Brother
Professional
- Messages
- 2,590
- Reaction score
- 533
- Points
- 113
The company is close to understanding all aspects of the attack, but one vulnerability raises many questions.
In early summer, Kaspersky Lab experts discovered a large-scale cyber operation aimed at infecting the iPhone of Russian users. This operation is called "Operation Triangulation". Russian officials blamed the American special services for organizing it.
Apple has declared its non-involvement in spyware attacks and released patches to fix vulnerabilities that were used for hacking.
Many Russian organizations have decided to stop using the iPhone. Meanwhile, Kaspersky Lab continued to investigate this operation.
On December 27, 2023, at the Chaos Communication Congress (37C3) in Hamburg, the company's experts presented the results of the "Operation Triangulation" study, which reveals a complex chain of attacks on Apple devices.
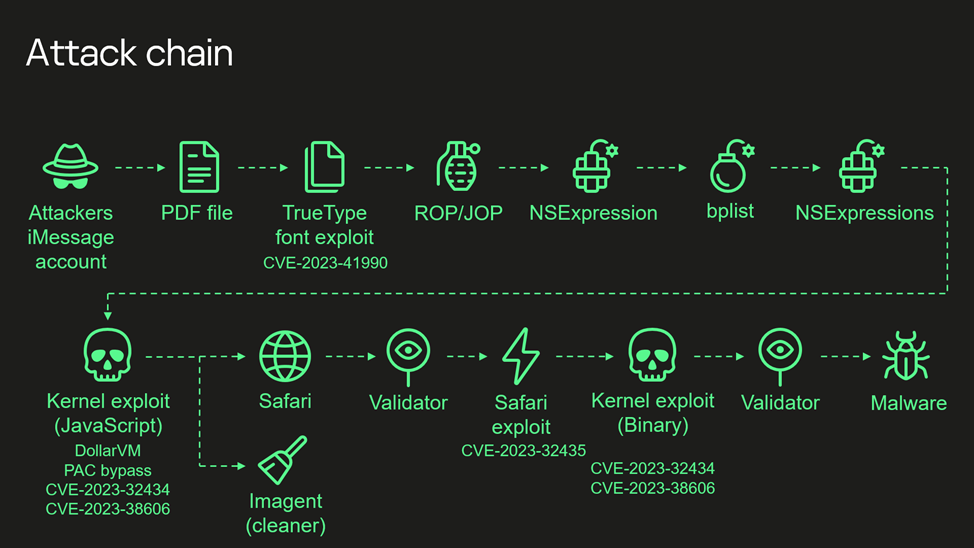
Operation Triangulation Attack Chain
An attack carried out through the iMessage app does not require active actions from the user. Its main feature is the use of four zero-day vulnerabilities in iOS up to version 16.2.
With its help, attackers can write the necessary data to the desired physical address, bypassing hardware memory protection. To do this, they need to write data, the destination address, and the hash of data to undocumented hardware registers of the chip that are not used by the firmware.
Experts suggest that this undocumented hardware feature was most likely intended for debugging or testing by Apple engineers or at the factory, or was enabled by mistake. Since this feature is not active in the firmware, experts have no idea how the attackers figured out how to use it.
In the technical part of the report, the researchers described in more detail the vulnerability CVE-2023-38606.
In early summer, Kaspersky Lab experts discovered a large-scale cyber operation aimed at infecting the iPhone of Russian users. This operation is called "Operation Triangulation". Russian officials blamed the American special services for organizing it.
Apple has declared its non-involvement in spyware attacks and released patches to fix vulnerabilities that were used for hacking.
Many Russian organizations have decided to stop using the iPhone. Meanwhile, Kaspersky Lab continued to investigate this operation.
On December 27, 2023, at the Chaos Communication Congress (37C3) in Hamburg, the company's experts presented the results of the "Operation Triangulation" study, which reveals a complex chain of attacks on Apple devices.

Operation Triangulation Attack Chain
An attack carried out through the iMessage app does not require active actions from the user. Its main feature is the use of four zero-day vulnerabilities in iOS up to version 16.2.
- Attackers sent a malicious attachment via iMessage, which is processed by the app without the user's knowledge.
- For remote code execution, the attachment exploits the vulnerability CVE-2023-41990 in an undocumented ADJUST instruction designed for TrueType fonts, which was present only on Apple devices. This instruction has existed since the early 90's and was removed in the latest patch.
- The attack used the technique of back-and transition-oriented programming. The penetration took place in several stages using the NSExpression/NSPredicate query language, and changes were made to the JavaScriptCore library environment that allowed a JavaScript exploit to be performed to increase privileges.
- The exploit is obfuscated to make it completely unreadable and minimize its size. However, it contains about 11,000 lines of code, mostly dedicated to manipulating JavaScriptCore and kernel memory.
- The exploit uses DollarVM ($vm), the JavaScriptCore debugging functionality, to manipulate JavaScriptCore memory from a script and execute native API functions.
- The exploit was designed to run on both older and newer iPhones and was designed to bypass the Pointer Authentication Code (PAC) to work on newer models.
- It exploited the vulnerability CVE-2023-32434, related to integer overflow in system calls for working with XNU kernel memory (mach_make_memory_entry and vm_map). It allowed read-write access to the entire physical memory of the device at the user level.
- Hardware I / O registers via Memory (MMIO) are used to bypass the Page Protection Layer (PPL). This issue was fixed in the CVE-2023-38606 patch.
- As a result of exploiting all the vulnerabilities, the JavaScript exploit gains full control over the device and can run spyware, but the attackers went the other way: a) started the IMAgent process and implemented a payload that erases traces of the attack from the device; b) started the Safari process in the background and redirected it to a web page to proceed to the next stage.
- The web page contains a script that verifies the victim, and if the verification is passed, it proceeds to the next stage — downloading the exploit for Safari.
- The Safari exploit exploits the vulnerability CVE-2023-32435, related to shellcode execution.
- The shellcode launches another kernel exploit in the form of a Mach object file. It exploits the same vulnerabilities CVE-2023-32434 and CVE-2023-38606. It is also impressive in its size and functionality, but it does not look at all like an exploit for the kernel written in JavaScript. Only some parts related to the exploitation of the aforementioned vulnerabilities coincide. However, most of its code is also designed to read and manipulate kernel memory. It contains various utilities for working with already compromised devices, which are mostly not used.
- The exploit gains root privileges and starts other steps that are responsible for downloading the spyware.
With its help, attackers can write the necessary data to the desired physical address, bypassing hardware memory protection. To do this, they need to write data, the destination address, and the hash of data to undocumented hardware registers of the chip that are not used by the firmware.
Experts suggest that this undocumented hardware feature was most likely intended for debugging or testing by Apple engineers or at the factory, or was enabled by mistake. Since this feature is not active in the firmware, experts have no idea how the attackers figured out how to use it.
In the technical part of the report, the researchers described in more detail the vulnerability CVE-2023-38606.

