The original of this material
© Kommersant, 19.03.2021, The Dark Side of the Darknet, Illustrations: Kommersant
Yulia Stepanova, Yulia Tishina
The shadow market for trading in personal data and access to IT infrastructure is a phenomenon that cannot be ignored, if only because of its impact on the economy, which loses 3.5 trillion rubles a year from hacker attacks. In late February-early March 2021, instead of the usual messages about successful cyber attacks on companies or banks, information about hacked hacker forums appeared. This would seem to be good news for data operators, who spend an average of $1.5 million annually on cybersecurity. But what is happening in the hacker community most of all resembles the redistribution of the market with all the ensuing consequences: cyber attacks will soon become more dangerous, and protection against them will be more expensive.
Losses of the Russian economy from the actions of cybercriminals in 2020, according to Sberbank, could amount to 3.5–3.6 trillion rubles. This amount is equal to 73% of the funds that, according to the authorities, within two years will be required to restore the entire economy of the country after the pandemic. Only the volume of the market for sales of stolen bank card data in 2020, according to Group-IB, approached 145 billion rubles, which is comparable to the spending of Russians on preferential mortgages this year. At the same time, most of the cyber attacks, according to Microsoft, come from Russia. In September 2020, the corporation reported that over the past two years it recorded more than 13 thousand notifications about hacker attacks, and the highest percentage of messages was caused by Russian actions.
But in early 2021, "Russian hackers" suddenly came under attack themselves. So, on January 20, the administrator of the Verified hacker forum reported hacking, on February 16-the CrdClub carding forum (fraudsters used it for transactions with fake credit card providers), on March 2, Exploit announced attacks, and on March 3 — the oldest Russian-language forum Maza. Hacker forums are actually exchanges for the sale of cybercrime goods and services, says Mikhail Kondrashin, Technical Director of Trend Micro in Russia and the CIS. Successful attacks on such "exchanges" can mean that the special services have become more active, and that cybercriminals themselves have started a war without rules for the redistribution of the shadow market. In any case, for decent data operators, the news about the hacked hackers seems good. But not everything is so simple. To begin with, the question arises why do specialists in data theft from the Internet put their own data into it at all.
In addition, according to experts, on the forums you can meet intermediaries who work out someone's order or earn money by reselling data and malware, those who have built their own botnet (a computer network of devices infected with malware) and offer it as a service.
Forum administrators are protected from outsiders by a complex registration mechanism and its high price. To register, you need to confirm your account and provide a "portfolio" or a guarantee from the current user, says Anton Ponomarev, ESET's Director of Corporate Sales in Russia. The Maza platform has a particularly complex registration mechanism, and its price is $1 thousand (the number of users is given by the fact that as a result of the March attack, the data of more than 2 thousand hackers was freely available). By the way, administrators of such sites — in fact, hackers who earn money from hackers— receive money both from registration and from participating in the fraudulent schemes discussed. According to the estimates of a Kommersant source in hacker circles, at least $0.5 million passes through the Maza forum every month, and the combined turnover of Maza, Verified and Exploit for a month exceeds more than $1 million.
On hacker forums, there are often reports about hacking other forums, but the distinctive feature of recent attacks was that they targeted the largest and most widely known resources in the underground, says Vadim Solovyov. "Three forums in one month is strange. I don't think they were ordinary hackers. Someone purposefully destroys the forums, " one of the founders of Exploit is sure.
The Maza, Verified and Exploit forums are allegedly linked by some Kommersant interlocutors to Dmitry Dokuchaev, an ex-operative of the FSB Information Security Center. The rumor that the forums could have been hacked on the order of the special services appeared against the background of the fact that Dmitry Dokuchaev asked the court for parole. His lawyer sent a corresponding appeal to the Lefortovo court on March 2. Part of the hacker community put forward a version that data obtained from Dmitry Dokuchaev in exchange for a reduction in the sentence was used to attack the forums.
However, this bright version, upon closer examination, reveals many weaknesses. First, the court did not reduce Dmitry Dokuchaev's prison term. Secondly, even Dmitry Dokuchaev's long-time antagonist, Pavel Vrublevsky, the founder of the ChronoPay payment system, did not directly point out him, but only told Kommersant that he did not know who hacked the forums, adding that "hacking will largely be the end of these communities and will remove the constant risk for Dmitry due to communication." with them." The Maza administrator told Kommersant that Dmitry Dokuchaev had nothing to do with the administration of the forum or its hacking.
But most importantly, after the attacks on the forums, there were no statements from law enforcement officers about their closure. Moreover, according to the source of Kommersant, a copy of Verified appeared at a different address, and the Exploit portal has now restored work. An announcement appeared on Verified that all users had their passwords reset, says Victoria Kivilevich, an analyst at the Kela cybersecurity company. According to her, CrdClub is now working, and Expoit only suspended the work of "mirror" in the legal segment of the Internet. This is not typical for the security services. So, in 2019, when Belarusian security forces went to the XakFor hacker forum for Russian-speaking cyber intruders, the site stopped working, and the Ministry of Internal Affairs and the Investigative Committee of the Republic reported on its closure.
Experts point out one more important point. "Attacks on such resources are not profitable for law enforcement agencies, since they themselves constantly draw data from there for work," says Igor Zalevsky.
As a result, a version comes to the fore that the major players of the shadow data trading market themselves have begun to redo it.
Local clashes between competing groups can have a devastating impact on the hacker community, whose main fear is deanonymization. It is possible if the owners of the hacked resources kept a log of IP addresses, says Vadim Solovyov. In this case, in his opinion, it will be much easier for law enforcement agencies to calculate the real location of criminals.
Exposing forum participants will certainly complicate the work of shadow sites, experts say. Their users will "flow" to other resources ," which is quite consistent with the tasks of the attackers, " Mr. Oganesyan believes, because we are talking about fighting competitors. But administrators of all remaining sites will complicate the procedure for accepting new members, increase the protection of digital infrastructure, and refuse to store user data, Anton Ponomarev believes.
Members of hacker groups will behave more cautiously, Ilya Tikhonov, an expert at the Softline Information Security Department, is sure. Against the background of such attacks, some hackers are already ceasing to engage in their activities, confirms Igor Zalevsky, head of the JSOC CERT Cyber Incident Investigation Department at Rostelecom. Those who "stay in the game" increase prices for their services, taking into account the risks of revealing their identity after hacking the next forum, he says.
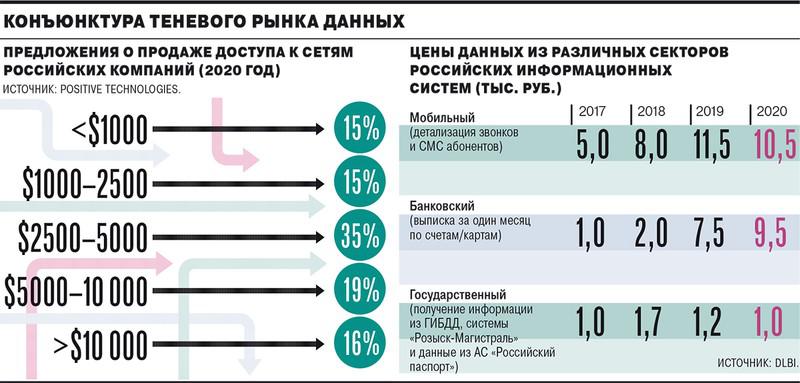
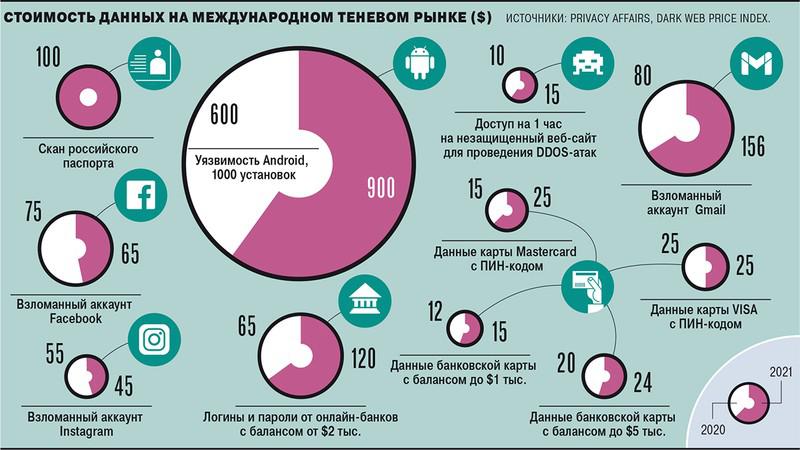
Now, according to Privacy Affairs, prices for various goods and services on the shadow market range from $15 for bank card data to $1 thousand for selling vulnerabilities in the Android system. Hacking various sites on the Internet, according to Positive Technologies, can cost from $40 for hacking mail to $4,500 for a targeted attack on a company.
Respectable companies and banks, in turn, will have to monitor security even more closely and increase their budgets for this area. In 2020, according to Cisco, the average cost of data protection in Russian organizations was $1.4 million. But already in 2021, 52% of Russian companies, according to PwC's forecast, plan to increase spending on cybersecurity, and 42% of organizations want to expand the number of employees employed in this area.
Click to enlarge
Click to enlarge
The original of this material
© Xakep.ru, 04.03.2021, Maza hacker forum affected by hacking
Maria Nefedova
Flashpoint specialists https://www.flashpoint-intel.com/bl...-maza-breached-by-unknown-attacker/обнаружили data leak from the closed Russian-language hack forum Maza (aka Mazafaka). The Forum is one of the oldest of its kind and has been operating since 2003. According to experts, its main contingent is "the most sophisticated cybercriminals and financial fraudsters, many of whom began their activities in the mid-to late 1990s."
So far, almost nothing is known about the attackers who compromised Maza. Yesterday, after a successful hack, they posted a warning on the forum saying: "This forum has been hacked. Your data was leaked." Obviously, Russian is not the native language of the attackers, and the message was passed through an online translator. It is reported that the data of approximately 3,000 users has been leaked.
Apparently, the forum "leaked" user IDs, usernames, email addresses, links to instant messengers, including Skype, MSN and Aim, as well as passwords, both hashed and obfuscated. At the same time, in the topic of hacking discussion, some users claim that only the old database was stolen, while others write that they intend to leave for another forum.
Flashpoint experts note that the news of the Maza hack came shortly after the successful compromise of another Russian-language hack forum, Verified, which was hacked on January 20, 2021. After that, on February 18, 2021, the new Verified administrators announced the change of ownership of the resource and began the process of deanonymizing the previous Verified operators, known under the nicknames INC, VR_Support and TechAdmin. The new administrators said that the previous owners of the site registered the IP addresses of all Verified users and collected a total of 3,801,697 addresses.
It is not yet known whether Maza hackers will take similar actions to take over the forum. The fact is that the INC administrator mentioned above is (or used to be) a Maza moderator.
Kommersant, 05.03.2021, "Maza hack": The anti-hacking group TeaMp0isoN may be behind the hack, says Igor Bederov, founder of the Internet Search company. According to Mr. Bederov, the leaked database contains data from more than 2 thousand specialized cybercriminals. Despite the rapid growth in the number of attacks, the hacker "elite" organized only 3% of them, the expert points out. The database will allow identifying some of the initiators of cybercrimes, Mr. Bederov believes.
Most likely, the reason for the attack was personal or financial interest, suggests Mr. Bederov. "It is possible that some of the participants were insulted or underpaid the money promised from the fraudulent scheme," he says. - <url> sidebar
Maza has been hacked before. The previous hack occurred in February 2011, and then the data of more than 2,000 users was compromised, as well as all their correspondence on the forum.
The original of this material
© Xakep.ru, 26.02.2011, Hacked the largest cybercrime forums in the Russian Federation, Illustrations: via Xakep.ru
The most famous closed forum for cybercriminals to date "MAZA.la "(or as it is also called, "MAZAFAKA"), whose administrators are Afx (presumably Alexey), Render, 4x4 and Fiesta, was subjected to a massive hacker attack on February 18, resulting in a forum database consisting of more than two thousand It was stolen and made available to the public.
The second wave was attacked no less private forum "Direct Connection", the administrator of which is a certain" k0pa", a native of the group" CyberLords Team " — the same team that the scandalous hacker from Novosibirsk Evgeny Anikin was a member of. Analysts suggest that Russian carders have started their own "Internet war" for the redistribution of influence in the world of cybercrime, the prerequisites of which are known only to them.
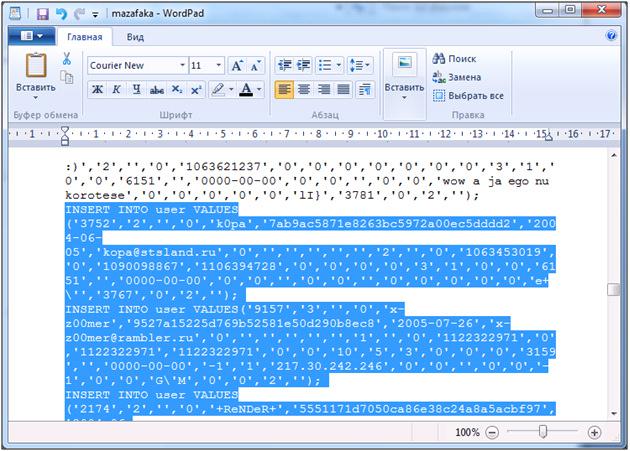
A screenshot with a dump of Maza users has been publishedThe range of people allowed to participate was constantly narrowed and checked by a special responsible person — "MF_SUPPORT", a native of Ukraine, whose work was funded by Administrators. In many ways, it was the quality of MF_SUPPORT's work that determined what the forum's contingent would be like. In addition, they also checked all transactions of forum participants.
"Cybercriminals use the most sophisticated schemes, and their places of communication are highly anonymous, so only a similar-minded contingent that shares the legal side of the issue with law enforcement agencies can resist them," said Joseph Blank, a representative of the RSA Anti-fraud Command Center.
Structurally, the activity of intruders was divided into several categories:
After publishing one of the screenshots from the forum on the Krebsonsecurity project, the attackers carefully took care of their anonymity, constantly changing their contactsAmong the forum participants "MAZA.la "there were such sensational "nicknames" as BadB (Vladislav Khorokhorin, 27 years old, arrested in France), Severa (a well-known spammer Pyotr Lavashov, who continues his criminal activities), zo0mer (Sergey Kozerev, against whom the US NSA conducted a separate investigation to identify sales lines for dumps. My0 (credit card merchant Roman Kkhoda, 26 years old), many of whom suffered a very harsh fate. All of them, in one way or another, fell under the eyes of Interpol and international security agencies, which have been looking for fraudsters for years.
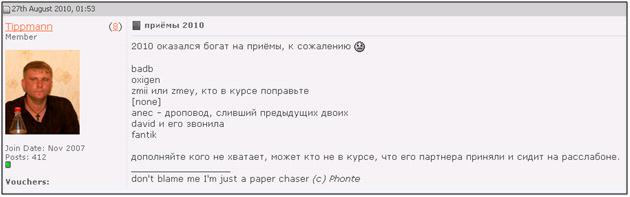
Forum participants actively tracked all the sorrows and misfortunes of their colleagues, covering the arrests of their" colleagues " in cybercrime (BadB-Vladislav Khorokhorin, arrested on August 7 in Nice for selling dumps of credit cards of users of many European countries)The participants themselves admitted that the forum became available not only to their "sphere", but also to people in uniform. For the first time, one of the official screenshots of the closed forum was made available to the foreign online publication Krebsonsecurity on October 24, 2010, which published a screenshot of the forum topic, which discussed the appearance of the new banking Trojan SpyEye at that time.
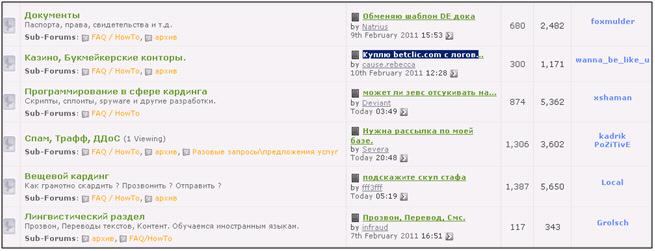
Peter Severa, a Russian who is one of the TOP 20 most famous spammers in the world, successfully participates in the discussion of forum topics and offers his services to cybercriminals in the Spam section
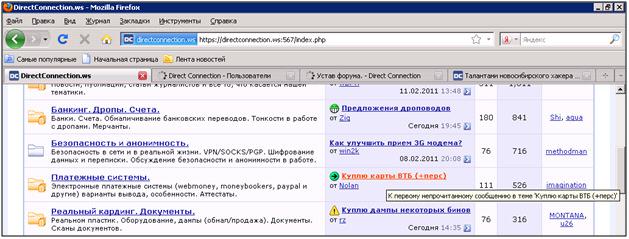
Participants of such closed platforms do not mind "working" in the Russian banking sector, issuing VTB bank cards to front persons for subsequent withdrawal of funds.For example, Peter SEVERA, a world-famous Russian spammer, advertises his services on two sites, only on DC — he does it in the person of a moderator.
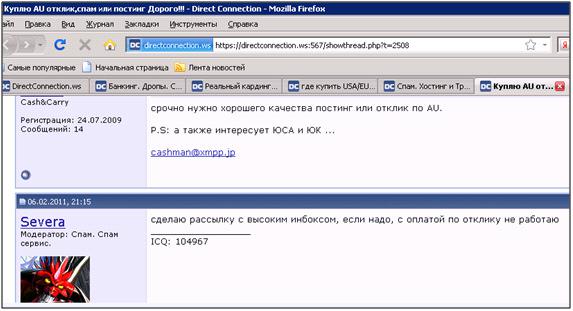
The most reputable cyber scammers can be seen on both sites, but in different rolesUnknown hackers broke into both forums, stealing the entire user base and their correspondence. Currently, the database has fallen into the hands of the most famous companies for the prevention of cybercrime and fraud — RSA, Anti Money Laundering Alliance and IISFA.
The original of this material
© Kommersant, 19.03.2021, "You can earn much more from attacks abroad"
Yulia Stepanova
Pavel Sitnikov, a former Russian hacker, told Kommersant about the work of Russian-language cybercrime forums and the consequences of hacking them.
— When and how did Russian-language hacker forums appear?
- Forums appeared in the 1990s to exchange information and communicate between hackers. They started making money on these sites in the 2000s. Exploit was originally a free open forum with a technical focus: its participants shared information about hacking methods and vulnerabilities. Later, the forum became more private, and registration on it began to cost $100. Maza and Verified are closed sites. They mostly host fraudulent schemes. Registration on Maza costs $1 thousand, for it you need to have three guarantors from among the forum participants.
— The leaked Maza database has more than 2 thousand users. Is this the actual number of forum participants?
— I think that in reality there were less than 2 thousand people communicating on the forum. Basically, there were those who had registered since its foundation. In recent years, new posts have rarely appeared on Maza. But the participants continued to conduct business and exchange contacts in private messages. They are the main value when hacking a forum. You can't earn money from this information, but it's interesting for the authorities.
— How will forum hacking affect the hacker business?
— The main consequence will be the replenishment of the" Most wanted FBI "honor roll. The impact of hacking on the hacker business and community is very painful. Forum participants have been doing business on these sites for decades, and after hacking, the public finds out about it. Hackers are afraid of being exposed.
— Can prices for cybercrime services rise?
— I think the prices of "breakout" will rise. But this is more likely due to the tightening of the policy of Roskomnadzor and the Ministry of Internal Affairs against leaks of personal data: the requirement to close bots-penetrators in Telegram, increasing fines for violations in the processing of such data.
— How much can hacking a hacker forum cost?
- From $1 million for a medium-sized forum to infinity.
— Do such hacks occur frequently?
- Attacks on hacker forums have always been successful — but they almost always try to hide them in all possible ways. There have been frequent attacks on Exploit before. This usually happens due to internal disputes, for example, one of the participants was blocked or deleted and they take revenge on the admins.
— Can attacks on forums be a response to the attacks of Russian-speaking hackers OldGremlin on Russian companies last year?
— It is not customary for Russian-speaking hackers to work on a domain zone .ru. This is due to the fact that, firstly, it is not good to shit where you live, and secondly, you can earn much more from attacks abroad. I don't think the forum hacks were a response to last year's attacks on Russian companies, because I doubt that they were attacks specifically from OldGremlin.
— What can be the reason for attacks on forums?
- The current attacks of hacker sites are a show execution. There is only one group working, and it is not yet clear who it is, but there are suspicions. The reason is the redistribution of spheres of influence. Those who were or are directly related to the sites or serve them are behind this. It is unlikely, almost unbelievable, that these are foreign hacker groups or special services.
© Kommersant, 19.03.2021, The Dark Side of the Darknet, Illustrations: Kommersant
Yulia Stepanova, Yulia Tishina
The shadow market for trading in personal data and access to IT infrastructure is a phenomenon that cannot be ignored, if only because of its impact on the economy, which loses 3.5 trillion rubles a year from hacker attacks. In late February-early March 2021, instead of the usual messages about successful cyber attacks on companies or banks, information about hacked hacker forums appeared. This would seem to be good news for data operators, who spend an average of $1.5 million annually on cybersecurity. But what is happening in the hacker community most of all resembles the redistribution of the market with all the ensuing consequences: cyber attacks will soon become more dangerous, and protection against them will be more expensive.
Losses of the Russian economy from the actions of cybercriminals in 2020, according to Sberbank, could amount to 3.5–3.6 trillion rubles. This amount is equal to 73% of the funds that, according to the authorities, within two years will be required to restore the entire economy of the country after the pandemic. Only the volume of the market for sales of stolen bank card data in 2020, according to Group-IB, approached 145 billion rubles, which is comparable to the spending of Russians on preferential mortgages this year. At the same time, most of the cyber attacks, according to Microsoft, come from Russia. In September 2020, the corporation reported that over the past two years it recorded more than 13 thousand notifications about hacker attacks, and the highest percentage of messages was caused by Russian actions.
But in early 2021, "Russian hackers" suddenly came under attack themselves. So, on January 20, the administrator of the Verified hacker forum reported hacking, on February 16-the CrdClub carding forum (fraudsters used it for transactions with fake credit card providers), on March 2, Exploit announced attacks, and on March 3 — the oldest Russian-language forum Maza. Hacker forums are actually exchanges for the sale of cybercrime goods and services, says Mikhail Kondrashin, Technical Director of Trend Micro in Russia and the CIS. Successful attacks on such "exchanges" can mean that the special services have become more active, and that cybercriminals themselves have started a war without rules for the redistribution of the shadow market. In any case, for decent data operators, the news about the hacked hackers seems good. But not everything is so simple. To begin with, the question arises why do specialists in data theft from the Internet put their own data into it at all.
Entry by guarantee
Hackers aren't the only ones who need hacker forums. On such forums, people buy or sell services or discuss practical aspects of their use, says Dmitry Galov, a cybersecurity expert at Kaspersky Lab. Therefore, among the active forum visitors there may be programmers who write the code of Trojans, but do not conduct attacks themselves, but sell their services to intruders, says Vadim Solovyov, a senior analyst at Positive Technologies. Another part of the audience of shadow sites is " private traders "who do not know how to" code", but want to make money by selling the collected data or by attacks. "For example, those who withdraw money from ATMs after an attack can also be registered on the forums," adds Mr. Solovyov.In addition, according to experts, on the forums you can meet intermediaries who work out someone's order or earn money by reselling data and malware, those who have built their own botnet (a computer network of devices infected with malware) and offer it as a service.
Forum administrators are protected from outsiders by a complex registration mechanism and its high price. To register, you need to confirm your account and provide a "portfolio" or a guarantee from the current user, says Anton Ponomarev, ESET's Director of Corporate Sales in Russia. The Maza platform has a particularly complex registration mechanism, and its price is $1 thousand (the number of users is given by the fact that as a result of the March attack, the data of more than 2 thousand hackers was freely available). By the way, administrators of such sites — in fact, hackers who earn money from hackers— receive money both from registration and from participating in the fraudulent schemes discussed. According to the estimates of a Kommersant source in hacker circles, at least $0.5 million passes through the Maza forum every month, and the combined turnover of Maza, Verified and Exploit for a month exceeds more than $1 million.
On hacker forums, there are often reports about hacking other forums, but the distinctive feature of recent attacks was that they targeted the largest and most widely known resources in the underground, says Vadim Solovyov. "Three forums in one month is strange. I don't think they were ordinary hackers. Someone purposefully destroys the forums, " one of the founders of Exploit is sure.
Punishing sword in uniform
The nature of hacking forums suggests that the attacker had detailed information about the work of the sites, experts interviewed by Kommersant are sure. The Exploit forum monitoring system, in particular, detected unauthorized access and attempts to intercept and analyze network traffic. Such an attack could have been carried out "only by special services or people who know where the servers are located," said one of the founders of Exploit (according to KrebsOnSecurity).The Maza, Verified and Exploit forums are allegedly linked by some Kommersant interlocutors to Dmitry Dokuchaev, an ex-operative of the FSB Information Security Center. The rumor that the forums could have been hacked on the order of the special services appeared against the background of the fact that Dmitry Dokuchaev asked the court for parole. His lawyer sent a corresponding appeal to the Lefortovo court on March 2. Part of the hacker community put forward a version that data obtained from Dmitry Dokuchaev in exchange for a reduction in the sentence was used to attack the forums.
However, this bright version, upon closer examination, reveals many weaknesses. First, the court did not reduce Dmitry Dokuchaev's prison term. Secondly, even Dmitry Dokuchaev's long-time antagonist, Pavel Vrublevsky, the founder of the ChronoPay payment system, did not directly point out him, but only told Kommersant that he did not know who hacked the forums, adding that "hacking will largely be the end of these communities and will remove the constant risk for Dmitry due to communication." with them." The Maza administrator told Kommersant that Dmitry Dokuchaev had nothing to do with the administration of the forum or its hacking.
But most importantly, after the attacks on the forums, there were no statements from law enforcement officers about their closure. Moreover, according to the source of Kommersant, a copy of Verified appeared at a different address, and the Exploit portal has now restored work. An announcement appeared on Verified that all users had their passwords reset, says Victoria Kivilevich, an analyst at the Kela cybersecurity company. According to her, CrdClub is now working, and Expoit only suspended the work of "mirror" in the legal segment of the Internet. This is not typical for the security services. So, in 2019, when Belarusian security forces went to the XakFor hacker forum for Russian-speaking cyber intruders, the site stopped working, and the Ministry of Internal Affairs and the Investigative Committee of the Republic reported on its closure.
Experts point out one more important point. "Attacks on such resources are not profitable for law enforcement agencies, since they themselves constantly draw data from there for work," says Igor Zalevsky.
As a result, a version comes to the fore that the major players of the shadow data trading market themselves have begun to redo it.
Cyberdistribution
The growth of attacks on hackers is most likely due to attempts to redo the black market of IT services and data trading, says Ashot Oganesyan, founder of the DLBI data leak intelligence service. In his opinion, owners of other forums, trying to destroy the reputation of competitors, or offended members of the community are behind the attacks. Pavel Sitnikov is also inclined to this version (see the interview).Local clashes between competing groups can have a devastating impact on the hacker community, whose main fear is deanonymization. It is possible if the owners of the hacked resources kept a log of IP addresses, says Vadim Solovyov. In this case, in his opinion, it will be much easier for law enforcement agencies to calculate the real location of criminals.
Exposing forum participants will certainly complicate the work of shadow sites, experts say. Their users will "flow" to other resources ," which is quite consistent with the tasks of the attackers, " Mr. Oganesyan believes, because we are talking about fighting competitors. But administrators of all remaining sites will complicate the procedure for accepting new members, increase the protection of digital infrastructure, and refuse to store user data, Anton Ponomarev believes.
Members of hacker groups will behave more cautiously, Ilya Tikhonov, an expert at the Softline Information Security Department, is sure. Against the background of such attacks, some hackers are already ceasing to engage in their activities, confirms Igor Zalevsky, head of the JSOC CERT Cyber Incident Investigation Department at Rostelecom. Those who "stay in the game" increase prices for their services, taking into account the risks of revealing their identity after hacking the next forum, he says.
Now, according to Privacy Affairs, prices for various goods and services on the shadow market range from $15 for bank card data to $1 thousand for selling vulnerabilities in the Android system. Hacking various sites on the Internet, according to Positive Technologies, can cost from $40 for hacking mail to $4,500 for a targeted attack on a company.
Respectable companies and banks, in turn, will have to monitor security even more closely and increase their budgets for this area. In 2020, according to Cisco, the average cost of data protection in Russian organizations was $1.4 million. But already in 2021, 52% of Russian companies, according to PwC's forecast, plan to increase spending on cybersecurity, and 42% of organizations want to expand the number of employees employed in this area.
***

Click to enlarge

Click to enlarge
***
Maza hack
Logins, passwords, contacts in Skype, MSN, Aim of almost 3000 users of the underground forum were stolen
The original of this material
© Xakep.ru, 04.03.2021, Maza hacker forum affected by hacking
Maria Nefedova
Flashpoint specialists https://www.flashpoint-intel.com/bl...-maza-breached-by-unknown-attacker/обнаружили data leak from the closed Russian-language hack forum Maza (aka Mazafaka). The Forum is one of the oldest of its kind and has been operating since 2003. According to experts, its main contingent is "the most sophisticated cybercriminals and financial fraudsters, many of whom began their activities in the mid-to late 1990s."
So far, almost nothing is known about the attackers who compromised Maza. Yesterday, after a successful hack, they posted a warning on the forum saying: "This forum has been hacked. Your data was leaked." Obviously, Russian is not the native language of the attackers, and the message was passed through an online translator. It is reported that the data of approximately 3,000 users has been leaked.
Apparently, the forum "leaked" user IDs, usernames, email addresses, links to instant messengers, including Skype, MSN and Aim, as well as passwords, both hashed and obfuscated. At the same time, in the topic of hacking discussion, some users claim that only the old database was stolen, while others write that they intend to leave for another forum.
Flashpoint experts note that the news of the Maza hack came shortly after the successful compromise of another Russian-language hack forum, Verified, which was hacked on January 20, 2021. After that, on February 18, 2021, the new Verified administrators announced the change of ownership of the resource and began the process of deanonymizing the previous Verified operators, known under the nicknames INC, VR_Support and TechAdmin. The new administrators said that the previous owners of the site registered the IP addresses of all Verified users and collected a total of 3,801,697 addresses.
It is not yet known whether Maza hackers will take similar actions to take over the forum. The fact is that the INC administrator mentioned above is (or used to be) a Maza moderator.
Kommersant, 05.03.2021, "Maza hack": The anti-hacking group TeaMp0isoN may be behind the hack, says Igor Bederov, founder of the Internet Search company. According to Mr. Bederov, the leaked database contains data from more than 2 thousand specialized cybercriminals. Despite the rapid growth in the number of attacks, the hacker "elite" organized only 3% of them, the expert points out. The database will allow identifying some of the initiators of cybercrimes, Mr. Bederov believes.
Most likely, the reason for the attack was personal or financial interest, suggests Mr. Bederov. "It is possible that some of the participants were insulted or underpaid the money promised from the fraudulent scheme," he says. - <url> sidebar
Maza has been hacked before. The previous hack occurred in February 2011, and then the data of more than 2,000 users was compromised, as well as all their correspondence on the forum.
***
Maza hack in 2011
The forum dealt in spam, hacker attacks, money withdrawal, trading in online casino accounts, and fake documents
The original of this material
© Xakep.ru, 26.02.2011, Hacked the largest cybercrime forums in the Russian Federation, Illustrations: via Xakep.ru
The most famous closed forum for cybercriminals to date "MAZA.la "(or as it is also called, "MAZAFAKA"), whose administrators are Afx (presumably Alexey), Render, 4x4 and Fiesta, was subjected to a massive hacker attack on February 18, resulting in a forum database consisting of more than two thousand It was stolen and made available to the public.
The second wave was attacked no less private forum "Direct Connection", the administrator of which is a certain" k0pa", a native of the group" CyberLords Team " — the same team that the scandalous hacker from Novosibirsk Evgeny Anikin was a member of. Analysts suggest that Russian carders have started their own "Internet war" for the redistribution of influence in the world of cybercrime, the prerequisites of which are known only to them.
MAZA.la
This forum was private and completely closed, access to it was open only by the presence of several trusted and reputable guarantors who already have an account on the forum. The project's security was ensured taking into account the latest trends in the field of information security: the use of digital security certificates, a built-in anti-phishing filter, etc. In addition, the project's servers were located in an area that was not subject to all possible cybercrime laws-in Taiwan.
A screenshot with a dump of Maza users has been publishedThe range of people allowed to participate was constantly narrowed and checked by a special responsible person — "MF_SUPPORT", a native of Ukraine, whose work was funded by Administrators. In many ways, it was the quality of MF_SUPPORT's work that determined what the forum's contingent would be like. In addition, they also checked all transactions of forum participants.
"Cybercriminals use the most sophisticated schemes, and their places of communication are highly anonymous, so only a similar-minded contingent that shares the legal side of the issue with law enforcement agencies can resist them," said Joseph Blank, a representative of the RSA Anti-fraud Command Center.
Structurally, the activity of intruders was divided into several categories:
- production of forged documents (passports, driver's licenses,
securities and instructions); - trading accounts of well-known online casinos, lottery agencies,
and bookmakers; - organization of unauthorized mass mailings;
- developing and creating malicious code;
- organization of services for withdrawing illegally obtained funds.

After publishing one of the screenshots from the forum on the Krebsonsecurity project, the attackers carefully took care of their anonymity, constantly changing their contactsAmong the forum participants "MAZA.la "there were such sensational "nicknames" as BadB (Vladislav Khorokhorin, 27 years old, arrested in France), Severa (a well-known spammer Pyotr Lavashov, who continues his criminal activities), zo0mer (Sergey Kozerev, against whom the US NSA conducted a separate investigation to identify sales lines for dumps. My0 (credit card merchant Roman Kkhoda, 26 years old), many of whom suffered a very harsh fate. All of them, in one way or another, fell under the eyes of Interpol and international security agencies, which have been looking for fraudsters for years.

Forum participants actively tracked all the sorrows and misfortunes of their colleagues, covering the arrests of their" colleagues " in cybercrime (BadB-Vladislav Khorokhorin, arrested on August 7 in Nice for selling dumps of credit cards of users of many European countries)The participants themselves admitted that the forum became available not only to their "sphere", but also to people in uniform. For the first time, one of the official screenshots of the closed forum was made available to the foreign online publication Krebsonsecurity on October 24, 2010, which published a screenshot of the forum topic, which discussed the appearance of the new banking Trojan SpyEye at that time.

Peter Severa, a Russian who is one of the TOP 20 most famous spammers in the world, successfully participates in the discussion of forum topics and offers his services to cybercriminals in the Spam section
Direct Connection
DC is a more private forum, although the faces there are absolutely the same.
Participants of such closed platforms do not mind "working" in the Russian banking sector, issuing VTB bank cards to front persons for subsequent withdrawal of funds.For example, Peter SEVERA, a world-famous Russian spammer, advertises his services on two sites, only on DC — he does it in the person of a moderator.

The most reputable cyber scammers can be seen on both sites, but in different rolesUnknown hackers broke into both forums, stealing the entire user base and their correspondence. Currently, the database has fallen into the hands of the most famous companies for the prevention of cybercrime and fraud — RSA, Anti Money Laundering Alliance and IISFA.
***
Price of hacking a hacker forum-from $1 million
The original of this material
© Kommersant, 19.03.2021, "You can earn much more from attacks abroad"
Yulia Stepanova
Pavel Sitnikov, a former Russian hacker, told Kommersant about the work of Russian-language cybercrime forums and the consequences of hacking them.
— When and how did Russian-language hacker forums appear?
- Forums appeared in the 1990s to exchange information and communicate between hackers. They started making money on these sites in the 2000s. Exploit was originally a free open forum with a technical focus: its participants shared information about hacking methods and vulnerabilities. Later, the forum became more private, and registration on it began to cost $100. Maza and Verified are closed sites. They mostly host fraudulent schemes. Registration on Maza costs $1 thousand, for it you need to have three guarantors from among the forum participants.
— The leaked Maza database has more than 2 thousand users. Is this the actual number of forum participants?
— I think that in reality there were less than 2 thousand people communicating on the forum. Basically, there were those who had registered since its foundation. In recent years, new posts have rarely appeared on Maza. But the participants continued to conduct business and exchange contacts in private messages. They are the main value when hacking a forum. You can't earn money from this information, but it's interesting for the authorities.
— How will forum hacking affect the hacker business?
— The main consequence will be the replenishment of the" Most wanted FBI "honor roll. The impact of hacking on the hacker business and community is very painful. Forum participants have been doing business on these sites for decades, and after hacking, the public finds out about it. Hackers are afraid of being exposed.
— Can prices for cybercrime services rise?
— I think the prices of "breakout" will rise. But this is more likely due to the tightening of the policy of Roskomnadzor and the Ministry of Internal Affairs against leaks of personal data: the requirement to close bots-penetrators in Telegram, increasing fines for violations in the processing of such data.
— How much can hacking a hacker forum cost?
- From $1 million for a medium-sized forum to infinity.
— Do such hacks occur frequently?
- Attacks on hacker forums have always been successful — but they almost always try to hide them in all possible ways. There have been frequent attacks on Exploit before. This usually happens due to internal disputes, for example, one of the participants was blocked or deleted and they take revenge on the admins.
— Can attacks on forums be a response to the attacks of Russian-speaking hackers OldGremlin on Russian companies last year?
— It is not customary for Russian-speaking hackers to work on a domain zone .ru. This is due to the fact that, firstly, it is not good to shit where you live, and secondly, you can earn much more from attacks abroad. I don't think the forum hacks were a response to last year's attacks on Russian companies, because I doubt that they were attacks specifically from OldGremlin.
— What can be the reason for attacks on forums?
- The current attacks of hacker sites are a show execution. There is only one group working, and it is not yet clear who it is, but there are suspicions. The reason is the redistribution of spheres of influence. Those who were or are directly related to the sites or serve them are behind this. It is unlikely, almost unbelievable, that these are foreign hacker groups or special services.
