Lord777
Professional
- Messages
- 2,577
- Reaction score
- 1,556
- Points
- 113
The updated data thief is even more invisible and dangerous.
The VMware Carbon Black team recorded a new wave of attacks on the Jupyter infostiler, which received an update and now uses PowerShell modifications, as well as falsifies digital signatures to disguise them as legitimate files.
Jupyter (Polazert, SolarMarker, Yellow Cockatoo), first documented in 2020 and written in .NET, is known for its methods of manipulating search engine optimization and malicious advertising, which are used to deceive users. Users trying to download popular programs end up on fake sites, which is where the infection occurs.
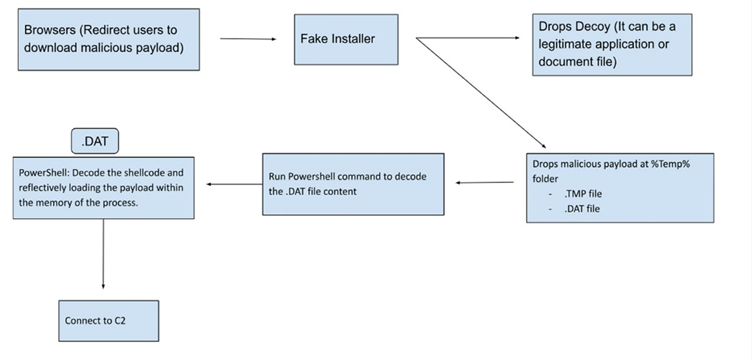
Jupyter Infostealer Infection Chain
The updated version of the software can not only collect credentials, but also establish an encrypted connection to the Command and Control server (C2) to steal data and execute arbitrary commands. The new changes include the use of different certificates to sign malware, which makes it look legitimate, while fake installers use PowerShell to start the infection chain.
The VMware Carbon Black team recorded a new wave of attacks on the Jupyter infostiler, which received an update and now uses PowerShell modifications, as well as falsifies digital signatures to disguise them as legitimate files.
Jupyter (Polazert, SolarMarker, Yellow Cockatoo), first documented in 2020 and written in .NET, is known for its methods of manipulating search engine optimization and malicious advertising, which are used to deceive users. Users trying to download popular programs end up on fake sites, which is where the infection occurs.

Jupyter Infostealer Infection Chain
The updated version of the software can not only collect credentials, but also establish an encrypted connection to the Command and Control server (C2) to steal data and execute arbitrary commands. The new changes include the use of different certificates to sign malware, which makes it look legitimate, while fake installers use PowerShell to start the infection chain.

