You've probably heard that TOR is packed with police officers and FBI agents. At the same time, they say that only their own people are allowed on Serious carder forums, and security guards have nothing to catch on the darknet. There is some truth in both, but what is it? Is there any benefit from monitoring the darknet?
Under the cut, let's talk about one of the most subtle and closed areas of work in information security, around which there are many well-founded and not so many rumors. Bastion analysts agreed to tell us what's what. A bonus feature is a list of tools that will help you explore the network underground on your own.
Intelligence agencies and police pursue their own goals, while we monitor the darknet for the sake of customers. They are concerned about information leaks and impending attacks, so we are monitoring them:
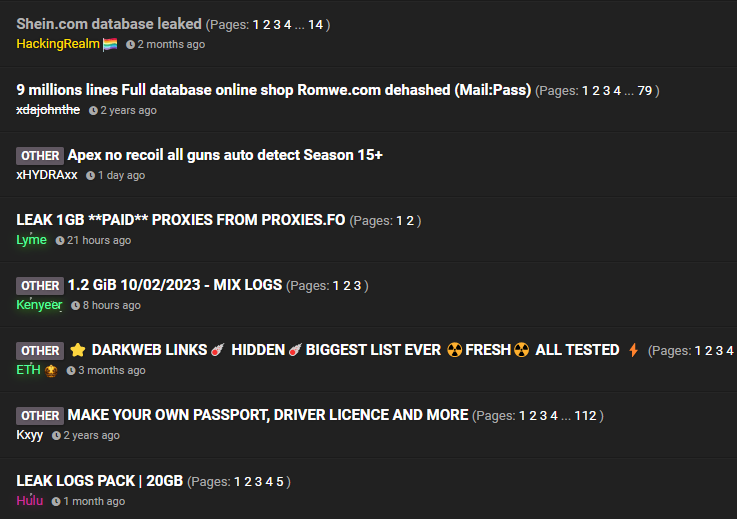
Hackers, carders, scammers and other illegal immigrants constantly wander from site to site, so the concept of "darknet" is blurred. These are not only overlay networks like TOR and I2P, but also a variety of deep web. A lot of interesting things happen in closed Telegram channels and chats. Groups discuss upcoming attacks in private IRC channels. It's hard to say what this is due to, but a significant part of the hacker community is migrating to Discord.
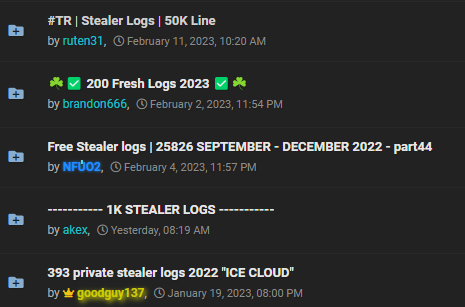
We also follow some forums on the regular web. As a rule, they are blocked in the civilized world, but they are hosted in God-forsaken places, and therefore they work calmly despite the illegal subject matter. And hacker groups are actively using Twitter for PR.
So we try to keep an eye on all the places where villains gather.
Features of these sources of information distinguish darknet monitoring from OSINT and activities such as monitoring brand mentions in social networks. OSINT's methods, techniques, and tactics are successfully applied on the darknet, but information is much more difficult to access there.
In addition, on the darknet, you often have to contact people, but let's talk about everything in order. The work on observing this space can be divided into two parts. The first is automated monitoring.
In addition, we make extensive use of open source crawlers and scripts:
As for the subject of the search, to track company mentions, we upload them to crawlers:
The main problem with such accounts is that they take a long time to create. To make them look "live", for example, you need to take a long pause between creating an email and registering on the forum.
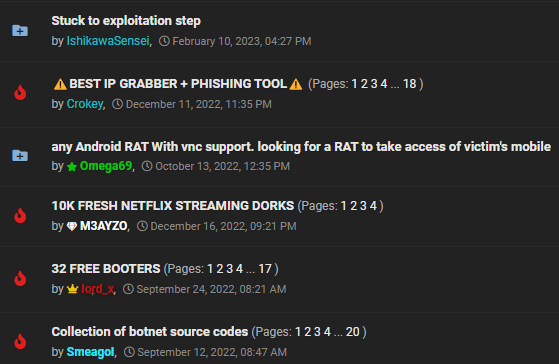
We are currently preparing virtuals to register on German darknet platforms. You will be able to use these accounts in at least 3 months. But it also requires an understanding of the subculture and a reputation in the community. Its leveling is a constant job.
How this is done is a sensitive issue. We can't disclose the methods, but let's say that reputation isn't necessarily earned through illegal means. Significant credit of trust can be obtained in the process of communication, with the help of psychology, competent questions and hints of awareness in certain things.
Your conditional length of service is also important. If an account exists for several years and its owner has participated in discussions, then from time to time they are invited somewhere. This often happens in Telegram. There is a new chat about illegal topics, and regulars of old sites are sent a link. This allows you to follow active attackers and continue collecting information for years.
However, from time to time something dangerous happens and requires a quick response. For example, the number of mentions of a company increases dramatically. Then we start an urgent search and find out what it is connected with.
Another situation: a message appears about the sale of the database or the director's certificate leaks. Then we notify the client's SOC and our team responsible for forensic analysis. They start searching for traces of the incident.
There are also non-standard tasks. So, once the company's security service became reliably aware that confidential information was stolen from them. We were asked to let you know when and where it will surface.
Recently, there has been more and more work, and it is becoming more diverse. You don't have to be bored. Activity on the darknet correlates with the social and political environment. As soon as any conflict escalates, all sorts of illegal activities increase around us.
It goes to organizations that are directly or indirectly associated with a particular state or social movement, market leaders, and companies that are active in the media. And sometimes, to get under the distribution, it is enough to be "in the wrong" jurisdiction, or accidentally be in the field of view of villains. So we are unlikely to be out of work any time soon. The experience of monitoring the darknet, and the information that can be extracted from this information space, remain in price.
Under the cut, let's talk about one of the most subtle and closed areas of work in information security, around which there are many well-founded and not so many rumors. Bastion analysts agreed to tell us what's what. A bonus feature is a list of tools that will help you explore the network underground on your own.
Recorded from the words of experts from the Bastion company, who wished to remain anonymous
Intelligence agencies and police pursue their own goals, while we monitor the darknet for the sake of customers. They are concerned about information leaks and impending attacks, so we are monitoring them:
- Any mention of client companies in connection with vulnerabilities or attacks.
- Mentions of all kinds of confidential information related to the work of the company and its employees.
- Data about new vulnerabilities in the software that is included in the company's stack.
- Information about the company's counterparties and partners in the context of malicious activity. For example, it can be monitoring attacks on supply chains.
The foggy Borders of the darknet

Hackers, carders, scammers and other illegal immigrants constantly wander from site to site, so the concept of "darknet" is blurred. These are not only overlay networks like TOR and I2P, but also a variety of deep web. A lot of interesting things happen in closed Telegram channels and chats. Groups discuss upcoming attacks in private IRC channels. It's hard to say what this is due to, but a significant part of the hacker community is migrating to Discord.

We also follow some forums on the regular web. As a rule, they are blocked in the civilized world, but they are hosted in God-forsaken places, and therefore they work calmly despite the illegal subject matter. And hacker groups are actively using Twitter for PR.
If a 10-thousandth person from a party writes something like: "Adobe-tonight you are*****", this is a bell that should be responded to. At the very least, this is a reason to check what is happening on closed sites
So we try to keep an eye on all the places where villains gather.
Features of these sources of information distinguish darknet monitoring from OSINT and activities such as monitoring brand mentions in social networks. OSINT's methods, techniques, and tactics are successfully applied on the darknet, but information is much more difficult to access there.
On the Internet, just turn on the VPN of a neutral country, which blocks almost nothing, and turn on the crawler. And here you have to cringe. One site is unavailable from this country, but this one works. From the other — on the contrary. Here TOR is needed, here I2P. Here they let you in by invitation, there they let you in by acquaintance. And there are plenty of scammers
In addition, on the darknet, you often have to contact people, but let's talk about everything in order. The work on observing this space can be divided into two parts. The first is automated monitoring.
Bot management
We use tools that work over the regular Internet, TOR, I2P, Telegram, and IRC channels. Some of them are imported commercial solutions. In the current reality, licenses for them have to be purchased in a complex, roundabout way, so we will not announce the names.In addition, we make extensive use of open source crawlers and scripts:
- ACHE Crawler, or rather, its modules that work on the darknet;
- megadose/OnionSearch — for collecting onion search results;
- josh0xA / darkdump — for darknet search from the command line;
- s-rah/onionscan — for finding correlations between onion sites;
- fastfire/deepdarkCTI — for collecting information about threats.
As for the subject of the search, to track company mentions, we upload them to crawlers:
- commercial name;
- name of the legal entity;
- INN NUMBER;
- OGRN;
- corporate domains;
- email addresses;
- protruding IP addresses;
- trademarks and product names;
- personal data of key individuals, such as directors;
- and other identifiers.
Crawlers work in real time, 24x7, but they don't understand the context, so we manually select relevant triggers. Of course, you can do this using rules, but the more complex automatic filtering is, the higher the chance of missing something important, losing key puzzle elements. But Open Source and boxed systems already provide only superficial monitoring. In order for them to work effectively, you need to constantly add new data sources, and this is where the real difficulties begin.It is enough for someone well-known in narrow circles to mention a new 0-day associated with a certain moment in such and such a product, and we notify customers who have it on the external page. We recommend that you increase your vigilance and set product logging to the maximum level
Bad reputation
To get into the cool hacker communities, you need to look like "your own", and not an analyst from Bastion. To do this, we create virtual, fake accounts with elaborate legends behind them. If someone is interested in the owner of such an account, they will find a person in the United States, the Netherlands, or Kazakhstan who has nothing to do with our company. When you understand the mechanics of deanon, it's easy to leave a false trail of bread crumbs. The main thing is to do without obvious clues, they, on the contrary, look suspicious.You go to the forum with free registration and see that only a couple of branches per week are created there. Consider it nothing happening. At the same time, hundreds of messages are left on sites where people with a reputation are allowed — as lively as if they had entered comments in VK
The main problem with such accounts is that they take a long time to create. To make them look "live", for example, you need to take a long pause between creating an email and registering on the forum.

We are currently preparing virtuals to register on German darknet platforms. You will be able to use these accounts in at least 3 months. But it also requires an understanding of the subculture and a reputation in the community. Its leveling is a constant job.
How this is done is a sensitive issue. We can't disclose the methods, but let's say that reputation isn't necessarily earned through illegal means. Significant credit of trust can be obtained in the process of communication, with the help of psychology, competent questions and hints of awareness in certain things.
A lot of things are clear just by your requests. If you ask, something like: "Guys! I wrote a virus on Delphi, I have it burning with Kaspersky and Norton. Throw, pliz, some cryptor", — you will never be taken seriously
Your conditional length of service is also important. If an account exists for several years and its owner has participated in discussions, then from time to time they are invited somewhere. This often happens in Telegram. There is a new chat about illegal topics, and regulars of old sites are sent a link. This allows you to follow active attackers and continue collecting information for years.
Fruit of the poisoned Tree
Most of this espionage work translates into banal periodic reporting. Once a month, we write and send the customer a report with an analysis of company-related activity.Recently, one of the forums discussed lists of license plates and car models of employees of a well-known company. This is discussed in advance, but as a rule, we transmit such things in periodic reports
However, from time to time something dangerous happens and requires a quick response. For example, the number of mentions of a company increases dramatically. Then we start an urgent search and find out what it is connected with.
Another situation: a message appears about the sale of the database or the director's certificate leaks. Then we notify the client's SOC and our team responsible for forensic analysis. They start searching for traces of the incident.
This is quite harmful work, but not because there is a lot of shock content on the darknet. It rarely appears in the forum sections that we monitor. The work is just nervous, like any other related to information security monitoring. Conditionally, at 2 am you are going to sleep, suddenly an alert comes and you pick it up urgently until six in the morning
There are also non-standard tasks. So, once the company's security service became reliably aware that confidential information was stolen from them. We were asked to let you know when and where it will surface.
Recently, there has been more and more work, and it is becoming more diverse. You don't have to be bored. Activity on the darknet correlates with the social and political environment. As soon as any conflict escalates, all sorts of illegal activities increase around us.
It goes to organizations that are directly or indirectly associated with a particular state or social movement, market leaders, and companies that are active in the media. And sometimes, to get under the distribution, it is enough to be "in the wrong" jurisdiction, or accidentally be in the field of view of villains. So we are unlikely to be out of work any time soon. The experience of monitoring the darknet, and the information that can be extracted from this information space, remain in price.
