Father
Professional
- Messages
- 2,602
- Reaction score
- 837
- Points
- 113
How does the most confidential browser work, does it really guarantee users anonymity, and should it be banned for the sake of fighting cybercrime?
Contrary to popular belief, criminal activity accounts for an insignificant proportion of the Tor network. In 2020, researchers from the United States and the United Kingdom estimated that only about 6% of Tor users commit illegal actions. Later, Avast analyzers estimated the share of illegal resources in onion traffic at 1.5%.
The majority of users use Tor to protect themselves from unwanted ads, open blocked Internet resources, and hide the details of their online activity from prying eyes, starting with the Internet service provider.
The Tor developers themselves define their goals as follows:
The Tor network consists of three elements:
1. Nodes ensure anonymity of the connection. The first node through which traffic enters the Tor network is called the input node, the subsequent nodes are called transmitting or relay nodes, and the last node is called output node. By default, the browser uses only one relay node, but the user can increase this number if they are willing to sacrifice even more connection speed for privacy.
It is important to understand that technically, nodes do not differ from each other: the same node can occupy different places in the chain at different times.
2. Directory servers store the identity of nodes on the Tor network. Their IDs are embedded in the Tor code, so the browser always has up-to-date information about active nodes.
Directory servers monitor node activity and replace non-functioning nodes with healthy ones. When you start Tor, the Tor browser first connects to the directory servers, gets a list of active nodes, and creates a chain: one node for entering, one for exiting, and one for relaying.
3. Bridges are a special type of relay nodes. They are not listed on directory servers, and you need to configure them manually-specify the bridge address to the browser.
The provider can block the usual nodes specified in the directories, but the bridge IDs are unknown to it. This allows users to bypass regional Tor blockages. At the same time, they have to independently perform the function of directory servers and update the list of input nodes.
Source: GitHub.
In addition to academic papers, there are also confirmed attacks with real consequences for browser users. In 2014, the professional community actively discussed the role of one of the American institutions in the operations of the FBI. Law enforcement agencies neutralized more than 400 drug marketplaces, including the largest at that time Silk Road 2.0. Before that, agents managed to establish control over the provider Freedom Hosting, whose servers hosted sites with child pornography.
To a large extent, these attacks were made possible thanks to" traditional " information security tools: establish control over the server, inject malicious code into the page, and intercept credentials. However, there are also specific methods that can be used to deanonymize Tor users.
Here are some of them:
1. Analysis of network activity. This attack targets traffic between the Tor exit node and the target site. The last node in the chain is the easiest to track, it is he who accesses the online resource. By monitoring the exit node, you can get traffic data that can be compared with other available user information. For example, a combination of the OS version, installed layout, time zone, and screen resolution.
Some users make a mistake and log in via Tor to their personal accounts in social networks, but you can also deanonymize your identity in other ways. You can create a user profile based on open network data and compare it with data from Tor. However, all this requires additional measures, in addition to working with the output node.
2. Reconstruction of the node chain. In the Tor network, a chain of connections is created randomly each time. If it were possible to reconstruct it, it would not remain anonymous — the perfect secrecy of the transfer is at the very heart of this private technology.
To compromise the network, you need to set up a malicious node and start accepting Tor traffic. However, you will again get incomplete data, because the node "knows" only the user ID and the next recipient of the request. In theory, an attacker can run a large number of nodes to better control the route that the request will take. However, in reality, this is an extremely time-consuming task — even if a third-party compromises 30% of all nodes in the network, the probability that a user request will pass through them in each of the three steps is about 3%.
3. Chain formation. Another way is to change the Tor Browser settings so that it sends requests to the nodes that the attacker needs. according to some reports, a similar scheme was used by FBI agents in their operation against drug traffickers. At least shortly after the incident, Tor developers reported that some of the relays on the network were reconfigured to deanonymize users. They urged everyone to update their browser to exclude malicious nodes from the network.
The main limitation of this method is that the user must install a modified version of Tor or give an attacker access to their computer in order to change the browser settings.
As can be seen from these examples, the Tor network itself proves its resistance to attacks. Successful deanonymization of users becomes possible only through extensive training and the use of additional tools.
"We will never be able to permanently deanonymize all Tor users, but we will be able to deanonymize a very small part of them through manual analysis."
To do this, agents use the techniques discussed above: using Tor nodes, they track the movement of traffic to a specific user. In addition, the NSA uses cookies — although Tor Browser allows you to disable them, many users do not. The published documents say that the NSA actively promotes controlled sites in order to attract the right audience and get their cookies.
In addition, the NSA worked to degrade the user experience to discourage people from using the Tor browser. To do this, you can, for example, organize DDoS attacks on the onion network, which slow down the already slow connection. In early 2023, Executive Director of The Tor Project Isabela Dias Fernandes she told about a series of attacks that hit the network for seven months. She stressed that the organizers are persevering and are upgrading their methods as the Tor network improves.
Russian law enforcement agencies are also concerned about the hidden exchange of data on the Internet. In 2014, the Ministry of Internal Affairs of the Russian Federation announced a tender for the development of a solution that would allow "providing information about users (user equipment) of the anonymous TOR network". However, in 2015, the contract was terminated — the contractor, which became the Central Research Institute of Economics, Informatics and Control Systems (Central Research Institute of EISU) from the Rostec structure, did not provide the result in the required time. Some commentators noted that the contract could have been broken for a diversion, so as not to arouse suspicion of Tor users. However, in the future, several more lawsuits were filed against the Central Research Institute of EISU, and in 2022 the organization was declared bankrupt. This development supports the version about the professional failure of the Research Institute's specialists.
So, today Tor Browser remains the most effective tool for Internet users who are worried about their privacy. You can often hear suggestions to ban this program in the name of fighting cybercrime. For example, in 2013, the FSB proposed such a bill.
To such arguments, Tor developers respond that criminal groups have other means to hide their actions. Given how small a proportion of illegal activity is in the onion network traffic, the carpet ban will hit law-abiding people who run Tor for other purposes to a greater extent.
Contrary to popular belief, criminal activity accounts for an insignificant proportion of the Tor network. In 2020, researchers from the United States and the United Kingdom estimated that only about 6% of Tor users commit illegal actions. Later, Avast analyzers estimated the share of illegal resources in onion traffic at 1.5%.
The majority of users use Tor to protect themselves from unwanted ads, open blocked Internet resources, and hide the details of their online activity from prying eyes, starting with the Internet service provider.
The Tor developers themselves define their goals as follows:
- Block attempts by websites and online services to find out the user's location and other private data that can be used to find out their habits and interests. The browser allows you to configure the level of information disclosure for each connection separately.
- Hide from the Internet service provider and other network participants what information the user receives and where it comes from. In this way, you can bypass regional restrictions and open any site, unless its administrator himself blocked work with Tor.
- Implement a distributed Internet connection scheme, in which data passes through several constantly changing Tor relays. Each repeater is managed by independent network participants, which provides more security than the traditional approach (one provider) or using a proxy server with a single hop.
How the Tor network works
A user's request to Tor sequentially passes through several unrelated points (nodes or nodes, from the English node), which makes it very difficult to track it (but possible-we'll talk about this later). Many users and organizations have installed and configured these nodes, creating together a decentralized network for receiving and relaying requests in the forwarding chain. At the same time, of course, pages in Tor open much slower than in a regular browser, which accesses the address directly, without intermediaries.The Tor network consists of three elements:
1. Nodes ensure anonymity of the connection. The first node through which traffic enters the Tor network is called the input node, the subsequent nodes are called transmitting or relay nodes, and the last node is called output node. By default, the browser uses only one relay node, but the user can increase this number if they are willing to sacrifice even more connection speed for privacy.
It is important to understand that technically, nodes do not differ from each other: the same node can occupy different places in the chain at different times.
2. Directory servers store the identity of nodes on the Tor network. Their IDs are embedded in the Tor code, so the browser always has up-to-date information about active nodes.
Directory servers monitor node activity and replace non-functioning nodes with healthy ones. When you start Tor, the Tor browser first connects to the directory servers, gets a list of active nodes, and creates a chain: one node for entering, one for exiting, and one for relaying.
3. Bridges are a special type of relay nodes. They are not listed on directory servers, and you need to configure them manually-specify the bridge address to the browser.
The provider can block the usual nodes specified in the directories, but the bridge IDs are unknown to it. This allows users to bypass regional Tor blockages. At the same time, they have to independently perform the function of directory servers and update the list of input nodes.
Is it possible to hack a Tor connection
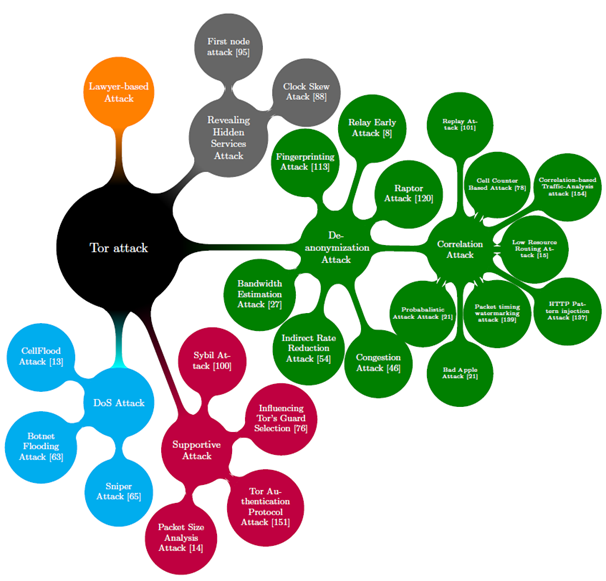
You can find a lot of research on the Internet that suggests different methods for deanonymizing Tor. As can be estimated from the "Map of Published Attacks", their description goes far beyond the scope of this article.
Source: GitHub.
In addition to academic papers, there are also confirmed attacks with real consequences for browser users. In 2014, the professional community actively discussed the role of one of the American institutions in the operations of the FBI. Law enforcement agencies neutralized more than 400 drug marketplaces, including the largest at that time Silk Road 2.0. Before that, agents managed to establish control over the provider Freedom Hosting, whose servers hosted sites with child pornography.
Sergey Polunin
Head of the Infrastructure IT Protection Group at Gazinformservis
First, the Tor has output nodes where you can track the user's IP address, which means that the owner of such a node can see the sites visited. Secondly, you can analyze traffic and try to find something interesting there. And third, law enforcement officers can use specially created Tor nodes that will look like absolutely legitimate, but will collect information about users and their activity.
All cases of catching someone in Top stories are very complex, and as a rule, users themselves leave enough information about themselves on other resources for deanonymization. There are quite a lot of cases in the United States-from a schoolboy from Florida who ordered a call from Darkweb about mining a school to the founder of the anonymous Silk Road marketplace. In each case, the FBI was able to catch them not only based on data from the anonymous network itself, but also because these people revealed a lot about themselves on completely open resources.
To a large extent, these attacks were made possible thanks to" traditional " information security tools: establish control over the server, inject malicious code into the page, and intercept credentials. However, there are also specific methods that can be used to deanonymize Tor users.
Here are some of them:
1. Analysis of network activity. This attack targets traffic between the Tor exit node and the target site. The last node in the chain is the easiest to track, it is he who accesses the online resource. By monitoring the exit node, you can get traffic data that can be compared with other available user information. For example, a combination of the OS version, installed layout, time zone, and screen resolution.
Some users make a mistake and log in via Tor to their personal accounts in social networks, but you can also deanonymize your identity in other ways. You can create a user profile based on open network data and compare it with data from Tor. However, all this requires additional measures, in addition to working with the output node.
2. Reconstruction of the node chain. In the Tor network, a chain of connections is created randomly each time. If it were possible to reconstruct it, it would not remain anonymous — the perfect secrecy of the transfer is at the very heart of this private technology.
To compromise the network, you need to set up a malicious node and start accepting Tor traffic. However, you will again get incomplete data, because the node "knows" only the user ID and the next recipient of the request. In theory, an attacker can run a large number of nodes to better control the route that the request will take. However, in reality, this is an extremely time-consuming task — even if a third-party compromises 30% of all nodes in the network, the probability that a user request will pass through them in each of the three steps is about 3%.
3. Chain formation. Another way is to change the Tor Browser settings so that it sends requests to the nodes that the attacker needs. according to some reports, a similar scheme was used by FBI agents in their operation against drug traffickers. At least shortly after the incident, Tor developers reported that some of the relays on the network were reconfigured to deanonymize users. They urged everyone to update their browser to exclude malicious nodes from the network.
The main limitation of this method is that the user must install a modified version of Tor or give an attacker access to their computer in order to change the browser settings.
As can be seen from these examples, the Tor network itself proves its resistance to attacks. Successful deanonymization of users becomes possible only through extensive training and the use of additional tools.
How intelligence agencies are trying to hack Tor
Among the documents of the US National Security Agency, which were published by Edward Snowden, there is a presentation called "Tor Stinks". In this article, NSA experts state:"We will never be able to permanently deanonymize all Tor users, but we will be able to deanonymize a very small part of them through manual analysis."
To do this, agents use the techniques discussed above: using Tor nodes, they track the movement of traffic to a specific user. In addition, the NSA uses cookies — although Tor Browser allows you to disable them, many users do not. The published documents say that the NSA actively promotes controlled sites in order to attract the right audience and get their cookies.
In addition, the NSA worked to degrade the user experience to discourage people from using the Tor browser. To do this, you can, for example, organize DDoS attacks on the onion network, which slow down the already slow connection. In early 2023, Executive Director of The Tor Project Isabela Dias Fernandes she told about a series of attacks that hit the network for seven months. She stressed that the organizers are persevering and are upgrading their methods as the Tor network improves.
Russian law enforcement agencies are also concerned about the hidden exchange of data on the Internet. In 2014, the Ministry of Internal Affairs of the Russian Federation announced a tender for the development of a solution that would allow "providing information about users (user equipment) of the anonymous TOR network". However, in 2015, the contract was terminated — the contractor, which became the Central Research Institute of Economics, Informatics and Control Systems (Central Research Institute of EISU) from the Rostec structure, did not provide the result in the required time. Some commentators noted that the contract could have been broken for a diversion, so as not to arouse suspicion of Tor users. However, in the future, several more lawsuits were filed against the Central Research Institute of EISU, and in 2022 the organization was declared bankrupt. This development supports the version about the professional failure of the Research Institute's specialists.
You can't prohibit it, or allow it?
Sergey Polunin
Head of the Infrastructure IT Protection Group at Gazinformservis
Indeed, access to a part of the Darknet is tightly bound by Tor and in general by this way of organizing traffic routing. But on the one hand, blocking Tor is not such a simple technical task, and on the other hand, Tor is a popular solution, but far from the only one. There are hundreds of other ways to share data, and cybercrime isn't going anywhere. And then, as practice shows, blocking itself will just encourage the creation of similar tools, only much more effective.
So, today Tor Browser remains the most effective tool for Internet users who are worried about their privacy. You can often hear suggestions to ban this program in the name of fighting cybercrime. For example, in 2013, the FSB proposed such a bill.
To such arguments, Tor developers respond that criminal groups have other means to hide their actions. Given how small a proportion of illegal activity is in the onion network traffic, the carpet ban will hit law-abiding people who run Tor for other purposes to a greater extent.

