Teacher
Professional
- Messages
- 2,669
- Reaction score
- 819
- Points
- 113
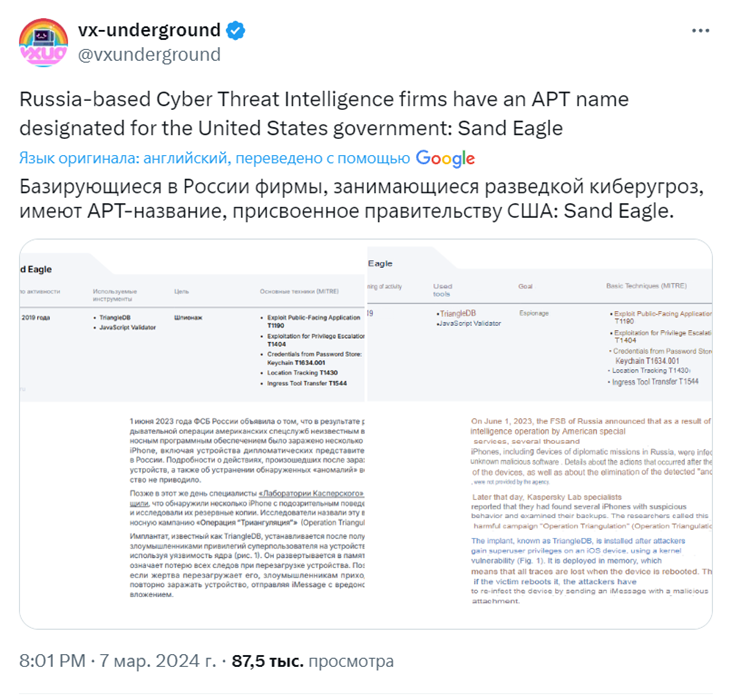
The vx-underground published a document in the social network X, in which Russian information security companies identified the group's activities, assigning it the code name Sand Eagle.
The document contains information about the group's actions attributed to American intelligence agencies, including attacks on countries hostile to the United States. The source of the document remains unknown.
Vx-underground tweetwith screenshots of the document
The document mentions that the FSB of Russia in June 2023 reported a spy attack by the US special services, which infected several thousand iPhones in Russia and abroad, including devices belonging to diplomatic missions.
In addition to attacks on targets in Russia, cases of infection of foreign devices using SIM cards registered to diplomatic missions and embassies in Russia, including the countries of the NATO bloc and the post-Soviet space, as well as Israel, the SAR and the PRC, were revealed.
Kaspersky Lab conducted its own investigation called "Operation Triangulation" and identified "several iPhones with suspicious behavior." During the work, it was found that the infection of devices occurs through a vulnerability in the iOS kernel, which allows the malicious program, called TriangleDB, to be installed in the device's memory. Traces of infection are erased after the device is rebooted, which forces users to re-expose their devices to risk by receiving iMessage messages with malware.
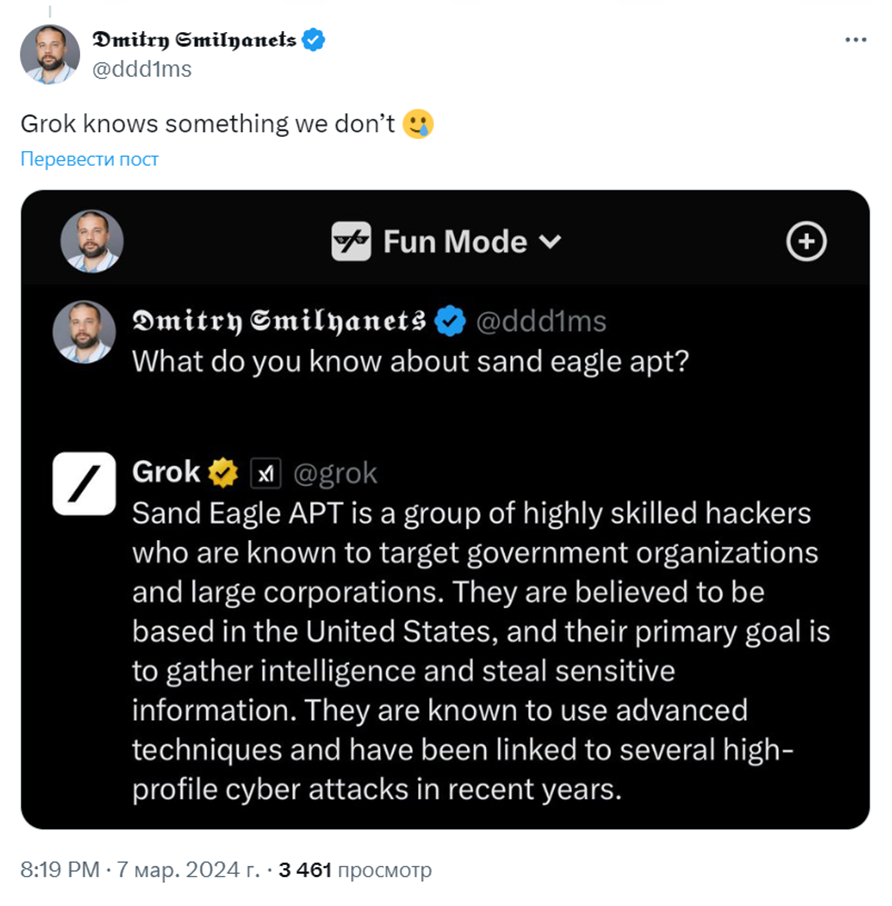
Dmitry Gmilnants, Director of Product Management at Recorded Future, also responded to the growing scandal by sharing a screenshot of the dialogue with the Grok chatbot. In response to a request about Sand Eagle, the chatbot identified them as an APT group from the United States that collects intelligence and steals confidential information, as well as is associated with a number of high-profile cyber attacks.
Gmilnan's dialogue with the chatbot
Gmilnants 'tweet highlights the mystery of the situation, especially considering that Internet searches for the name Sand Eagle only lead to images of birds and the novel "Eagle in the Sand".
Bill Marczak, a cyber threat researcher at CitizenLab, in response to a vx-underground post, said that the Chinese company Qihoo 360 mentioned the name Sand Eagle back in 2022 in its research, which has now been deleted. In its 2023 threat report, Qihoo 360 clarifies that Sand / Desert Eagle is actually a Middle East group not affiliated with Operation Triangulation.
Despite the lack of information about Sand Eagle in open sources, the situation raises many questions about the group's activity in cyberspace. Until now, the real confirmed origin of the group, its activities and the direction of attacks remain unknown.
The document contains information about the group's actions attributed to American intelligence agencies, including attacks on countries hostile to the United States. The source of the document remains unknown.

Vx-underground tweetwith screenshots of the document
The document mentions that the FSB of Russia in June 2023 reported a spy attack by the US special services, which infected several thousand iPhones in Russia and abroad, including devices belonging to diplomatic missions.
In addition to attacks on targets in Russia, cases of infection of foreign devices using SIM cards registered to diplomatic missions and embassies in Russia, including the countries of the NATO bloc and the post-Soviet space, as well as Israel, the SAR and the PRC, were revealed.
Kaspersky Lab conducted its own investigation called "Operation Triangulation" and identified "several iPhones with suspicious behavior." During the work, it was found that the infection of devices occurs through a vulnerability in the iOS kernel, which allows the malicious program, called TriangleDB, to be installed in the device's memory. Traces of infection are erased after the device is rebooted, which forces users to re-expose their devices to risk by receiving iMessage messages with malware.
Dmitry Gmilnants, Director of Product Management at Recorded Future, also responded to the growing scandal by sharing a screenshot of the dialogue with the Grok chatbot. In response to a request about Sand Eagle, the chatbot identified them as an APT group from the United States that collects intelligence and steals confidential information, as well as is associated with a number of high-profile cyber attacks.

Gmilnan's dialogue with the chatbot
Gmilnants 'tweet highlights the mystery of the situation, especially considering that Internet searches for the name Sand Eagle only lead to images of birds and the novel "Eagle in the Sand".
Bill Marczak, a cyber threat researcher at CitizenLab, in response to a vx-underground post, said that the Chinese company Qihoo 360 mentioned the name Sand Eagle back in 2022 in its research, which has now been deleted. In its 2023 threat report, Qihoo 360 clarifies that Sand / Desert Eagle is actually a Middle East group not affiliated with Operation Triangulation.
Despite the lack of information about Sand Eagle in open sources, the situation raises many questions about the group's activity in cyberspace. Until now, the real confirmed origin of the group, its activities and the direction of attacks remain unknown.

