Brother
Professional
- Messages
- 2,590
- Reaction score
- 533
- Points
- 113
How hackers mask malicious activity in network traffic and target their victims.
Security researchers from Kroll have provided a detailed analysis of the C2 server operation of the well-known Sysembc malware. According to a report published last week, SystemBC has become much more actively used by attackers from the second to the third quarter of 2023.
This malware, first discovered back in 2018, allows dark hackers to remotely control an infected host and deliver additional malware, including Trojans, Cobalt Strike, and ransomware viruses.
A special feature of SystemBC is the use of a SOCKS5 proxy to mask network traffic, which provides constant hidden access to the system after hacking. The malware is distributed on cybercrime forums using a paid model.
SystemBC clients are provided with an installation package that includes an executable implant file, C2 server binaries for Windows and Linux, and a PHP file for displaying the C2 panel interface. The kit also includes instructions in several languages with detailed descriptions of the steps and commands to run.
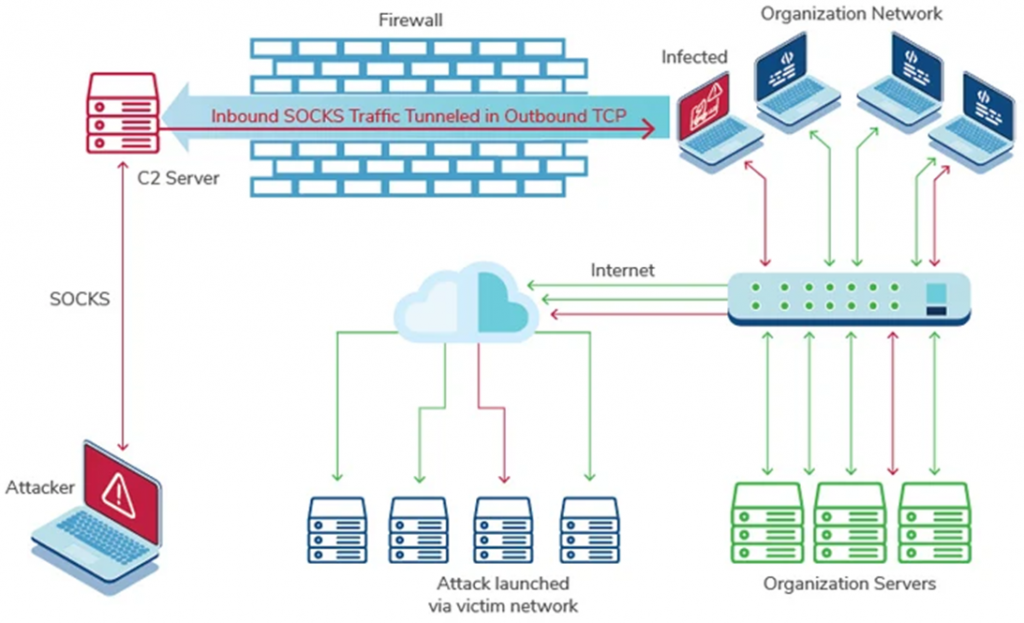
Attack pattern using SystemBC
C2 Server Executables "server.exe" for Windows and "server. out" for Linux-designed to open at least three TCP ports to simplify the flow of C2 traffic. The server component also uses three other files to record information about the interaction of the implant as a proxy server and loader, as well as details related to specific victims.
The C2 panel, written in PHP, is quite minimalistic and displays a list of active implants. It is also used to execute shellcode and arbitrary files on the infected machine. Kroll researchers noted that the shellcode functionality has full remote capabilities, not limited to reverse connection.
In addition, Kroll analyzed an updated version of DarkGate (5.2.3), a remote access Trojan that allows attackers to fully control victims systems, steal confidential data, and distribute more malware. Security researcher Sean Straw pointed out a weakness in the malware's custom Base64 alphabet, which makes it easier to decode the keylogger's configuration and output.
The results of both investigations highlight the importance of continuously monitoring and updating cybersecurity systems to protect against complex and ever-evolving threats.
Security researchers from Kroll have provided a detailed analysis of the C2 server operation of the well-known Sysembc malware. According to a report published last week, SystemBC has become much more actively used by attackers from the second to the third quarter of 2023.
This malware, first discovered back in 2018, allows dark hackers to remotely control an infected host and deliver additional malware, including Trojans, Cobalt Strike, and ransomware viruses.
A special feature of SystemBC is the use of a SOCKS5 proxy to mask network traffic, which provides constant hidden access to the system after hacking. The malware is distributed on cybercrime forums using a paid model.
SystemBC clients are provided with an installation package that includes an executable implant file, C2 server binaries for Windows and Linux, and a PHP file for displaying the C2 panel interface. The kit also includes instructions in several languages with detailed descriptions of the steps and commands to run.

Attack pattern using SystemBC
C2 Server Executables "server.exe" for Windows and "server. out" for Linux-designed to open at least three TCP ports to simplify the flow of C2 traffic. The server component also uses three other files to record information about the interaction of the implant as a proxy server and loader, as well as details related to specific victims.
The C2 panel, written in PHP, is quite minimalistic and displays a list of active implants. It is also used to execute shellcode and arbitrary files on the infected machine. Kroll researchers noted that the shellcode functionality has full remote capabilities, not limited to reverse connection.
In addition, Kroll analyzed an updated version of DarkGate (5.2.3), a remote access Trojan that allows attackers to fully control victims systems, steal confidential data, and distribute more malware. Security researcher Sean Straw pointed out a weakness in the malware's custom Base64 alphabet, which makes it easier to decode the keylogger's configuration and output.
The results of both investigations highlight the importance of continuously monitoring and updating cybersecurity systems to protect against complex and ever-evolving threats.

