Carding
Professional
- Messages
- 2,870
- Reaction score
- 2,494
- Points
- 113
In a new wave of attacks, hackers spread cryptographers through phishing emails with malicious XLL attachments.
The ransomware software "Cyclops" distributed under the RaaS model, which we wrote about in early June, has been rebranded. It is now called "Knight". Apparently, the hackers wanted to use this name to emphasize the exceptional quality and nobility of their product, but there are also questions about these parameters.
According to a previous report by Uptycs researchers, the original Cyclops campaign distributed cryptographic programs for Windows, macOS, and Linux / ESXi. Malware for stealing data from Windows and Linux was also available on the same platform, an approach that is very unusual for subscription-based ransomware.
In addition to the standard version of Cyclops, a lightweight version of the ransomware for mass spam mailings was also distributed. Unlike the main version, it used a fixed buyout amount instead of an individual one with the ability to negotiate.
At the end of July, the ransomware operation Cyclops officially changed its name to Knight, and its authors announced an update to the lightweight version for batch distribution. A new data leak site has also been launched.
One of the Sophos researchers has already discovered a new spam campaign that distributes Knight phishing emails under the guise of complaints from TripAdvisor users about specific establishments. In the case under review, there was a complaint about the hotel.
The spam email contains a ZIP archive with an HTML page disguised as a PDF document. It mimics the interface of the TripAdvisor website and suggests uploading a file to view the complaint.
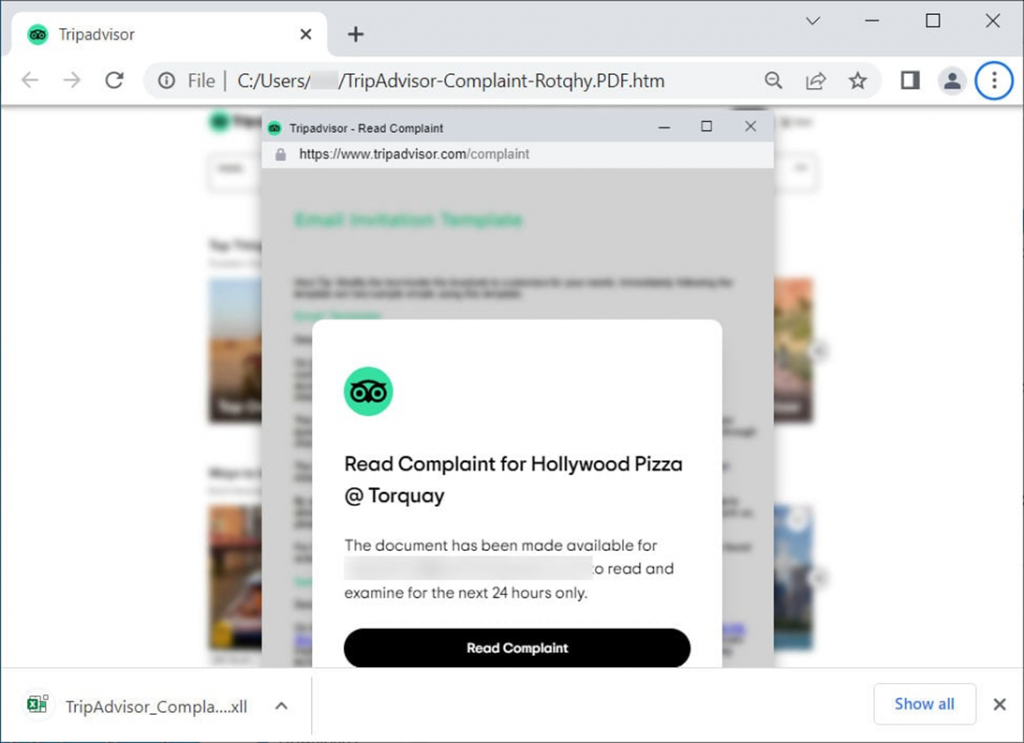
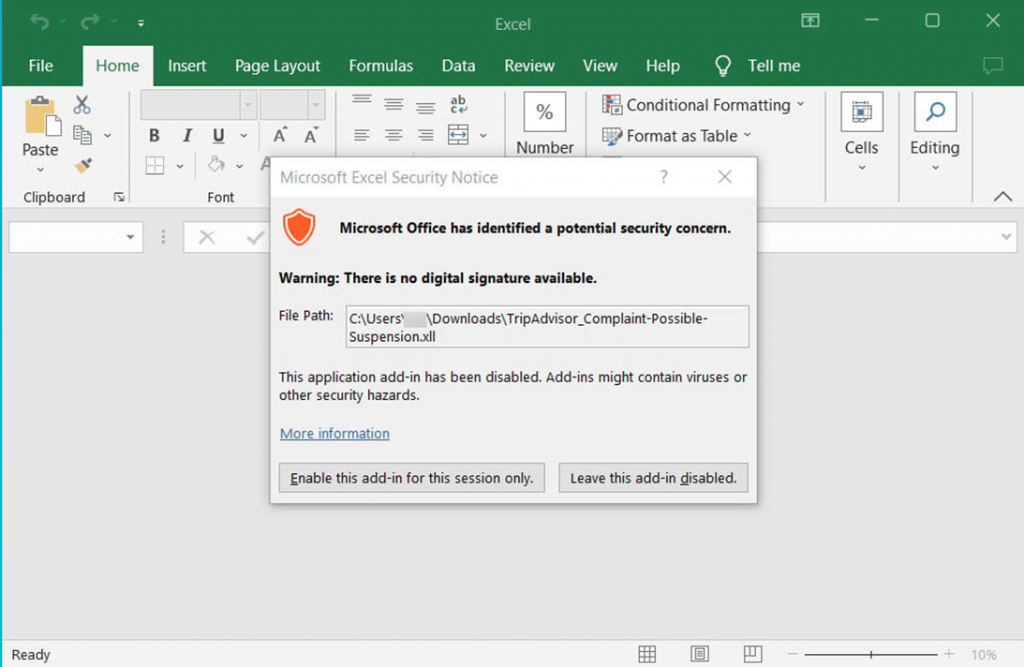
A click on the "Read complaint" link downloads a malicious XLL file, which is launched via Microsoft Excel along with the activation of the add-in.NET in the program activates the cryptographer.
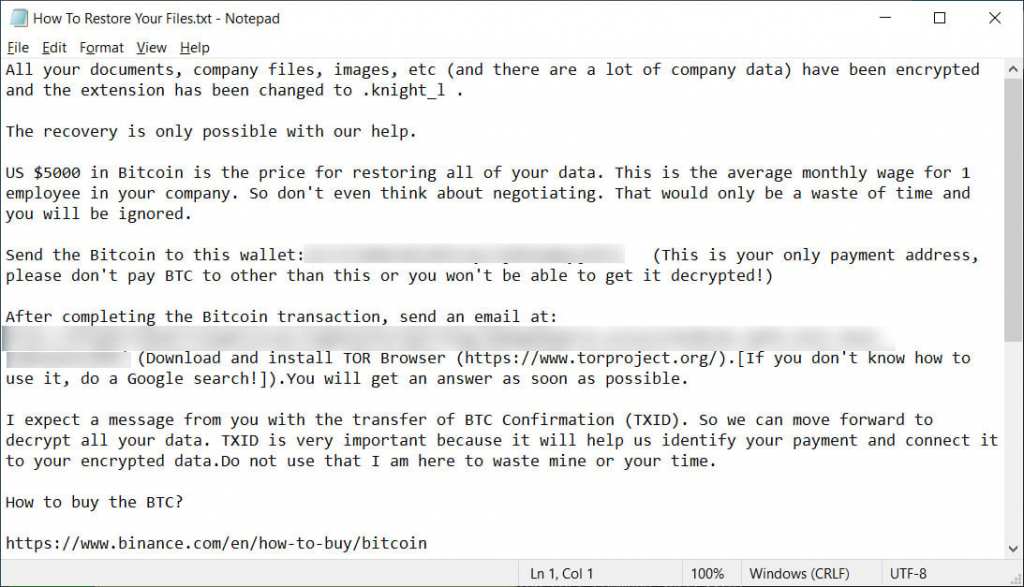
When all the data on the victim's computer is encrypted, the victim will see a ransom note in each folder of the computer. The note introduces the victim to the situation and offers to transfer $ 5,000 to the specified bitcoin wallet for unblocking data.
The double extortion strategy is not used in this operation, so you should not worry about publishing your data on cybercrime forums.
Experts strongly recommend that you refrain from paying a ransom in this particular campaign, even if extremely important data is encrypted for which no backups have been created. There is a high probability that the decryptor will not be provided by Knight partners.
Such conclusions were drawn by security experts due to hackers using the same cryptocurrency wallet for all their victims, although the ransom note states the opposite. Since the transactions are anonymous, the ransomware will not be able to understand which particular victim paid the ransom, and therefore the attackers will not be able to provide a decryptor.
Whether this is done intentionally or by mistake, this approach clearly does not give Knight ransomware a reputation.
To protect yourself from the attack of classic ransomware programs that encrypt your data without first uploading it to the server of intruders, you need to regularly make backups of critical files. So, even in the event of a successful attack, you will only lose time, but not your precious information.
(c) https://www.securitylab.ru/news/540926.php
The ransomware software "Cyclops" distributed under the RaaS model, which we wrote about in early June, has been rebranded. It is now called "Knight". Apparently, the hackers wanted to use this name to emphasize the exceptional quality and nobility of their product, but there are also questions about these parameters.
According to a previous report by Uptycs researchers, the original Cyclops campaign distributed cryptographic programs for Windows, macOS, and Linux / ESXi. Malware for stealing data from Windows and Linux was also available on the same platform, an approach that is very unusual for subscription-based ransomware.
In addition to the standard version of Cyclops, a lightweight version of the ransomware for mass spam mailings was also distributed. Unlike the main version, it used a fixed buyout amount instead of an individual one with the ability to negotiate.
At the end of July, the ransomware operation Cyclops officially changed its name to Knight, and its authors announced an update to the lightweight version for batch distribution. A new data leak site has also been launched.
One of the Sophos researchers has already discovered a new spam campaign that distributes Knight phishing emails under the guise of complaints from TripAdvisor users about specific establishments. In the case under review, there was a complaint about the hotel.
The spam email contains a ZIP archive with an HTML page disguised as a PDF document. It mimics the interface of the TripAdvisor website and suggests uploading a file to view the complaint.

A click on the "Read complaint" link downloads a malicious XLL file, which is launched via Microsoft Excel along with the activation of the add-in.NET in the program activates the cryptographer.

When all the data on the victim's computer is encrypted, the victim will see a ransom note in each folder of the computer. The note introduces the victim to the situation and offers to transfer $ 5,000 to the specified bitcoin wallet for unblocking data.

The double extortion strategy is not used in this operation, so you should not worry about publishing your data on cybercrime forums.
Experts strongly recommend that you refrain from paying a ransom in this particular campaign, even if extremely important data is encrypted for which no backups have been created. There is a high probability that the decryptor will not be provided by Knight partners.
Such conclusions were drawn by security experts due to hackers using the same cryptocurrency wallet for all their victims, although the ransom note states the opposite. Since the transactions are anonymous, the ransomware will not be able to understand which particular victim paid the ransom, and therefore the attackers will not be able to provide a decryptor.
Whether this is done intentionally or by mistake, this approach clearly does not give Knight ransomware a reputation.
To protect yourself from the attack of classic ransomware programs that encrypt your data without first uploading it to the server of intruders, you need to regularly make backups of critical files. So, even in the event of a successful attack, you will only lose time, but not your precious information.
(c) https://www.securitylab.ru/news/540926.php

