How Windows Assistant became the hackers command center.
Trend Micro revealed new methods of cyberattacks by the RedCurl group, which uses a legitimate Windows component to execute malicious commands.
The Program Compatibility Assistant ( PCA) component, designed to solve compatibility problems with older programs, is now being exploited by attackers to bypass security systems and secretly execute commands by using the tool as an alternative command-line interpreter.
The RedCurl attack chain involves using phishing emails with malicious attachments in ISO and IMG format to activate a multi-step process that starts with downloading the curl utility from a remote server, which then acts as a channel for delivering the loader (ms.dll or ps.dll).
The malicious DLL, in turn, uses PCA to start the download process, which establishes a connection to the same domain that curl uses to load the loader. In addition, cybercriminals use the open source Impacket software to execute commands without authorization.
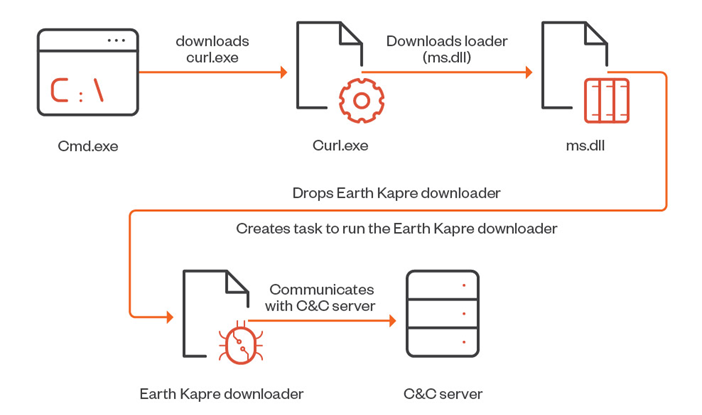
RedCurl Attack Chain
The RedCurl group, which has been active since 2018 and was first identified in 2019, specializes in cyber espionage. Attackers use unique tools to steal business correspondence, personal data of employees, and legal documents.
In February, F. A. C. C. T. researchers identified a new RedCurl malware campaign targeting organizations in Australia, Singapore, and Hong Kong. The attacks affected the construction, logistics, air transportation, and mining industries.
Trend Micro revealed new methods of cyberattacks by the RedCurl group, which uses a legitimate Windows component to execute malicious commands.
The Program Compatibility Assistant ( PCA) component, designed to solve compatibility problems with older programs, is now being exploited by attackers to bypass security systems and secretly execute commands by using the tool as an alternative command-line interpreter.
The RedCurl attack chain involves using phishing emails with malicious attachments in ISO and IMG format to activate a multi-step process that starts with downloading the curl utility from a remote server, which then acts as a channel for delivering the loader (ms.dll or ps.dll).
The malicious DLL, in turn, uses PCA to start the download process, which establishes a connection to the same domain that curl uses to load the loader. In addition, cybercriminals use the open source Impacket software to execute commands without authorization.

RedCurl Attack Chain
The RedCurl group, which has been active since 2018 and was first identified in 2019, specializes in cyber espionage. Attackers use unique tools to steal business correspondence, personal data of employees, and legal documents.
In February, F. A. C. C. T. researchers identified a new RedCurl malware campaign targeting organizations in Australia, Singapore, and Hong Kong. The attacks affected the construction, logistics, air transportation, and mining industries.
