Victims lose control of their savings, unaware of the hack until the last moment.
Cybersecurity experts have discovered a complex multi-stage attack that uses phishing messages with invoice themes to spread a variety of malicious software, including Venom RAT, Remcos RAT, XWorm, NanoCore RAT, and various infostilers targeting cryptocurrency wallets.
According to Fortinet researchers, attackers send emails with attachments in Scalable Vector Graphics (SVG) format. When such files are opened, the infection chain is activated.
A distinctive feature of the attack is the use of the BatCloak malware obfuscation tool, as well as ScrubCrypt for delivering malware in the form of obfuscated batch scripts.
BatCloak, which has been publicly available on shadow forums since the end of 2022, is based on the Jlaive tool. Its main function is to load the next stage of the payload in a way that bypasses traditional detection mechanisms. The ScrubCrypt crypter, first documented by researchers in March 2023, is also considered one of the iterations of BatCloak.
In the latest campaign analyzed by experts, the aforementioned SVG file serves as a channel for transmitting a ZIP archive containing a batch script, probably created using BatCloak. The script then unpacks the ScrubCrypt batch file for the final launch of Venom RAT, but not before configuring persistence on the system and taking steps to bypass AMSI and ETW protection.
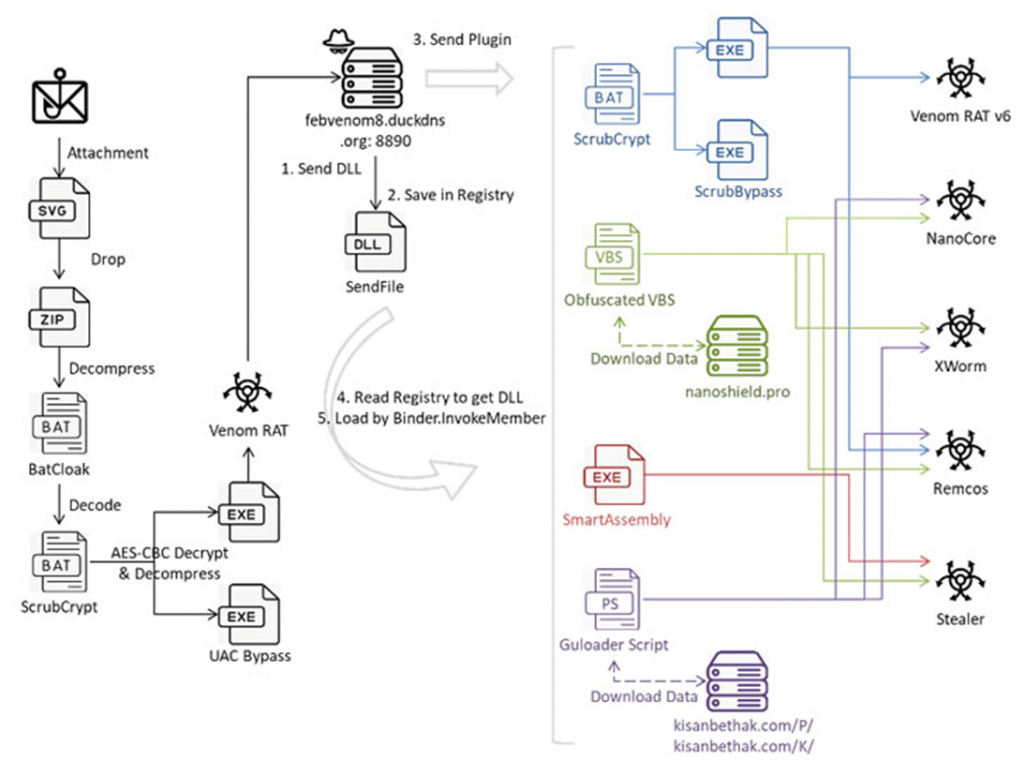
Full attack pattern
Venom RAT, which is an offshoot of Quasar RAT, allows attackers to monitor infected systems, collect confidential information, and execute commands received from the management server.
"The main Venom RAT program may seem simple, but it supports communication channels with the C2 server to get additional plugins, expanding the possible list of malicious actions," says security researcher Kara Lin.
The plugin system also delivers an infostiler that collects information about the system and exfiltrates data from folders associated with crypto wallets and applications such as Atomic Wallet, Electrum, Ethereum, Exodus, Jaxx Liberty, Zcash, Foxmail, and Telegram.
"Our analysis reveals a sophisticated attack using layered obfuscation and evasion techniques to propagate and execute VenomRAT via ScrubCrypt," Lin adds.
Attackers use a variety of methods, including phishing emails with malicious attachments, obfuscated script files, and PowerShell GuLoader, to infiltrate and compromise victims ' systems. In addition, the deployment of plugins via different payloads emphasizes the versatility and adaptability of this malicious campaign.
A similar incident, which we covered just yesterday, demonstrates similar tactics for spreading malware through phishing campaigns with the theme of invoices aimed at corporate networks.
Nowadays, a simple click on an unverified investment can lead to very serious consequences, including leakage of confidential data and financial losses. Therefore, it is critically important to constantly update your cybersecurity knowledge and use all available security tools to minimize the risks of virtual threats.
Cybersecurity experts have discovered a complex multi-stage attack that uses phishing messages with invoice themes to spread a variety of malicious software, including Venom RAT, Remcos RAT, XWorm, NanoCore RAT, and various infostilers targeting cryptocurrency wallets.
According to Fortinet researchers, attackers send emails with attachments in Scalable Vector Graphics (SVG) format. When such files are opened, the infection chain is activated.
A distinctive feature of the attack is the use of the BatCloak malware obfuscation tool, as well as ScrubCrypt for delivering malware in the form of obfuscated batch scripts.
BatCloak, which has been publicly available on shadow forums since the end of 2022, is based on the Jlaive tool. Its main function is to load the next stage of the payload in a way that bypasses traditional detection mechanisms. The ScrubCrypt crypter, first documented by researchers in March 2023, is also considered one of the iterations of BatCloak.
In the latest campaign analyzed by experts, the aforementioned SVG file serves as a channel for transmitting a ZIP archive containing a batch script, probably created using BatCloak. The script then unpacks the ScrubCrypt batch file for the final launch of Venom RAT, but not before configuring persistence on the system and taking steps to bypass AMSI and ETW protection.

Full attack pattern
Venom RAT, which is an offshoot of Quasar RAT, allows attackers to monitor infected systems, collect confidential information, and execute commands received from the management server.
"The main Venom RAT program may seem simple, but it supports communication channels with the C2 server to get additional plugins, expanding the possible list of malicious actions," says security researcher Kara Lin.
The plugin system also delivers an infostiler that collects information about the system and exfiltrates data from folders associated with crypto wallets and applications such as Atomic Wallet, Electrum, Ethereum, Exodus, Jaxx Liberty, Zcash, Foxmail, and Telegram.
"Our analysis reveals a sophisticated attack using layered obfuscation and evasion techniques to propagate and execute VenomRAT via ScrubCrypt," Lin adds.
Attackers use a variety of methods, including phishing emails with malicious attachments, obfuscated script files, and PowerShell GuLoader, to infiltrate and compromise victims ' systems. In addition, the deployment of plugins via different payloads emphasizes the versatility and adaptability of this malicious campaign.
A similar incident, which we covered just yesterday, demonstrates similar tactics for spreading malware through phishing campaigns with the theme of invoices aimed at corporate networks.
Nowadays, a simple click on an unverified investment can lead to very serious consequences, including leakage of confidential data and financial losses. Therefore, it is critically important to constantly update your cybersecurity knowledge and use all available security tools to minimize the risks of virtual threats.
