security threats. Much attention is paid to threats related to information leaks through technical channels. - FSTEC's Basic PD Threat Model, 2008
A document of the FSTEC of Russia containing classification schemes of typical threats to personal data security, as well as a description of a small number of the most likely threats.
Part 5 - 100 + thematic links about bank hacks
When preparing materials for the following articles, a fairly extensive collection of links to topics was accumulated:- hacker attacks on banks,
- technical analysis of bank hacks,
- overview of typical vulnerabilities in banking networks,
- judicial practice,
- analysts, forecasts, and other articles on banking security.
At some point in time, the number of selected materials has grown into quality, so this selection may be of interest in itself.
Publications in the media about hackers and incidents
2015
1. "Hackers from Gorny Altai stole tens of millions from the bank”" –altapress.ru, 20152. "Hackers from Moscow face 10 years for stealing 20 million rubles from a bank”, – sobesednik.ru, 2015
2016
3. "Hackers stole a billion rubles from four banks using a bot”, – Life.ru, 20164. Plot: "Theft from the Russian International Bank (RMB)"
a) "Hackers stole more than half a billion rubles from the correspondent account in the Central Bank," — interfax.ru, 2016
b) "Russian International Bank named the amount of funds stolen by hackers”, — rbc.ru, 2016
5. Plot: "Theft from Metallinvestbank"
a) "Hackers withdrew 677 million rubles. from the accounts of Metallinvestbank", – rbc.ru, 2016
b) ” Due to a hacker attack, Metallinvestbank lost 200 million rubles, " — ria.ru, 2016
c) "Metallinvestbank press release on theft", — metallinvestbank.ru, 2016
d) "Hacker-style robbery”, — kommersant.ru, 2017
6. "ABS didn't work”, – kommersant.ru, 2016
7. "Hackers stole almost 2 billion rubles from banks with the help of" letters from the Central Bank " – RBC.ru, 2016
8. "A million in a couple of minutes. How hackers rob banks around the world”, — 21.by, 2016
9. "Hackers" accused of embezzling more than 2.6 million rubles from bank accounts in various regions of the country will appear in court in the Sverdlovsk region" - Prosecutor General's Office of the Russian Federation, 2016
10. Plot: Hacker group Lurk
) "Lurk Banking Trojan: specially designed for Russia", — Securelist.ru, 2016
b) "Employees of the Russian Ministry of Internal Affairs and the Federal Security Service of Russia detained Internet hackers”, - Ministry of Internal Affairs of Russia, 2016
c) "Hunting for Lurk”, — Securelist.ru, 2016
11. "The court recovered 470 million rubles from the processing company UCS”, — vedomosti.ru, 2016
2017
12. "From Utah to the Yenisei: hackers attack US and Russian banks”, — Газета.ги, 201713. "Group-IB assessed the scale of activity of Russian-speaking hackers MoneyTaker”, — rbc.ru,2017
14. "The co-founder of Group-IB spoke about those who committed a cyber attack on Russian banks”" — rbc.ru, 2017
15. Plot: "Theft from the bank "Globex"
a) "Hackers came running to SWIFT”, — kommersant.ru, 2017
b) "Hackers came to Globex, — kommersant.ru, 2017
c) "Hackers stole $1 million from a VEB subsidiary bank”, — vedomosti.ru, 2017
16. "Hacker attacks were grouped together”, — Коммерсант.ги, 2017
17. "Digital Security denies Zeronights member's connection to MoneyTaker", — anti-malware.ru, 2017
18. Plot: A group of 14 hackers robbing banks
a) "A boxer from Ukraine led a group of hackers who stole 1 billion rubles from banks”" — Life.ru, 2016
b) "The hacker's remorse program worked”" — kommersant.ru, 2017
c) "The court breaks into a hacker network”,- kommersant.ru, 2017
2018
19. "Hackers stole hundreds of millions from banks in Mexico”, — SecurityLab.ru, 201820. Plot: "Criminal group from Volzhsky"
a) "A hacker who stole funds from bank cards was detained in Volzhsky”" - SecurityLab.ru, 2018
b) "Hackers earned up to half a million a day”, — Коммерсант.ги, 2018
21. Plot: "Preparing for an attack on Russian payment systems"
a) "In Seversk, a hacker was convicted for preparing an attack on Russian payment systems”" — SecurityLab.ru, 2018
b) "A cyberattack on Russian electronic payment systems was prevented in Tomsk”, — ib-bank.ru, 2018
22. "In the Stavropol Territory, a hacker was detained for hacking ATMs and stealing funds”" - SecurityLab.ru, 2018
23. "In Saratov, a hacker stole more than 380 thousand rubles using a phishing site”, — SecurityLab.ru, 2018
24. "St. Petersburg hacker stole funds from bank cards”, — SecurityLab.ru, 2018
25. "Ghost hackers steal money from the Central Bank”, — dailystorm.ru, 2018
26. "Novice hackers have teachers on hacking ATMs," — dni24.com, 2018
27. Plot: "Arrest of the leader of the criminal group Carbanak / Anunak / Cobalt"
) “Mastermind behind eur 1 billion cyber bank robbery arrested in spain”, — Европол, 2018 + (here)
b) "A Ukrainian hacker, allegedly the leader of Carbanak, has been arrested," -SecurityLab.ru, 2018
c) "The leader of Carbanak got caught on unwillingness to pay for the car on time”, — SecurityLab.ru, 2018
28. Plot: "The continuation of the activity of the criminal group Cobalt after the arrest of its leader"
a) "Group-IB: Despite leader's arrest, Cobalt group continues attacks on banks” - Group-IB, 2018
b) "The arrest of the leader did not stop the activities of the Cobalt group: hackers attacked major banks in Russia and the CIS”" — xakep.ru, 2018
29. "Cybercriminals who stole funds from bank customers have been convicted in Moscow —" SecurityLab reports.Ru, 2018
30. "PIR Bank lost more than 58 million rubles as a result of a cyber attack —" - SecurityLab.Ru, 2018
31. "The investigative bodies of the Ministry of Internal Affairs of Russia sent to the court a case on embezzlement of funds from bank cards of citizens", - The Ministry of Internal Affairs of Russia, 2018
32. "Cyber fraudsters convicted in Moscow for stealing money through online banking accounts” - Interfax news agency, 2018
33. Plot: "Theft from the" PIR Bank "
a) "PIR for hackers", — kommersant.ru, 2018
b) "How do you like this, Carbanak?", — Gorup-ib.ru, 2018
34."The Prosecutor's Office of the Republic of Bashkortostan sent a criminal case to the court on the fact of theft by hackers of more than 8 million rubles”" - the Prosecutor General's Office of the Russian Federation, 2018
35. "In the US, a court has charged 3 members of the hacker group Carbanak", — SecurityLab.ru, 2018
36. "Yekaterinburg hackers stole 1.2 billion rubles from banks," — SecurityLab.ru, 2018
37. "In Rostov, a hacker stole more than 1 million rubles from an ATM", — SecurityLab.ru, 2018
38. "Hackers have withdrawn about $ 100,000 from the Housing Finance Bank," RIA Novosti, 2018
Technical analysis of incidents
2014
1. Report: "COMPUTER FORENSIC INVESTIGATION OF {mobile} BANKING TROJAN", - Zeronights 2014, Boris Ivanov2015
2. Report: "Technical report on the activities of a criminal group engaged in targeted attacks — Anunak” – - Group-IB, 2015 (+ article)3. Report: "Attacks on brokerage and settlement systems”, - Group-IB, 2015
4. Big Bank Heist: The Carbanak APT campaign, – securelist.ru, 2015 (+ english report)
2016
5. "The number of APT bank robberies using Metel, GCMAN, and Carbanak 2.0 attacks is increasing," – securelist.ru, 20166. Report: "Buhtrap: Evolution of targeted attacks on banks”, - Group-IB, 2016
7. Отчет: “Cobalt snatch”, — Positive Technologies, 2016
2017
8. Report: "Cobalt strikes back: new attacks on financial institutions”, - Positive Technologies, 20179. "Following the trail of Cobalt: tactics of a logical attack on ATMs in the investigation of Group-IB”,-Group-IB company blog on habr.com, 2017
10. "Secrets of Cobalt As the Cobalt Group overcomes security measures”, - Group-IB, 2017
11. "MoneyTaker: Group-IB Stealth hunt declassifies hackers attacking banks in the US and Russia” - Group-IB, 2017
12. "Lazarus Technologies of espionage and targeted attacks by pro-government hackers from North Korea and unknown details of their operations in the Group-IB report "Lazarus: Architecture, Tools, attribution", - Group-IB, 2017
13. Attacks on ATMs on the example of GreenDispenser: organization and technology”, - Positive Technologies, 2017
14. "The Silence — a new targeted attack on financial institutions", — Securelist.ru, 2017
15. "TwoBee Financial Campaign", — Securelist.ru, 2017
2018
16. "Big difference: Cobalt vs MoneyTaker What is the difference between the two most active criminal groups”, - Group-IB, 201817. "New attacks on banks” - Positive Technologies, 2018
18. Webinar: "Research on targeted attacks on financial institutions”, - Positive Technologies, 2018 (+ presentation)
19. "Attacks on industrial enterprises using RMS and TeamViewer", — Securelist.ru, 2018
20. "Hackers attack banks using Microsoft Publisher files", — SecurityLab.ru, 2018
Forecasts and reviews
2016
1. "Financial Stability Review II-III quarters of 2016", - Bank of Russia, 20162017
2. “Hi-Tech Crime Trends 2017”, — Group-IB, 2017 (+ this report is located on an external resource)3. "Report of the Center for Monitoring and Responding to Computer attacks in the Credit and Financial Sector of the Main Directorate for Information Security and Protection of the Bank of Russia: June 1, 2016-September 1, 2017", - FinCERT of the Central Bank of the Russian Federation, 2017
4. "The main types of attacks in the credit and financial sector in 2017”, - FinCERT of the Central Bank of the Russian Federation, 2017
5. "Review of unauthorized money transfers in 2017”, - FinCERT of the Central Bank of the Russian Federation, 2017
6. "Cybercriminals against Financial institutions: what to expect in 2018", — Securelist.ru, 2017
7. Webinar: "Current cyber threats-2017: trends and forecasts”, - Positive Technologies, 2018 (+ report)
2018
8. "Financial cyber threats in 2017”, — Securelist.ru, 2018Judicial practice
1. "Materials of court proceedings between JSC Kemsotsinbank and other banks through which the money stolen from it was cashed" - Arbitration and Appeal Courts, 2017-18 (here and here)
Regular reviews and thematic resources
1. "Crimes in the banking sector", – amulet-group.ru2. "Archive securelist.ru, category "Attack on banks", — securelist.ru
3. FinCERT of the Bank of Russia, — Bank of Russia
4. "Investigations of high-tech crimes”, - Rubricator on the site Group-IB.ru
5. The story " Hacker attacks on Russian banks”, - RIA Novosti
6. Threat Actor Map
7. Category: "Burglary guards", — Komersant.ru
8. "Rubricator: Cybercrime on the official website of the Ministry of Internal Affairs of Russia" — - Ministry of Internal Affairs of Russia
9. Periodic reports: State of Crime — Ministry of Internal Affairs of Russia
Vulnerabilities
2013
1. "Security analysis of mobile banking applications for 2012”, - Digital Security, 20132014
2. "Mobile banking security: the possibility of implementing a MitM attack”, - Digital Security, 20143. "VM escape: 101", - Digital Security company blog on habr.com, 2014
2015
4. "Security of web resources of Russian Banks”, - Digital Security, 20152016
5. Webinar: "Pitfalls of Applied Cryptography — - Positive Technologies, 2016 (+ presentation)2017
6. "Financial Industry Application Vulnerabilities”, - Positive Technologies, 20177. "Automated Code Analysis: Web application vulnerability statistics for 2017”, - Positive Technologies, 2017
8. "Statistics of attacks on web applications: IV quarter of 2017”, - Positive Technologies, 2017
9. "Corporate information Systems: penetration testing attack scenarios”, - Positive Technologies, 2017
10. Webinar: "Typical scenarios of attacks on wireless networks”, - Positive Technologies, 2017 (+ presentation)
11. Webinar: "Typical scenarios of attacks on a corporate information system”, - Positive Technologies, 2017 (+ presentation)
2018
12. "Research: More than half of remote banking systems contain critical vulnerabilities”" - Positive Technologies blog on habr.com, 201813. Webinar: "Advanced attacks on Microsoft Active Directory: ways to detect and protect", - Positive Technologies, 2018 (+ presentation)
14. "Vulnerabilities of corporate information systems 2018", - Positive Technologies, 2018
15. "How Social Engineering opens doors to hackers in your organization” - Positive Technologies, 2018
16. Webinar: "ATM Security Analysis: logical attacks and vulnerabilities”, - Positive Technologies, 2018 (+ presentation)
17. "They got to the bills through the safe," — kommersant.ru, 2018
18. "Low-level hacking of NCR ATMs", - Positive Technologies company blog on habr.com, 2018
Analytical articles
2013
1. "Ensuring the security of RBS systems at all stages of the life cycle”, - Analytical Banking Magazine, 20132014
2. "Attacks on automated banking systems”, BIS-journal, 2014
2015
3. "ABS under the gun”, - Analytical Banking Magazine, 20154. "21st Century Heist: Hackers managed to steal $1 billion” - Kaspersky Lab, 2015
5. “Russian financial cybercrime: how it works”, — securelist.com, 2015
2016
6. "Dozens of Russian banks lost millions of dollars due to cybercriminal attacks” - Kaspersky Lab, 20167. "A banker who can steal everything” – securelist.com, 2016
8. "Hackers against banks: the most high-profile crimes of recent years", — Rbc.ru, 2016
2017
9. "How hackers prepare attacks on banks” - Positive Technologies blog on habr.com, 201710. "Targeted attacks on banks Russia as a testing ground”, - Group-IB, 2017
11. "Hacker-style robbery”, — Kommersant.ru, 2017
2018
12. "News sites in Runet distributed a Banking Trojan", — Securelist.ru, 201813. "$3,000 per night. How do cybercriminals who can rob anyone work? " — tut.by, 2018
14. "Cyber attacks are our daily routine. Hackers targeted mobile banks and industry”, — 360tv.ru, 2018
15. "Attacks on banks”, - Positive Technologie, 2018
16. "Theft schemes in RBS systems and five levels of countering them",-Group-IB company blog on habr.com, 2018
17. "Pegasus crept up unnoticed", — Kommersant.ru, 2018
18. "Criminal Cyber Services Market 2018", - Positive Technology, 2018
19. "Trojans are multiplying in mobile banking", — Kommersant.ru, 2018
20. «APT Trends Report Q2 2018», — Securelist.com, 2018
21. "On crimes committed using modern information and communication technologies" — Prosecutor General's Office of the Russian Federation, 2018
Various
1. "INSTRUCTIONS for responding to incidents related to remote banking systems”, Group-IB, 2012 (announcement)Part 6 - Analysis of banking crimes

(c) The Ministry of Internal Affairs of Russia. A fragment of surveillance footage from the moment when money was stolen from an ATM
This article is devoted to the analysis and identification of patterns in crimes aimed at stealing money from banks or their customers.
Further in the article we will present a sample of more than one hundred real crimes of recent years. All considered crimes will be classified and provided with a brief description. Then a comprehensive analysis will be conducted, which will provide answers to the main questions of banking security, in particular:
- What type of crime is most dangerous for banks?
- Which banking professions are most often involved in criminal activity?
- Are there any patterns in the actions of criminals, and if so, what are they?
- ... and others.
SAMPLE INFORMATION
Sources and time frame
The sources of data on crimes included in the sample were articles on news resources and press releases of law enforcement agencies: the Ministry of Internal Affairs of the Russian Federation, the Prosecutor General's Office of the Russian Federation, the Investigative Committee of the Russian Federation, etc.
Given the huge number of" ordinary " crimes, the sample size for them was limited to the last year — approximately from 07.2017 to 07.2018. The time range of the analyzed "computer" crimes is wider — from 2015 to 2018.
Classification of crimes
From the point of view of banking security, the most important factors in the analysis of crimes will be:
- number of malefactors who participated in the commission of the crime;
- degree of involvement of insiders in the crime;
- type of crime: "computer" or "ordinary".
Based on the above, all the crimes under consideration were classified as follows::
In the beginning, they were divided into two types:
- "Computer" crimes — that is, crimes committed as a result of unauthorized access to information, computer hacking, and so on.
- «Обычные» преступления — любые другие преступления, не относящиеся к «компьютерным».
Then crimes of each type were divided into two categories:
- Crimes committed with the participation of bank employees. This category will include crimes in which at least one of the criminals is a bank employee.
- Crimes committed without the participation of bank employees.
Each of the resulting categories, in turn, was divided into two more types:
- Crimes committed by individuals.
- Crimes committed by a group of persons by prior agreement.
The generalized classification scheme is as follows:
"Ordinary" crimes, without the participation of bank employees | "Computer" crimes, without the participation of bank employees | ||
Loner | Group | Loner | Group |
"Ordinary" crimes involving bank employees | Computer crimes involving bank employees | ||
Loner | Group | Loner | Group |
Data representation
The description of each crime includes the name and reference of the original article, followed by a summary description of the crime as a table.
Example.
"In Krasnoyarsk, the police detained suspects in the theft of 15 million rubles from ATMs," - Banks. <url>, 2018
| Type of crime: | theft of cash from ATMs or payment terminals |
| Articles of the Criminal Code of the Russian Federation: | part 4 of article 158 |
| Description of the crime: | Criminals, using the software, opened payment terminals and stole the money in them. |
| Damage (million rubles): | 15 |
| Maximum penalty (years of imprisonment): | - |
| Information about criminals: | a criminal group consisting of three men: two 23-year-olds and one 50-year-old |
Here:
Crime type-contains a brief description of the crime.
Articles of the Criminal Code of the Russian Federation — contains a list of articles of the Criminal Code of the Russian Federation, according to which law enforcement agencies have qualified this crime.
Damage (million rubles — - contains the amount of total damage caused by the crime, expressed in millions of rubles. If the crime involved amounts in foreign currency, they were converted into rubles at the rate of 60 rubles per US dollar and 70 rubles per euro. In cases where the amount of the attempted theft differs from the amount of actual losses, the first amount is indicated.
Maximum penalty (years of imprisonment) - contains information about the maximum penalty that was imposed on criminals for committing this crime.
Information about criminals-contains a description of the persons who committed the crime.
If the source does not contain the required data, then “- ”is indicated in the corresponding column of the description.
Given the huge amount of data, descriptions of all crimes are hidden under spoilers.
Data quality
For an adequate interpretation of the results obtained in this article, it is necessary to take into account the following facts:
- In the sample under consideration, there are about a hundred crimes, while according to the report of the Ministry of Internal Affairs of Russia "State of Crime", thousands of crimes qualified under similar articles of the Criminal Code were committed during the period under review.
- The sample contains the most high-profile crimes.
- The information sources used do not contain high-quality comprehensive data on crimes.
CRIME SAMPLING
"Ordinary" crimes committed by individuals who are not bank employees
List of “ordinary " crimes committed by individuals who are not employees of the bank
1. "A resident of Izhevsk received more than eight years in a high-security penal colony for a raid on a bank," - Banks.<url>, 2018
| Type of crime: | assault on a bank branch |
| Articles of the Criminal Code of the Russian Federation: | item "b" of part 4 of Article 162 |
| Description of the crime: | receiving cash from bank employees at gunpoint |
| Damage (million rubles): | 2,6 |
| Maximum penalty (years of imprisonment): | 8 |
| Information about criminals: | man |
| Type of crime: | theft of cash from ATMs or payment terminals |
| Articles of the Criminal Code of the Russian Federation: | part 3 of Article 30, part 4 of Article 158 |
| Description of the crime: | physical opening of the ATM |
| Damage (million rubles): | 2 |
| Maximum penalty (years of imprisonment): | - |
| Information about criminals: | male, 38 years old |
| Type of crime: | theft of cash from ATMs or payment terminals |
| Articles of the Criminal Code of the Russian Federation: | part 4 of article 158 |
| Description of the crime: | physical opening of the ATM |
| Damage (million rubles): | 6,579 |
| Maximum penalty (years of imprisonment): | - |
| Information about criminals: | - |
| Type of crime: | theft of cash from ATMs or payment terminals |
| Articles of the Criminal Code of the Russian Federation: | Article 30, article 158 |
| Description of the crime: | physical opening of the ATM |
| Damage (million rubles): | 1,3 |
| Maximum penalty (years of imprisonment): | 3 |
| Information about criminals: | male, 34 years old |
| Type of crime: | assault on a bank branch |
| Articles of the Criminal Code of the Russian Federation: | item "b" of part 4 of Article 162 |
| Description of the crime: | receiving cash from bank employees at gunpoint |
| Damage (million rubles): | 8 |
| Maximum penalty (years of imprisonment): | 10 |
| Information about criminals: | male, 45 years old |
| Type of crime: | assault on a bank branch |
| Articles of the Criminal Code of the Russian Federation: | article 162 |
| Description of the crime: | receiving cash from bank employees at gunpoint |
| Damage (million rubles): | 8 |
| Maximum penalty (years of imprisonment): | - |
| Information about criminals: | man |
| Type of crime: | assault on a bank branch |
| Articles of the Criminal Code of the Russian Federation: | part 2 of Article 162, part 2 of Article 161 |
| Description of the crime: | receiving cash from bank employees at gunpoint |
| Damage (million rubles): | 0,624 |
| Maximum penalty (years of imprisonment): | - |
| Information about criminals: | male, 36 years old |
| Type of crime: | assault on a bank branch |
| Articles of the Criminal Code of the Russian Federation: | part 2 of article 162 |
| Description of the crime: | attempt to receive cash from bank employees when they are threatened with the use of weapons |
| Damage (million rubles): | - |
| Maximum penalty (years of imprisonment): | - |
| Information about criminals: | male, 19 years old |
| Type of crime: | assault on a bank branch |
| Articles of the Criminal Code of the Russian Federation: | - |
| Description of the crime: | receiving cash from bank employees at gunpoint |
| Damage (million rubles): | - |
| Maximum penalty (years of imprisonment): | - |
| Information about criminals: | man |
| Type of crime: | credit fraud |
| Articles of the Criminal Code of the Russian Federation: | part 1, 3 of Article 159 |
| Description of the crime: | The criminal, working in one of the stores, by drawing up forged contracts with commercial banks, issued loans on behalf of unsuspecting citizens. The malefactor spent the received money at her own discretion |
| Damage (million rubles): | 3,5 |
| Maximum penalty (years of imprisonment): | 3 |
| Information about criminals: | female, 36 years old |
11. The plot "Robber from the Federal Penitentiary Service":
a) "Ex-employee of the Federal Penitentiary Service of the Samara region was sentenced for bank robbery" - Volga News, 2017
b) "Victims of the Solidarity Bank robbery demand a million rubles from the offender," Volga News, 2017
| Type of crime: | assault on a bank branch |
| Articles of the Criminal Code of the Russian Federation: | part 4 of article 162 |
| Description of the crime: | receiving cash from bank employees at gunpoint |
| Damage (million rubles): | 5,8 |
| Maximum penalty (years of imprisonment): | 6 |
| Information about criminals: | male, former employee of the Federal Penitentiary Service |
12. The plot of "Robber fitness trainer":
a) "Kazan fitness trainer was given 10 years for robbery in Bystrobank", - Realnoe vremya, 2017
b) "Fast robbery: "gangster" stole almost 5 million rubles from the Kazan "Bystrobank", - Realnoe vremya, 2016
| Type of crime: | assault on a bank branch |
| Articles of the Criminal Code of the Russian Federation: | part 4 of article 162 |
| Description of the crime: | receiving cash from bank employees at gunpoint |
| Damage (million rubles): | 4,8 |
| Maximum penalty (years of imprisonment): | 10 |
| Information about criminals: | male fitness trainer |
Main characteristics of crimes
The number of crimes considered is 12.
The minimum damage caused by a crime is 624 thousand rubles.
The maximum damage caused by a crime is 8 million rubles.
The minimum penalty for a crime is 3 years in prison.
The maximum penalty for the crime is 10 years in prison.
Crimes committed by women:
- fraud in the field of lending.
Crimes committed by men:
- theft of cash from ATMs or payment terminals;
- assault on a bank branch.
Crime analysis
The main crimes in this group are crimes related to the manifestation of violence, namely robberies on bank branches and physical hacking of ATMs. These crimes were usually committed by men in their 30s and 40s, and two cases deserve special attention. The first is a crime committed by a former employee of the Federal Penitentiary Service, and the second is a robbery committed by a former fitness trainer. If the first case is indicative of the fact that the crimes were committed by a person who was called upon to protect the law, then the second case partly resembles the plot of the film "Blood and Sweat: Anabolics", where the main criminal was also a fitness trainer, although he robbed not a bank, but his client.
Female offenders, unlike men, generally do not commit violent crimes. Instead, they use cunning and guile. So the only crime in this group committed by a woman is fraud in the field of lending, namely, the registration of fictitious loans using stolen personal data of individuals.
"Ordinary" crimes committed by lone employees of the bank
List of “ordinary " crimes committed by lone employees of the bank
1. "In Orenburg, the former manager of a bank branch was sent to a penal colony for embezzlement of 16 million rubles," - Banks.<url>, 2018
| Type of crime: | unauthorized transfers (debits) from the bank's customer accounts |
| Articles of the Criminal Code of the Russian Federation: | part 4 of article 159 |
| Description of the crime: | unauthorized withdrawal of funds from customer accounts in the form of cash |
| Damage (million rubles): | 16 |
| Maximum penalty (years of imprisonment): | 4 |
| Information about criminals: | 44-year-old female bank branch manager |
| Type of crime: | unauthorized transfers (debits) from the bank's customer accounts |
| Articles of the Criminal Code of the Russian Federation: | article 159 |
| Description of the crime: | unauthorized transfer of funds from customer accounts due to falsification of primary accounting documents |
| Damage (million rubles): | 0,172 |
| Maximum penalty (years of imprisonment): | - |
| Information about criminals: | female, 30 years old, acting manager of the operational office |
| Type of crime: | unauthorized transfers (debits) from bank clients ' accounts, theft of cash from the bank's cash desk |
| Articles of the Criminal Code of the Russian Federation: | part 4 of Article 160, part 3 of Article 159 |
| Description of the crime: | theft of money from the bank's cash register and customer accounts |
| Damage (million rubles): | 63,5 |
| Maximum penalty (years of imprisonment): | - |
| Information about criminals: | female, 62 years old, director of a bank branch |
| Type of crime: | credit fraud |
| Articles of the Criminal Code of the Russian Federation: | article 159 |
| Description of the crime: | issuing a deliberately non-repayable loan |
| Damage (million rubles): | 150 |
| Maximum penalty (years of imprisonment): | - |
| Information about criminals: | male bank owner |
| Type of crime: | securities fraud |
| Articles of the Criminal Code of the Russian Federation: | part 4 of article 159 |
| Description of the crime: | assignment of customer bills as a result of fictitious exchanges |
| Damage (million rubles): | 20 |
| Maximum penalty (years of imprisonment): | 2 |
| Information about criminals: | female, 47 years old, Head of the Corporate Customer Service Sector |
| Type of crime: | unauthorized transfers (debits) from the bank's customer accounts |
| Articles of the Criminal Code of the Russian Federation: | part 4 of article 158 |
| Description of the crime: | withdraw funds to a fake bank card linked to a legitimate client. |
| Damage (million rubles): | 3 |
| Maximum penalty (years of imprisonment): | - |
| Information about criminals: | female, 33 years old, bank employee |
| Type of crime: | theft of cash from a bank's cash register |
| Articles of the Criminal Code of the Russian Federation: | part 4 of article 160 |
| Description of the crime: | theft of cash from the cash register |
| Damage (million rubles): | 780 |
| Maximum penalty (years of imprisonment): | - |
| Information about criminals: | male bank owner |
| Type of crime: | theft of cash from a bank's cash register |
| Articles of the Criminal Code of the Russian Federation: | part 4 of article 160 |
| Description of the crime: | theft from a bank branch's cash register |
| Damage (million rubles): | 4 |
| Maximum penalty (years of imprisonment): | 3 |
| Information about criminals: | female, 33 years old, cashier |
| Type of crime: | unauthorized transfers (debits) from the bank's customer accounts |
| Articles of the Criminal Code of the Russian Federation: | part 3 of Article 159 |
| Description of the crime: | unauthorized transfer of money from customer accounts |
| Damage (million rubles): | 0,527 |
| Maximum penalty (years of imprisonment): | - |
| Information about criminals: | female, 46 years old, client manager |
| Type of crime: | stealing bank money |
| Articles of the Criminal Code of the Russian Federation: | part 4 of article 159 |
| Description of the crime: | The criminal stole money by executing a fictitious banking operation |
| Damage (million rubles): | 15 |
| Maximum penalty (years of imprisonment): | - |
| Information about criminals: | female, 43 years old, bank employee |
| Type of crime: | theft of cash from a bank's cash register |
| Articles of the Criminal Code of the Russian Federation: | part 4 of article 160 |
| Description of the crime: | theft of cash from the cash register |
| Damage (million rubles): | 2 |
| Maximum penalty (years of imprisonment): | - |
| Information about criminals: | male, 30 years old, bank employee |
| Type of crime: | unauthorized transfers (debits) from the bank's customer accounts |
| Articles of the Criminal Code of the Russian Federation: | part 4 of article 159 |
| Description of the crime: | the criminal transferred funds intended for early repayment of consumer loans to savings cards issued in the name of customers without their knowledge, which she managed independently. |
| Damage (million rubles): | 1 |
| Maximum penalty (years of imprisonment): | - |
| Information about criminals: | female, 24 years old, financial expert of the bank |
| Type of crime: | unauthorized transfers (debits) from the bank's customer accounts |
| Articles of the Criminal Code of the Russian Federation: | part 3 of article 160 |
| Description of the crime: | forgery of documents and fictitious cash transactions |
| Damage (million rubles): | 0,9 |
| Maximum penalty (years of imprisonment): | 2 |
| Information about criminals: | female, 28 years old, bank employee |
| Type of crime: | unauthorized transfers (debits) from the bank's customer accounts |
| Articles of the Criminal Code of the Russian Federation: | article 159 |
| Description of the crime: | forgery of documents and fictitious cash transactions |
| Damage (million rubles): | 1000 |
| Maximum penalty (years of imprisonment): | - |
| Information about criminals: | male head of the bank's additional office |
| Type of crime: | theft of cash during collection |
| Articles of the Criminal Code of the Russian Federation: | part 4 of article 160 |
| Description of the crime: | embezzlement of part of the money from collection bags |
| Damage (million rubles): | 4,2 |
| Maximum penalty (years of imprisonment): | - |
| Information about criminals: | male, 28 years old, collection officer |
| Type of crime: | theft of cash from a bank's cash register |
| Articles of the Criminal Code of the Russian Federation: | part 3 of article 160 |
| Description of the crime: | theft of cash from the cash register |
| Damage (million rubles): | 0,585 |
| Maximum penalty (years of imprisonment): | - |
| Information about criminals: | female, 36 years old, cashier |
| Type of crime: | credit fraud |
| Articles of the Criminal Code of the Russian Federation: | article 159 |
| Description of the crime: | The criminal deliberately underestimated the value of real estate that was pledged to the bank. After that, he entered into an assignment agreement, informing the client of the false value of the property belonging to him. Thus the accused stole money belonging to the bank |
| Damage (million rubles): | 5 |
| Maximum penalty (years of imprisonment): | - |
| Information about criminals: | male, Deputy Chairman of the bank's management Board |
| Type of crime: | theft of cash during collection |
| Articles of the Criminal Code of the Russian Federation: | part 4 of article 160 |
| Description of the crime: | theft from collection bags |
| Damage (million rubles): | 2 |
| Maximum penalty (years of imprisonment): | - |
| Information about criminals: | male, 25 years old, collection officer |
| Type of crime: | theft of cash from a bank's cash register |
| Articles of the Criminal Code of the Russian Federation: | part 4 of article 158 |
| Description of the crime: | theft of cash from the cash register |
| Damage (million rubles): | 13 |
| Maximum penalty (years of imprisonment): | - |
| Information about criminals: | female, 43 years old, cashier |
| Type of crime: | credit fraud |
| Articles of the Criminal Code of the Russian Federation: | part 4 of article 159 |
| Description of the crime: | making fictitious loans for bank clients |
| Damage (million rubles): | 1,43 |
| Maximum penalty (years of imprisonment): | - |
| Information about criminals: | female bank manager |
| Type of crime: | unauthorized transfers (debits) from the bank's customer accounts |
| Articles of the Criminal Code of the Russian Federation: | item "b" of part 2 of Article 158, part 3 of Article 159, part 3 of Article 160 |
| Description of the crime: | The criminal carried out the issue of non-personalized bank cards, which she later appropriated. After that, she stole money by cashing it out through ATMs |
| Damage (million rubles): | 2,5 |
| Maximum penalty (years of imprisonment): | - |
| Information about criminals: | female, 29 years old, bank employee |
| Type of crime: | - |
| Articles of the Criminal Code of the Russian Federation: | Article 30, article 183 |
| Description of the crime: | the criminal illegally copied information from the bank's database on legal entity clients to an electronic carrier, and then the attacker decided to sell the data he copied. |
| Damage (million rubles): | 0,2 |
| Maximum penalty (years of imprisonment): | - |
| Information about criminals: | male, chief specialist of the credit examination department |
Main characteristics of crimes
The number of crimes considered is 22.
The minimum damage caused by a crime is 172 thousand rubles.
The maximum damage caused by a crime is 1 billion rubles.
The minimum penalty for a crime is 2 years in prison.
The maximum penalty for the crime is 4 years in prison.
Crimes committed by women:
- unauthorized transfers (debits) from the bank's customer accounts;
- theft of cash from a bank's cash register;
- credit fraud;
- securities fraud;
- stealing bank money.
Crimes committed by men:
- theft of cash from a bank's cash register;
- unauthorized transfers (debits) from the bank's customer accounts;
- theft of cash during collection;
- fraud in the field of lending.
Positions of criminals:
- owner of the bank;
- Deputy Chairman of the bank's Management Board;
- director of the bank's branch;
- bank branch manager;
- acting Manager of the bank's operational office;
- Head of the Corporate Customer Service Sector;
- cashier;
- client manager;
- financial expert;
- collection officer;
- bank manager;
- bank employee.
Crime analysis
The following typical scenarios can be distinguished in crimes of this group:
- Lower-level bank managers engage in credit or securities fraud, and also steal money from customer accounts.
- Cashiers or collectors steal the money entrusted to them.
- Top managers of the bank steal money by embezzlement or issuing deliberately non-repayable loans.
An interesting fact is that in this group, the overwhelming majority of criminals are women, and their behavior can be divided into two archetypes:
- "Tikhushnitsy" — work and secretly steal for years.
- "Desperate" — commit one or more thefts and go on the run.
In the list of crimes of this group, there is a case that is not related to the analyzed banking crimes, but still quite interesting. This is a case in which a bank employee "leaked" a customer database and then tried to sell it. However, he was caught red-handed.
"Ordinary" crimes committed by groups of individuals without the participation of bank employees
List of “ordinary " crimes committed by groups of individuals without the participation of bank employees
1. "The Prosecutor's Office of the Kabardino-Balkar Republic approved an indictment in a criminal case on six episodes of fraud in the amount of more than 16 million rubles" — - Prosecutor General's Office of the Russian Federation, 2018
| Type of crime: | stealing bank money |
| Articles of the Criminal Code of the Russian Federation: | part 2 of Article 159, part 3 of Article 159, part 4 of Article 159, part 3 of Article 30 |
| Description of the crime: | - |
| Damage (million rubles): | 16 |
| Maximum penalty (years of imprisonment): | - |
| Information about criminals: | a criminal group consisting of a man and his accomplices |
| Type of crime: | assault on a bank branch |
| Articles of the Criminal Code of the Russian Federation: | article 162 |
| Description of the crime: | receiving cash from bank employees at gunpoint |
| Damage (million rubles): | 6 |
| Maximum penalty (years of imprisonment): | - |
| Information about criminals: | a criminal group of 5 people |
| Type of crime: | assault on a bank branch |
| Articles of the Criminal Code of the Russian Federation: | part 3 of article 162 |
| Description of the crime: | attempt to receive cash from bank employees when they are threatened with the use of weapons |
| Damage (million rubles): | - |
| Maximum penalty (years of imprisonment): | - |
| Information about criminals: | a criminal group of 22 and 24-year-old men |
| Type of crime: | assault on a bank branch |
| Articles of the Criminal Code of the Russian Federation: | article 162 |
| Description of the crime: | receiving cash from bank employees at gunpoint |
| Damage (million rubles): | 23 |
| Maximum penalty (years of imprisonment): | 9,5 |
| Information about criminals: | a criminal group of 3 44-year-old men |
| Type of crime: | assault on a bank branch |
| Articles of the Criminal Code of the Russian Federation: | paragraphs "a, b" of part 4 of Article 162, paragraph "b" of Part 3 of Article 161, part 1 of Article 174.1 |
| Description of the crime: | receiving cash from bank employees at gunpoint |
| Damage (million rubles): | 6,3 |
| Maximum penalty (years of imprisonment): | 14 |
| Information about criminals: | criminal group of 5 men |
| Type of crime: | credit fraud |
| Articles of the Criminal Code of the Russian Federation: | article 159 |
| Description of the crime: | obtaining loans from banks based on forged documents |
| Damage (million rubles): | 500 |
| Maximum penalty (years of imprisonment): | - |
| Information about criminals: | criminal group |
| Type of crime: | assault on a bank branch |
| Articles of the Criminal Code of the Russian Federation: | article 162 |
| Description of the crime: | receiving cash from bank employees at gunpoint |
| Damage (million rubles): | 5,3 |
| Maximum penalty (years of imprisonment): | - |
| Information about criminals: | criminal group |
| Type of crime: | unauthorized transfers (debits) from the bank's customer accounts |
| Articles of the Criminal Code of the Russian Federation: | article 159 |
| Description of the crime: | getting access to customer accounts based on fictitious documents submitted to the bank |
| Damage (million rubles): | 98 |
| Maximum penalty (years of imprisonment): | 6 |
| Information about criminals: | a criminal group of 7 people |
| Type of crime: | theft of cash from ATMs or payment terminals |
| Articles of the Criminal Code of the Russian Federation: | - |
| Description of the crime: | the criminals opened the ATM, cut the contact loop, connected the device to the control unit and stole the hard drive of the DVR and cash. |
| Damage (million rubles): | 4,5 |
| Maximum penalty (years of imprisonment): | - |
| Information about criminals: | criminal group of 2 people |
| Type of crime: | credit fraud |
| Articles of the Criminal Code of the Russian Federation: | Part 4 of Article 159, paragraphs "a", " b " of Part 4 of Article 174.1 |
| Description of the crime: | lending to enterprises controlled by criminals using false information. |
| Damage (million rubles): | 739 |
| Maximum penalty (years of imprisonment): | - |
| Information about criminals: | a criminal group of 2 people, a man and a woman |
| Type of crime: | securities fraud |
| Articles of the Criminal Code of the Russian Federation: | part 4 of article 159 |
| Description of the crime: | execution of transactions with securities at deliberately low or inflated prices |
| Damage (million rubles): | 4500 |
| Maximum penalty (years of imprisonment): | - |
| Information about criminals: | criminal group |
| Type of crime: | credit fraud |
| Articles of the Criminal Code of the Russian Federation: | part 4 of article 159 |
| Description of the crime: | receipt and non-repayment of consumer loans |
| Damage (million rubles): | 52 |
| Maximum penalty (years of imprisonment): | - |
| Information about criminals: | a criminal group of three women |
| Type of crime: | assault on a bank branch |
| Articles of the Criminal Code of the Russian Federation: | - |
| Description of the crime: | criminals broke into bank branches, tied up employees with tape and stole money from safes |
| Damage (million rubles): | 1,1 |
| Maximum penalty (years of imprisonment): | - |
| Information about criminals: | a criminal group of three men |
| Type of crime: | credit fraud |
| Articles of the Criminal Code of the Russian Federation: | article 159 |
| Description of the crime: | getting non-repayable loans |
| Damage (million rubles): | 132 |
| Maximum penalty (years of imprisonment): | 4,5 |
| Information about criminals: | a criminal group that included the owner of several companies, a man. |
| Type of crime: | credit fraud |
| Articles of the Criminal Code of the Russian Federation: | article 159 |
| Description of the crime: | getting a non-repayable loan, selling collateral |
| Damage (million rubles): | 190 |
| Maximum penalty (years of imprisonment): | - |
| Information about criminals: | a criminal group consisting of the head of a legal entity and his accomplice |
| Type of crime: | credit fraud |
| Articles of the Criminal Code of the Russian Federation: | Part 4 of Article 159, part 4 of Article 174.1 |
| Description of the crime: | getting knowingly non-repayable loans |
| Damage (million rubles): | 160 |
| Maximum penalty (years of imprisonment): | - |
| Information about criminals: | criminal group consisting of 2 participants-managers of a legal entity, a bank client |
| Type of crime: | unauthorized transfers (debits) from the bank's customer accounts |
| Articles of the Criminal Code of the Russian Federation: | - |
| Description of the crime: | Malefactors observed citizens at ATMs. After learning the PIN code, the attackers threw the victim a wallet and offered to return it to the bank or keep it for themselves. And then the alleged owner of the wallet appeared and demanded to turn out the pockets. At this moment, the victims ' bank card was being replaced with a plastic dummy similar in appearance. Having got someone else's card, the scammers immediately transferred the victims ' money to their own account |
| Damage (million rubles): | 1,2 |
| Maximum penalty (years of imprisonment): | - |
| Information about criminals: | criminal group |
| Type of crime: | |
| Articles of the Criminal Code of the Russian Federation: | Article 30, article 159 |
| Description of the crime: | criminals produced fictitious documents with bank customer data and gained access to financial transactions on open accounts. In this way, the defendants stole the funds of several depositors |
| Damage (million rubles): | 98 |
| Maximum penalty (years of imprisonment): | |
| Information about criminals: | a criminal group of 6 people |
| Type of crime: | unauthorized transfers (debits) from the bank's customer accounts |
| Articles of the Criminal Code of the Russian Federation: | Article 30, article 159 |
| Description of the crime: | Attempt to receive funds by submitting forged documents to the bank |
| Damage (million rubles): | 870 |
| Maximum penalty (years of imprisonment): | - |
| Information about criminals: | a criminal group consisting of two women aged 28 and 35 |
Main characteristics of crimes
The number of crimes considered is 19.
The minimum damage caused by a crime is 1 million 100 thousand rubles.
The maximum damage caused by the crime is 4.5 billion rubles.
The minimum penalty for a crime is 4.5 years in prison.
The maximum penalty for the crime is 14 years in prison.
Crimes committed by women:
- unauthorized transfers (debits) from the bank's customer accounts;
- fraud in the field of lending.
Crimes committed by men:
- credit fraud;
- stealing bank money;
- assault on a bank branch.
The maximum size of a criminal group is 7 members.
Crime analysis
If we compare the structure of crimes in this group with the structure of similar crimes committed by individuals, we can see a significant shift from violent crimes to intellectual crimes related to fraud. In addition to changes in the structure, the damage caused by crimes has also increased. The group under consideration contains:
- crimes that caused the maximum economic damage in comparison with other crimes: 4.5 billion rubles;
- a crime that carries a maximum penalty of 14 years in prison.
Interesting crimes in this group include fraud committed in Chuvashia. Here, the criminals used the classic "lost wallet" wiring, during which they physically stole the victims ' bank cards and, using previously spied PIN codes, withdrew money from them at ATMs. To prevent the victim from suspecting theft, the criminals slipped a plastic blank instead of a real card.
"Ordinary" crimes committed by groups of individuals with the participation of bank employees
List of "ordinary" crimes committed by groups of individuals with the participation of bank employees
Main characteristics of crimes
The number of crimes considered is 20.
The minimum damage caused by a crime is 1 million 600 thousand rubles.
The maximum damage caused by a crime is 2 billion rubles. 100 million rubles.
The minimum penalty for a crime is 2.5 years in prison.
The maximum penalty for the crime is 12 years in prison.
Crimes committed by women:
- unauthorized transfers (debits) from the bank's customer accounts;
- fraud in the field of lending.
Crimes committed by men:
- credit fraud;
- unauthorized transfers (debits) from the bank's customer accounts;
- theft of cash from ATMs or payment terminals.
The maximum size of a criminal group is 8 members.
Positions of criminals:
- Chairman of the bank's Board of Directors;
- president of the bank;
- Chairman of the bank's Management Board;
- Deputy Chairman of the bank's Management Board;
- Vice-President of the bank;
- Director of the bank's regional branch;
- head of the additional office;
- Head of the Credit and deposit Department;
- deputy head of the credit department;
- Head of Small Business Lending Department;
- Chief economist of the additional office;
- consultant manager of the bank's branch sales department;
- sales manager;
- collection officer;
- bank employee.
Crime analysis
The main difference between crimes of this group and those previously considered is that in the vast majority of cases, the affected party is the bank, and the main method of causing damage is the issuance of deliberately non — repayable loans. In addition to credit fraud, the attackers also engaged in the theft of customers ' money committed in various ways. The cadre of criminals is quite remarkable: among them there are many middle-and senior-level managers, as well as bank owners.
The most interesting crime in this group can be considered a combination in which the attackers first gained control of the bank, and then by issuing non-repayable loans withdrew funds from it, which eventually caused damage in more than 2 billion rubles.
"Computer-related" crimes committed by individuals who are not bank employees
List of "computer" crimes committed by individuals who are not employees of the bank
1. "A suspect was detained in Izhevsk in an attempt to steal money from an ATM", - The Ministry of Internal Affairs of Russia, 2018
| Type of crime: | theft of cash from ATMs or payment terminals |
| Articles of the Criminal Code of the Russian Federation: | - |
| Description of the crime: | having passed to one of the terminals, the malefactor connected to it the smartphone and by means of special software tried to steal the money which was in the ATM. |
| Damage (million rubles): | 1,2 |
| Maximum penalty (years of imprisonment): | - |
| Information about criminals: | male, 28 years old |
| Type of crime: | unauthorized transfers (debits) from the bank's customer accounts |
| Articles of the Criminal Code of the Russian Federation: | part 1 of Article 187, part 1 of Article 173.1 |
| Description of the crime: | The criminal, having access to the Bank-Client program and electronic signatures of 52 commercial organizations, provided fake payment documents to banks for two years. In them, he indicated information about the purpose of payments that did not correspond to reality. To obtain financial benefits, the man registered a limited liability company |
| Damage (million rubles): | - |
| Maximum penalty (years of imprisonment): | - |
| Information about criminals: | male, 49 years old |
| Type of crime: | unauthorized transfers (debits) from the bank's customer accounts |
| Articles of the Criminal Code of the Russian Federation: | part 2 of Article 158 |
| Description of the crime: | Criminals infected victims ' mobile phones with malware. As a result, they could make payments on their behalf in the Internet Client-Bank system |
| Damage (million rubles): | 0,12 |
| Maximum penalty (years of imprisonment): | - |
| Information about criminals: | male, 29 years old |
| Type of crime: | theft of cash from ATMs or payment terminals |
| Articles of the Criminal Code of the Russian Federation: | - |
| Description of the crime: | the criminal remotely gained access to the software of the bank terminal and infected it with an "electronic virus", with which he stole cash |
| Damage (million rubles): | 0,455 |
| Maximum penalty (years of imprisonment): | - |
| Information about criminals: | male, 30 years old |
| Type of crime: | unauthorized transfers (debits) from the bank's customer accounts |
| Articles of the Criminal Code of the Russian Federation: | - |
| Description of the crime: | the attacker purchased a copy of the website of one of the banks via the Internet, and then modified it. Then the fraudster posted an advertisement on the Odnoklassniki social network about the bank holding an action, during which any client can receive a reward if they register using the link in the video description. In turn, the link led to a resource created by the attacker. He transferred the stolen funds to e-wallets, and then to his bank card. |
| Damage (million rubles): | 0,38 |
| Maximum penalty (years of imprisonment): | - |
| Information about criminals: | male, 26 years old |
6. The story " Theft from Texbank”:
a) "After a failure in the operating system, 27 million rubles disappeared from the Moscow bank", - Kommersant, 2017
b) "An actor from St. Petersburg stole 27 million rubles from Texbank", - Channel 5, 2017
| Type of crime: | unauthorized transfers from bank accounts |
| Articles of the Criminal Code of the Russian Federation: | - |
| Description of the crime: | after a failure in the bank's operating system, funds disappeared from the account |
| Damage (million rubles): | 27 |
| Maximum penalty (years of imprisonment): | - |
| Information about criminals: | male, 30 years old |
Main characteristics of crimes
The number of crimes considered is 6.
The minimum damage caused by a crime is 120 thousand rubles.
The maximum damage caused by the crime is 27 million rubles.
Minimum penalty for a crime-no data available.
Maximum penalty for a crime-no data available.
Crimes committed by women are not recorded.
Crimes committed by men:
- stealing bank money;
- unauthorized transfers (debits) from the bank's customer accounts;
- theft of cash from ATMs or payment terminals.
Crime analysis
"Computer" crimes committed by lone individuals are mainly directed against bank customers and consist in stealing victims ' money through the Client-Bank Internet systems and performing unauthorized operations on their payment cards.
In addition to attacks on customers, lone hackers stole money from ATMs, and just as in the case of Texbank, they tried to steal money by hacking into the bank's IT systems.
It is noteworthy that among the criminals there is not a single representative of the fair sex.
"Computer-related" crimes committed by a group of individuals that included bank employees
List of "computer" crimes committed by a group of individuals that included bank employees
1. "A case on fraud in the field of computer information was submitted to the court in the Central District", - The Ministry of Internal Affairs of Russia, 2017
| Type of crime: | unauthorized transfers (debits) from the bank's customer accounts |
| Articles of the Criminal Code of the Russian Federation: | Article 30, article 159.6 |
| Description of the crime: | "by modifying computer information” |
| Damage (million rubles): | 6 |
| Maximum penalty (years of imprisonment): | - |
| Information about criminals: | criminal group consisting of: a leading bank manager, a 30-year-old woman and her accomplice |
| Type of crime: | unauthorized transfers (debits) from the bank's customer accounts |
| Articles of the Criminal Code of the Russian Federation: | article 159 |
| Description of the crime: | Criminals, being employees of the bank, copied personal data of customers and passed them on to accomplices, who later transferred money from the victims ' accounts via online banking, after which they cashed out the stolen funds at ATMs in Moscow and the Moscow region. |
| Damage (million rubles): | 20 |
| Maximum penalty (years of imprisonment): | - |
| Information about criminals: | a criminal group of 10 people, including bank employees |
Main characteristics of crimes
The number of crimes considered is 2.
The minimum damage caused by a crime is 6 million rubles.
The maximum damage caused by a crime is 20 million rubles.
Minimum penalty for a crime-no data available.
Maximum penalty for a crime-no data available.
Crimes committed by women:
- unauthorized transfers (debits) from the bank's customer accounts.
Crimes committed by men:
- unauthorized transfers (debits) from the bank's customer accounts.
The maximum size of a criminal group is 10 members.
Positions of criminals:
- leading manager of the bank.
Types of crimes — unauthorized transfers (debits) from bank clients ' accounts.
Crime analysis
"Computer" crimes committed with the participation of bank employees are quite rare. There are only two of them in our sample. And all these are actions of criminal groups. There are no" computer " crimes committed by lone individuals at all.
In all the crimes of this group, the attackers tried to steal customer funds. Both men and women were involved in the crimes. Also, the fact that there are no banking IT specialists among the criminals is striking.
"Computer" crimes committed by groups of individuals without the participation of bank employees
List of "computer" crimes committed by groups of individuals without the participation of bank employees
1. "In Krasnoyarsk, the police detained suspects in the theft of 15 million rubles from ATMs," — Banks.<url>, 2018
| Type of crime: | theft of cash from ATMs or payment terminals |
| Articles of the Criminal Code of the Russian Federation: | part 4 of article 158 |
| Description of the crime: | Criminals, using the software, opened payment terminals and stole the money in them. |
| Damage (million rubles): | 15 |
| Maximum penalty (years of imprisonment): | - |
| Information about criminals: | a criminal group consisting of three men: two 23-year-olds and one 50-year-old |
| Type of crime: | unauthorized transfers from bank accounts |
| Articles of the Criminal Code of the Russian Federation: | article 159.6 |
| Description of the crime: | The criminal rented PoS-terminals allegedly for cashing out money. Then, acting with an accomplice, using the received PoS terminals and payment cards issued to unidentified persons at their disposal, he made a number of financial transactions to pay for goods and return funds to his accounts, allegedly on the basis of refusal of services. |
| Damage (million rubles): | 1400 |
| Maximum penalty (years of imprisonment): | - |
| Information about criminals: | a criminal group consisting of a man and his accomplice |
| Type of crime: | theft of cash from ATMs or payment terminals |
| Articles of the Criminal Code of the Russian Federation: | part 4 of article 158 |
| Description of the crime: | committing theft by hacking ATM software |
| Damage (million rubles): | 6 |
| Maximum penalty (years of imprisonment): | - |
| Information about criminals: | a criminal group of 4 participants |
| Type of crime: | unauthorized transfers (debits) from the bank's customer accounts |
| Articles of the Criminal Code of the Russian Federation: | item "a", " b "of part 2 of Article 158, item" b " of Part 3 of Article 158 |
| Description of the crime: | Criminals searched in garbage cans near ATMs for checks containing details of access to the Client-Bank Internet system. Then they made SIM cards using forged powers of attorney for the phone numbers of the bank's client. After that, they accessed the ICB system and withdrew funds. |
| Damage (million rubles): | 0,66 |
| Maximum penalty (years of imprisonment): | 5 |
| Information about criminals: | a criminal group consisting of two 34-year-old women and their male accomplice |
| Type of crime: | unauthorized transfers (debits) from the bank's customer accounts |
| Articles of the Criminal Code of the Russian Federation: | article 272, article 158 |
| Description of the crime: | Criminals created phishing pages that mimic the resources of popular payment systems and air ticket sales services. Having received the victims ' bank details, the scammers used them to steal money from the citizen's accounts and e-wallets. |
| Damage (million rubles): | - |
| Maximum penalty (years of imprisonment): | - |
| Information about criminals: | a criminal group of two men |
| Type of crime: | theft of cash from ATMs or payment terminals |
| Articles of the Criminal Code of the Russian Federation: | - |
| Description of the crime: | stealing money using malware |
| Damage (million rubles): | 5 |
| Maximum penalty (years of imprisonment): | - |
| Information about criminals: | a criminal group consisting of two men aged 27 and 43 |
| Type of crime: | unauthorized transfers (debits) from the bank's customer accounts |
| Articles of the Criminal Code of the Russian Federation: | Part 4 of Article 159.6 |
| Description of the crime: | Criminals infected victims ' mobile phones with malware, then sent hidden SMS messages to withdraw money from their Internet Client-Bank systems to their accounts |
| Damage (million rubles): | 50 |
| Maximum penalty (years of imprisonment): | - |
| Information about criminals: | criminal group consisting of: 20 people and 30 — year-old male supervisors |
| Type of crime: | theft of cash from ATMs or payment terminals |
| Articles of the Criminal Code of the Russian Federation: | part 3 of Article 30, part 4 of Article 158 |
| Description of the crime: | attempted theft using specialized malware |
| Damage (million rubles): | - |
| Maximum penalty (years of imprisonment): | - |
| Information about criminals: | a criminal group of three members and a 34-year-old male leader. |
| Type of crime: | theft of cash from ATMs or payment terminals |
| Articles of the Criminal Code of the Russian Federation: | part 3 of Article 30, part 4 of Article 158 |
| Description of the crime: | physical opening of an ATM and the use of malware |
| Damage (million rubles): | - |
| Maximum penalty (years of imprisonment): | - |
| Information about criminals: | a criminal group of 4 men |
| Type of crime: | stealing bank money |
| Articles of the Criminal Code of the Russian Federation: | - |
| Description of the crime: | - |
| Damage (million rubles): | 47 |
| Maximum penalty (years of imprisonment): | - |
| Information about criminals: | - |
| Type of crime: | unauthorized transfers from bank accounts |
| Articles of the Criminal Code of the Russian Federation: | Article 159, article 210 |
| Description of the crime: | A group of Internet scammers with knowledge in the field of programming and technology developed a bot that at a certain point in time, after conducting transactions from account to account, made cancellations of operations, but by this time funds were already sent by payment order via Internet banking, and the team came to the bank with a delay. Most of the transfers were made from dollar to ruble accounts, or from dollar to euro accounts. The fraudsters operated according to the following scheme: they got bank cards in someone else's names, went to the terminal, replenished the account by moving to another terminal, withdrew an insignificant amount and took a receipt, after which, having received a receipt from the ATM with authorization data for a direct legal ATM card withdrawal operation, they used its details via ITS Internet and formed a fake account. an electronic order in the form of a reverse transaction to cancel a withdrawal operation. As a result of such actions, the bank card account balance was restored and replenished to the specified amount. Thus, a gang of hacker programmers was able to cause damage to four banks in the amount of more than one billion rubles. |
| Damage (million rubles): | 1000 |
| Maximum penalty (years of imprisonment): | - |
| Information about criminals: | a criminal group of 16 people |
| Type of crime: | unauthorized transfers from bank accounts |
| Articles of the Criminal Code of the Russian Federation: | - |
| Description of the crime: | hacking the automated banking system (ABS) |
| Damage (million rubles): | 100 |
| Maximum penalty (years of imprisonment): | - |
| Information about criminals: | criminal group |
| Type of crime: | unauthorized transfers from bank accounts |
| Articles of the Criminal Code of the Russian Federation: | - |
| Description of the crime: | penetration into the bank's network, using malicious Buhtrap code |
| Damage (million rubles): | 1800 |
| Maximum penalty (years of imprisonment): | - |
| Information about criminals: | Buhtrap Crime Group |
| Type of crime: | unauthorized transfers (debits) from the bank's customer accounts |
| Articles of the Criminal Code of the Russian Federation: | article 273 |
| Description of the crime: | embezzlement of funds using malware installed on the victim's phone |
| Damage (million rubles): | - |
| Maximum penalty (years of imprisonment): | - |
| Information about criminals: | a criminal group of 2 men, one of whom is 19 years old |
| Type of crime: | unauthorized transfers (debits) from the bank's customer accounts |
| Articles of the Criminal Code of the Russian Federation: | Part 4 of Article 159.6 |
| Description of the crime: | The attackers remotely hacked the computer of the Tuymazinsky post office and transferred over 8 million rubles to their phone accounts, after which they cashed them out using electronic payment systems. To commit the crime, they used special software. |
| Damage (million rubles): | 8 |
| Maximum penalty (years of imprisonment): | - |
| Information about criminals: | criminal group consisting of 2 men aged 34 and 35 |
| Type of crime: | unauthorized transfers from bank accounts |
| Articles of the Criminal Code of the Russian Federation: | part 2 of Article 272, part 2 of Article 273, Article 274, part 2 of Article 159.6 |
| Description of the crime: | hacking of the banking network, making unauthorized transfers from the bank's correspondent accounts to individuals ' card accounts in other banks, cash-out at ATMs |
| Damage (million rubles): | 2,6 |
| Maximum penalty (years of imprisonment): | - |
| Information about criminals: | criminal group consisting of 2 men aged 34 and 35 |
| Type of crime: | unauthorized transfers from bank accounts |
| Articles of the Criminal Code of the Russian Federation: | - |
| Description of the crime: | A "Transaction cancellation" attack. The fraudster uses the issuing bank's cards to withdraw cash from an ATM — this money belongs to the bank that serves the ATM (acquirer). Immediately after that, the fraudster's accomplice sends a request to the payment system to cancel the operation. |
| Damage (million rubles): | 470 |
| Maximum penalty (years of imprisonment): | - |
| Information about criminals: | unknown criminal group |
| Type of crime: | unauthorized transfers (debits) from the bank's customer accounts |
| Articles of the Criminal Code of the Russian Federation: | Article 158, article 183, article 272 |
| Description of the crime: | Criminals obtained illegal access to electronic accounts of Trans-Baikal residents opened in the Chita branch of one of the banks, and using fake passports and the Internet Banking application, transferred funds to their controlled accounts, and then cashed them in the bank's branch. |
| Damage (million rubles): | 3 |
| Maximum penalty (years of imprisonment): | - |
| Information about criminals: | a criminal group of 5 people |
| Type of crime: | unauthorized transfers (debits) from the bank's customer accounts |
| Articles of the Criminal Code of the Russian Federation: | part 3 of Article 272, part 4 of Article 159.6, part 3 of Article 272, part 4 of Article 159.6 |
| Description of the crime: | Criminals distributed malicious software on the Internet and gained access to the computers of a commercial organization that accepted payments for cellular communication services, as well as a bank in Petropavlovsk-Kamchatsky. Having received the opportunity to manage money transfers, members of the organized group stole more than 60.5 million rubles, which they transferred to the bank accounts of front organizations controlled by them and cashed out |
| Damage (million rubles): | 60,5 |
| Maximum penalty (years of imprisonment): | - |
| Information about criminals: | criminal group of 2 men |
| Type of crime: | unauthorized transfers (debits) from the bank's customer accounts |
| Articles of the Criminal Code of the Russian Federation: | Article 159.6, article 174.1 |
| Description of the crime: | The criminal sent out SMS messages containing a link to the malicious mobile application " Banks in the palm of your hand”. Victims entered their payment card details there. After that, the criminal committed theft from their accounts. |
| Damage (million rubles): | 1 |
| Maximum penalty (years of imprisonment): | - |
| Information about criminals: | criminal group consisting of a 32-year-old man and accomplices |
| Type of crime: | unauthorized transfers (debits) from the bank's customer accounts |
| Articles of the Criminal Code of the Russian Federation: | - |
| Description of the crime: | Malefactors carried out substitution of details in payment orders unloaded from 1C: Enterprise and sent through the remote banking system for execution to the bank |
| Damage (million rubles): | 200 |
| Maximum penalty (years of imprisonment): | - |
| Information about criminals: | - |
22. The story " Theft from the Russian International Bank”:
a) "Hackers stole more than half a billion rubles from the correspondent account in the Central Bank", - Interfax, 2016
b) "Russian International Bank named the amount of funds stolen by hackers", - RBC, 2016
c) "Hackers stole almost 2 billion rubles from banks using "letters from the Central Bank", - RBC, 2016
| Type of crime: | unauthorized transfers from bank accounts |
| Articles of the Criminal Code of the Russian Federation: | - |
| Description of the crime: | hackers made several thousand unauthorized transfers from the corresponding bank account to the accounts of legal entities and individuals in about 60 banks, after which some of the funds were cashed out |
| Damage (million rubles): | 508, 67 |
| Maximum penalty (years of imprisonment): | - |
| Information about criminals: | criminal group |
23. The story "Theft from Metallinvestbank":
a) " Hackers withdrew 677 million rubles. from Metallinvestbank's accounts", - RBC, 2016
b) "Metallinvestbank lost 200 million rubles due to a hacker attack", - RIA Novosti, 2016
c) "Metallinvestbank press release on theft" — - Metalinvestbank, 2016
d) "Hacker-style robbery", - Kommersant, 2017
| Type of crime: | unauthorized transfers from bank accounts |
| Articles of the Criminal Code of the Russian Federation: | - |
| Description of the crime: | Hacking the KBR APM. Funds were debited from the bank's correspondent account and transferred to individual accounts in various Russian banks |
| Damage (million rubles): | 677 |
| Maximum penalty (years of imprisonment): | - |
| Information about criminals: | criminal group “Buhtrap", 50 people |
24. The plot "Theft from the bank "Globex"":
a) "Hackers came running to SWIFT", - Kommersant, 2017
b) "Hackers came to Globex", - Kommersant, 2017
c) "Hackers stole $1 million from a subsidiary bank of VEB", - Vedomosti, 2017
| Type of crime: | unauthorized transfers from bank accounts |
| Articles of the Criminal Code of the Russian Federation: | - |
| Description of the crime: | hacking the bank's network, withdrawing funds via the SWIFT payment system |
| Damage (million rubles): | 60 |
| Maximum penalty (years of imprisonment): | - |
| Information about criminals: | Cobalt Crime Group |
25. The plot "Theft from the PIR Bank":
a) "A feast for hackers", - Kommersant, 2018
b) " How do you like this, Carbanak?", - Group-IB, 2018
| Type of crime: | unauthorized transfers from bank accounts |
| Articles of the Criminal Code of the Russian Federation: | - |
| Description of the crime: | At the end of May 2018, hackers compromised a router in one of PIR Bank's divisions and gained access to its local network. The attackers got to the KBR automated workstation (automated workplace of a Bank of Russia client), formed payment orders, and on July 3 sent several tranches of money "on the flight". In total, hackers tried to steal about 58 million rubles. Transfers went to pre-prepared accounts and plastic cards in 17 banks out of the top 50, most of them were immediately cashed out by the hackers ' accomplices-money mule |
| Damage (million rubles): | 58 |
| Maximum penalty (years of imprisonment): | - |
| Information about criminals: | criminal group, MoneyTaker |
26. The plot "A group of 14 hackers robbing banks":
a) "The hacker's remorse program worked", - Kommersant, 2017
b) "A boxer from Ukraine led a group of hackers who stole 1 billion rubles from banks," - <url>, 2016
c) "The court breaks into a hacker network," - Kommersant, 2017
| Type of crime: | unauthorized transfers from bank accounts, theft of cash from ATMs or payment terminals |
| Articles of the Criminal Code of the Russian Federation: | Article 159.6, Article 158, part 2 of Article 210 |
| Description of the crime: | a) The theft was carried out using a special program that allowed you to withdraw money from the accounts of bank customers, and then restore the balance at the expense of the funds of the financial structures themselves. b) Theft of cash from ATMs, using special devices that allow you to control the process of issuing banknotes |
| Damage (million rubles): | 1000 |
| Maximum penalty (years of imprisonment): | 7 |
| Information about criminals: | a criminal group of 14 men |
27. The story "Hacker group Lurk":
a) "Lurk Banking Trojan: specially designed for Russia", — Securelist.ru, 2016
b) "Employees of the Ministry of Internal Affairs of Russia and the Federal Security Service of Russia detained Internet hackers", - The Ministry of Internal Affairs of Russia, 2016
c) "Hunting for Lurk", — Securelist.ru, 2016
| Type of crime: | unauthorized transfers from the bank's accounts, unauthorized transfers (debits) from the bank's clients ' accounts |
| Articles of the Criminal Code of the Russian Federation: | Part 1 and 2 of article 210 |
| Description of the crime: | use of malicious code that replaces payment details on the client side of the RBS system, attacks on the KBR AWP |
| Damage (million rubles): | 2000 |
| Maximum penalty (years of imprisonment): | - |
| Information about criminals: | Lurk criminal group consisting of 50 members |
28. The plot "Hackers of Popelsha":
a) "Cyber fraudsters convicted in Moscow for stealing money through online bank accounts", - Interfax, 2018
b) "The court found members of the group guilty of stealing 12.5 million rubles from 7,000 Russian bank accounts", - Group-IB, 2018
| Type of crime: | unauthorized transfers (debits) from the bank's customer accounts |
| Articles of the Criminal Code of the Russian Federation: | article 272, article 273, article 159 |
| Description of the crime: | criminals used a computer virus to steal the identification data of bank customers, gain access to bank accounts and transfer money to themselves |
| Damage (million rubles): | 12,5 |
| Maximum penalty (years of imprisonment): | 8 |
| Information about criminals: | a criminal group consisting of 2 23-year-old men, an accomplice, a 19-year-old man and other participants |
Main characteristics of crimes
The number of crimes considered is 28.
The minimum damage caused by a crime is 660 thousand rubles.
The maximum damage caused by the crime is 2 billion rubles.
The minimum penalty for a crime is 5 years in prison.
The maximum penalty for the crime is 8 years in prison.
Crimes committed by women:
- unauthorized transfers (debits) from the bank's customer accounts.
Crimes committed by men:
- unauthorized transfers (debits) from the bank's customer accounts;
- unauthorized transfers from bank accounts;
- theft of cash from ATMs or payment terminals.
The maximum size of a criminal group is 50 members.
Crime analysis
Crimes of this group are classic hacker crimes, among which the following typical scenarios can be distinguished::
- Theft of cash from ATMs by running malware on them.
- Theft of bank money by conducting "transaction cancellation" attacks in international payment systems (IPSS).
- Theft of a bank's money by hacking its corporate network and making unauthorized transfers from its correspondent accounts.
- Theft of clients ' money by obtaining their banking details and accessing remote banking systems.
The type of crimes and the damage they cause depends to a greater extent on the qualifications and to a lesser extent on the number of groups that committed them.
For example, there are crimes committed by a group of 5 participants, as a result of which 3 million rubles were stolen, and there are crimes committed by 2 bandits, but caused damage of 60 million rubles. At the same time, the maximum damage was caused by the actions of professional criminal groups with dozens of participants. These gangs can safely be called "hacker enterprises", since they committed so many crimes that they even posted job vacancies to fulfill all their plans.
Among all the crimes considered, we can single out the actions of a criminal group consisting of two women and their male accomplice who robbed Sberbank customers. Of interest is the fact that the criminals were not particularly gifted hackers who developed clever Trojans or used 0-day exploits, instead they rummaged in the trash cans next to Sberbank ATMs, found checks containing bank account details, and then made unauthorized transfers using regular Sberbank funds.Online".
AGGREGATE ANALYSIS OF ALL CRIMES
Up to this point, we have analyzed crimes by groups. Now we will conduct a generalized analysis of all crimes in the sample.
Information about crimes
Note. When calculating damages from crimes involving several types of illegal actions (for example, fraud in the field of lending and unauthorized transfers from bank accounts), the total damage is evenly distributed among all types.
In terms of the total number of crimes, the TOP 3 types of crimes will be:
- unauthorized transfers (debits) from the bank's customer accounts (29.1%);
- credit fraud (20.9%);
- theft of cash from ATMs or payment terminals (12.7%);
assault on a bank branch (12.7%);
In terms of the total amount of damage, the TOP 3 types of crimes will be:
- credit fraud (44.3%);
- unauthorized transfers from bank accounts (23.2%);
- securities fraud (14.8%)
The most dangerous type of crime is recognized as "fraud in the field of lending", since it occupies the first place in terms of damage and the second in terms of the number of crimes committed.
The crime that caused the maximum damage is securities fraud, which caused losses of 4.5 billion rubles to Otkritie Bank.
The crime for which the maximum penalty is imposed is robberies on bank branches in the Sverdlovsk region, for which one of the bandits was imprisoned for 14 years.
The maximum amount of cash that criminals stole is 780 million rubles (stolen from the cash register by the former owner of Ergobank).
The maximum amount of cash stolen by criminals who are not employees of the bank is 23 million rubles (assault on a branch of a Moscow bank).
The maximum amount of money stolen by hackers due to hacking into the bank's IT systems is quite difficult to reliably determine, since the size of the theft attempt and the size of the actual stolen money are always different. The maximum theft attempt is 1 billion rubles. 400 million rubles (attempted theft from the bank "Ring of the Urals"). There is no reliable information about the amount of money actually stolen.
Personnel-related risks
Positions of criminals who are employees (or owners) of the bank:
- owner of the bank;
- Chairman of the bank's Board of Directors;
- president of the bank;
- Chairman of the bank's Management Board;
- Deputy Chairman of the bank's Management Board;
- Vice-President of the bank;
- Director of the bank's regional branch;
- director of the bank's branch;
- bank branch manager;
- head of the additional office;
- acting Manager of the bank's operational office;
- Head of the Credit and deposit Department;
- Head of Small Business Lending Department;
- Head of the Corporate Customer Service Sector;
- Chief economist of the additional office;
- consultant manager of the bank's branch sales department;
- sales manager;
- leading manager of the bank;
- bank manager;
- client manager;
- financial expert;
- cashier;
- collection officer.
It is definitely impossible to answer the question of which employee is the most dangerous for the bank. In this case, the following patterns can be distinguished:
- Everyone steals where they can steal. The bank's top management steals from the bank. Lower-level specialists steal mostly from customers. Middle managers steal from customers and from the bank.
- Top management is less likely to commit crimes, but the damage from them is higher. Mid-level managers and specialists steal more often, but the damage from theft is less.
- Women-junior and mid-level managers of the bank-are at risk of committing crimes related to fraud or theft of cash.
Information about criminals and patterns in their actions
Crimes committed by women:
- unauthorized transfers (debits) from the bank's customer accounts;
- theft of cash from a bank's cash register;
- credit fraud;
- securities fraud;
- stealing bank money.
Crimes committed by men:
- theft of cash from ATMs or payment terminals;
- assault on a bank branch
- theft of cash from a bank's cash register;
- unauthorized transfers (debits) from the bank's customer accounts;
- unauthorized transfers from bank accounts
- theft of cash during collection;
- credit fraud;
- stealing bank money.
The age of the perpetrators is from 19 to 62 years.
The maximum size of criminal groups is 50 participants.
The analysis of crimes revealed the following patterns:
- Lone hackers tend to steal from customers; hacker groups "work" on both customers and banks.
- Crimes against banks bring maximum income to criminals
- Crimes committed by groups cause more damage than crimes committed by individuals.
- Men are involved in almost any type of crime. Women do not commit violent crimes or conduct computer attacks.
- Most crimes are committed at the most efficient age of 25-45 years.
- The type of crimes and the damage they cause depends to a greater extent on the qualifications and to a lesser extent on the number of groups that committed them.
Forecasts
The current situation with "computer" crimes, in which they are highly profitable and poorly disclosed, suggests that in the "classic" organized criminal groups (OPGs), along with brigades dealing with "traditional" crimes (racketeering, drugs, etc.), hacker departments will appear in the near future.Part 7 - Basic Threat Model

This article presents a basic model of threats to the information security of bank wire transfers made through the payment system of the Bank of Russia.
The threats presented here are valid for almost any bank in the Russian Federation, as well as for any other organizations that use thick clients with cryptographic payment confirmation for settlements.
This threat model is designed to ensure practical security and generate internal bank documentation in accordance with the requirements of Bank of Russia Regulations No. 552-P of August 24, 2016 and No. 382-P of June 9, 2012.
The use of information from the article for illegal purposes is prosecuted by law.
Modeling methodology
Structure of the threat model
One of the most successful ways to simulate computer attacks today is Kill chain. This method represents a computer attack as a sequence of steps performed by attackers to achieve their goals.
Most of the stages are described in the MITRE ATT&CK Matrix, but there is no decoding of the final actions — "Actions" (the last stage of the Kill chain), for which the attackers carried out the attack and which, in fact, are stealing money from the bank. Another problem with using the classic Kill chain for threat modeling is the lack of a description of availability-related threats.
This threat model is designed to compensate for these shortcomings. To do this, it will formally consist of two parts:
- The first one will describe accessibility issues.
- The second one, which is a classic Kill chain with the last stage decrypted, will describe a "computer" theft of money from a bank.
Methodology for forming a threat model
The main requirements for the created threat model were:
- keep it compact and minimize duplication,
- complete threat identification and easy model refinement,
- enabling both business professionals and technicians to work with the model.
To achieve these goals, the model was built on the basis of the "threat tree" methodology, which was slightly improved:
- Threats were described starting from the business level, and gradually decomposed into technical components.
- Threats specific to typical elements of the information infrastructure (for example, network connections, cryptographic information protection systems,...) they were grouped into standard threat models.
- Further, when modeling threats specific to typical elements of the information infrastructure, instead of duplicating the threat description, a link to the corresponding standard model was given.
How to apply this threat model to real objects
Applying this threat model to real objects should begin with clarifying the description of the information infrastructure, and then, if necessary, conduct a more detailed decomposition of threats.The procedure for updating threats described in the model should be carried out in accordance with the organization's internal documents. In the absence of such documents, they can be developed on the basis of the methods discussed in the previous article of the study.
Features of the threat model design
This threat model uses the following design rules:
- The threat model is a tree of threats. The threat tree is written as a hierarchical list, where each element of the list corresponds to a node in the tree and, accordingly, to a specific threat.
- The name of the threat starts with the threat ID, which looks like:
Y<Threat Code>
where "Y — is short for threat, and "Threat code" is the threat number in the hierarchical list (threat tree). - The threat description can contain two blocks:
- Explanations contain explanations of the threat described. Examples of threat implementation, explanations of decisions made during decomposition, modeling restrictions, and other information can be provided here.
- The decomposition contains a hierarchical list of child threats.
- When decomposing threats by default, it is assumed that the implementation of at least one child threat leads to the implementation of the parent threat. If the implementation of the parent threat depends on the implementation of child threats in a different way, then the type of dependency is indicated at the end of the line describing the parent element:
- (I) - the implementation of the parent threat occurs only when all child threats are implemented.
- (Scenario) - the implementation of the parent threat occurs in a certain specific scenario or algorithm for implementing child threats.
- Links to threats described in the same or other threat models follow the template: Link: "< Name of the threat model>.<Name of the threat>".
- If the name of a child threat starts with<...>, it means that the full name of the parent threat must be inserted instead of<...>.
Basic model of threats to information security of bank non-cash payments
The security object for which the threat model (scope)is applied
The scope of this threat model applies to the process of non-cash money transfers through the Bank of Russia payment system.
Architecture
The model's coverage area includes the following information infrastructure::
Here:
"Bank of Russia Payment System Section" means a section of information infrastructure that is subject to the requirements of Bank of Russia Regulation No. 552-P of August 24, 2016. The criterion for classifying an information infrastructure as a BR substation site is processing of electronic messages in the UFEBS format at information infrastructure facilities.
"Electronic message transmission channel" includes the bank's communication channel with the Central Bank of the Russian Federation, built through a specialized telecom operator or modem connection, as well as an electronic message exchange mechanism that operates using a courier and alienable machine data carriers (OMNI).
The list of premises that fall within the threat model's coverage area is determined by the criterion of whether they contain information infrastructure facilities that are involved in money transfers.
Model Restrictions
This threat model applies only to the option of organizing a payment infrastructure with the KBR APM, which combines encryption and electronic signature functions, and does not consider the case of using the KBR-N APM, where the electronic signature is performed "on the ABS side".
Top-level security threats
Decomposition
Y1. Termination of the non-cash transfer system.
Y2. Theft of funds during the operation of the non-cash transfer system.
Y1. Termination of the non-cash transfer system
Explanations
Potential damage from the implementation of this threat can be estimated based on the following assumptions:
- Bank account service agreements concluded between clients and the bank usually contain a note stating how long the bank is required to perform the payment. Violation of the terms specified in the agreement entails the bank's liability to the client.
- If the bank suddenly stops executing payments, it will raise questions about its financial stability, and, as a result, may provoke a massive outflow of deposits.
- Continuity of payments is one of the conditions for maintaining a banking license. Systematic failures and failures can raise serious questions to the bank from the Central Bank of the Russian Federation and lead to revocation of the license.
In general, the maximum allowable delay in payment execution can be considered one flight during a business day. A further increase in the delay will lead to more and more damage to the bank.
When decomposing this threat, the following documents were taken into account:
- The BSI Threat catalog.
- Recommendations in the field of standardization of the Bank of Russia RS BR IBBS-2.2-2009. Ensuring information security of organizations of the banking system of the Russian Federation.
- GOST R 51275-2006 Information security. An informatization object. Factors affecting the information. General provisions.
Decomposition
Y1. 1. Problems with the equipment or data carriers used in making transfers:
Y1. 1. 1. Failures and failures.
Y1. 1. 2. Theft.
Y1. 1. 3. Loss.
Y1. 2. Destruction of programs or data necessary for making transfers.
Y1. 3. Malicious actors perform denial-of-service (DoS, DDoS) attacks on technical means and communication channels used for making transfers.
Y1. 4. Inability to exchange electronic messages with the payment system of the Central Bank of the Russian Federation (S):
Y1.4.1.<...>, carried out through network connections:
Y1. 4. 1. 1. Inoperable communication channels with the Central Bank of the Russian Federation (S):
Y1. 4. 1. 1. 1. < ... > provided by a specialized telecom operator.
Y1.4.1.1.2. <...>, organized as a modem connection.
U1. 4. 1. 2. Termination of information used to authenticate a network connection with the Central Bank of the Russian Federation.
Y1. 4. 2.<...>, carried out by courier on alienated machine information carriers (OMNI):
Y1. 4. 2. 1. Lack of properly executed documents:
Y1.4.2.1.1 <...>, confirming the courier's credentials.
Y1.4.2.1.2 <...>, accompanying payments on OMNI.
Y1. 5. Termination of cryptographic keys used to protect electronic messages:
Y1. 5. 1. Expiration of cryptographic keys.
Y1. 5. 2. Compromise of cryptographic keys.
U1. 5. 3. Provocation by intruders of the Central Bank of the Russian Federation certification center to block the operation of the bank's cryptographic keys.
Y1. 6. Absence at the workplace of persons involved in making non-cash payments.
Y1. 7. Use of outdated versions of the software used for making non-cash transfers.
Y1. 8. The occurrence of conditions in the premises under which it is impossible for the normal functioning of technical means, communication channels and personnel involved in transfers:
Y1. 8. 1. Lack of power supply.
Y1. 8. 2. Significant violations of the temperature regime (overheating, hypothermia).
Y1. 8. 3. Fire.
Y1. 8. 4. Flooding of the room.
Y1. 8. 5. Collapse or threat of collapse of premises.
Y1. 8. 6. Armed attack.
Y1. 8. 7. Radioactive or chemical contamination.
Y1. 8. 8. Strong electromagnetic interference.
Y1. 8. 9. Epidemics.
Y1. 9. Administrative termination of access to buildings or premises where the information infrastructure used for making payments is located:
U1. 9. 1. Blocking access by the authorities:
U1. 9. 1. 1. Conducting searches or other operational investigative measures.
Y1. 9. 1. 2. Holding cultural events, religious holidays, etc.
Y1. 9. 2. Blocking access by the owner:
Y1. 9. 2. 1. Conflict of economic entities.
У1.10. The effect of force majeure circumstances (natural disasters, catastrophes, mass riots, terrorist attacks, military operations, zombie apocalypse,...).
Y2. Theft of funds during the operation of the non-cash transfer system
Explanations
Theft of funds during the operation of a non-cash transfer system is the theft of non-cash funds with their subsequent or simultaneous withdrawal from the victim bank.
Theft of non-cash funds is an unauthorized change in the customer's or bank's account balance. These changes may occur as a result of:
- abnormal change in the account balance;
- unauthorized intrabank or interbank money transfer.
We will call an abnormal change in the account balance actions that are not regulated by the bank's internal documentation, as a result of which an unauthorized decrease or increase in the bank account balance occurred. Examples of such actions can be: making a fictitious bank transaction, directly changing the balance in a storage location (for example, in a database), and other actions.
An abnormal change in the account balance is usually accompanied by regular operations to spend stolen funds. Such operations include:
- cashing out money at ATMs of the victim bank,
- making money transfers to accounts opened with other banks,
- making online purchases,
- etc.
An unauthorized transfer of funds is a transfer made without the consent of persons who have the right to dispose of funds and, as a rule, made by executing a forged order for the transfer of funds by the bank.
Fake money transfer orders can be generated either through the fault of customers or the bank. In this threat model, only threats that are within the bank's area of responsibility will be considered. In this model, only payment orders will be considered as money transfer orders.
In general, it can be assumed that the bank's processing of intrabank transfers is a special case of processing interbank transfers, so to preserve the compactness of the model, only interbank transfers will be considered in the future.
Theft of non-cash funds can be performed both in the execution of outgoing payment orders and in the execution of incoming payment orders. At the same time, we will refer to the outgoing payment order as a payment order sent by the bank to the Bank of Russia payment system, and we will refer to the incoming payment order as a payment order received by the bank from the Bank of Russia payment system.
Decomposition
Y2. 1. Execution of fake outgoing payment orders by the bank.
Y2. 2. Execution of fake incoming payment orders by the bank.
Y2. 3. Abnormal changes in account balances.
Y2. 1. Execution of fake outgoing payment orders by the bank
Explanations
The main reason why a bank can execute a fake payment order is due to its introduction by intruders into the business process of payment processing.
Decomposition
Y2. 1. 1. Introduction of a fake outgoing payment order into the business process of payment processing by intruders.
Y2. 1. 1. Introduction of a fake outgoing payment order into the business process of payment processing by intruders
Explanations
Decomposition of this threat will be performed by elements of the information infrastructure in which a fake payment order may be introduced.
| Elements | Decomposition of the threat "Y2. 1. 1. Introduction of a fake outgoing payment order into the business process of payment processing by intruders" |
| Bank Operator | Y2. 1. 1. 1. |
| RBS Server | Y2. 1. 1. 2. |
| DBO-ABS Integration Module | У2.1.1.3. |
| ABS | У2.1.1.4. |
| ABS-CBD Integration Module | Y2. 1. 1. 5. |
| ARM OF the CBD | Y2. 1. 1. 6. |
| CBD-UTA Integration Module | Y2. 1. 1. 7. |
| UTA | Y2. 1. 1. 8. |
| Electronic message transmission channel | Y2. 1. 1. 9. |
Decomposition
Y2. 1. 1. 1.<...> in the "Bank Operator" element.
Y2. 1. 1. 2.<...> in the "RBS Server" element.
Y2. 1. 1. 3.<...> in the "DBO-ABS Integration Module" element.
Y2. 1. 1. 4.<...> in the " ABS " element.
Y2. 1. 1. 5.<...> in the "ABS-CBD Integration Module" element.
Y2.1.1.6 .<...> in the "APM KBR" element.
Y2.1.1.7 .<...> in the "CBD-UTA Integration Module" element.
Y2. 1. 1. 8.<...> in the "UTA" element.
Y2. 1. 1. 9.<...> in the "Email transmission channel" element.
Y2. 1. 1. 1.<...> in the "Bank Operator" element
Explanations
When accepting a paper payment order from the client, the operator enters an electronic document based on it in the ABS. The vast majority of modern ABS systems are based on the client-server architecture, which makes it possible to analyze this threat based on a typical threat model of client-server information systems.
Decomposition
Y2. 1. 1.1. 1.The bank's operator accepted a forged paper payment order from an attacker who introduced himself as a bank customer.
U2. 1. 1. 1. 2.A fake electronic payment order was entered in the ABS on behalf of the bank's operator.
Y2.1.1.1.2.1. The operator acted with malicious intent or made an unintentional mistake.
Y2.1.1.1.2.2. Malefactors acted on behalf of the operator:
Y2.1.1.1.2.2.1. Link: "Standard threat model. An information system based on the client-server architecture. Y1. Performing unauthorized actions by intruders on behalf of a legitimate user".
Note. Typical threat models will be discussed in the following articles.
Y2. 1. 1. 2.<...> in the"RBS Server" element
Decomposition
Y2. 1. 1. 2. 1. The RBS server accepted a duly certified payment order on behalf of the client, but it was drawn up by intruders without the client's consent:
Y2.1.1.2.1.1. Link: "Standard threat model. An information system based on the client-server architecture. Y1. Performing unauthorized actions by intruders on behalf of a legitimate user".
Y2. 1. 1. 2. 2. Attackers introduced a fake payment order into the RBS server:
Y2.1.1.2.2.1. Link: "Standard threat model. An information system based on the client-server architecture. Y2. Unauthorized modification of protected information during its processing by the server part of the information system".
У2.1.1.3. <...> in the "DBO-ABS Integration Module"element
Decomposition
Y2. 1. 1. 3. 1. Link: "Standard threat model. Integration module. Y1. Introduction of fake information by intruders through the integration module".
У2.1.1.4. <...> in the"ABS" element
Decomposition
Y2. 1. 1. 4. 1. Link: "Standard threat model. An information system based on the client-server architecture. Y2. Unauthorized modification of protected information during its processing by the server part of the information system".
Y2. 1. 1. 5.<...> in the "ABS-CBD Integration Module" element
Decomposition
Y2. 1. 1. 5. 1. Link: "Standard threat model. Integration module. Y1. Introduction of fake information by intruders through the integration module".
Y2. 1. 1. 6.<...> in the "APM KBR" element
Explanations
The main function of the KBR automated control system in terms of information security is cryptographic protection of electronic messages exchanged by the bank with the payment system of the Bank of Russia. All outgoing payment documents are encrypted using the Bank of Russia's public keys and the bank's private electronic signature keys.
Decomposition (S):
Y2. 1. 1. 6. 1. Encryption of a fake payment order using the Bank of Russia's public keys:
Y2.1.1.6.1.1. Link: "Standard threat model. Cryptographic information protection system. Y2. Encryption of forged data on behalf of a legitimate sender".
Y2. 1. 1. 6. 2. Electronic signature of a forged payment order on the bank's private keys:
Y2.1.1.6.2.1. Link: "Standard threat model. Cryptographic information protection system. Y4. Creating an electronic signature of a legitimate signatory under forged data".
Y2. 1. 1. 7.<...> in the "CBD-UTA Integration Module"element
Explanations
In accordance with the technological process of payment processing, electronic messages on the KBR — CBR AWP section are signed with an electronic signature and encrypted. Accordingly, the introduction of a fake payment order at this stage is possible only if the attackers managed to bypass the standard cryptographic protection procedure to encrypt and sign the fake payment order.
Decomposition (S):
Y2. 1. 1. 7. 1. Link: "Current threat model. Y2. 1. 1. 6.<...> in the "APM KBR" element.
Y2. 1. 1. 7. 2. Link: "Typical threat model. Integration module. Y1. Introduction of fake information by intruders through the integration module".
Y2. 1. 1. 8.<...> in the"UTA" element
Explanations
UTA is essentially an information robot that exchanges cryptographically secure electronic messages with the Central Bank of the Russian Federation. Threats to the information security of this element correspond to the threats of integration modules.
Decomposition (S):
Y2. 1. 1. 8. 1. Link: "Current threat model. Y2. 1. 1. 6.<...> in the "APM KBR" element.
Y2. 1. 1. 8. 2. Link: "Typical threat model. Integration module. Y1. Introduction of fake information by intruders through the integration module".
Y2. 1. 1. 9.<...> in the"Email transmission channel" element
Decomposition (S):
Y2. 1. 1. 9. 1. Link: "Current threat model. Y2. 1. 1. 6.<...> in the "APM KBR" element.
U2. 1. 1. 9. 2. Transfer of a fake payment order to the Bank of Russia by intruders:
Y2.1.1.9.2.1. <...> during a communication session with the Bank of Russia established on behalf of the bank.
Y2.1.1.9.2.2. <...> with the help of an OMNI courier.
Y2. 2. Execution of a fake incoming payment order by the bank
Decomposition
Y2. 2. 1. Introduction of a fake incoming payment order into the business process of payment processing by intruders.
Y2. 2. 1. Introduction of a fake incoming payment order into the business process of payment processing by intruders
Explanations
Payment orders are encrypted and signed with an electronic signature in the KBR — Bank of Russia Automated Payment System section. In general, payment orders are not cryptographically secure in the KBR — ABS AWP section.
Payment orders received by the bank are encrypted on the bank's public keys and signed with the Bank of Russia's private keys. The key cryptographic protection system is based on the private public key infrastructure (private PKI), implemented on the basis of the SCAD Signature SCSI and includes: The certification center of the Bank of Russia and its users is credit organizations. All participants in the public key infrastructure trust certificates issued by the Central Bank of the Russian Federation certification center.
Thus, in order to implement a fake incoming payment order, attackers need to compromise the recipient bank's public encryption keys and electronic signature keys, whose certificates are trusted by the recipient bank.
Decomposition of this threat will be performed based on infrastructure elements where fake incoming payment orders may be introduced.
| Elements | Decomposition of the threat "Y2. 2. 1. Introduction of a fake incoming payment order into the business process of payment processing by intruders" |
| ABS | Y2. 2. 1. 1. |
| ABS-CBD Integration Module | Y2. 2. 1. 2. |
| ARM OF the CBD | Y2. 2. 1. 3. |
| CBD-UTA Integration Module | Y2. 2. 1. 4. |
| UTA | Y2. 2. 1. 5. |
| Electronic message transmission channel | Y2. 2. 1. 6. |
Decomposition
Y2. 2. 1. 1.<...> in the " ABS " element.
Y2. 2. 1. 2.<...> in the "ABS-CBD Integration Module" element.
Y2.2.1.3 .<...> in the "APM KBR" element.
Y2.2.1.4 .<...> in the "CBD-UTA Integration Module" element.
Y2. 2. 1. 5.<...> in the "UTA" element.
Y2. 2. 1. 6.<...> in the "Email transmission channel" element.
Y2. 2. 1. 1.<...> in the"ABS" element
Decomposition
Y2. 2. 1. 1. 1. Link: "Standard threat model. An information system based on the client-server architecture. Y2. Unauthorized modification of protected information during its processing by the server part of the information system".
Y2. 2. 1. 2.<...> in the "ABS-CBD Integration Module" element
Decomposition
Y2. 2. 1. 2. 1. Link: "Standard threat model. Integration module. Y1. Introduction of fake information by intruders through the integration module".
Y2. 2. 1. 3.<...> in the "APM KBR" element
Explanations
When processing incoming payment documents, the AWP KBR is the last line of defense, whose task is to decrypt and verify the integrity of incoming cryptographically protected electronic messages. The protection of this stage will be neutralized if the Automated Control System of the KBR, after receiving a fake payment order at the entrance, informs that the electronic signature under it is correct.
Decomposition
Y2. 2. 1. 3. 1. Successful verification of the electronic signature of a fake incoming payment order:
Y2.2.1.3.1.1 Link: "Standard threat model. Cryptographic information protection system. Y5. Getting a positive result of checking the electronic signature of forged data".
Y2. 2. 1. 4.<...> in the "CBD-UTA Integration Module"element
Explanations
Starting from this element and continuing to the Bank of Russia payment system, attackers lose the possibility of unauthorized access to the cryptographic information protection system (ICSI). Therefore, all data coming from the Integration Module to the KBR AWP must be correctly encrypted and signed. For encryption, attackers must use the bank's public keys, and for electronic signatures, private keys that the bank trusts with certificates.
Decomposition (S):
Y2. 2. 1. 4. 1. Neutralizing the cryptographic protection of incoming electronic messages (S):
Y2.2.1.4.1.1. Encryption of a fake payment order using the bank's public keys:
Y2.2.1.4.1.1.1. Link: "Standard model threats. Cryptographic information protection system. Y2. Encryption of forged data on behalf of a legitimate sender".
Y2.2.1.4.1.2. Electronic signature of a fake payment order based on private keys trusted by the bank:
Y2.2.1.4.1.2.1. Link: "Standard threat model. Cryptographic information protection system. Y4. Creating an electronic signature of a legitimate signer under forged data".
Y2. 2. 1. 4. 2. Link: "Standard threat model. Integration module. Y1. Introduction of fake information by intruders through the integration module".
Y2. 2. 1. 5.<...> in the"UTA" element
Decomposition:
Y2. 2. 1. 5. 1. Link: "Current threat model. Y2. 2. 1. 4.<...> in the "CBD-UTA Integration Module" element.
Y2. 2. 1. 6.<...> in the"Email transmission channel" element
Decomposition (S):
Y2. 2. 1. 6. 1. Link: "Current threat model.Y2. 2. 1. 4. 1. Neutralizing the cryptographic protection of incoming electronic messages".
Y2. 2. 1. 6. 2. Receiving a fake payment order from the Central Bank of the Russian Federation:
Y2.2.1.6.2.1. <...> during a communication session with the Bank of Russia established by the Bank of on behalf of the bank.
Y2.2.1.6.2.2. <...> with the help of an OMNI courier.
Conclusion
The next article in the series will cover typical threat models.:Part 8 - Typical threat models
This article completes a series of publications devoted to ensuring information security of bank non-cash payments. Here we'll look at the typical threat models referenced in the base model:- Typical threat model. Network connection.
- Typical threat model. An information system based on the client-server architecture.
- Typical threat model. Access control system.
- Typical threat model. Integration module.
- Typical threat model. Cryptographic information protection system.
Information for readers who are familiar with the study, starting with this publication.HABRO-WARNING !!! Dear habrovchane, this is not an entertainment post.
The 40+ pages of materials hidden under the cut are designed to help people who specialize in banking or information security at work or study. These materials are the final product of the research and are written in a dry, formal tone. In fact, these are blanks for internal information security documents.
Well, the traditional one — "the use of information from the article for illegal purposes is prosecuted by law." Have a productive reading experience!
What the study is about
You are reading a guide for a specialist responsible for ensuring information security of payments in a bank.
TYPICAL THREAT MODEL. NETWORK CONNECTION
The security object for which the threat model (scope)is applied
The object of protection is data transmitted over a network connection that operates in data transmission networks built on the basis of the TCP/IP stack.
Architecture
Description of the architecture elements:
- "End nodes" — nodes that exchange protected information.
- "Intermediate nodes" — elements of the data transmission network: routers, switches, access servers, proxy servers, and other equipment-through which network connection traffic is transmitted. In general, a network connection can function without intermediate nodes (directly between end nodes).
Top-level security threats
Decomposition
Y1. Unauthorized access to the transmitted data.
Y2. Unauthorized modification of the transmitted data.
Y3. Violation of the authorship of the transmitted data.
Y1. Unauthorized access to the transmitted data
Decomposition
Y1. 1. < ... > performed on end or intermediate nodes:
Y1. 1. 1. < ... > by reading data while they are in the node's storage devices:
Y1.1.1.1. <...> in RAM.
Explanation of Y1. 1. 1. 1.
For example, during data processing by the node's network stack.
У1.1.1.2. <...> in non-volatile memory.
Explanation of Y1. 1. 1. 2.
For example, when storing transmitted data in a cache, temporary files, or paging files.
Y1. 2. < ... > performed on third-party nodes of the data transmission network:
Y1. 2. 1. < ... > by capturing all packets that reach the node's network interface:
Explanation of Y1. 2. 1.
All packets are captured by switching the network card to promiscuous mode (promiscuous mode for wired adapters or monitor mode for wi-fi adapters).
Y1. 2. 2. < ... > by performing man-in-the-middle (MiTM) attacks, but without modifying the transmitted data (not counting network protocol overhead).
Y1. 2. 2. 1. Link: "Standard threat model. Network connection. Y2. Unauthorized modification of the transmitted data".
U1. 3.<...>, carried out due to information leakage through technical channels (TCUI) from physical nodes or communication lines.
U1. 4.<...>, carried out by installing special technical means (STS) at the end or intermediate nodes intended for secret information retrieval.
Y2. Unauthorized modification of the transmitted data
Decomposition
Y2. 1. < ... > performed on end or intermediate nodes:
Y2. 1. 1. < ... > by reading and modifying data while it is in the storage devices of nodes:
Y2.1.1.1. <...> in RAM:
Y2. 1. 1.2.<...> in non-volatile memory:
Y2. 2. < ... > performed on third-party nodes of the data transmission network:
Y2. 2. 1. < ... > by performing man-in-the-middle (MiTM) attacks and redirecting traffic to the attackers 'node:
Y2.2.1.1. Physically connecting the attackers' equipment when the network connection is broken.
Y2. 2. 1. 2. Attacks on network protocols:
Y2.2.1.2.1. <...> management of virtual local area networks (VLANs):
Y2.2.1.2.1.1. VLAN hopping.
Y2.2.1.2.1.2. Unauthorized modification of VLAN settings on switches or routers.
У2.2.1.2.2. <...> traffic routing:
Y2.2.1.2.2.1. Unauthorized modification of static routing tables for routers.
Y2.2.1.2.2.2. Attackers announce fake routes via dynamic routing protocols.
Y2.2.1.2.3. <...> Automatic configuration:
Y2.2.1.2.3.1. Rogue DHCP.
У2.2.1.2.3.2. Rogue WPAD.
Y2.2.1.2.4. <...> addressing and name resolution:
Y2.2.1.2.4.1. ARP spoofing.
У2.2.1.2.4.2. DNS spoofing.
Y2.2.1.2.4.3. Making unauthorized changes to local hostname files (hosts, lmhosts, etc.)
Y3. Violation of the authorship of the transmitted data
Decomposition
Y3. 1. Neutralizing the mechanisms for determining the authorship of information by specifying false information about the author or data source:
Y3. 1. 1. Changing the information about the author contained in the transmitted information.
Y3. 1. 1. 1. Neutralization of cryptographic protection of integrity and authorship of transmitted data:
Y3. 1. 1. 1. 1. Reference: "Standard threat model. Cryptographic information protection system.
Y4. Creation of an electronic signature of a legitimate signatory under forged data".
Y3. 1. 1. 2. Neutralization of copyright protection of transmitted data, implemented using one-time confirmation codes:
Y3. 1. 1. 2. 1. SIM swap.
Y3. 1. 2. Changing information about the source of transmitted information:
Y3. 1. 2. 1. IP spoofing.
У3.1.2.2. MAC spoofing.
TYPICAL THREAT MODEL. AN INFORMATION SYSTEM BASED ON THE CLIENT-SERVER ARCHITECTURE
The security object for which the threat model (scope)is applied
The object of protection is an information system built on the basis of the client-server architecture.
Architecture
Description of the architecture elements:
- "Client" – the device on which the client part of the information system operates.
- "Server" – the device on which the server part of the information system operates.
- "Data warehouse" — a part of the server infrastructure of an information system intended for storing data processed by the information system.
- "Network connection" — an information exchange channel between the Client and the Server that passes through the data transmission network. For a more detailed description of the element model, see " Typical Threat Model. Network connection".
Limitations
When modeling an object, the following restrictions are set::
- The user interacts with the information system within finite time intervals, called work sessions.
- At the beginning of each session, the user is identified, authenticated, and authorized.
- All protected information is stored on the back-end of the information system.
Top-level security threats
Decomposition
Y1. Attackers perform unauthorized actions on behalf of a legitimate user.
Y2. Unauthorized modification of protected information during its processing by the server part of the information system.
Y1. Attackers perform unauthorized actions on behalf of a legitimate user
Explanations
Usually, in information systems, actions are associated with the user who performed them using:
- system operation logs (logs).
- special attributes of data objects that contain information about the user who created or modified them.
In relation to the work session, this threat can be decomposed into:
- <...> performed during the user's session.
- <...> performed outside the user's work session.
A user session can be initiated:
- By the user.
- By intruders.
At this stage, the intermediate decomposition of this threat will look like this:
Y1. 1. Unauthorized actions were performed within the user's session:
Y1. 1. 1.<...>, installed by the attacked user.
Y1. 1. 2. < ... > installed by intruders.
Y1. 2. Unauthorized actions were performed outside the user's session.
From the point of view of information infrastructure objects that can be affected by intruders, the decomposition of intermediate threats will look like this::
| Elements | Threat decomposition | ||
|---|---|---|---|
| Y1. 1. 1. | У1.1.2. | Y1. 2. | |
| Client | Y1. 1. 1. 1. | Y1. 1. 2. 1. | |
| Network connection | У1.1.1.2. | ||
| Server | Y1. 2. 1. |
Decomposition
Y1. 1. Unauthorized actions were performed within the user's session:
Y1. 1. 1.<...>, installed by the attacked user:
Y1. 1. 1. 1. Attackers independently operated from the Client:
Y1. 1. 1. 1. 1 Attackers used standard access tools of the information system:
Y1.1.1.1.1.1. The attackers used the Client's physical I / O facilities (keyboard, mouse, monitor, or touch screen). mobile device):
Y1.1.1.1.1.1.1. The attackers operated during periods of time when the session is active, I / O facilities are available, and the user is not in place.
Y1.1.1.1.1.2. Attackers used remote administration tools (either standard or provided by malicious code) to manage the Client:
Y1.1.1.1.1.2.1. The attackers operated during periods of time when the session is active, I / O tools are available, and the user is unable to use them. out of place.
Y1.1.1.1.1.2.2. The attackers used remote administration tools that are invisible to the attacked user.
Y1. 1. 1. 2. Attackers substituted data in the network connection between the Client and Server, modifying it so that it was perceived as the actions of a legitimate user:
Y1. 1.1.2. 1.Link: "Typical threat model. Network connection. Y2. Unauthorized modification of the transmitted data".
Y1. 1. 1. 3. Attackers forced the user to perform their specified actions using social engineering methods.
Y1. 1. 2 < ... > installed by the attackers:
Y1. 1. 2. 1. The attackers acted from the Client (S):
Y1. 1. 2. 1. 1. The attackers neutralized the access control system of the information system:
Y1.1.2.1.1.1. Link: "Typical threat model. Access control system. Y1. Unauthorized establishment of a work session on behalf of a legitimate user".
Y1. 1. 2. 1. 2. The attackers used the standard access tools of the information system
Y1. 1. 2. 2. The attackers operated from other nodes of the data transmission network from which a network connection can be established with the Server (S):
Y1. 1. 2. 2. 1. The attackers neutralized the differentiation system Information system access number:
U1.1.2.2.1.1. Link: "Standard threat model. Access control system. Y1. Unauthorized establishment of a work session on behalf of a legitimate user".
Y1. 1. 2. 2. 2. The attackers used non-standard means of accessing the information system.
Explanation of Y1. 1. 2. 2. 2.
Attackers could install a standard client of the information system on a third-party node, or they could use non-standard software that implements standard exchange protocols between the Client and the Server.
Y1. 2 Unauthorized actions were performed outside the user's session.
Y1. 2. 1 Attackers performed unauthorized actions, and then made unauthorized changes to the logs of the information system or special attributes of data objects, indicating that the actions performed by them were performed by a legitimate user.
Y2. Unauthorized modification of protected information during its processing by the server part of the information system
Decomposition
Y2. 1. Attackers modify the protected information using standard information system tools and do this on behalf of a legitimate user.
Y2. 1. 1. Link: "Standard threat model. An information system based on the client-server architecture. Y1. Performing unauthorized actions by intruders on behalf of a legitimate user".
Y2. 2. Attackers modify protected information by using data access mechanisms that are not provided for in the normal mode of operation of the information system.
Y2. 2. 1. Attackers modify files containing protected information:
Y2.2.1.1. <...>, using the file management mechanisms provided by the operating system.
Y2.2.1.2. <...> by provoking the recovery of files from an unauthorized modified backup.
Y2. 2. 2. Attackers modify the protected information stored in the database (S):
Y2. 2. 2. 1. Attackers neutralize the DBMS access control system:
Y2. 2. 2. 1. 1. Link: "Standard threat model. Access control system. Y1. Unauthorized establishment of a work session on behalf of a legitimate user".
Y2. 2. 2. 2. Attackers modify information using standard DBMS interfaces to access data.
Y2. 3. Attackers modify the protected information by unauthorized modification of the algorithms of the software processing it.
Y2. 3. 1. The source code of the software is modified.
Y2.3. 1.The machine code of the software is modified.
Y2. 4. Attackers modify protected information by exploiting vulnerabilities in the information system software.
Y2. 5. Attackers modify protected information when it is transmitted between components of the back-end of an information system (for example, a database server and an application server):
Y2. 5. 1. Reference: "Typical threat model. Network connection. Y2. Unauthorized modification of the transmitted data".
TYPICAL THREAT MODEL. ACCESS CONTROL SYSTEM
The security object for which the threat model (scope)is applied
The security object for which this threat model is applied corresponds to the security object of the threat model: "Typical Threat Model. An information system based on the client-server architecture."
In this threat model, a user access control system is understood as an information system component that implements the following functions:
- Identification of users.
- User authentication.
- User authorizations.
- Logging user actions.
Top-level security threats
Decomposition
Y1. Unauthorized establishment of a work session on behalf of a legitimate user.
Y2. Unauthorized elevation of user privileges in the information system.
Y1. Unauthorized establishment of a work session on behalf of a legitimate user
Explanations
The breakdown of this threat will generally depend on the type of user identification and authentication systems used.
This model will only consider a user identification and authentication system that uses a text-based username and password. At the same time, we assume that the user's login is publicly available information known to attackers.
Decomposition
Y1. 1. < ... > by compromising credentials:
Y1.1. 1. Attackers compromised the user's credentials while storing them.
Explanation of Y1. 1. 1.
For example, credentials could be written on a sticker attached to the monitor.
Y1. 1. 2. The user accidentally or maliciously transferred access details to intruders.
Y1. 1. 2. 1. The user spoke the credentials out loud when entering them.
Y1. 1. 2. 2. The user intentionally passed their credentials:
Y1.1.2.2.1. <...> to your work colleagues.
Explanation of Y1. 1. 2. 2. 1.
For example, so that they can replace it during the period of illness.
У1.1.2.2.2. <...> contractors of the employer performing work on information infrastructure objects.
У1.1.2.2.3. <...> to third parties.
Explanation of Y1. 1. 2. 2. 3.
One, but not the only option for implementing this threat is the use of social engineering methods by attackers.
Y1. 1. 3. Attackers picked up credentials by brute force:
Y1.1.3.1. <...> using standard access mechanisms.
Y1.1.3.2. <...> by previously intercepted codes (for example, password hashes) for storing credentials.
Y1. 1. 4. Attackers used malicious code to intercept user credentials.
Y1. 1. 5. Attackers extracted credentials from the network connection between the Client and Server:
Y1. 1.5. 1.Link: "Typical threat model. Network connection. Y1. Unauthorized access to the transmitted data".
Y1. 1. 6. Attackers extracted credentials from the records of monitoring systems:
Y1. 1. 6. 1.<...> video surveillance systems (if keystrokes on the keyboard were recorded during operation).
У1.1.6.2. <...> systems for monitoring employee actions at the computer
Explanation of Y1. 1. 6. 2.
An example of such a system is StuffCop.
Y1. 1. 7. Attackers compromised the user's credentials due to shortcomings in the process of transmitting them.
Explanation of Y1. 1. 7.
For example, transmitting passwords in clear text via email.
Y1. 1. 8. Attackers found out the credentials by monitoring the user's session using remote administration systems.
Y1. 1. 9. Attackers extracted credentials as a result of their leakage through technical channels (TCUI):
Y1. 1. 9. 1. Attackers spied on the user entering credentials from the keyboard:
Y1. 1. 9. 1. 1 Attackers were located in close proximity to the user and saw the user entering credentials data with your own eyes.
Explanation Y1. 1. 9. 1. 1
Such cases can include actions of colleagues at work or when the user's keyboard is visible to visitors of the organization.
Y1. 1. 9. 1. 2 Attackers used additional technical means, such as binoculars or an unmanned aerial vehicle, and saw the login data being entered through a window.
Y1. 1. 9. 2. Attackers extracted credentials from records of radio communication between the keyboard and the computer's system unit if they were connected via a radio interface (for example, Bluetooth).
Y1. 1. 9. 3. The attackers intercepted the credentials due to their leakage through the channel of spurious electromagnetic radiation and interference (PEMIN).
Explanation of Y1. 1. 9. 3.
Examples of the attack are here and here.
Y1. 1. 9. 4. The attacker intercepted the input of credentials from the keyboard by using special technical means (STS) designed to secretly remove information.
Explanation of Y1. 1. 9. 4.
Examples of devices.
Y1. 1. 9. 5. Attackers intercepted the input of credentials from the keyboard by
analyzing the Wi-Fi signal modulated by the user's keystroke process.
Explanation of Y1. 1. 9. 5.
Example of an attack.
Y1. 1. 9. 6. Attackers intercepted the input of credentials from the keyboard by analyzing the sounds of keystrokes.
Explanation of Y1. 1. 9. 6.
Y1. 1. 9. 7. Attackers intercepted the input of credentials from the keyboard of a mobile device by analyzing the accelerometer readings.
Explanation of Y1. 1. 9. 7.
Y1. 1. 10. < ... > previously saved on the Client.
Explanation of Y1. 1. 10.
For example, a user could save a username and password in the browser to access a specific site.
Y1. 1. 11. Attackers compromised credentials due to shortcomings in the process of revoking user access.
Explanation of Y1. 1. 11.
For example, after a user was dismissed, their accounts were not blocked.
Y1. 2. < ... > by exploiting vulnerabilities in the access control system.
Y2. Unauthorized elevation of user privileges in the information system
Decomposition
Y2. 1 <...> by making unauthorized changes to data containing information about user privileges.
Y2. 2 <...> by exploiting vulnerabilities in the access control system.
Y2. 3. < ... > due to shortcomings in the user access control process.
Explanation of Y2. 3.
Example 1. The user was granted more access to work than he needed for official reasons.
Example 2. After the user was transferred to another position, the previously granted access rights were not revoked.
TYPICAL THREAT MODEL. INTEGRATION MODULE
The security object for which the threat model (scope)is applied
Integration module – a set of information infrastructure objects designed to organize information exchange between information systems.
Given the fact that in corporate networks it is not always possible to clearly separate one information system from another, the integration module can also be considered as a link between components within one information system.
Architecture
The generalized scheme of the integration module looks like this:
Description of the architecture elements:
- "Exchange server" – a node / service / component of an information system that performs the function of data exchange with another information system.
- "Intermediary" – a node / service intended for organizing interaction between information systems, but not part of them.
Examples of "Intermediaries" include email services, enterprise service buses ( SoA architecture), third-party file servers, and so on. In general, the integration module may not contain "Intermediaries". - "Data processing software" – a set of programs that implements data exchange protocols and format conversion.
For example, converting data from the UFEBS format to the ABS format, changing message statuses during transmission, and so on. - "Network connection" corresponds to the object described in the typical threat model "Network Connection". Some of the network connections shown in the diagram above may not exist.
Examples of integration modules
Scheme 1. Integration of ABS and AWP KBR via a third-party file server
To execute payments, an authorized bank employee unloads electronic payment documents from the ABS and saves them to a file (in its own format, for example, an SQL dump) on the network folder (\\...\SHARE\) of the file server. Then this file is converted to a set of files in the UFEBS format using a converter script, which is then read by the KBR APM.
After that, an authorized employee — a user of the KBR automated Control System-encrypts and signs the received files and sends them to the Bank of Russia payment system.
When payments are received from the Bank of Russia, the KBR Automated Control System performs their decryption and verification of the electronic signature, and then writes them to the file server as a set of files in the UFEBS format. Before importing payment documents to ABS, they are converted using a converter script from the UFEBS format to the ABS format.
We will assume that in this scheme, the ABS operates on one physical server, the KBR AWP operates on a dedicated computer, and the converter script operates on a file server.
Correspondence of objects of the considered schema to the elements of the integration module model:
"Exchange servers on the ABS side" – the ABS server.
"Exchange servers from the KBR AWP" – the KBR AWP computer.
Intermediary – a third-party file server.
Data Processing Software – a script converter.
Scheme 2. Integration of ABS and AWS KBR when placing a shared network folder with payments on AWS KBR
Everything is similar to Scheme 1, but a separate file server is not used, instead a network folder (\\...\SHARE\) with electronic payment documents is placed on a computer with the KBR APM. The script converter also works on the KBR WORKSTATION.
Correspondence of objects of the considered scheme to the elements of the integration module model:
Similar to Scheme 1, but the "Intermediary" is not used.
Scheme 3. Integration of ABS and AWP KBR-N via IBM WebSphera MQ and implementation of electronic document signing "on the ABS side"
ABS runs on a platform that is not supported by the SCAD Signature SCSI. Outgoing electronic documents are signed on a special electronic signature server (EP Server). The same server verifies the electronic signature of incoming documents from the Bank of Russia.
ABS uploads a file with payment documents in its own format to the Item Instance Server.
The EP server uses a converter script to convert the file to e-mail messages in the UFEBS format. After that, the e-mail messages are signed and transmitted to IBM WebSphere MQ.
The KBR-N AWP accesses IBM WebSphere MQ and receives signed payment messages from there, after which an authorized employee — a user of the KBR AWP — encrypts them and sends them to the payment system of the Bank of Russia.
When payments are received from the Bank of Russia, the KBR-N automated Payment System decrypts them and verifies the electronic signature. Successfully processed payments in the form of decrypted and signed e-mail messages in the UFEBS format are transmitted to IBM WebSphere MQ, from where they are received by the EP Server.
The Item instance server verifies the electronic signature of received payments and saves them to an ABS file. After that, an authorized employee — an ABS user-uploads the resulting file to the ABS in accordance with the established procedure.
Correspondence of objects of the considered schema to the elements of the integration module model:
"Exchange server on the ABS side" – the ABS server.
"Exchange server from the KBR AWP" — the computer of the KBR AWP.
"Intermediary" – the EP Server and IBM WebSphere MQ.
"Data processing software" – a script converter, SCSI SCAD Signature on the Instance Server.
Scheme 4. Integration of the RBS and ABS Server via the API provided by the dedicated exchange server
We will assume that the bank uses several remote banking systems(RBS):
- Internet Client-Bank for individuals (ICB FL);
- "Internet Client-Bank" for legal entities (ICB YUL).
In order to ensure information security, all ABS interaction with RBS systems is carried out through a dedicated exchange server operating within the framework of the ABS information system.
Next, we will consider the process of interaction of the RBS system of the ICB of the legal entity with the ABS.
The RBS server, having received a duly certified payment order from the client, must create a corresponding document in the ABS based on it. To do this, it uses the API to transmit information to the exchange server, which, in turn, enters data into the ABS.
When the client's account balances change, the ABS generates electronic notifications, which are transmitted to the RBS server via the exchange server.
Correspondence of objects of the considered schema to the elements of the integration module model:
"Exchange server on the part of RBS" – the RBS server of IKB YUL.
"Exchange server on the ABS side" – the exchange server.
"Intermediary" – missing.
"Data processing software" – components of the RBS Server responsible for using the exchange server API, components of the exchange server responsible for using the ABS API.
Top-level security threats
Decomposition
Y1. Introduction of fake information by intruders through the integration module.
Y1. Introduction of fake information by intruders through the integration module
Decomposition
Y1. 1. Unauthorized modification of legitimate data when it is transmitted over network connections:
Y1.1.1 Link: "Typical threat model. Network connection. Y2. Unauthorized modification of the transmitted data".
Y1. 2. Transmission of forged data via communication channels on behalf of a legitimate exchange participant:
Y1. 1. 2 Link: "Standard threat model. Network connection. Y3. Violation of the authorship of the transmitted data".
Y1. 3. Unauthorized modification of legitimate data during their processing on Exchange Servers or Intermediaries:
Y1. 3. 1. Link: "Typical threat model. An information system based on the client-server architecture. Y2. Unauthorized modification of protected information during its processing by the server part of the information system".
Y1. 4. Creating fake data on Exchange Servers or Intermediaries on behalf of a legitimate exchange participant:
Y1. 4. 1. Link: "Standard threat model. An information system based on the client-server architecture. Y1. Performing unauthorized actions by intruders on behalf of a legitimate user".
Y1. 5. Unauthorized modification of data during their processing using data processing software:
Y1. 5. 1. < ... > due to unauthorized changes made by intruders to the settings (configuration) of the data processing software.
Y1. 5. 2. < ... > due to unauthorized changes made by intruders to the executable files of the data processing software.
Y1. 5. 3. < ... > due to interactive management of data processing work by intruders.
TYPICAL THREAT MODEL. CRYPTOGRAPHIC INFORMATION PROTECTION SYSTEM
The security object for which the threat model (scope)is applied
The object of protection is the cryptographic information protection system used to ensure the security of the information system.
Architecture
The basis of any information system is the application software (software) that implements its target functionality.
Cryptographic protection is usually implemented by calling cryptographic primitives from the business logic of the application software, which are placed in specialized libraries – cryptokernels.
Cryptographic primitives include low-level cryptographic functions, such as:
- encrypt / decrypt a block of data;
- create / verify an electronic signature for a data block;
- calculate the hash function of the data block;
- generate / upload / upload key information;
- etc.
The business logic of application software uses cryptographic primitives to implement higher-level functionality:
- encrypt the file with the selected recipients ' keys;
- establish a secure network connection;
- inform about the results of electronic signature verification;
- and so on.
The interaction of business logic and the cryptokernel can be performed:
- directly, by calling business logic cryptographic primitives from dynamic libraries of the cryptokernel (. DLL-for Windows, .SO-for Linux);
- indirectly, through cryptographic wrapper interfaces (wrappers), for example, MS Crypto API, Java Cryptography Architecture, PKCS#11, etc. In this case, the business logic accesses the crypto interface, and it broadcasts the call to the corresponding crypto core, which in this case is called a cryptoprovider. Using cryptographic interfaces allows application software to abstract from specific cryptographic algorithms and be more flexible.
There are two typical schemes for organizing a cryptokernel:
The elements in these diagrams can be either separate software modules running on the same computer, or network services interacting within a computer network.
When using systems built according to Scheme 1, the application software and the cryptokernel work within a single cryptographic tool operating environment (SPS), for example, on the same computer running the same operating system. As a rule, the user of the system can run other programs within the same operating environment, including those containing malicious code. In such circumstances, there is a serious risk of leakage of private cryptographic keys.
To minimize the risk, scheme 2 is used, in which the cryptokernel is divided into two parts:
- The first part, together with the application software, works in an untrusted environment, where there is a risk of infection with malicious code. We will call this part the "software part".
- The second part runs in a trusted environment on a dedicated device that contains a private key store. Next, we will call this part-the "hardware part".
The division of a cryptokernel into software and hardware parts is very conditional. There are systems on the market that are built according to the scheme with a shared cryptokernel, but the" hardware " part of which is represented as a virtual machine image-virtual HSM (example).
The interaction of both parts of the cryptokernel occurs in such a way that private cryptographic keys are never transmitted to the software part and, accordingly, cannot be stolen using malicious code.
The interaction interface (API) and the set of cryptographic primitives provided to the application software by the cryptokernel are the same in both cases. The difference lies in the way they are implemented.
So, when using a scheme with a split cryptonuclear, the interaction of software and hardware is performed according to the following principle:
- Cryptographic primitives that do not require the use of a private key (for example, calculating a hash function, verifying an electronic signature, etc.) are performed by the software part.
- Cryptographic primitives that use a private key (creating an electronic signature, decrypting data, etc.) are performed by the hardware.
Let's illustrate the operation of a split cryptonuclear using the example of creating an electronic signature:
- The software part calculates the hash function of the signed data and transmits this value to the hardware via the exchange channel between cryptokernels.
- The hardware part, using the private key and hash, generates the value of the electronic signature and transmits it to the software part via the exchange channel.
- The software part returns the received value to the application software.
Features of checking the correctness of an electronic signature
When the receiving party receives data signed with an electronic signature, it must perform several verification steps. A positive result of checking the electronic signature is achieved only if all the verification stages are successfully completed.
Stage 1. Control of data integrity and data authorship.
Content of the stage. The electronic signature of the data is checked using the appropriate cryptographic algorithm. Successful completion of this stage indicates that the data has not been modified since it was signed, as well as that the signature was made with a private key corresponding to the public key of electronic signature verification.
Stage execution location: cryptokernel.
Stage 2. Control of trust in the public key of the signer and control of the validity period of the private key of the electronic signature.
Content of the stage. The stage consists of two intermediate sub-stages. At the first stage, it is determined whether the public key for verifying the electronic signature was trusted at the time of signing the data. The second stage determines whether the private key of the electronic signature was valid at the time of signing the data. In general, the validity periods of these keys may not coincide (for example, for qualified certificates of electronic signature verification keys). Methods for establishing trust in the signer's public key are determined by the rules of electronic document management adopted by the interacting parties.
Stage execution location: application software / cryptokernel.
Stage 3. Control of the signatory's authority.
Content of the stage. In accordance with the established rules of electronic document management, it is checked whether the signatory had the right to certify the protected data. For an example, here is a situation of violation of authority. Suppose there is an organization where all employees have an electronic signature. The internal electronic document management system receives an order from the manager, but signed with the electronic signature of the warehouse manager. Accordingly, such a document cannot be considered legitimate.
Stage execution location: application software.
Assumptions made when describing the security object
- Information transfer channels, with the exception of key exchange channels, also pass through application software, APIs, and the cryptokernel.
- Information about trust in public keys and / or certificates, as well as information about the powers of public key holders, is placed in the public key store.
- The application software works with the public key store via a cryptokernel.
Example of an information system protected by the SCSI
To illustrate the previously presented schemes, we will consider a hypothetical information system and select all its structural elements.Description of the information system
Two organizations decided to introduce legally significant electronic document management (EDI) between them. To do this, they entered into an agreement in which they prescribed that documents will be transmitted by e-mail, and at the same time they must be encrypted and signed with a qualified electronic signature. Office programs from the Microsoft Office 2016 package should be used as tools for creating and processing documents, and cryptographic protection tools should be used for CryptoPro SCSI and CryptoARM encryption software.
Description of the organization's infrastructure 1
Organization 1 has decided that it will install CryptoPro's SCSI and CryptoARM software on the user's WORKSTATION-a physical computer. Encryption and electronic signature keys will be stored on the ruToken key carrier, which operates in the extracted key mode. The user will prepare electronic documents locally on their computer, then encrypt them, sign them, and send them using a locally installed email client.
Description of the organization's infrastructure 2
Organization 2 decided to move the encryption and electronic signature functions to a dedicated VM. In this case, all cryptographic operations will be performed automatically.
To do this, two network folders are organized on the dedicated VM:"\\...\In\", "\\...\Out\". To the network folder"\\...\In\ " files received from the counterparty will be automatically placed in plain text. These files will be decrypted and the electronic signature will be verified.
In the "\\...\Out\" folder, the user will place files that need to be encrypted, signed,and sent to the counterparty. The user will prepare the files themselves on their own ARM.
To perform the encryption and electronic signature functions, CryptoPro SCSI, CryptoARM software, and an email client are installed on the VM. All VM elements will be automatically managed using scripts developed by system administrators. Scripts are logged in log files (logs).
Cryptographic keys of the electronic signature will be placed on a token with an unrecoverable JaCarta GOST key, which the user will connect to their local computer.
The token will be forwarded to the VM using specialized USB-over-IP software installed on the user's ARM and on the VM.
The system clock on the user's ARM in organization 1 will be adjusted manually. The system clock of a specialized VM in organization 2 will be synchronized with the system clock of the hypervisor, which, in turn, will be synchronized over the Internet with public time servers.
Selection of SCSI structural elements
Based on the above description of the IT infrastructure, we will select the structural elements of the SCSI and write them down in a table.
Table-Correspondence of elements of the SCSI model to elements of information systems
| Item Name | Organization 1 | Organization 2 |
| Application Software | BY CryptoARM | BY CryptoARM |
| Software part of the cryptokernel | SKZI CryptoPro CSP | SKZI CryptoPro CSP |
| Cryptokernel Hardware | absent | JaCarta GOST |
| API | MS CryptoAPI | MS CryptoAPI |
| Public Key Storage | User's APM: - hard disk. - standard Windows certificate storage. | Hypervisor: — hard disk. Virtual machine: — hard disk. - standard Windows certificate storage. |
| Private Key Storage | ruToken key carrier that works in the extracted key mode | JaCarta GOST key carrier operating in non-recoverable key mode |
| Public key exchange channel | User's APM: - RAM. | Hypervisor: - RAM. Virtual machine: - RAM. |
| Private key exchange channel | User's APM: - USB bus — - RAM. | absent |
| Exchange channel between cryptokernels | missing (no hardware part of the cryptokernel) | User's workstation: - USB bus — - RAM; -USB-over-IP software module — - Network interface. Corporate network of the organization 2. Hypervisor: - RAM. — network interface. Virtual machine: — network interface — - RAM; -USB-over-IP software module. |
| Open data exchange channel | User's AWP: -I / O tools — - RAM; — hard disk. | User's AWP: -I / O tools — - RAM; — hard disk. — network interface. Corporate network of the organization 2. Hypervisor: — network interface — - RAM; — hard disk. Virtual machine: — network interface — - RAM; — hard disk. |
| Secure data exchange channel | The Internet. Corporate network of the organization 1. User's APM: - hard disk. - RAM. — network interface. | The Internet. Corporate network of the organization 2. Hypervisor: — network interface — - RAM; — hard disk. Virtual machine: — network interface — - RAM; — hard disk. |
| Time transmission channel | User's AWP: -I / O tools — - RAM; - system timer. | The Internet. Corporate network of the organization 2, Hypervisor: — network interface — - RAM; - system timer. Virtual machine: - RAM. - system timer. |
| Control command transmission channel | User's AWP: -I / O tools — - RAM. (Graphical User Interface FOR CryptoARM) | Virtual machine: - RAM. — hard disk. (Automation Scripts) |
| Channel for receiving work results | User's AWP: -I / O tools — - RAM. (Graphical User Interface FOR CryptoARM) | Virtual machine: - RAM. — hard disk. (Log files for automation scripts) |
Top-level security threats
Explanations
Assumptions used in threat decomposition:
- Strong cryptographic algorithms are used.
- Cryptographic algorithms are used in a secure way in the correct operating modes (for example, ECB is not used to encrypt large amounts of data, the permissible load on the key is taken into account, etc.).
- Attackers know all the algorithms, protocols, and public keys used.
- All encrypted data can be read by attackers.
- Attackers are able to reproduce any software elements in the system.
Decomposition
Y1. Compromise of private cryptographic keys.
Y2. Encryption of forged data on behalf of a legitimate sender.
Y3. Decryption of encrypted data by persons who are not legitimate recipients of the data (intruders).
Y4. Creating an electronic signature of a legitimate signatory under forged data.
Y5. Getting a positive result of checking the electronic signature of forged data.
Y6. Erroneous acceptance of electronic documents for execution due to problems in the organization of electronic document management.
U7. Unauthorized access to protected data during their processing by the SCSI.
Y1. Compromise of private cryptographic keys
Y1. 1. Getting a private key from the private key store.
Y1. 2. Obtaining a private key from objects of the cryptographic medium functioning environment, in which it can temporarily reside.
Explanation of Y1. 2.
Objects that can temporarily store a private key include:
- random access memory,
- temporary files,
- swap files,
- hibernation files,
- snapshot files of the" hot " state of virtual machines, including files of the contents of the RAM of paused virtual machines.
Y1. 2. 1. Extracting private keys from working RAM by freezing RAM modules, extracting them and then reading the data (freeze attack).
Explanation of Y1. 2. 1.
Example of an attack.
Y1. 3. Getting a private key from the private key exchange channel.
Explanation of Y1. 3.
An example of the implementation of this threat will be given below.
Y1. 4. Unauthorized modification of the cryptokernel, as a result of which private keys become known to intruders.
Y1. 5. Compromise of the private key as a result of using technical channels of information leakage.
Explanation of Y1. 5.
Example of an attack.
Y1. 6. Compromise of the private key as a result of the use of special technical means (STS) intended for secret removal of information ("bugs").
Y1. 7. Compromise of private keys in the process of storing them outside the SCSI.
Explanation of Y1. 7.
For example, a user stores their key media in a desktop mailbox, from which they can easily be extracted by intruders.
Y2. Encryption of forged data on behalf of a legitimate sender
Explanations
This threat is considered only for data encryption schemes with sender authentication. Examples of such schemes are given in the recommendations for standardization R 1323565.1.004-2017 " Information technology. Cryptographic protection of information. Shared key generation schemes with public key authentication". For other cryptographic schemes, this threat does not exist, since encryption is performed on the recipient's public keys, and they are generally known to attackers.
Decomposition
Y2. 1. Compromise of the sender's private key:
Y2. 1. 1. Link: "Typical threat model. Cryptographic information protection system.Y1. Compromise of private cryptographic keys".
Y2. 2. Substitution of input data in the open data exchange channel.
Notes Y2. 2.
Y3. Decryption of encrypted data by persons who are not legitimate recipients of the data (intruders)
Decomposition
Y3. 1. Compromise of private keys of the recipient of encrypted data.
Y3. 1. 1 Link: "Typical threat model. Cryptographic information protection system. Y1. Compromise of private cryptographic keys".
Y3. 2. Substitution of encrypted data in the secure data exchange channel.
Y4. Creating an electronic signature of a legitimate signatory under forged data
Decomposition
Y4. 1. Compromise of the private keys of the electronic signature of a legitimate signer.
Y4. 1. 1 Link: "Standard threat model. Cryptographic information protection system. Y1. Compromise of private cryptographic keys".
Y4. 2. Substitution of signed data in the open data exchange channel.
Note U4. 2.
Y5. Getting a positive result of checking the electronic signature of forged data
Decomposition
Y5. 1. Attackers intercept a message about a negative result of checking an electronic signature in the work results transmission channel and replace it with a message with a positive result.
Y5. 2. Attackers carry out an attack on the trust of signature certificates (SCENARIO — all elements are required):
Y5. 2. 1. Attackers generate a public and private key of an electronic signature. If the system uses electronic signature key certificates, they generate an electronic signature certificate that is as similar as possible to the certificate of the intended sender of the data whose message they want to forge.
U5. 2. 2. Attackers make unauthorized changes to the public key store, giving the generated public key the necessary level of trust and authority.
U5. 2. 3. Attackers sign fake data with a previously generated electronic signature key and embed it in the secure data exchange channel.
Y5. 3. Attackers carry out an attack using expired electronic signature keys of a legal signer (SCENARIO — all elements are required):
Y5.3.1. Attackers compromise expired (not currently valid)ones private keys of the legitimate sender's electronic signature.
Y5. 3. 2. Attackers substitute the time in the time transfer channel for the time when the compromised keys were still valid.
U5. 3. 3. Attackers sign fake data with a previously compromised electronic signature key and embed it in the secure data exchange channel.
Y5. 4. Attackers carry out an attack using compromised electronic signature keys of a legal signer (SCENARIO — all elements are required):
Y5. 4. 1. Attackers make a copy of the public key store.
U5. 4. 2. Attackers compromise the private keys of one of the legitimate senders. The latter notices a compromise, revokes the keys, and information about revoking the key is placed in the public key store.
Y5. 4. 3. Attackers replace the public key store with a previously copied one.
U5. 4. 4. Attackers sign fake data with a previously compromised electronic signature key and embed it in the secure data exchange channel.
U5. 5. < ... > due to the presence of errors in the implementation of the 2nd and 3rd stages of electronic signature verification:
Explanation of Y5. 5.
Y5. 5. 1. Verification of trust in the certificate of the electronic signature key only by the presence of trust in the certificate with which it is signed, without CRL or OCSP checks.
Explanation of Y5. 5. 1.
Y5. 5. 2. When building a chain of trust for a certificate, the authority of issuing certificates is not analyzed
Explanation of Y5. 5. 2.
Example of an attack against SSL / TLS certificates.
The attackers bought a legitimate certificate for their email address. They then made a fraudulent site certificate and signed it with their certificate. If the authorization check is not performed, then when checking the chain of trust, it will be correct, and, accordingly, the fraudulent certificate will also be correct.
Y5. 5. 3. When building a chain of trust for a certificate, intermediate certificates are not checked for revocation.
Y5. 5. 4. CRLs are updated less frequently than they are issued by the certification authority.
U5. 5. 5. The decision to trust the electronic signature is made before the OCSP response about the certificate status is received, sent for a request made later than the time of signature formation or earlier than the next CRL is received after the signature formation.
Explanation of U5. 5. 5.
In the regulations of most CA, the time of revocation of a certificate is considered to be the time when the nearest CRL containing information about the revocation of the certificate is issued.
Y5. 5. 6. When receiving signed data, the identity of the certificate to the sender is not checked.
Explanation of Y5. 5. 6.
Example of an attack. For SSL certificates: the address of the called server may not match the value of the CN field in the certificate.
Example of an attack. Attackers compromised the electronic signature keys of one of the payment system participants. After that, they hacked the network of another participant and sent payment documents signed with compromised keys to the settlement server of the payment system on their behalf. If the server analyzes only trust and does not check compliance, then fraudulent documents will be considered legitimate.
Y6. Erroneous acceptance of electronic documents for execution due to problems in the organization of electronic document management.
Decomposition
Y6. 1. The receiving party does not detect duplication of the received documents.
Explanation of U6. 1.
Example of an attack. Attackers can intercept a document sent to the recipient, even if it is cryptographically secure, and then repeatedly send it to the secure data transmission channel. If the recipient does not detect duplicates, then all received documents will be perceived and processed as different documents.
U7. Unauthorized access to protected data during their processing by the SCSI
Decomposition
Y7. 1.<...> due to information leakage through third-party channels (side channel attack).
Explanation of U7. 1.
Example of an attack.
Y7. 2.<...> due to the neutralization of protection against unauthorized access to information processed on the SCSI:
U7. 2. 1. Operation of the SCSI in violation of the requirements described in the SCSI documentation.
Y7. 2. 2. < ... > implemented in due to the presence of vulnerabilities in:
Y7. 2. 2. 1.<...> anti-unauthorized access tools.
U7. 2. 2. 2.<...> the SCSI itself.
U7. 2. 2. 3.<...> the operating environment of the cryptographic tool.
Examples of attacks
The scenarios discussed below obviously contain errors in the organization of information security and serve only to illustrate possible attacks.Scenario 1. Example of implementing threats Y2. 2 and Y4. 2.
Item Description
The KBR AWP software and SCAD Signature SCSI are installed on a physical computer that is not connected to the computer network. As a key carrier, the vdToken FCN is used in the mode of operation with an unrecoverable key.
The settlement procedure assumes that the settlement specialist downloads electronic messages in clear text from his work computer (the scheme of the old KBR WORKSTATION) from a special secure file server, then writes them to an alienable USB flash drive and transfers them to the KBR workstation, where he encrypts and signs them. After that, the specialist transfers protected electronic messages to the alienated medium, and then writes them to the file server via his work computer, from where they get to the UTA and then to the payment system of the Bank of Russia.
In this case, the channels for exchanging open and protected data will include: the file server, the specialist's work computer, and the media to be disposed of.
Attack
Unauthorized intruders install a remote control system on the specialist's work computer and, at the time of recording payment orders (electronic messages) in plain text on the alienated medium, replace the contents of one of them. The specialist transfers payment orders to the KBR APM, signs and encrypts them without noticing the substitution (for example, due to a large number of payment orders on a flight, fatigue, etc.). After that, the fake payment order passes through the technological chain and enters the payment system of the Bank of Russia.
Scenario 2. Example of implementing threats Y2. 2 and Y4. 2.
Item Description
The computer with installed AWP KBR, SCAD Signature and connected key carrier FCN vdToken functions in a dedicated room without access from the staff.
The calculation specialist connects to the KBR workstation in remote access mode via the RDP protocol.
Attack
Attackers intercept banking details used by the settlement specialist to connect and work with the KBR automated control system (for example, by using malicious code on their computer). Then they connect on their behalf and send a fake payment order to the Bank of Russia's payment system.
Scenario 3. Example of the implementation of the threat Y1. 3.
Item Description
Let's consider one of the hypothetical options for implementing the ABS-KBR integration modules for a new scheme (AWP KBR-N), in which the electronic signature of outgoing documents occurs on the ABS side. At the same time, we will assume that ABS operates on the basis of an operating system that is not supported by the SCAD Signature SCSI, and, accordingly, the cryptographic functionality is transferred to a separate virtual machine — the ABS-KBR integration module.
The key storage medium is a regular USB token that works in the extracted key mode. When connecting the key media to the hypervisor, it turned out that there were no free USB ports in the system, so we decided to connect the USB token via a network USB hub, and install a USB-over-IP client on the VM that will communicate with the hub.
Attack
Attackers intercepted the private key of an electronic signature from the communication channel between the USB hub and the hypervisor (data was transmitted in clear form). Having the private key, the attackers created a fake payment order, signed it with an electronic signature, and sent it to the KBR-N ARM for execution.
Scenario 4. Example of implementing U5.5 threats.
Item Description
Let's consider the same scheme as in the previous scenario. We assume that e-mail messages coming from the KBR-N AWP fall into the \ \ folder...\SHARE\In, and those that are sent to the KBR-N ARM and then to the Bank of Russia payment system are sent to \\...\SHARE\out.
We will also assume that when implementing the integration module, the lists of revoked certificates are updated only when cryptographic keys are reissued, and also that electronic messages received in the \\folder are updated...\SHARE\In is checked only for integrity control and control of trust in the public key of the electronic signature.
Attack
The attackers, using the keys stolen in the previous scenario, signed a fake payment order containing information about the receipt of money to the account of a fraudulent client and embedded it in the secure data exchange channel. Since there is no verification that the payment order was signed by the Bank of Russia, it is accepted for execution.
