Cryptographic attacks are sweeping the world like a tsunami. In Russia, companies with previously compromised credentials are more likely to fall under the wave. Another situation is when victims used publicly available applications with vulnerabilities, such as Microsoft Exchange. If the first case accounts for 24% of cryptographic attacks, then the second case accounts for 43%. Such data is provided by Kaspersky Lab in its annual report.
However, this article will not focus on the causes of the disaster, but on the exciting moment-negotiations with extortionists. The Cyber Media portal has studied the real correspondence of cryptographers with victims over the past three years. The most illustrative examples, conclusions and recommendations of experts – see below.
The second way to choose a target for hacking is random. Most often, a company becomes a victim of cryptographers only because it fell under a large-scale network scan, which was massively conducted by the group.
And finally, the third way is when ransomware attacks the company purposefully. As Dmitry Ovchinnikov notes, this is the worst option, since the criminals knew who they were attacking and prepared their attack well. Most likely, these are experienced hackers from a well-known criminal group.
Such groups are so advanced that they track the victim's earnings and issue a ransom based on this amount. This is usually 1-5% of the company's annual revenue. Such data was presented in an interview with Oleg Skulkin from BI. ZONE.
An example of a well – planned attack is the Acer case, which became known in 2021. Then the publication The Record said that a major manufacturer of computer equipment demanded 50 million US dollars (a record publicly announced amount for such incidents). In the same article, a screen of darknet correspondence with extortionists from the REvil group was given. He makes it clear that at some point the negotiations have reached an impasse.
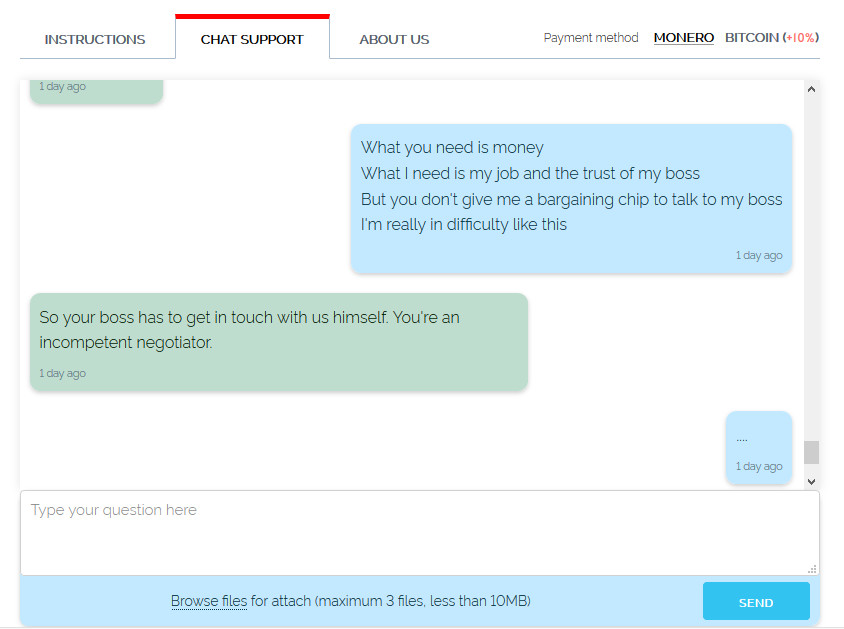
When extortionists demand to call one of the adults…
Groups often make no secret of the fact that they collect and analyze data about the victim. Sometimes called sources. In the example below, they refer to information about the victim's credit accounts and purchased cyber insurance policies.
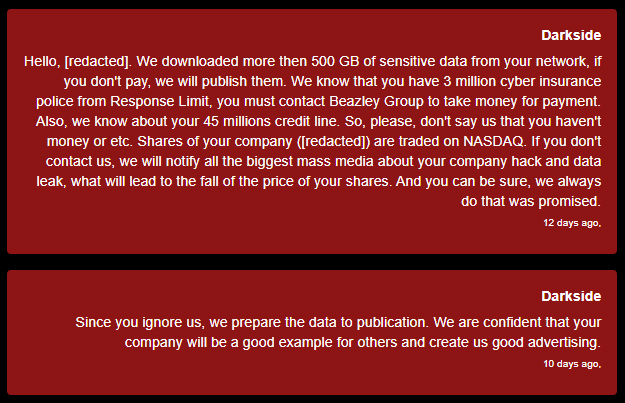
"What's your proof?" according to the Darkside version
The situation is worse if cryptographers threaten not only to publish, but also to sell the victim's confidential data. In particular, the guys from Conti used to be famous for such blackmail.
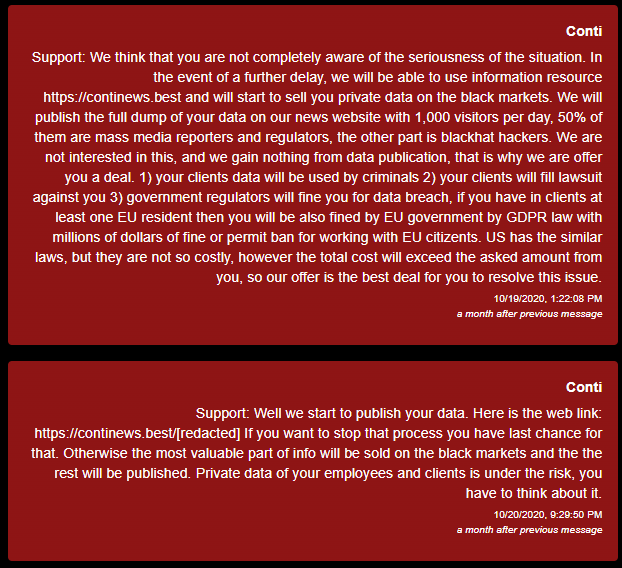
And they, like many extortionists, threaten fines from the European Union and the US government.
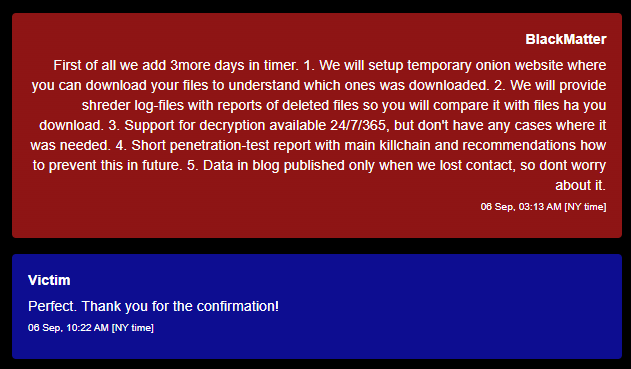
Need penetration tests? Criminals will help (point 4)
At the same time, cryptographers often use traditional marketing moves. Many offer discounts for a quick purchase or transfer in a convenient currency (bitcoins).
Sometimes the customer focus is off the scale – attackers make concessions because of the sympathy and difficult financial situation of the victim. In the example below, the Czech company was able to prove that it was not ready to pay US $ 1 million. As a result, the purchase price was reduced by 50%.
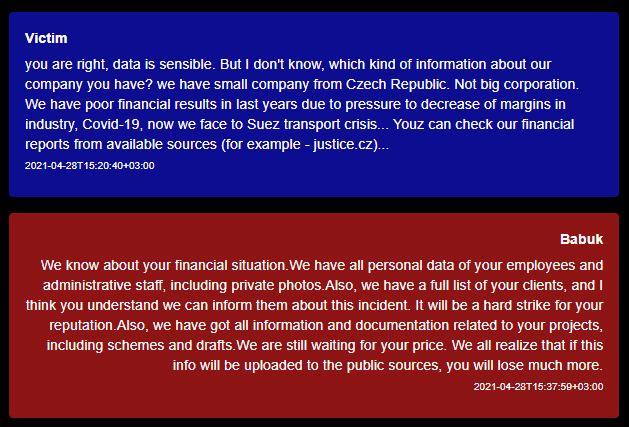
Victim complains about Suez Canal lockdown and pandemic
There are even stories with absolute happyendom. As a rule, such negotiations start with a total mistake – hackers miss the target. This is what happened to a company from Armenia. Extortionists from Avaddon expected to receive 300 thousand dollars, to which the interlocutor gave them: "This is the budget of my entire country!". A few days later, it turned out that the group does not work in the CIS countries and therefore will decrypt all data for free.
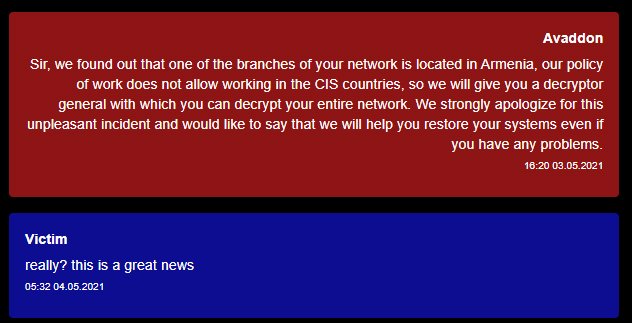
Here's the twist: the cryptographer apologizes to the victim
Experts confirm that you need to communicate. At least in order to get evidence of hacking. In practice, they are provided by all serious cryptographers.
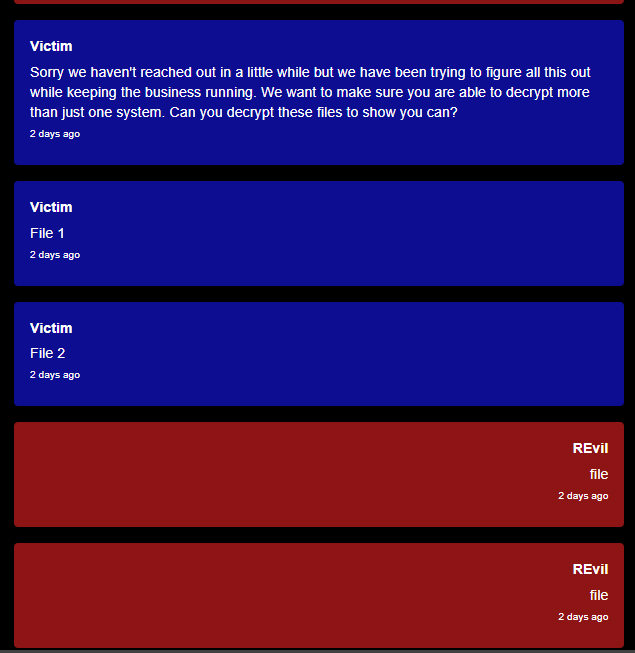
Usually proofs are provided immediately
The next stage of negotiations is to assess the damage that awaits the company. Perhaps the amount of the buyout will be comparable to the work on restoring infrastructure and data. Moreover, there is no guarantee that after paying the ransom, attackers will not leave holes in your information security system or give you the key to decrypt data.
In addition, experts recommend contacting the police as soon as you receive a message demanding a ransom. But this step remains at the discretion of the company's management.
Many things, as it turned out in practice, can be negotiated. If you need to lower the price or help with the installation of the decryptor program, please. I want to test the product in advance or get advice for the future-welcome. Malefactors live by the rules of business and value their reputation. But all this applies only to serious groups, of which there are no more than a dozen in the world so far.
In all other cases, it is better not to expect that the situation will be corrected by a single transfer in bitcoins. Experts recommend following the algorithm:
In any case, you can't do without information security specialists in a situation with cyber extortion. Even if the ransomware received a ransom and decrypted the files, the data remained compromised. What to do with them next is a completely different story. And it is better to solve it by specialists.
The article uses project materials ransomch.at.*
However, this article will not focus on the causes of the disaster, but on the exciting moment-negotiations with extortionists. The Cyber Media portal has studied the real correspondence of cryptographers with victims over the past three years. The most illustrative examples, conclusions and recommendations of experts – see below.
Ransomware attacks: How hackers choose a target
Experts believe that cyber-extortionists usually follow one of three paths in their search for victims. The first and most obvious one is that one of the employees is to blame.Dmitry Ovchinnikov
Chief Specialist of the Integrated Information Security Systems Department of Gazinformservis
An insider can leak information to attackers. It may also be a former colleague who was not denied access in time or did not know about a vulnerability in your network. Without a detailed investigation, this can not be determined, so do not rush to accuse your colleagues of criminal actions. But you can't discount this option either. This is a bad option, as you can get nasty out of a sense of revenge. Pay the money, and the servers will remain encrypted.
The second way to choose a target for hacking is random. Most often, a company becomes a victim of cryptographers only because it fell under a large-scale network scan, which was massively conducted by the group.
Dmitry Ovchinnikov
Chief Specialist of the Integrated Information Security Systems Department of Gazinformservis
Most likely, in this case, the ransom demand will not be very large, since you are faced with medium-sized criminals who simply found your resources exposed on the Internet without protection and simply broke into your servers, without even specifying who they are attacking. Generally acceptable option. The negotiations will be held without surprises.
And finally, the third way is when ransomware attacks the company purposefully. As Dmitry Ovchinnikov notes, this is the worst option, since the criminals knew who they were attacking and prepared their attack well. Most likely, these are experienced hackers from a well-known criminal group.
Dmitry Ovchinnikov
Chief Specialist of the Integrated Information Security Systems Department of Gazinformservis
But even in this case, do not be upset. If you are being targeted, then the criminals are professionals. They are all right with motivation, they work for money, which means that it is easy to negotiate with them.
Such groups are so advanced that they track the victim's earnings and issue a ransom based on this amount. This is usually 1-5% of the company's annual revenue. Such data was presented in an interview with Oleg Skulkin from BI. ZONE.
An example of a well – planned attack is the Acer case, which became known in 2021. Then the publication The Record said that a major manufacturer of computer equipment demanded 50 million US dollars (a record publicly announced amount for such incidents). In the same article, a screen of darknet correspondence with extortionists from the REvil group was given. He makes it clear that at some point the negotiations have reached an impasse.

When extortionists demand to call one of the adults…
Groups often make no secret of the fact that they collect and analyze data about the victim. Sometimes called sources. In the example below, they refer to information about the victim's credit accounts and purchased cyber insurance policies.

"What's your proof?" according to the Darkside version
Blackmail entered the chat
Judging by real correspondence with victims, cyber-extortionists often not only encrypt data, but also threaten to publish it. For many companies, this is a heavy blow – an incident can affect relationships with customers and partners and damage the company's reputation.The situation is worse if cryptographers threaten not only to publish, but also to sell the victim's confidential data. In particular, the guys from Conti used to be famous for such blackmail.

And they, like many extortionists, threaten fines from the European Union and the US government.
Nothing personal, just business
Groups that engage in cyber extortion often don't look like criminals in chat rooms, but rather like major IT vendors. They provide solutions for decrypting files, they have free demo versions of the product, and even their own analytical departments. Moreover, many extortionists are engaged in consulting – after payment, they are ready to tell you exactly how the client's network was hacked and what security measures they need to take.
Need penetration tests? Criminals will help (point 4)
At the same time, cryptographers often use traditional marketing moves. Many offer discounts for a quick purchase or transfer in a convenient currency (bitcoins).
Sometimes the customer focus is off the scale – attackers make concessions because of the sympathy and difficult financial situation of the victim. In the example below, the Czech company was able to prove that it was not ready to pay US $ 1 million. As a result, the purchase price was reduced by 50%.

Victim complains about Suez Canal lockdown and pandemic
There are even stories with absolute happyendom. As a rule, such negotiations start with a total mistake – hackers miss the target. This is what happened to a company from Armenia. Extortionists from Avaddon expected to receive 300 thousand dollars, to which the interlocutor gave them: "This is the budget of my entire country!". A few days later, it turned out that the group does not work in the CIS countries and therefore will decrypt all data for free.

Here's the twist: the cryptographer apologizes to the victim
I can't keep silent, or How to communicate with cryptographers
What should I do if cybercriminals managed to encrypt the company's data and they got in touch? The example above shows that silence would cost the Armenian victim more than willingness to engage in dialogue.Experts confirm that you need to communicate. At least in order to get evidence of hacking. In practice, they are provided by all serious cryptographers.

Usually proofs are provided immediately
The next stage of negotiations is to assess the damage that awaits the company. Perhaps the amount of the buyout will be comparable to the work on restoring infrastructure and data. Moreover, there is no guarantee that after paying the ransom, attackers will not leave holes in your information security system or give you the key to decrypt data.
Dmitry Ovchinnikov
Chief Specialist of the Integrated Information Security Systems Department of Gazinformservis
Once you have thoroughly calculated the consequences of the damage, you can decide whether to pay the ransom or refuse. In both cases, it is necessary to conduct a full investigation of the incident and necessarily strengthen security measures. If you do not have enough experience in forensic science, then attract outside experts.
In addition, experts recommend contacting the police as soon as you receive a message demanding a ransom. But this step remains at the discretion of the company's management.
Fyodor Muzalevsky
Director of the Technical Department of RTM Group
If you encounter cryptographers for the first time, I advise you to record the traces of the crime. This way you can contact the law enforcement agencies.
In addition, you need to check for backups and give an order to restore data. And I recommend not to take everything to heart. Negotiations are a standard technique of cyber scammers, they have nothing against you specifically.
Conclusions
Cyber extortion is primarily a business, so it is better to conduct negotiations with groups in a business format.Many things, as it turned out in practice, can be negotiated. If you need to lower the price or help with the installation of the decryptor program, please. I want to test the product in advance or get advice for the future-welcome. Malefactors live by the rules of business and value their reputation. But all this applies only to serious groups, of which there are no more than a dozen in the world so far.
In all other cases, it is better not to expect that the situation will be corrected by a single transfer in bitcoins. Experts recommend following the algorithm:
- Get evidence of hacking and record traces of the crime.
- Assess possible damage – financial and reputational.
- Contact the police (optional).
- Pay or ignore it.
- Conduct an investigation into the incident and strengthen security measures.
In any case, you can't do without information security specialists in a situation with cyber extortion. Even if the ransomware received a ransom and decrypted the files, the data remained compromised. What to do with them next is a completely different story. And it is better to solve it by specialists.
The article uses project materials ransomch.at.*
