Father
Professional
- Messages
- 2,602
- Reaction score
- 837
- Points
- 113
Leaked documents revealed the tracking of Internet traffic and the UK's involvement in espionage.
During the leak of secret documents, the Chinese company Xitan Lab revealed details about the NSA's sophisticated global Internet traffic monitoring system, which can intercept user traffic around the world and inject malware using browser-level vulnerabilities. The system includes two key components: Turboil and Turbine.
Turmoil and Turbine: The Heart of Global Surveillance
Turmoil is a passive data acquisition system that operates through sensors distributed across key points in the global network. The system analyzes the traffic passing through it, extracting valuable information from it, including encrypted VPN and VoIP data. In addition to monitoring Internet traffic, Turmoil can also monitor satellite communications, microwave communications, underwater optical cables, and other traffic.
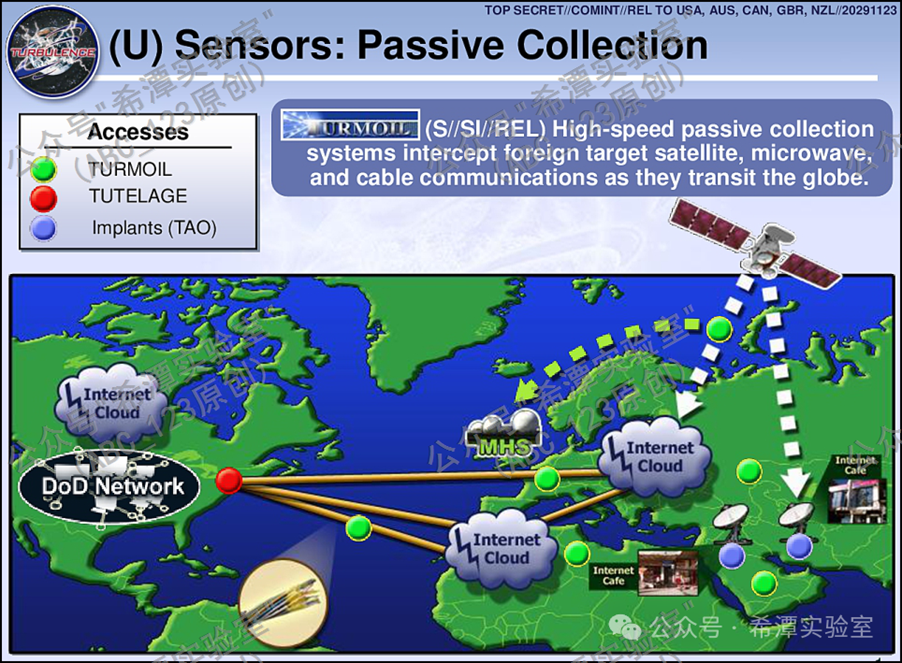
Green circles – Turmoil monitoring sites around the world;MHS-NSA's Menwith Hill base in the UK.
Presumably, the main link in the tracking system is one of the largest spy bases of the US NSA Menwith Hill in the UK, where hundreds of NSA analysts work side by side with employees of the UK Government Communications Center. The base is known for its full-fledged ground-based satellite stations and intelligence-gathering activities
Turmoil operators use special filters to select data streams that interest them, such as activity in Google, Yahoo, Facebook* and Skype services. TURMOIL only processes network data packets, not session information. The system filters out valuable network data packets and sends them to the XKEYSCORE tracking program for storage and further analysis.
If significant goals are detected, the system activates Turbine for further actions.
Turbine is an active intervention system designed to inject malware into target devices. The system is able to redirect traffic to the FoxAcid espionage platform within a second, using vulnerabilities to deliver implants to target computers.
System collaboration
The system operation process is illustrated by the example of a user trying to log in to Facebook. If Turmoil determines that a user is of interest, then Turbine redirects their request through a malicious server, which uses browser vulnerabilities to install malware on the user's device. In this way, the NSA is able to collect information from the infected device.
The study highlights that the Turmoil and Turbine systems are only part of the NSA's large and complex global monitoring mechanism. Further publications revealing other components of this system are expected. Information about the actions of the NSA raises concerns about the scale of surveillance on the Internet and calls into question the security of the global network.
During the leak of secret documents, the Chinese company Xitan Lab revealed details about the NSA's sophisticated global Internet traffic monitoring system, which can intercept user traffic around the world and inject malware using browser-level vulnerabilities. The system includes two key components: Turboil and Turbine.
Turmoil and Turbine: The Heart of Global Surveillance
Turmoil is a passive data acquisition system that operates through sensors distributed across key points in the global network. The system analyzes the traffic passing through it, extracting valuable information from it, including encrypted VPN and VoIP data. In addition to monitoring Internet traffic, Turmoil can also monitor satellite communications, microwave communications, underwater optical cables, and other traffic.

Green circles – Turmoil monitoring sites around the world;MHS-NSA's Menwith Hill base in the UK.
Presumably, the main link in the tracking system is one of the largest spy bases of the US NSA Menwith Hill in the UK, where hundreds of NSA analysts work side by side with employees of the UK Government Communications Center. The base is known for its full-fledged ground-based satellite stations and intelligence-gathering activities
Turmoil operators use special filters to select data streams that interest them, such as activity in Google, Yahoo, Facebook* and Skype services. TURMOIL only processes network data packets, not session information. The system filters out valuable network data packets and sends them to the XKEYSCORE tracking program for storage and further analysis.
If significant goals are detected, the system activates Turbine for further actions.
Turbine is an active intervention system designed to inject malware into target devices. The system is able to redirect traffic to the FoxAcid espionage platform within a second, using vulnerabilities to deliver implants to target computers.
System collaboration
The system operation process is illustrated by the example of a user trying to log in to Facebook. If Turmoil determines that a user is of interest, then Turbine redirects their request through a malicious server, which uses browser vulnerabilities to install malware on the user's device. In this way, the NSA is able to collect information from the infected device.
The study highlights that the Turmoil and Turbine systems are only part of the NSA's large and complex global monitoring mechanism. Further publications revealing other components of this system are expected. Information about the actions of the NSA raises concerns about the scale of surveillance on the Internet and calls into question the security of the global network.

