Teacher
Professional
- Messages
- 2,669
- Reaction score
- 819
- Points
- 113
The multi-stage execution technique allows you to bypass any protection.
Security researchers have discovered a new variant of the StopCrypt ransomware, also known as STOP. This version uses a multi-step execution process using shellcodes to bypass security tools, making the malware particularly dangerous due to the complexity of detection.
StopCrypt is the most widely distributed ransomware, but despite this, it is rarely mentioned by security researchers. Unlike other well-known operations, such as LockBit, BlackCat and Clop, STOP is not aimed at business structures, but at ordinary users, aiming to receive small buybacks in the amount of $ 400 to $ 1,000.
The spread of this virus is usually carried out through malicious advertising and dubious sites offering downloads of free software, cheats for games and "cracks", which leads to infection of users ' systems with various types of malware, including Trojans, infostilers and StopCrypt itself.
Since the first appearance of STOP in 2018, the virus cryptographer has not undergone significant changes, with the exception of the release of new versions to fix critical errors. Therefore, each new STOP option attracts attention because of the large number of people who may be affected by it.
The SonicWall identified a new STOP option that now uses a multi-step execution mechanism. It involves downloading an unrelated DLL file (msim32.dll), probably as a distraction, as well as implementing long time delay loops, which helps circumvent time-related security measures.
This is followed by a step using the "Process Hollowing" method, in which StopCrypt intercepts legitimate processes and enters its payload for hidden execution in memory. This is achieved through a series of precisely organized API calls that manipulate the process's memory and control the flow.
After the final payload is executed, a number of actions are performed to ensure that the ransomware is always running, including changing access control lists (ACLs) to prevent users from deleting important files and directories of the malware, and creating a scheduled task to execute the payload every five minutes.
As a result, the files are encrypted and the extension ".msjd" is added to their new names, and a text note is created in each affected folder with instructions on how to pay a ransom for data recovery.
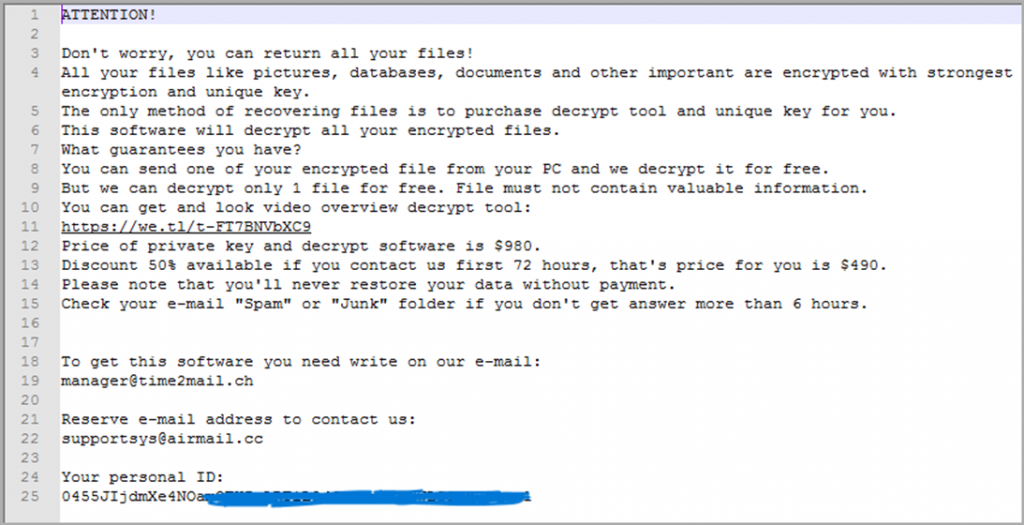
A ransom note "calming" victim
StopCrypt's evolution into a more stealthy and powerful threat underscores a worrying trend in cybercrime. Although the financial requirements of StopCrypt are not high and its operators are not engaged in stealing and publishing data in the public domain, the damage that this ransomware can cause to ordinary people can be very significant.
To avoid becoming a victim of StopCrypt ransomware or similar malware, it is important to be careful when downloading programs from untrusted sources, regularly update your software and antivirus programs, create data backups, and raise awareness of cyber threats.
Following basic cybersecurity measures will help prevent infection and minimize damage from this and other ransomware threats.
Security researchers have discovered a new variant of the StopCrypt ransomware, also known as STOP. This version uses a multi-step execution process using shellcodes to bypass security tools, making the malware particularly dangerous due to the complexity of detection.
StopCrypt is the most widely distributed ransomware, but despite this, it is rarely mentioned by security researchers. Unlike other well-known operations, such as LockBit, BlackCat and Clop, STOP is not aimed at business structures, but at ordinary users, aiming to receive small buybacks in the amount of $ 400 to $ 1,000.
The spread of this virus is usually carried out through malicious advertising and dubious sites offering downloads of free software, cheats for games and "cracks", which leads to infection of users ' systems with various types of malware, including Trojans, infostilers and StopCrypt itself.
Since the first appearance of STOP in 2018, the virus cryptographer has not undergone significant changes, with the exception of the release of new versions to fix critical errors. Therefore, each new STOP option attracts attention because of the large number of people who may be affected by it.
The SonicWall identified a new STOP option that now uses a multi-step execution mechanism. It involves downloading an unrelated DLL file (msim32.dll), probably as a distraction, as well as implementing long time delay loops, which helps circumvent time-related security measures.
This is followed by a step using the "Process Hollowing" method, in which StopCrypt intercepts legitimate processes and enters its payload for hidden execution in memory. This is achieved through a series of precisely organized API calls that manipulate the process's memory and control the flow.
After the final payload is executed, a number of actions are performed to ensure that the ransomware is always running, including changing access control lists (ACLs) to prevent users from deleting important files and directories of the malware, and creating a scheduled task to execute the payload every five minutes.
As a result, the files are encrypted and the extension ".msjd" is added to their new names, and a text note is created in each affected folder with instructions on how to pay a ransom for data recovery.

A ransom note "calming" victim
StopCrypt's evolution into a more stealthy and powerful threat underscores a worrying trend in cybercrime. Although the financial requirements of StopCrypt are not high and its operators are not engaged in stealing and publishing data in the public domain, the damage that this ransomware can cause to ordinary people can be very significant.
To avoid becoming a victim of StopCrypt ransomware or similar malware, it is important to be careful when downloading programs from untrusted sources, regularly update your software and antivirus programs, create data backups, and raise awareness of cyber threats.
Following basic cybersecurity measures will help prevent infection and minimize damage from this and other ransomware threats.

