Like many of you, we read dozens of English-language texts about our work. Some of them are so interesting that I want to share them. We decided to publish translations from time to time – some people may find them useful.
Let's start with an article by Brian Krebs from the Krebs on Security blog. He studied a 25-page report from the Cambridge University Cybercrime Center on what makes hackers work and how attractive it really is. The text is given with small abbreviations that do not affect the meaning. The article helps to remove the "rose-colored glasses" when looking at the world of cybercrime.
Our head of the information security service Alexey Drozd (aka labyrinth) gave his additions and comments in the course of the text. After all, although cybercrime is not limited to individual countries, there are still differences on different sides of the ocean. You can expand or hide comments to read only the translation of the original text.
When law enforcement agencies report on the arrest of a cybercriminal, the defendant often looks like a daredevil who conducts complex, but profitable and exciting activities. But modern cybercriminals are increasingly working for the customer. As a result, the bulk of cybercriminals time is spent on tedious and boring work providing customer service and technical support. Such conclusions are made by researchers at the Cybercrime Center at the University of Cambridge.
Excuses from hackers
Their document examines the amount of work and its quality that cybercriminals have to support. In particular, the researchers focused on how criminals who sell botnet creation services, custom malware, organize DDoS attacks, etc. work. To do this, we interviewed current and former hackers, as well as studied messages on underground forums and in chat rooms.
A stock image of a hacker that has become a textbook. Hackers are portrayed as mysterious heroes. In reality, these are people who lead a boring office life
Romantic descriptions of cybercrime activities ignore the mundane, meaningless work that must be done to support the illegal online economy. Meanwhile, most of the people involved in criminal schemes do exactly what they do: they do boring office work. No more exciting than the actions of legal system administrators.
See for yourself
Citadel is a social platform for serving hacker clients. Never before has there been anything like the Citadel CRM Store, built on the model of the best support systems for ordinary commercial products:
Richard Clayton, co-author of the report and director of the Cambridge Cybercrime Center, believes that politicians and law enforcement agencies are doing themselves a disservice by issuing press releases to investigate the actions of sophisticated and advanced criminals.
"When people are interested in cybercrime, they want to learn about 'rock stars' and exciting high-paying jobs. In fact, for most people involved in cybercrime, they do something completely different, " says Clayton KrebsOnSecurity.
And indeed,
when in 2014 Sergey Pavlovich's book "How I stole a million. Confessions of a repentant carder", it read like a real detective story. It's no secret that in some aspects the hero could be envied. But in my opinion, Sergey's example is an exception to the rule. After all, if you look at a "typical" violator, it turns out to be an employee of a mobile phone salon who uploaded the details of subscriber calls for a couple of hundred rubles. Of the 327 court cases in 2019, 70% were from the telecom industry.
Quote from a study by the University of Cambridge's Cybercrime Center:
The lifetime of underground services depends on reputation, and its basis is reliability, efficiency, quality of customer service, and speed of response to customer requests. As a result, these services usually require significant investment in the personnel needed to operate the customer support service (via a ticket system or live chat), solve payment problems, or teach customers how to use the service.
I recall the initiative of one very large platform for the sale of drugs.
A telegram chat of emergency medical care was created especially forfinished end customers. The platform was ready to pay for expert advice so that they could help consumers overcome crisis situations remotely (for example, withdrawal symptoms). We can only guess how much money was spent on such a "service".
In an interview, a former support service administrator explained how tired he was of working with clients who thought it was normal to put all the hard work of running the service on him.
From the interview:
The researchers note that burnout is a common problem of customer service employees, " which is characterized not so much by a gradual withdrawal from once interesting activities, but by an increase in boredom and frustration. As soon as the low social and financial ceiling of this work is reached."
Besides,
insignificant employees are merged first. For example, to make a deal with the investigation and shorten your sentence.
Developers are also quickly overwhelmed by customer requests and negative reviews for any failure, even if the service generally works well.
A vivid illustration of how developers are held hostage to this situation is the story of the infamous Zeus Trojan, a powerful password – stealing software that stole hundreds of millions of dollars from companies. It is believed that the malware author quit his job and made the source code public mainly in order to focus on less tedious work than supporting hundreds of clients. By the way, by opening the code, he gave rise to an entire industry of "malware as a service".
The ZeuS experience may not be the best example. The service owner's desire to get away from supporting hundreds of customers has led him to focus his attention and resources on creating a much more sophisticated malware called GameOverZeus.
A similar story happened with Marcus Hutchins, who told Wired that he "quickly got bored with his botnets and hosting services, which required communicating with a lot of"cranky customers." Therefore, he chose to focus his efforts on something that he liked much more – improving his own malware. Cambridge-based Clayton and his colleagues argue that the last two examples are the exception rather than the rule, as ordinary hackers are forced to pull their own strings.
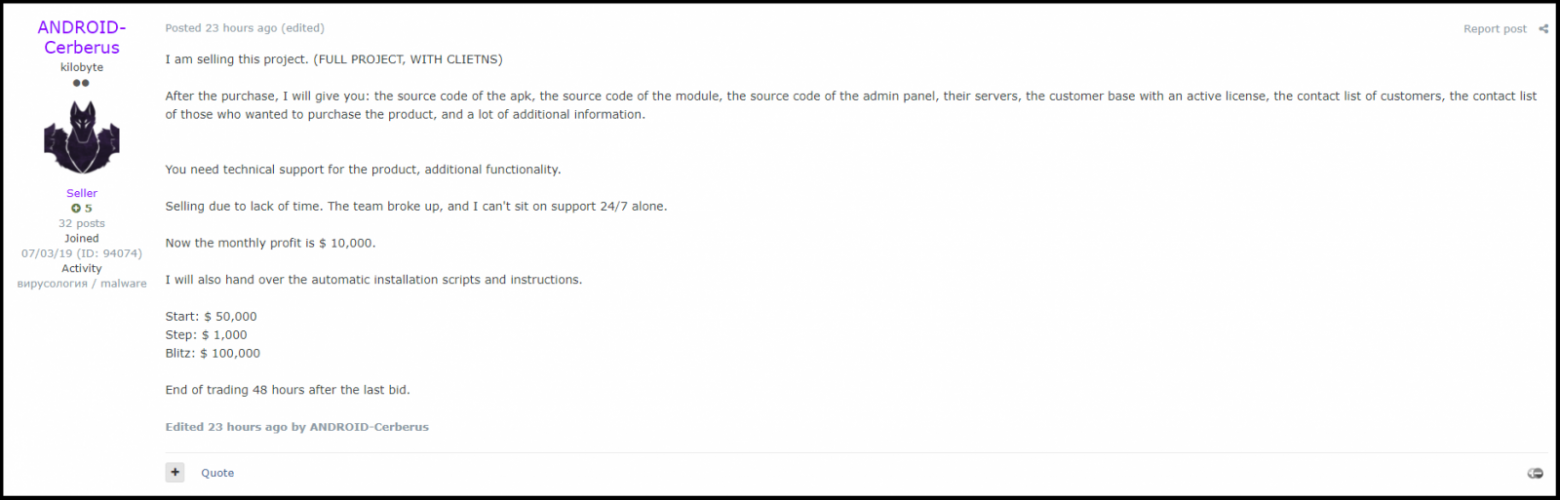
A good example is the Cerberus banking malware.
In early August, source codes were put up for sale on one of the hacker forums. This price includes everything at once: from the source code to the client list, along with installation instructions and scripts for working together components. In other words, the buyer will receive the source code of the malicious APK, the module, as well as "keys" from the admin panel and servers.
Moreover, the seller wrote that the reason for selling the source code is simple: allegedly, the hack group that created Cerberus has broken up, and there is no one else to deal with round-the-clock support. As a result, everything was put up for sale, including the database of customers with an active license, as well as contacts of customers and potential buyers.
Researchers point to an important factor in the fight against cybercrime, which is often overlooked. We are talking about making the work of cybercriminals as time-consuming and boring as possible. Destroying domain names and other infrastructure makes more sense than just"catching up". Yes, attackers simply move the infrastructure and continue working, but this creates constant tedious work for them.
In the document, the researchers stipulate that speaking about the "boredom" of low-skilled underground work, they do not want to cast a shadow on the value and importance of the work of system administrators working in the legal field. You can't compare the knowledge and skills of these two groups of people.
Because it's not just about boredom,
but also in a hassle. It's probably a shame when you realize that on the bright side you can earn the same amount or even more, while having a social package and not having problems with the law. But even if you discard the nerves, there are still a lot of problems of domestic use. So, a successful hacking or theft of data/money is at best 50% of success. Data must be sold, money must be withdrawn. I already wrote above that breaking alone is hardly possible. The same applies to money withdrawal. At almost all stages, you will have to interact with "partners", who can be much more careless in security issues. As a result, even if the hacker himself knows how to be anonymous, it is not a fact that his accomplices know this.
The authors believe that the wording of press releases, statements of law enforcement agencies and politicians should change. Now they focus on the fact that criminal behavior is harmful and dangerous, that this activity requires a high level of technical skills, that there is a lot of money involved, but there is a high risk of detection, arrest and prosecution. All this only fuels the desire of those who are employed in the black sector of the economy. Conversely, messages that emphasize that work is tedious, low-skilled, and poorly paid can affect the inhabitants of the near-criminal subculture.
In addition, messages that highlight the lack of sysadmins and pen testers in legitimate businesses ("you can do the same in the legal field and get good money") can demonstrate that the desired experience can be obtained in a more prosaic way, without plunging into illegal activities.
And not only experience.
Many companies are willing to pay for finding vulnerabilities in their products. And some are even willing to buy someone else's. The evolution of cybercrime has led to the fact that we see the same business processes on different sides. But only on the " dark side "there are not even" cookies " left.
The study itself is available here
(c) Original author: Brian Krebs
Let's start with an article by Brian Krebs from the Krebs on Security blog. He studied a 25-page report from the Cambridge University Cybercrime Center on what makes hackers work and how attractive it really is. The text is given with small abbreviations that do not affect the meaning. The article helps to remove the "rose-colored glasses" when looking at the world of cybercrime.
Our head of the information security service Alexey Drozd (aka labyrinth) gave his additions and comments in the course of the text. After all, although cybercrime is not limited to individual countries, there are still differences on different sides of the ocean. You can expand or hide comments to read only the translation of the original text.
When law enforcement agencies report on the arrest of a cybercriminal, the defendant often looks like a daredevil who conducts complex, but profitable and exciting activities. But modern cybercriminals are increasingly working for the customer. As a result, the bulk of cybercriminals time is spent on tedious and boring work providing customer service and technical support. Such conclusions are made by researchers at the Cybercrime Center at the University of Cambridge.
Excuses from hackers
Their document examines the amount of work and its quality that cybercriminals have to support. In particular, the researchers focused on how criminals who sell botnet creation services, custom malware, organize DDoS attacks, etc. work. To do this, we interviewed current and former hackers, as well as studied messages on underground forums and in chat rooms.
A stock image of a hacker that has become a textbook. Hackers are portrayed as mysterious heroes. In reality, these are people who lead a boring office life
Romantic descriptions of cybercrime activities ignore the mundane, meaningless work that must be done to support the illegal online economy. Meanwhile, most of the people involved in criminal schemes do exactly what they do: they do boring office work. No more exciting than the actions of legal system administrators.
See for yourself
Citadel is a social platform for serving hacker clients. Never before has there been anything like the Citadel CRM Store, built on the model of the best support systems for ordinary commercial products:
- bug reports and technical support;
- requests for creating additional modules and applications (public or private requests);
- voting for new ideas, offering your own price for the development/improvement of a new module, the possibility of partial prepayment to motivate developers;
- ability to comment on any app and send a private message to another social network member;
- monitoring all stages of development of a new module, developers update the current status and the time remaining until the end of development;
- convenient jabber notifications for new users and new messages, or new modules/applications.
Richard Clayton, co-author of the report and director of the Cambridge Cybercrime Center, believes that politicians and law enforcement agencies are doing themselves a disservice by issuing press releases to investigate the actions of sophisticated and advanced criminals.
"When people are interested in cybercrime, they want to learn about 'rock stars' and exciting high-paying jobs. In fact, for most people involved in cybercrime, they do something completely different, " says Clayton KrebsOnSecurity.
And indeed,
when in 2014 Sergey Pavlovich's book "How I stole a million. Confessions of a repentant carder", it read like a real detective story. It's no secret that in some aspects the hero could be envied. But in my opinion, Sergey's example is an exception to the rule. After all, if you look at a "typical" violator, it turns out to be an employee of a mobile phone salon who uploaded the details of subscriber calls for a couple of hundred rubles. Of the 327 court cases in 2019, 70% were from the telecom industry.
Quote from a study by the University of Cambridge's Cybercrime Center:
"As cybercrime has essentially become an entire underground economy, there is also a need for a set of auxiliary supporting infrastructure-just like in the legal economy of developed countries. Cybercriminals have started creating boring, low-paying jobs. This work is less about adventurism and involvement in the forbidden world. It is about the need to ensure the stability of services. But those who came to these positions were most likely attracted by exciting images of hackers and complex technical tasks.
Real work does not give you the enthusiastic emotions that were in the early hacker communities. Most modern hackers can be compared to messengers in drug gangs. They are willing to work for little money in the hope that one day they will be able to rise in the hierarchy to the top positions. The real state of affairs causes boredom, which occurs in any other job, where a person understands that it is impossible to achieve status and high incomes. In other words, the shadow online economy is characterized by the same processes as the regular labor market."
Cyberdepression
The lifetime of underground services depends on reputation, and its basis is reliability, efficiency, quality of customer service, and speed of response to customer requests. As a result, these services usually require significant investment in the personnel needed to operate the customer support service (via a ticket system or live chat), solve payment problems, or teach customers how to use the service.
I recall the initiative of one very large platform for the sale of drugs.
A telegram chat of emergency medical care was created especially for
In an interview, a former support service administrator explained how tired he was of working with clients who thought it was normal to put all the hard work of running the service on him.
From the interview:
"After a year of such work, I lost all motivation, I didn't care anymore. So I just left and started living a normal life. Creating a service (in the original booter service a. k. a. “stressor”) is not difficult. It is difficult to ensure its operability. You need to put all your effort, all your attention. You have to sit in front of the computer screen, scan, filter, then filter-and so on 30 times in 4 hours. It's infuriating."
The researchers note that burnout is a common problem of customer service employees, " which is characterized not so much by a gradual withdrawal from once interesting activities, but by an increase in boredom and frustration. As soon as the low social and financial ceiling of this work is reached."
Besides,
insignificant employees are merged first. For example, to make a deal with the investigation and shorten your sentence.
Whimsical customers
Developers are also quickly overwhelmed by customer requests and negative reviews for any failure, even if the service generally works well.
A vivid illustration of how developers are held hostage to this situation is the story of the infamous Zeus Trojan, a powerful password – stealing software that stole hundreds of millions of dollars from companies. It is believed that the malware author quit his job and made the source code public mainly in order to focus on less tedious work than supporting hundreds of clients. By the way, by opening the code, he gave rise to an entire industry of "malware as a service".
The ZeuS experience may not be the best example. The service owner's desire to get away from supporting hundreds of customers has led him to focus his attention and resources on creating a much more sophisticated malware called GameOverZeus.
A similar story happened with Marcus Hutchins, who told Wired that he "quickly got bored with his botnets and hosting services, which required communicating with a lot of"cranky customers." Therefore, he chose to focus his efforts on something that he liked much more – improving his own malware. Cambridge-based Clayton and his colleagues argue that the last two examples are the exception rather than the rule, as ordinary hackers are forced to pull their own strings.
A good example is the Cerberus banking malware.
In early August, source codes were put up for sale on one of the hacker forums. This price includes everything at once: from the source code to the client list, along with installation instructions and scripts for working together components. In other words, the buyer will receive the source code of the malicious APK, the module, as well as "keys" from the admin panel and servers.
Moreover, the seller wrote that the reason for selling the source code is simple: allegedly, the hack group that created Cerberus has broken up, and there is no one else to deal with round-the-clock support. As a result, everything was put up for sale, including the database of customers with an active license, as well as contacts of customers and potential buyers.

Boredom that kills interest in the case
Researchers point to an important factor in the fight against cybercrime, which is often overlooked. We are talking about making the work of cybercriminals as time-consuming and boring as possible. Destroying domain names and other infrastructure makes more sense than just"catching up". Yes, attackers simply move the infrastructure and continue working, but this creates constant tedious work for them.
In the document, the researchers stipulate that speaking about the "boredom" of low-skilled underground work, they do not want to cast a shadow on the value and importance of the work of system administrators working in the legal field. You can't compare the knowledge and skills of these two groups of people.
Because it's not just about boredom,
but also in a hassle. It's probably a shame when you realize that on the bright side you can earn the same amount or even more, while having a social package and not having problems with the law. But even if you discard the nerves, there are still a lot of problems of domestic use. So, a successful hacking or theft of data/money is at best 50% of success. Data must be sold, money must be withdrawn. I already wrote above that breaking alone is hardly possible. The same applies to money withdrawal. At almost all stages, you will have to interact with "partners", who can be much more careless in security issues. As a result, even if the hacker himself knows how to be anonymous, it is not a fact that his accomplices know this.
The authors believe that the wording of press releases, statements of law enforcement agencies and politicians should change. Now they focus on the fact that criminal behavior is harmful and dangerous, that this activity requires a high level of technical skills, that there is a lot of money involved, but there is a high risk of detection, arrest and prosecution. All this only fuels the desire of those who are employed in the black sector of the economy. Conversely, messages that emphasize that work is tedious, low-skilled, and poorly paid can affect the inhabitants of the near-criminal subculture.
In addition, messages that highlight the lack of sysadmins and pen testers in legitimate businesses ("you can do the same in the legal field and get good money") can demonstrate that the desired experience can be obtained in a more prosaic way, without plunging into illegal activities.
And not only experience.
Many companies are willing to pay for finding vulnerabilities in their products. And some are even willing to buy someone else's. The evolution of cybercrime has led to the fact that we see the same business processes on different sides. But only on the " dark side "there are not even" cookies " left.
The study itself is available here
(c) Original author: Brian Krebs
