Teacher
Professional
- Messages
- 2,669
- Reaction score
- 819
- Points
- 113
CONTENT
INTRODUCTION
The modern world can no longer be imagined without mobile communications. So, in the life of everyone who uses Internet services (RBS, payment systems, mobile banks, online stores, portals of government services), SMS with one-time codes to confirm various operations have become firmly established. The security of this authentication method is based only on restricting the access of attackers to telecommunication networks.
We must not forget about the rapidly developing Internet of Things, which is spreading everywhere, penetrating both the management of industrial processes and the infrastructure of cities. Disruptions in the operation of the mobile network can completely paralyze these systems, leading both to isolated cases of stopping smart home devices or a car, causing dissatisfaction with the operator's customers, and to more dangerous consequences, for example, traffic collapses or power outages.
This report presents the results of a study of the security of SS7 networks. The Signaling System 7 standard is used to exchange service information between network devices in telecommunication networks. At the time this standard was being developed, only fixed line operators had access to the SS7 network, so security was not a priority. Today, the signaling network is no longer isolated to the same extent, so an attacker who has gained access to it in one way or another has the ability to exploit security flaws in order to listen to subscribers' voice calls, read SMS, steal money from accounts, bypass billing systems, or affect the functioning of the mobile network.
Despite the emergence of new generation 4G networks using a different signaling system - Diameter, SS7 security problems will remain relevant for a long time, since telecom operators still have to provide support for 2G / 3G standards and interoperability between networks of different generations. Moreover, research proves that the Diameter protocol is subject to the same threats as SS7. The vulnerabilities of this protocol, as well as a description of possible cross-protocol attacks, during which the shortcomings of both Diameter and SS7 are exploited, will be published in one of the next analytical reports.
We decided to show not only the vulnerabilities that we identify in the course of analyzing the security of SS7 networks, but also the facts of the actual exploitation of these vulnerabilities in order to demonstrate the scale of the security problems of modern communication networks. We tracked how the security situation of SS7 networks has changed over the past three years; learned what protection means are used by telecom operators and how effective the existing solutions are in real conditions.
TERMS AND DESIGNATIONS
HLR (Home Location Register) is a database that contains information about the subscriber.
MSC (Mobile Switching Center) is a mobile telephone switch.
SS7 (Signaling System 7) is a common channel signaling system used in international and local telephone networks.
STP (Signaling Transfer Point) is an edge node for routing signaling messages.
VLR (Visitor Location Register) - a database that contains information about the location and movement of the subscriber.
SUMMARY
The security of SS7 networks is still low. All studied networks contain dangerous vulnerabilities that can disrupt the availability of services for subscribers. Almost every network can listen to a subscriber's conversation or read incoming SMS, and fraudulent operations can be successfully carried out in 78% of networks.
Attackers are aware of vulnerabilities and exploit them. The PT Telecom Attack Discovery system for detecting and preventing attacks detects real attacks that cybercriminals carry out on the networks of telecom operators. Mostly they are aimed at collecting information about subscribers and network configuration. However, we also observe such attacks, which, in all likelihood, are carried out with the aim of fraud, interception of subscriber traffic and disruption of availability.
Operators are aware of the risks involved. Measures are being taken to reduce the likelihood of threats being realized. To date, it has been possible to reduce the risk of information leakage about the network and subscribers. In 2017, the SMS Home Routing system was functioning in all the networks studied, and a filtering and blocking system for signaling traffic was installed in every third network.
The solutions used are not effective enough. Despite the active introduction of additional protection systems, all networks were exposed to vulnerabilities associated with both special cases of incorrect hardware configuration, and with architectural problems of SS7 signaling networks, which cannot be eliminated with the available means. Only a comprehensive approach to solving security problems, including regular security analysis, keeping network parameters up-to-date, constant monitoring of signaling traffic and timely detection of illegitimate activity, can provide a high level of protection from criminals.
VULNERABILITIES OF SS7 NETWORKS
Research methodology
Every year Positive Technologies experts carry out dozens of works to analyze the security of SS7 signaling networks. The checks simulate the actions of a potential intruder who is supposed to carry out attacks from an international or national network external to the operator. An attacker has the ability to send requests for application-level protocols to the tested network, which can lead to the implementation of various threats both in relation to the operator itself and its subscribers, if the operator does not take sufficient protection measures. To emulate a malicious node, special equipment is used - PT Telecom Vulnerability Scanner.
For the study, we selected 24 of the most informative projects for analyzing the security of SS7 networks in 2016–2017, during which the most complete list of checks was carried out. As part of our benchmarking analysis, we also used the data provided in our 2015 research report.
Portrait of the participants
In 2020–2021, operators from Europe (including Russia) and the Middle East took part in the study.
Half of the participants were telecom operators with a subscriber base of more than 40 million people. Smaller companies, with less than 10 million subscribers, were predominantly virtual mobile operators based on larger telecoms.
Statistics on the main types of threats
We highlight the following threats that an attacker can implement by exploiting the security flaws of mobile operators' networks:
Disclosure of information about a subscriber refers to the leakage of IMSI identifiers, disclosure of the location of the subscriber, as well as other information, such as current balance or profile details. Disclosure of information about the operator's network is fraught with leakage of information about the configuration of the SS7 network.
At the moment, there are known such techniques for intercepting subscriber traffic in SS7 networks, which allow you to listen or redirect incoming and outgoing voice calls to third-party numbers, as well as intercept users' SMS.
Fraudulent attacks can be carried out against both the operator and subscribers. For example, changing the billing category for roaming calls or bypassing the billing system can harm the telecom operator, and transferring funds from the account, redirecting calls to paid numbers, or subscribing to paid services - to network users.
In this study, we only consider denial of service for individual subscribers, since only a small number of operators perform testing of network elements in the framework of security audits, which can be fraught with disruptions in the operation of the mobile network. It should be taken into account that the disruption of functioning can be massive if the attackers have a subscriber base of the operator or have sufficient resources to select subscriber identifiers.
As operators' awareness of the security issues of SS7 networks is gradually increasing, operators are beginning to implement security measures against attacks. If in 2015 each studied network was exposed to all types of threats, then over the past two years there have been positive changes in the overall level of network security.
The risks of information leakage about the operator's network, fraud and interception of subscriber traffic have significantly decreased. Nevertheless, each network examined, as before, is subject to vulnerabilities that allow obtaining information about subscribers or causing a denial of service.
Consider the proportion of successful attack attempts that the experts were able to implement as part of their work on security analysis.
As you can see, first of all, operators are taking measures aimed at reducing the risk of disclosing information about the network and subscribers, since this information serves as the initial data for the implementation of many other attacks. Compared to 2015, the share of successful attacks aimed at disclosing information about the operator's network decreased by almost three times, and it was twice less likely to obtain data on network subscribers. Methods of protection against such attacks are quite simple, and there are ready-made solutions on the information security market, but 100% of networks are still vulnerable to disclosure of information about subscribers, which indicates the insufficient effectiveness of existing solutions.
For other types of threats, the percentage of successful attacks changed insignificantly. As we will show later, the reason is that the implementation of traffic filtering and blocking systems cannot compensate for the architectural problems of SS7; a different approach is required to minimize these risks.
The following reasons can be identified for which the implementation of certain threats is possible:
In particular, attacks are possible aimed at disclosing the location of the subscriber, redirecting or intercepting a call, intercepting SMS, changing the payment category or profile of the subscriber. Lack of location check refers to signaling messages arriving in the subscriber's home network from the network in the coverage area of which the subscriber is in roaming. If the signal message is composed correctly, there is no way to check its authenticity only by the received parameters. An additional check is needed to see if the subscriber is actually in the network from which the signaling traffic came.
The difficulty of verifying the belonging of a network subscriber is associated with signaling messages sent by the telecom operator to its subscribers who are in roaming to another network in which these subscribers are currently registered. To determine illegitimate traffic, you need to check the correspondence between the message source and the subscriber identifier. If the source address and subscriber ID correspond to the same operator, then the message is legitimate. But if a match is not found, this does not mean falsification of the message, since the source address can be changed, for example, by the transit operator. We can confidently talk about the illegitimacy of this type of signaling traffic if it comes from external networks and is directed to the subscribers of the home network.
SMS Home Routing is a hardware and software complex designed to hide real subscriber identifiers and addresses of network equipment. It is used in 85% of the studied networks; however, incorrect configuration allows attacks to bypass the protection mechanism. In networks where the SMS Home Routing system was absent, absolutely all attempts to obtain subscriber IDs and information about the network were successful.
Operators are actively introducing filtering and blocking systems for signaling traffic: in 2017, they were already functioning in a third of the networks studied. As a result, attacks that exploit vulnerabilities associated with the lack of message filtering are currently successful only in 10% of cases, which is three times better than in previous years.
To carry out attacks, standard messages are used to perform service operations. These messages must be checked at the border or within the operator's network to prevent illegitimate requests. One and the same attack can be carried out by several messages (methods), while the success of different methods is not the same. Next, we will analyze in detail what methods and with what degree of probability attackers can implement all of the listed threats.
Leaked subscriber information
As mentioned above, the primary measure to reduce the likelihood of most attacks is to reduce the risk of disclosing IMSI - unique identifiers of subscribers. Compared to 2015, it was possible to find out IMSI by the subscriber's phone number in the past year about 4 times less often.
Today it is possible to determine the location of a subscriber in 75% of networks, while the share of successful attacks using various methods is 33%, which is also much better than previous indicators.
7. The proportion of successful attacks by types of threats associated with obtaining information about a subscriber
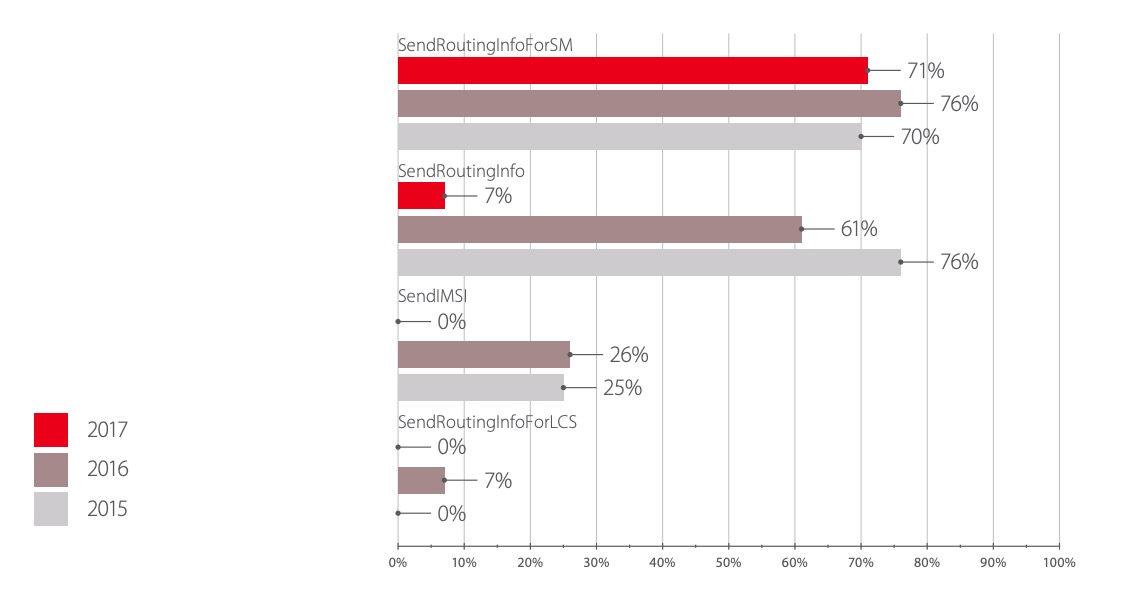
Disclosure of information about a subscriber can be implemented by four methods, the success of which is shown in Fig. eight.
Methods used to obtain the subscriber's IMSI (percentage of successful attacks)
The decrease in the share of successful attacks using the SendRoutingInfo and SendIMSI methods is due to the introduction of filtering tools in operators' networks. The SendRoutingInfo message is used to receive routing information about the subscriber for an incoming voice call and should only be sent within the operator's home network. The SendIMSI message for requesting the IMSI of a subscriber by his phone number is currently practically not used by operators, but is processed in mobile networks in order to fully ensure compliance with standards.
The SendRoutingInfoForLCS method was successfully used only in two studied networks, which is also associated with effective message filtering. The method is used to request information by services that require data about the user's location.
The SendRoutingInfoForSM message is sent to obtain the routing information required to deliver the incoming SMS. In order not to reveal the real subscriber IDs and addresses of network elements, the message received from the external network should be forwarded to the SMS Home Routing system and return virtual data. Despite the fact that most networks use SMS Home Routing, we often encounter incorrect configuration of the edge network equipment (STP / FW), as a result of which a request is sent to the HLR bypassing the SMS Router device and returns the real IMSI of the subscriber and data about the network configuration operator.
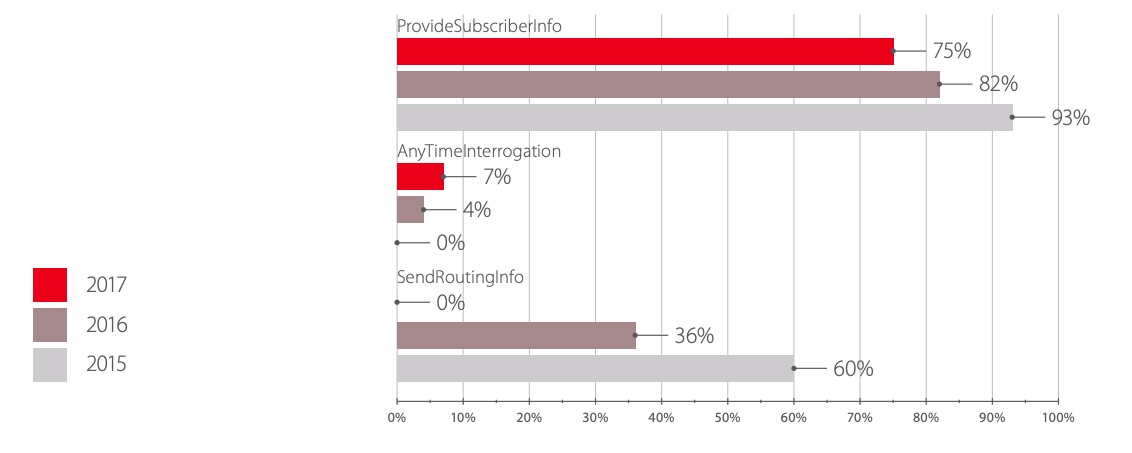
It was mainly possible to determine the location of the subscriber using the ProvideSubscriberInfo method. This is due to the architectural flaws of SS7 networks. The ProvideSubscriberInfo message shall only be processed if the source of the message and the subscriber ID match the same operator. The problem is that due to the architectural features of SS7 networks, it is impossible to determine the subscriber's ownership of the operator's network. To protect against such attacks, it is necessary to use traffic filtering systems.
In 2015, we assumed that carriers were well aware of the AnyTimeInterrogation attacks, which reveal the user's location by their phone number, and the corresponding protection methods - since none of our attempts were successful. However, over the next two years, we encountered networks that lacked filtering for this message.
Methods used to determine the location of the subscriber (percentage of successful attacks)
Disclosing the balance or details of a user profile does not pose an immediate serious risk, so protection against these threats appears to be a lower priority. In addition, protection against most of the methods used is possible only with constant monitoring and filtering of signaling traffic. It is possible to implement the corresponding attacks on each investigated network; for this, the following messages are used:
Leaked operator information
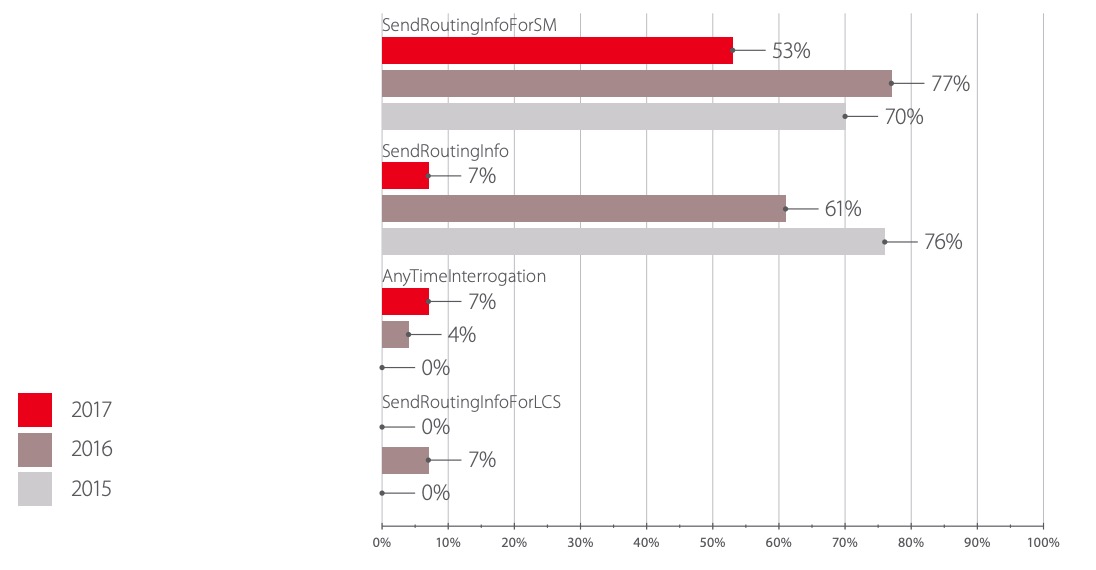
In the course of the checks, more than half of the attacks related to SMS Home Routing configuration problems, which allow obtaining network configuration data, were carried out. Overall, however, operators have achieved a significant reduction in the likelihood of such disclosures.
Methods used to obtain information about the configuration of the SS7 network (percentage of successful attacks)
The increase in the number of successful attacks using the SendRoutingInfoForSM method in 2016 was caused by the fact that we investigated several networks in which SMS Home Routing was absent.
Interception of subscriber traffic
It was possible to listen to or redirect incoming and outgoing calls of subscribers to third-party numbers in more than half of the cases.
Call forwarding is only meant to transfer a call to a third-party number. The evolution of this attack allows the connection to be established in such a way that an attacker can listen in on the subscriber's conversation.
The UpdateLocation message is used to notify the HLR that the subscriber has changed the serving switch. By sending a fake request to register a subscriber in the attacker's network, incoming SMS or calls are intercepted. When an incoming call arrives, the operator's network sends a request to the fake network to obtain the subscriber's roaming number. An attacker can reply with his own PBX number, and in this case, incoming traffic will go to his equipment. Then, after sending a repeated request to register a subscriber in the real network, the attacker can redirect the call to the subscriber's number. As a result, the conversation will pass through the equipment controlled by the attacker. The same principle is at the heart of intercepting incoming calls with the RegisterSS method,
The high percentage of successful attacks is due to the lack of verification of the real location of the subscriber. To reduce the likelihood of attacks using these methods, it is necessary to ensure constant monitoring of signaling traffic and analysis of illegitimate activity to identify suspicious nodes, build lists of prohibited and trusted networks, and immediately block requests from prohibited sources.
Outgoing calls are listened to according to a similar scheme: a specially formed InsertSubscriberData message replaces the platform address for call charging in the subscriber's profile stored in the VLR database. When a request arrives at a new address, the attacker first redirects the outgoing call to the equipment under his control and only then to the called subscriber.
Thus, the attacker is able to listen to any conversation of the subscriber.
Fraud
A wide range of methods are known that can be used by criminals in order to obtain financial gain at the expense of the operator or network subscribers. These methods can be divided into four categories:
Illegal call forwarding of incoming or outgoing calls
Call forwarding also allows for other fraudulent schemes. So, for example, if a subscriber makes an outgoing call to the bank, then by redirecting him to his own number and introducing himself as a bank employee, the offender can find out confidential information necessary to confirm his identity, in particular, passport data and a code word. The opposite situation is also possible: by forwarding incoming calls, an attacker can impersonate a subscriber, for example, to confirm banking transactions.
Calls are redirected using the previously mentioned UpdateLocation, RegisterSS, InsertSubscriberData methods, as well as the AnyTimeModification method, with which you can make changes to the subscriber profile (note that none of the attacks by the AnyTimeModification method led to the desired result).
Operation of USSD requests
An attacker can transfer money from the account of a subscriber or operator's partners by exploiting the ability to send fake USSD requests using the ProcessUnstructuredSSRequest method. Another method - UnstructedSSNotify - is used to send notifications to subscribers on behalf of various services, including from the operator itself. An attacker can send a fake notification on behalf of a trusted service containing instructions that the subscriber must follow: send an SMS to a paid number to activate the service, call a fake bank number in connection with suspicious card transactions, or follow the link to update the application.
SMS manipulation
Change subscriber profile
Information about the billing platform and service subscriptions is stored in the subscriber's profile. To bypass the billing system in real time, it is necessary to delete the subscriber's O-CSI subscription, which is used to make outgoing calls by the subscriber, or change the billing platform address to a fictitious one. In order to prevent non-chargeable calls, the O-CSI parameters indicate that if the platform is unavailable, the call must be terminated. However, you can override this parameter so that the call continues without contacting the platform. As a result, the legitimate platform will not receive information about calls and, accordingly, will not perform tariffication.
Attacks using the InsertSubscriberData and DeleteSubscriberData methods were successfully carried out in more than 80% of cases, and attempts to attack using the AnyTimeModification method were unsuccessful.
Denial of service
All attack attempts resulted in denial of service to subscribers, with the exception of the InsertSubscriberData method (83% of successful attacks). The AnyTimeModification method can be used for the same purpose, however, the security parameters of all the studied networks prevented the passage of these requests.
In addition to the ability to make voice calls and exchange SMS, the subscriber may lose access to the Internet when carrying out an attack using the InsertSubscriberData method.
Despite the fact that the considered violations of the network functioning are purposeful and affect only one subscriber in each case, a massive failure in service is not excluded if the attacker has a base of subscriber identifiers or can brute force the identifiers.
These service disruptions can be critical for IoT devices. This is a rapidly growing market of billions of devices that require access to telecommunications networks to operate. Periodic failure of smart home systems, video surveillance systems, devices that track the location of a car, or the stoppage of industrial processes of an enterprise can lead to a significant churn of customers.
When deleting the VLR address from the HLR, in which the subscriber is currently registered, through the PurgeMS procedure initiated by a certain third node, the following occurs. Incoming calls cannot be routed to the serving VLR / MSC because there is no registration address in the HLR. In this case, outgoing calls to the subscriber are available, since the registration record in the VLR has not changed.
Restoring the registration to the HLR in the usual way - by rebooting the phone (or other device) - does not work, since the VLR does not initiate the UpdateLocation procedure in relation to the HLR, assuming that there are no changes in the subscriber's registration data.
As a result, it is possible to restore the registration, and, accordingly, the subscriber's availability for incoming calls, only when registering in the coverage area of another serving MSC, for example, if you first manually select the network of another operator, and then select the home network again. Another option is to relocate to another MSC in your home network.
Protective measures and their effectiveness
The identified vulnerabilities are associated with both incorrect configuration of network equipment or security tools, and with fundamental shortcomings of SS7 networks. If in the first case it is enough to make changes to the device configuration to eliminate vulnerabilities, then the architectural problems of networks can be solved only by correct filtering and monitoring of signaling traffic. To ensure the analysis and blocking of incoming messages without disrupting the functioning of the network, special additional equipment is required. Let's consider what protection tools were used in the networks under study and to what extent they help to reduce the risks of threats.
The SMS Home Routing complex was installed in almost all networks. Since 2016, operators have begun to implement filtering and blocking systems for signaling traffic, and in 2017 such systems were already functioning in every third network surveyed.
The SMS Home Routing system is aimed at counteracting the disclosure of the subscriber's IMSI and network configuration using the SendRoutingInfoForSM method, and indeed, the percentage of successful attacks if it is installed is reduced by a third. However, due to incorrect configuration of the equipment, in 67% of cases, real data can be obtained.
It should be remembered that SMS Home Routing cannot be used to protect against other types of attacks. Moreover, this system is not designed to protect the network, but is installed to properly route incoming SMS. Studies show that networks using SMS Home Routing are not more secure than others, possibly because carriers often rely solely on SMS Home Routing, neglecting additional security measures.
Let us compare the results of attempts to carry out attacks by various methods, to counter which it is currently recommended to use filtering and blocking systems for signaling traffic.
At the same time, it is obvious that even the use of a filtering system is not able to ensure absolute network security. Let's figure out why this is happening.
All messages described in this report fall into three categories as defined in GSMA IR.82:
Traffic filtering systems provide complete protection against attacks involving messages of the first category, and in the case of messages of the second category, the proportion of successful attacks is halved.
The situation is different with the third category. Unjustified blocking of such messages can affect the service of a subscriber who is actually in roaming. For example, an erroneous blocking of a legitimate registration of a subscriber in an external network can lead to the fact that the subscriber will be left without communication in roaming, and for the operator this means a clear shortfall in profit and a possible loss of the client. Identifying illegitimate requests is a complex technical challenge. It is recommended to filter messages based on the lists of trusted and prohibited sources provided by roaming partners; however, the volume of such lists and the need for their constant updating significantly complicate the implementation of the solution in practice. For fear of disrupting the functioning of the network, operators are very cautious about blocking such messages.
To achieve a high level of protection against all types of threats under consideration, an integrated approach to information security is required. First of all, it is important to conduct a regular analysis of the security of the signaling network, as this allows you to identify actual vulnerabilities that may arise when changing the network configuration and parameters of network equipment, and to assess the risks associated with information security.
In addition, it is required to ensure constant monitoring and analysis of messages crossing the network boundaries in order to keep the security parameters up to date, timely identify potential threats and respond to them. Instructions for using monitoring systems to counter attacks are also contained in the GSMA 1... This task should be performed using dedicated threat detection systems that can intelligently analyze messages in real time. This solution allows detecting illegal activity of external nodes at an early stage and transmitting information about them to the signaling traffic filtering system to increase its efficiency, for example, to update the lists of prohibited nodes, and also allows detecting configuration errors in network devices and notifying the operator's employees about the need to fix them.
Security is a process, so you cannot limit yourself to one-off measures (audits or implementation of safeguards). An integrated approach is used by Positive Technologies specialists to protect the signaling networks of their clients, you can find out more on the website by asking a question through the feedback form or by writing to us at info@ptsecurity.com
In the next section, we will explore whether existing defenses can be used against intruders in a real-world environment, and how using threat detection and prevention can help protect your network.
ATTACKS ON THE SS7 NETWORK
We examined the vulnerabilities that SS7 networks are exposed to and the possible threats associated with their exploitation. The question remains: how do the results of security research correlate with real life, qualifications and capabilities of real criminals? In this section, we will present the results of security monitoring projects in SS7 networks and see what attacks mobile operators actually face and whether the existing protection measures are effective in practice.
Methodology
Security monitoring projects in SS7 networks were carried out for large telecom operators in Europe and the Middle East. The purpose of these works was to demonstrate the capabilities of the PT Telecom Attack Discovery (PT TAD) system, which is designed to analyze signaling traffic in real time and detect illegal activity with the ability to block unauthorized messages or alert third-party filtering and traffic blocking tools. This approach allows you to timely identify potential threats and respond to them without adversely affecting the functioning of the network.
PT TAD can also be used as a passive system for detecting illegitimate activity, in this case the system allows analyzing the passing traffic, but does not affect it. Our research presents the results of traffic monitoring in passive mode.
Statistics on detected attacks
All networks where security events were monitored used SMS Home Routing equipment, and one or another system for filtering and blocking signaling traffic was installed in every third network.
During the monitoring, we obtained results indicating that attackers are not only well aware of the security problems of signaling networks, but also actively exploit these vulnerabilities.
The table for each threat shows the vertical distribution of all attack attempts by the methods used. The proportions of successful attacks are listed for each threat and separately for each method. An empty cell means that the message does not lead to the implementation of this threat.
For example, an attempt to get the IMSI of a subscriber in 79.9% of cases is carried out by violators using the SendRoutingInfo method. In general, the violator succeeds in obtaining IMSI by one method or another in 34.5% of cases. And the SendRoutingInfo method itself is successful in 22.6% of attack attempts.
As we found out, the source of most attacks are not the national operators of the country in which the security monitoring was carried out, but the international telecom operators. Suspicious inquiries come mainly from countries in Asia and Africa; This is probably due to the fact that in these countries it is easier for an attacker to buy access to the SS7 network. At the same time, physical access to the equipment of the operator who provided the ability to connect to the SS7 network is not required, the attacker can be anywhere in the world.
To demonstrate the average number of attacks per day, we chose a large operator with a subscriber base of more than 40 million people, who agreed to publish the data without specifying the company name.
Information leak
Almost all the attacks recorded were aimed at disclosing information about the subscriber and about the operator's network. Attacks for fraud, interception of subscriber traffic and disruption of subscriber availability combined amounted to less than two percent 2.
This distribution is due to the fact that the attacker first of all needs to find out the subscriber identifiers and the addresses of the operator's network nodes. Only if the necessary information is obtained at the first stage, further attacks can be carried out. At the same time, the collection of information does not necessarily indicate an impending targeted attack on the subscriber. Instead of carrying out technically sophisticated attacks, there is a simpler way to profit by selling information to other criminal groups. Massive queries of the same type may indicate that the attackers are compiling subscriber databases, in which telephone numbers and user IDs are compared, and also collecting data about the operator for the subsequent sale of the obtained information on the black market.
Every third attack aimed at obtaining the user's IMSI, and every fifth attack aimed at disclosing the network configuration, returned the required information to the attacker.
Mainly two methods were used to obtain information - AnyTimeInterrogation and SendRoutingInfo. In addition to the fact that both methods reveal information about the network, and the SendRoutingInfo method returns the IMSI of subscribers, these messages also allow us to find out the location of the subscriber. The results show that in 17.5% of cases, the network's responses to such requests contained data on the location of the subscriber.
It is interesting to note that SMS Home Routing was installed on all networks to counter SendRoutingInfoForSM attacks. The SendRoutingInfoForSM message requests the information required to deliver the incoming SMS - the subscriber ID and the serving node address. In normal operation, this message should be followed by an incoming SMS, otherwise the requests are considered illegitimate. Each request should be sent to the SMS Home Routing system, which returns virtual identifiers and addresses in response, however, due to the supposedly incorrect configuration of the network equipment, this method of protection was not effective enough - in 87% of cases, suspicious requests bypassed SMS Home Routing. We noted similar results in the course of work on the security analysis of SS7 networks.
Fraud
About a quarter of all attempts were successful: the messages were accepted by the operator's network as legitimate, regardless of the availability of traffic filtering tools.
Traffic interception
Illegal UpdateLocation requests accounted for only 0.01% of the total number of attacks, but this method poses a particular danger because it allows you to intercept subscriber SMS containing confidential information and redirect calls to attackers' numbers, which can be used by criminals for fraudulent purposes.
In 2017, SMS interception was a prime example of an attack using vulnerabilities in SS7 networks.subscribers of the German mobile operator, as a result of which the criminals managed to steal money from the bank accounts of users. The attack was carried out in two stages. At the first stage, the criminals sent users letters containing a link to a phishing site masquerading as the bank's official website, and stole logins and passwords from bank accounts. To pass two-factor authentication and confirm further operations, they needed access to one-time codes that the bank sends to the user via SMS. It is believed that the criminals had previously purchased access to the SS7 network on the black market. At the second stage of the attack, they registered subscribers in a fake network, posing as a roaming partner - a foreign mobile operator. After that, incoming SMS containing one-time codes and notifications of completed transactions, sent to the attackers' number. According to experts, the criminals carried out attacks mainly at night in order to reduce the likelihood of detection of their actions.
Denial of service
Denial of service is a serious threat to electronic devices in the Internet of Things. Not only individual user devices are connected to communication networks today, but also elements of the infrastructure of smart cities, modern industrial enterprises, transport, energy and other companies.
As we have already noted, an attacker can conduct an attack on a subscriber availability violation in such a way that the restoration of communication will be impossible without contacting technical support, and the average user unavailability time exceeds three hours. Loss of reputation as a reliable telecom provider can deprive the operator of a significant proportion of customers who prefer to use the services of other companies.
An example of an attack
As noted above, implementing individual defenses without providing an integrated security approach is not enough to counter all attacks that exploit vulnerabilities that are rooted in the very architecture of SS7 networks.
Let's consider a real example, identified during the work. The attack was a series of sequential steps that were combined into a logical chain by the intrusion detection system, while the existing security systems were unable to recognize individual requests as illegitimate. First of all, the attackers made a successful attempt to find out the subscriber's IMSI by phone number. Having received the information necessary for further actions, they tried to establish the location of the subscriber, but this stage of the attack ended in failure. A day later, the attackers sent a request to register a subscriber in the fake network, which was executed by the operator's network, and were able to intercept the subscriber's incoming calls and SMS, which was probably their goal. Let's consider each step in more detail.
The PT TAD attack detection and prevention system recorded SendRoutingInfoForSM messages for a subscriber of the operator's home network, which were sent from an external node. The messages were flagged as suspicious because they were not followed by the sending of an SMS, as is assumed in the case of legitimate activity. Each such message was followed by an attempted ProvideSubscriberInfo attack that was blocked by the network. PT TAD detected a sequential combination of SendRoutingInfoForSM and ProvideSubscriberInfo attacks with an interval of 1-2 seconds, which indicates that the actions to determine the location of subscribers are automated.
Since the operator's network used the SMS Home Routing system, the response to the SendRoutingInfoForSM message did not have to contain the real IMSI, as well as the address of the real MSC / VLR. However, a package formed in a certain way made it possible to bypass the not quite correctly configured mechanism of SMS Home Routing. The Edge STP MUST route SendRoutingInfoForSM messages received from the outside to the SMS Router. However, if in the STP configuration, routing by addressing type has a higher priority than checking the opcode, then an attacker can send a SendRoutingInfoForSM message, addressing it in the numbering plan (E.214) inherent in the subscriber registration in the roaming network (UpdateLocation), and STP will route the signaling message without checking the opcode. As a result of the attack, the attacker received not the platform address and virtual IMSI, but the actual MSC / VLR address of the subscriber and its real IMSI. It was this data that was used for the subsequent attempt to attack ProvideSubscriberInfo in order to determine the location of the subscriber.
After detecting attempts to attack from one node, which acts as different equipment (MSC and HLR in this case), the node was marked as suspicious. The next day, this site received an UpdateLocation request to update the registration of the same subscriber. The request did not violate the subscriber movement matrix, since the previous UpdateLocation message was received six hours earlier and was passed by the signaling traffic filtering system as legitimate.
If a comprehensive approach to security was applied in the network, namely security monitoring with an integrated blocking system, then after a successful SendRoutingInfoForSM attack and an unsuccessful ProvideSubscriberInfo, the monitoring system would immediately notify the filtering module that it is necessary to update the list of prohibited nodes to block any traffic coming from of this node.
CONCLUSION
According to the results of the study, the security of mobile networks is still at a low level. The vast majority of networks are susceptible to vulnerabilities that allow intercepting voice calls and messages from subscribers, conducting fraudulent operations and disrupting the availability of services for subscribers.
The cybercriminals are well aware of the existing vulnerabilities, and we have already seen the consequences of their attacks, using the example of a recent incident that affected subscribers of a German telecom operator: money was stolen from users' bank accounts. Judging by the level of illegitimate activity detected by the PT TAD attack detection and prevention system, we can expect new similar incidents in the near future.
We noted that operators are aware of the security flaws in signaling networks and are starting to implement additional security measures to close vulnerabilities, including filtering and blocking signaling traffic. However, these systems cannot completely solve the problems associated with the features of the architecture of SS7 networks.
Dealing with criminals requires a comprehensive approach to security. It is necessary to regularly analyze the security of the signaling network in order to identify existing vulnerabilities and develop measures to reduce the risks of threats, and then keep the security parameters up to date. In addition, it is important to continuously monitor and analyze messages crossing network boundaries to identify potential attacks. This task can be performed by an attack detection and prevention system that allows early detection of illegal activity and blocking suspicious requests, or transferring information about unauthorized connections to third-party systems, thereby increasing the effectiveness of existing protection tools. This approach allows you to provide a high level of protection,
ptsecurity.com
- Introduction
- Terms and designations
- Summary
- SS7 network vulnerabilities
- Research methodology
- Portrait of the participants
- Statistics on the main types of threats
- Leaked subscriber information
- Leaked operator information
- Interception of subscriber traffic
- Fraud
- Denial of service
- Protective measures and their effectiveness
- SS7 network attacks
- Methodology
- Statistics on detected attacks
- Information leak
- Fraud
- Traffic interception
- Denial of service
- An example of an attack
- Conclusion
INTRODUCTION
The modern world can no longer be imagined without mobile communications. So, in the life of everyone who uses Internet services (RBS, payment systems, mobile banks, online stores, portals of government services), SMS with one-time codes to confirm various operations have become firmly established. The security of this authentication method is based only on restricting the access of attackers to telecommunication networks.
We must not forget about the rapidly developing Internet of Things, which is spreading everywhere, penetrating both the management of industrial processes and the infrastructure of cities. Disruptions in the operation of the mobile network can completely paralyze these systems, leading both to isolated cases of stopping smart home devices or a car, causing dissatisfaction with the operator's customers, and to more dangerous consequences, for example, traffic collapses or power outages.
This report presents the results of a study of the security of SS7 networks. The Signaling System 7 standard is used to exchange service information between network devices in telecommunication networks. At the time this standard was being developed, only fixed line operators had access to the SS7 network, so security was not a priority. Today, the signaling network is no longer isolated to the same extent, so an attacker who has gained access to it in one way or another has the ability to exploit security flaws in order to listen to subscribers' voice calls, read SMS, steal money from accounts, bypass billing systems, or affect the functioning of the mobile network.
Despite the emergence of new generation 4G networks using a different signaling system - Diameter, SS7 security problems will remain relevant for a long time, since telecom operators still have to provide support for 2G / 3G standards and interoperability between networks of different generations. Moreover, research proves that the Diameter protocol is subject to the same threats as SS7. The vulnerabilities of this protocol, as well as a description of possible cross-protocol attacks, during which the shortcomings of both Diameter and SS7 are exploited, will be published in one of the next analytical reports.
We decided to show not only the vulnerabilities that we identify in the course of analyzing the security of SS7 networks, but also the facts of the actual exploitation of these vulnerabilities in order to demonstrate the scale of the security problems of modern communication networks. We tracked how the security situation of SS7 networks has changed over the past three years; learned what protection means are used by telecom operators and how effective the existing solutions are in real conditions.
TERMS AND DESIGNATIONS
HLR (Home Location Register) is a database that contains information about the subscriber.
MSC (Mobile Switching Center) is a mobile telephone switch.
SS7 (Signaling System 7) is a common channel signaling system used in international and local telephone networks.
STP (Signaling Transfer Point) is an edge node for routing signaling messages.
VLR (Visitor Location Register) - a database that contains information about the location and movement of the subscriber.
SUMMARY
The security of SS7 networks is still low. All studied networks contain dangerous vulnerabilities that can disrupt the availability of services for subscribers. Almost every network can listen to a subscriber's conversation or read incoming SMS, and fraudulent operations can be successfully carried out in 78% of networks.
Attackers are aware of vulnerabilities and exploit them. The PT Telecom Attack Discovery system for detecting and preventing attacks detects real attacks that cybercriminals carry out on the networks of telecom operators. Mostly they are aimed at collecting information about subscribers and network configuration. However, we also observe such attacks, which, in all likelihood, are carried out with the aim of fraud, interception of subscriber traffic and disruption of availability.
Operators are aware of the risks involved. Measures are being taken to reduce the likelihood of threats being realized. To date, it has been possible to reduce the risk of information leakage about the network and subscribers. In 2017, the SMS Home Routing system was functioning in all the networks studied, and a filtering and blocking system for signaling traffic was installed in every third network.
The solutions used are not effective enough. Despite the active introduction of additional protection systems, all networks were exposed to vulnerabilities associated with both special cases of incorrect hardware configuration, and with architectural problems of SS7 signaling networks, which cannot be eliminated with the available means. Only a comprehensive approach to solving security problems, including regular security analysis, keeping network parameters up-to-date, constant monitoring of signaling traffic and timely detection of illegitimate activity, can provide a high level of protection from criminals.
VULNERABILITIES OF SS7 NETWORKS
Research methodology
Every year Positive Technologies experts carry out dozens of works to analyze the security of SS7 signaling networks. The checks simulate the actions of a potential intruder who is supposed to carry out attacks from an international or national network external to the operator. An attacker has the ability to send requests for application-level protocols to the tested network, which can lead to the implementation of various threats both in relation to the operator itself and its subscribers, if the operator does not take sufficient protection measures. To emulate a malicious node, special equipment is used - PT Telecom Vulnerability Scanner.
For the study, we selected 24 of the most informative projects for analyzing the security of SS7 networks in 2016–2017, during which the most complete list of checks was carried out. As part of our benchmarking analysis, we also used the data provided in our 2015 research report.
Portrait of the participants
In 2020–2021, operators from Europe (including Russia) and the Middle East took part in the study.
Half of the participants were telecom operators with a subscriber base of more than 40 million people. Smaller companies, with less than 10 million subscribers, were predominantly virtual mobile operators based on larger telecoms.
Statistics on the main types of threats
We highlight the following threats that an attacker can implement by exploiting the security flaws of mobile operators' networks:
- disclosure of information about the subscriber;
- disclosure of information about the operator's network;
- interception of subscriber traffic;
- fraud;
- denial of service.
Disclosure of information about a subscriber refers to the leakage of IMSI identifiers, disclosure of the location of the subscriber, as well as other information, such as current balance or profile details. Disclosure of information about the operator's network is fraught with leakage of information about the configuration of the SS7 network.
At the moment, there are known such techniques for intercepting subscriber traffic in SS7 networks, which allow you to listen or redirect incoming and outgoing voice calls to third-party numbers, as well as intercept users' SMS.
Fraudulent attacks can be carried out against both the operator and subscribers. For example, changing the billing category for roaming calls or bypassing the billing system can harm the telecom operator, and transferring funds from the account, redirecting calls to paid numbers, or subscribing to paid services - to network users.
In this study, we only consider denial of service for individual subscribers, since only a small number of operators perform testing of network elements in the framework of security audits, which can be fraught with disruptions in the operation of the mobile network. It should be taken into account that the disruption of functioning can be massive if the attackers have a subscriber base of the operator or have sufficient resources to select subscriber identifiers.
As operators' awareness of the security issues of SS7 networks is gradually increasing, operators are beginning to implement security measures against attacks. If in 2015 each studied network was exposed to all types of threats, then over the past two years there have been positive changes in the overall level of network security.
Carriers are taking SS7 security more seriously and deploying security controls
The risks of information leakage about the operator's network, fraud and interception of subscriber traffic have significantly decreased. Nevertheless, each network examined, as before, is subject to vulnerabilities that allow obtaining information about subscribers or causing a denial of service.
Consider the proportion of successful attack attempts that the experts were able to implement as part of their work on security analysis.
As you can see, first of all, operators are taking measures aimed at reducing the risk of disclosing information about the network and subscribers, since this information serves as the initial data for the implementation of many other attacks. Compared to 2015, the share of successful attacks aimed at disclosing information about the operator's network decreased by almost three times, and it was twice less likely to obtain data on network subscribers. Methods of protection against such attacks are quite simple, and there are ready-made solutions on the information security market, but 100% of networks are still vulnerable to disclosure of information about subscribers, which indicates the insufficient effectiveness of existing solutions.
For other types of threats, the percentage of successful attacks changed insignificantly. As we will show later, the reason is that the implementation of traffic filtering and blocking systems cannot compensate for the architectural problems of SS7; a different approach is required to minimize these risks.
Architectural problems of SS7 networks are not solved by existing traffic filtering tools
The following reasons can be identified for which the implementation of certain threats is possible:
- lack of verification of the real location of the subscriber;
- the impossibility of verifying the affiliation of a network subscriber;
- flaws in SMS Home Routing configuration;
- lack of message filtering.
In particular, attacks are possible aimed at disclosing the location of the subscriber, redirecting or intercepting a call, intercepting SMS, changing the payment category or profile of the subscriber. Lack of location check refers to signaling messages arriving in the subscriber's home network from the network in the coverage area of which the subscriber is in roaming. If the signal message is composed correctly, there is no way to check its authenticity only by the received parameters. An additional check is needed to see if the subscriber is actually in the network from which the signaling traffic came.
The difficulty of verifying the belonging of a network subscriber is associated with signaling messages sent by the telecom operator to its subscribers who are in roaming to another network in which these subscribers are currently registered. To determine illegitimate traffic, you need to check the correspondence between the message source and the subscriber identifier. If the source address and subscriber ID correspond to the same operator, then the message is legitimate. But if a match is not found, this does not mean falsification of the message, since the source address can be changed, for example, by the transit operator. We can confidently talk about the illegitimacy of this type of signaling traffic if it comes from external networks and is directed to the subscribers of the home network.
SMS Home Routing is a hardware and software complex designed to hide real subscriber identifiers and addresses of network equipment. It is used in 85% of the studied networks; however, incorrect configuration allows attacks to bypass the protection mechanism. In networks where the SMS Home Routing system was absent, absolutely all attempts to obtain subscriber IDs and information about the network were successful.
Operators are actively introducing filtering and blocking systems for signaling traffic: in 2017, they were already functioning in a third of the networks studied. As a result, attacks that exploit vulnerabilities associated with the lack of message filtering are currently successful only in 10% of cases, which is three times better than in previous years.
To carry out attacks, standard messages are used to perform service operations. These messages must be checked at the border or within the operator's network to prevent illegitimate requests. One and the same attack can be carried out by several messages (methods), while the success of different methods is not the same. Next, we will analyze in detail what methods and with what degree of probability attackers can implement all of the listed threats.
Leaked subscriber information
As mentioned above, the primary measure to reduce the likelihood of most attacks is to reduce the risk of disclosing IMSI - unique identifiers of subscribers. Compared to 2015, it was possible to find out IMSI by the subscriber's phone number in the past year about 4 times less often.
Today it is possible to determine the location of a subscriber in 75% of networks, while the share of successful attacks using various methods is 33%, which is also much better than previous indicators.
7. The proportion of successful attacks by types of threats associated with obtaining information about a subscriber
Disclosure of information about a subscriber can be implemented by four methods, the success of which is shown in Fig. eight.

Methods used to obtain the subscriber's IMSI (percentage of successful attacks)
The decrease in the share of successful attacks using the SendRoutingInfo and SendIMSI methods is due to the introduction of filtering tools in operators' networks. The SendRoutingInfo message is used to receive routing information about the subscriber for an incoming voice call and should only be sent within the operator's home network. The SendIMSI message for requesting the IMSI of a subscriber by his phone number is currently practically not used by operators, but is processed in mobile networks in order to fully ensure compliance with standards.
The SendRoutingInfoForLCS method was successfully used only in two studied networks, which is also associated with effective message filtering. The method is used to request information by services that require data about the user's location.
The SendRoutingInfoForSM message is sent to obtain the routing information required to deliver the incoming SMS. In order not to reveal the real subscriber IDs and addresses of network elements, the message received from the external network should be forwarded to the SMS Home Routing system and return virtual data. Despite the fact that most networks use SMS Home Routing, we often encounter incorrect configuration of the edge network equipment (STP / FW), as a result of which a request is sent to the HLR bypassing the SMS Router device and returns the real IMSI of the subscriber and data about the network configuration operator.
It was mainly possible to determine the location of the subscriber using the ProvideSubscriberInfo method. This is due to the architectural flaws of SS7 networks. The ProvideSubscriberInfo message shall only be processed if the source of the message and the subscriber ID match the same operator. The problem is that due to the architectural features of SS7 networks, it is impossible to determine the subscriber's ownership of the operator's network. To protect against such attacks, it is necessary to use traffic filtering systems.
In 2015, we assumed that carriers were well aware of the AnyTimeInterrogation attacks, which reveal the user's location by their phone number, and the corresponding protection methods - since none of our attempts were successful. However, over the next two years, we encountered networks that lacked filtering for this message.

Methods used to determine the location of the subscriber (percentage of successful attacks)
Disclosing the balance or details of a user profile does not pose an immediate serious risk, so protection against these threats appears to be a lower priority. In addition, protection against most of the methods used is possible only with constant monitoring and filtering of signaling traffic. It is possible to implement the corresponding attacks on each investigated network; for this, the following messages are used:
- RestoreData;
- InterrogateSS;
- ProcessUnstructuredSS;
- UpdateLocation;
- AnyTimeSubscriptionInterrogation
Leaked operator information
In the course of the checks, more than half of the attacks related to SMS Home Routing configuration problems, which allow obtaining network configuration data, were carried out. Overall, however, operators have achieved a significant reduction in the likelihood of such disclosures.

Methods used to obtain information about the configuration of the SS7 network (percentage of successful attacks)
The increase in the number of successful attacks using the SendRoutingInfoForSM method in 2016 was caused by the fact that we investigated several networks in which SMS Home Routing was absent.
Interception of subscriber traffic
The risk of interception of user traffic is still quite high. The overwhelming majority of attempts to intercept subscribers' SMS have been successful. Today, extremely important information is transmitted via SMS - passwords for two-factor authentication, which are sent by services that provide remote banking services, Internet payments, etc. a large volume of traffic, the reason for the termination of the contract.9 out of 10 SMS can be intercepted by fraudsters
It was possible to listen to or redirect incoming and outgoing calls of subscribers to third-party numbers in more than half of the cases.
Call forwarding is only meant to transfer a call to a third-party number. The evolution of this attack allows the connection to be established in such a way that an attacker can listen in on the subscriber's conversation.
The UpdateLocation message is used to notify the HLR that the subscriber has changed the serving switch. By sending a fake request to register a subscriber in the attacker's network, incoming SMS or calls are intercepted. When an incoming call arrives, the operator's network sends a request to the fake network to obtain the subscriber's roaming number. An attacker can reply with his own PBX number, and in this case, incoming traffic will go to his equipment. Then, after sending a repeated request to register a subscriber in the real network, the attacker can redirect the call to the subscriber's number. As a result, the conversation will pass through the equipment controlled by the attacker. The same principle is at the heart of intercepting incoming calls with the RegisterSS method,
The high percentage of successful attacks is due to the lack of verification of the real location of the subscriber. To reduce the likelihood of attacks using these methods, it is necessary to ensure constant monitoring of signaling traffic and analysis of illegitimate activity to identify suspicious nodes, build lists of prohibited and trusted networks, and immediately block requests from prohibited sources.
Outgoing calls are listened to according to a similar scheme: a specially formed InsertSubscriberData message replaces the platform address for call charging in the subscriber's profile stored in the VLR database. When a request arrives at a new address, the attacker first redirects the outgoing call to the equipment under his control and only then to the called subscriber.
Thus, the attacker is able to listen to any conversation of the subscriber.
78% of networks are susceptible to fraud
Fraud
A wide range of methods are known that can be used by criminals in order to obtain financial gain at the expense of the operator or network subscribers. These methods can be divided into four categories:
- illegal forwarding of incoming or outgoing calls;
- exploitation of USSD requests;
- manipulation of SMS;
- changing the subscriber's profile.
Illegal call forwarding of incoming or outgoing calls
An attacker can redirect subscribers' voice calls to premium numbers or to a third-party number in order to evade tariffication. The connection will be paid at the expense of the subscriber if unconditional forwarding is set to the attacker's number or at the expense of the telecom operator - if the subscriber is registered in a false network and his roaming number is changed.A fraudster can find out passport data and a passphrase, posing as a bank employee
Call forwarding also allows for other fraudulent schemes. So, for example, if a subscriber makes an outgoing call to the bank, then by redirecting him to his own number and introducing himself as a bank employee, the offender can find out confidential information necessary to confirm his identity, in particular, passport data and a code word. The opposite situation is also possible: by forwarding incoming calls, an attacker can impersonate a subscriber, for example, to confirm banking transactions.
Calls are redirected using the previously mentioned UpdateLocation, RegisterSS, InsertSubscriberData methods, as well as the AnyTimeModification method, with which you can make changes to the subscriber profile (note that none of the attacks by the AnyTimeModification method led to the desired result).
Operation of USSD requests
An attacker can transfer money from the account of a subscriber or operator's partners by exploiting the ability to send fake USSD requests using the ProcessUnstructuredSSRequest method. Another method - UnstructedSSNotify - is used to send notifications to subscribers on behalf of various services, including from the operator itself. An attacker can send a fake notification on behalf of a trusted service containing instructions that the subscriber must follow: send an SMS to a paid number to activate the service, call a fake bank number in connection with suspicious card transactions, or follow the link to update the application.
SMS manipulation
Phishing or advertising messaging can be organized by sending fake SMS on behalf of arbitrary subscribers or services using the MT-ForwardSM and MO-ForwardSM methods. The MT-ForwardSM method is designed to deliver incoming messages and can be used by cybercriminals to generate fake incoming SMS messages. Unauthorized use of the MO-ForwardSM method allows you to send outgoing messages on behalf of and at the expense of network subscribers. In 2017, all networks that were checked in the course of security analysis were exposed to vulnerabilities associated with insufficient analysis of signaling traffic, which allow sending fake messages.All networks allow sending fake SMS on behalf of subscribers or trusted services
Change subscriber profile
Information about the billing platform and service subscriptions is stored in the subscriber's profile. To bypass the billing system in real time, it is necessary to delete the subscriber's O-CSI subscription, which is used to make outgoing calls by the subscriber, or change the billing platform address to a fictitious one. In order to prevent non-chargeable calls, the O-CSI parameters indicate that if the platform is unavailable, the call must be terminated. However, you can override this parameter so that the call continues without contacting the platform. As a result, the legitimate platform will not receive information about calls and, accordingly, will not perform tariffication.
Attacks using the InsertSubscriberData and DeleteSubscriberData methods were successfully carried out in more than 80% of cases, and attempts to attack using the AnyTimeModification method were unsuccessful.
Denial of service
Today, attacks aimed at denial of service to individual subscribers are possible in every network investigated. The identified shortcomings are associated with the architectural problems of the protocols (the inability to verify the subscriber's ownership of the network and the lack of verification of the real location of the subscriber) and allow successfully carrying out attacks by the following methods:Denial of service to subscribers is possible in 100% of networks
- UpdateLocation;
- RegisterSS;
- InsertSubscriberData;
- PurgeMS.
All attack attempts resulted in denial of service to subscribers, with the exception of the InsertSubscriberData method (83% of successful attacks). The AnyTimeModification method can be used for the same purpose, however, the security parameters of all the studied networks prevented the passage of these requests.
In addition to the ability to make voice calls and exchange SMS, the subscriber may lose access to the Internet when carrying out an attack using the InsertSubscriberData method.
Despite the fact that the considered violations of the network functioning are purposeful and affect only one subscriber in each case, a massive failure in service is not excluded if the attacker has a base of subscriber identifiers or can brute force the identifiers.
These service disruptions can be critical for IoT devices. This is a rapidly growing market of billions of devices that require access to telecommunications networks to operate. Periodic failure of smart home systems, video surveillance systems, devices that track the location of a car, or the stoppage of industrial processes of an enterprise can lead to a significant churn of customers.
When conducting research, we found that the average time of subscriber unavailability after such an attack is more than three hours, and in some cases, when a request for an accessibility violation is made, the current subscriber profile in the database changes, and the equipment is not able to restore the profile, even when the subscriber reboots the device. ... This has happened in accessibility attacks using the PurgeMS and InsertSubscriberData methods.3 hours - average time of subscriber unavailability
When deleting the VLR address from the HLR, in which the subscriber is currently registered, through the PurgeMS procedure initiated by a certain third node, the following occurs. Incoming calls cannot be routed to the serving VLR / MSC because there is no registration address in the HLR. In this case, outgoing calls to the subscriber are available, since the registration record in the VLR has not changed.
Restoring the registration to the HLR in the usual way - by rebooting the phone (or other device) - does not work, since the VLR does not initiate the UpdateLocation procedure in relation to the HLR, assuming that there are no changes in the subscriber's registration data.
As a result, it is possible to restore the registration, and, accordingly, the subscriber's availability for incoming calls, only when registering in the coverage area of another serving MSC, for example, if you first manually select the network of another operator, and then select the home network again. Another option is to relocate to another MSC in your home network.
Smart device failures can lead to customer churn
Protective measures and their effectiveness
The identified vulnerabilities are associated with both incorrect configuration of network equipment or security tools, and with fundamental shortcomings of SS7 networks. If in the first case it is enough to make changes to the device configuration to eliminate vulnerabilities, then the architectural problems of networks can be solved only by correct filtering and monitoring of signaling traffic. To ensure the analysis and blocking of incoming messages without disrupting the functioning of the network, special additional equipment is required. Let's consider what protection tools were used in the networks under study and to what extent they help to reduce the risks of threats.
The SMS Home Routing complex was installed in almost all networks. Since 2016, operators have begun to implement filtering and blocking systems for signaling traffic, and in 2017 such systems were already functioning in every third network surveyed.
The SMS Home Routing system is aimed at counteracting the disclosure of the subscriber's IMSI and network configuration using the SendRoutingInfoForSM method, and indeed, the percentage of successful attacks if it is installed is reduced by a third. However, due to incorrect configuration of the equipment, in 67% of cases, real data can be obtained.
It should be remembered that SMS Home Routing cannot be used to protect against other types of attacks. Moreover, this system is not designed to protect the network, but is installed to properly route incoming SMS. Studies show that networks using SMS Home Routing are not more secure than others, possibly because carriers often rely solely on SMS Home Routing, neglecting additional security measures.
Let us compare the results of attempts to carry out attacks by various methods, to counter which it is currently recommended to use filtering and blocking systems for signaling traffic.
As we can see, correct filtering of signaling traffic can reduce the risks of unauthorized requests. This is partly confirmed by the following diagram, which compares the feasibility of each threat. It is worth highlighting the fact that in networks where the system of filtering and blocking traffic was introduced, not a single attempt to track the location of the subscriber was successful. In other networks, attempts to determine the location were successful in 40% of cases.The use of a filtering system is not able to ensure absolute network security
At the same time, it is obvious that even the use of a filtering system is not able to ensure absolute network security. Let's figure out why this is happening.
All messages described in this report fall into three categories as defined in GSMA IR.82:
- messages transmitted exclusively between devices in the operator's home network;
- messages that are transmitted from the operator's home network to the subscriber's guest network;
- which are transmitted from the guest network to the operator's home network.
Traffic filtering systems provide complete protection against attacks involving messages of the first category, and in the case of messages of the second category, the proportion of successful attacks is halved.
The situation is different with the third category. Unjustified blocking of such messages can affect the service of a subscriber who is actually in roaming. For example, an erroneous blocking of a legitimate registration of a subscriber in an external network can lead to the fact that the subscriber will be left without communication in roaming, and for the operator this means a clear shortfall in profit and a possible loss of the client. Identifying illegitimate requests is a complex technical challenge. It is recommended to filter messages based on the lists of trusted and prohibited sources provided by roaming partners; however, the volume of such lists and the need for their constant updating significantly complicate the implementation of the solution in practice. For fear of disrupting the functioning of the network, operators are very cautious about blocking such messages.
To achieve a high level of protection against all types of threats under consideration, an integrated approach to information security is required. First of all, it is important to conduct a regular analysis of the security of the signaling network, as this allows you to identify actual vulnerabilities that may arise when changing the network configuration and parameters of network equipment, and to assess the risks associated with information security.
In addition, it is required to ensure constant monitoring and analysis of messages crossing the network boundaries in order to keep the security parameters up to date, timely identify potential threats and respond to them. Instructions for using monitoring systems to counter attacks are also contained in the GSMA 1... This task should be performed using dedicated threat detection systems that can intelligently analyze messages in real time. This solution allows detecting illegal activity of external nodes at an early stage and transmitting information about them to the signaling traffic filtering system to increase its efficiency, for example, to update the lists of prohibited nodes, and also allows detecting configuration errors in network devices and notifying the operator's employees about the need to fix them.
Security is a process, so you cannot limit yourself to one-off measures (audits or implementation of safeguards). An integrated approach is used by Positive Technologies specialists to protect the signaling networks of their clients, you can find out more on the website by asking a question through the feedback form or by writing to us at info@ptsecurity.com
In the next section, we will explore whether existing defenses can be used against intruders in a real-world environment, and how using threat detection and prevention can help protect your network.
ATTACKS ON THE SS7 NETWORK
We examined the vulnerabilities that SS7 networks are exposed to and the possible threats associated with their exploitation. The question remains: how do the results of security research correlate with real life, qualifications and capabilities of real criminals? In this section, we will present the results of security monitoring projects in SS7 networks and see what attacks mobile operators actually face and whether the existing protection measures are effective in practice.
Methodology
Security monitoring projects in SS7 networks were carried out for large telecom operators in Europe and the Middle East. The purpose of these works was to demonstrate the capabilities of the PT Telecom Attack Discovery (PT TAD) system, which is designed to analyze signaling traffic in real time and detect illegal activity with the ability to block unauthorized messages or alert third-party filtering and traffic blocking tools. This approach allows you to timely identify potential threats and respond to them without adversely affecting the functioning of the network.
PT TAD can also be used as a passive system for detecting illegitimate activity, in this case the system allows analyzing the passing traffic, but does not affect it. Our research presents the results of traffic monitoring in passive mode.
Statistics on detected attacks
All networks where security events were monitored used SMS Home Routing equipment, and one or another system for filtering and blocking signaling traffic was installed in every third network.
During the monitoring, we obtained results indicating that attackers are not only well aware of the security problems of signaling networks, but also actively exploit these vulnerabilities.
The table for each threat shows the vertical distribution of all attack attempts by the methods used. The proportions of successful attacks are listed for each threat and separately for each method. An empty cell means that the message does not lead to the implementation of this threat.
For example, an attempt to get the IMSI of a subscriber in 79.9% of cases is carried out by violators using the SendRoutingInfo method. In general, the violator succeeds in obtaining IMSI by one method or another in 34.5% of cases. And the SendRoutingInfo method itself is successful in 22.6% of attack attempts.
As we found out, the source of most attacks are not the national operators of the country in which the security monitoring was carried out, but the international telecom operators. Suspicious inquiries come mainly from countries in Asia and Africa; This is probably due to the fact that in these countries it is easier for an attacker to buy access to the SS7 network. At the same time, physical access to the equipment of the operator who provided the ability to connect to the SS7 network is not required, the attacker can be anywhere in the world.
To demonstrate the average number of attacks per day, we chose a large operator with a subscriber base of more than 40 million people, who agreed to publish the data without specifying the company name.
Information leak
Almost all the attacks recorded were aimed at disclosing information about the subscriber and about the operator's network. Attacks for fraud, interception of subscriber traffic and disruption of subscriber availability combined amounted to less than two percent 2.
This distribution is due to the fact that the attacker first of all needs to find out the subscriber identifiers and the addresses of the operator's network nodes. Only if the necessary information is obtained at the first stage, further attacks can be carried out. At the same time, the collection of information does not necessarily indicate an impending targeted attack on the subscriber. Instead of carrying out technically sophisticated attacks, there is a simpler way to profit by selling information to other criminal groups. Massive queries of the same type may indicate that the attackers are compiling subscriber databases, in which telephone numbers and user IDs are compared, and also collecting data about the operator for the subsequent sale of the obtained information on the black market.
Every third attack aimed at obtaining the user's IMSI, and every fifth attack aimed at disclosing the network configuration, returned the required information to the attacker.
Mainly two methods were used to obtain information - AnyTimeInterrogation and SendRoutingInfo. In addition to the fact that both methods reveal information about the network, and the SendRoutingInfo method returns the IMSI of subscribers, these messages also allow us to find out the location of the subscriber. The results show that in 17.5% of cases, the network's responses to such requests contained data on the location of the subscriber.
Filtering parameters on network equipment (STP, HLR) or a correctly configured signaling traffic filtering system would completely eliminate the possibility of attacks using these messages, and therefore reduce the risk of other threats. However, in practice, the message filtering parameters are not always set correctly. Thus, the percentage of responses to suspicious requests to determine the user's location in networks protected by the signaling traffic blocking system turned out to be two times lower than in other networks. Approximately the same results were obtained for attacks aimed at disclosing network configuration and subscriber IDs. In general, these are good indicators indicating the effectiveness of the protection measures taken, but with the correct configuration, the rate of successful attacks would be reduced to zero.In 87% of cases, suspicious requests bypassed SMS Home Routing
It is interesting to note that SMS Home Routing was installed on all networks to counter SendRoutingInfoForSM attacks. The SendRoutingInfoForSM message requests the information required to deliver the incoming SMS - the subscriber ID and the serving node address. In normal operation, this message should be followed by an incoming SMS, otherwise the requests are considered illegitimate. Each request should be sent to the SMS Home Routing system, which returns virtual identifiers and addresses in response, however, due to the supposedly incorrect configuration of the network equipment, this method of protection was not effective enough - in 87% of cases, suspicious requests bypassed SMS Home Routing. We noted similar results in the course of work on the security analysis of SS7 networks.
Fraud
Fraudulent attacks against both the operator and subscribers accounted for only 1.32%, and a significant part of them fell on the operation of USSD requests. Unauthorized sending of USSD requests allows you to transfer money from a subscriber's account, subscribe a subscriber to an expensive service, or send a phishing message on behalf of a trusted service.23% of fraudulent attacks are successfully carried out by cybercriminals
About a quarter of all attempts were successful: the messages were accepted by the operator's network as legitimate, regardless of the availability of traffic filtering tools.
Traffic interception
During the course of the work, UpdateLocation requests for registration of a subscriber in the new network, coming from suspicious sources, were recorded. At the same time, not a single attempt at fake registration was rejected by the operator's network. As the results of work on security analysis and data from security monitoring projects show, the use of a system of filtering and blocking traffic does not provide significant advantages in this case - to protect against such attacks, it is necessary to take comprehensive security measures.100% of attacks aimed at intercepting SMS are successful
Illegal UpdateLocation requests accounted for only 0.01% of the total number of attacks, but this method poses a particular danger because it allows you to intercept subscriber SMS containing confidential information and redirect calls to attackers' numbers, which can be used by criminals for fraudulent purposes.
In 2017, SMS interception was a prime example of an attack using vulnerabilities in SS7 networks.subscribers of the German mobile operator, as a result of which the criminals managed to steal money from the bank accounts of users. The attack was carried out in two stages. At the first stage, the criminals sent users letters containing a link to a phishing site masquerading as the bank's official website, and stole logins and passwords from bank accounts. To pass two-factor authentication and confirm further operations, they needed access to one-time codes that the bank sends to the user via SMS. It is believed that the criminals had previously purchased access to the SS7 network on the black market. At the second stage of the attack, they registered subscribers in a fake network, posing as a roaming partner - a foreign mobile operator. After that, incoming SMS containing one-time codes and notifications of completed transactions, sent to the attackers' number. According to experts, the criminals carried out attacks mainly at night in order to reduce the likelihood of detection of their actions.
Denial of service
Attacks aimed at denial of service to individual subscribers were also few in number, with only 7.8% of such attacks being successful. The InsertSubscriberData method was mainly used, but 99% of these messages remained unanswered, that is, they were ignored by the operator's network. The presence of traffic filtering and blocking systems had a significant impact on the bottom line: the percentage of successfully processed requests in these networks was four times lower than in the rest, but it was not possible to completely protect against such attacks.Denial of service is dangerous for the Internet of Things
Denial of service is a serious threat to electronic devices in the Internet of Things. Not only individual user devices are connected to communication networks today, but also elements of the infrastructure of smart cities, modern industrial enterprises, transport, energy and other companies.
As we have already noted, an attacker can conduct an attack on a subscriber availability violation in such a way that the restoration of communication will be impossible without contacting technical support, and the average user unavailability time exceeds three hours. Loss of reputation as a reliable telecom provider can deprive the operator of a significant proportion of customers who prefer to use the services of other companies.
An example of an attack
As noted above, implementing individual defenses without providing an integrated security approach is not enough to counter all attacks that exploit vulnerabilities that are rooted in the very architecture of SS7 networks.
Let's consider a real example, identified during the work. The attack was a series of sequential steps that were combined into a logical chain by the intrusion detection system, while the existing security systems were unable to recognize individual requests as illegitimate. First of all, the attackers made a successful attempt to find out the subscriber's IMSI by phone number. Having received the information necessary for further actions, they tried to establish the location of the subscriber, but this stage of the attack ended in failure. A day later, the attackers sent a request to register a subscriber in the fake network, which was executed by the operator's network, and were able to intercept the subscriber's incoming calls and SMS, which was probably their goal. Let's consider each step in more detail.
The PT TAD attack detection and prevention system recorded SendRoutingInfoForSM messages for a subscriber of the operator's home network, which were sent from an external node. The messages were flagged as suspicious because they were not followed by the sending of an SMS, as is assumed in the case of legitimate activity. Each such message was followed by an attempted ProvideSubscriberInfo attack that was blocked by the network. PT TAD detected a sequential combination of SendRoutingInfoForSM and ProvideSubscriberInfo attacks with an interval of 1-2 seconds, which indicates that the actions to determine the location of subscribers are automated.
Since the operator's network used the SMS Home Routing system, the response to the SendRoutingInfoForSM message did not have to contain the real IMSI, as well as the address of the real MSC / VLR. However, a package formed in a certain way made it possible to bypass the not quite correctly configured mechanism of SMS Home Routing. The Edge STP MUST route SendRoutingInfoForSM messages received from the outside to the SMS Router. However, if in the STP configuration, routing by addressing type has a higher priority than checking the opcode, then an attacker can send a SendRoutingInfoForSM message, addressing it in the numbering plan (E.214) inherent in the subscriber registration in the roaming network (UpdateLocation), and STP will route the signaling message without checking the opcode. As a result of the attack, the attacker received not the platform address and virtual IMSI, but the actual MSC / VLR address of the subscriber and its real IMSI. It was this data that was used for the subsequent attempt to attack ProvideSubscriberInfo in order to determine the location of the subscriber.
After detecting attempts to attack from one node, which acts as different equipment (MSC and HLR in this case), the node was marked as suspicious. The next day, this site received an UpdateLocation request to update the registration of the same subscriber. The request did not violate the subscriber movement matrix, since the previous UpdateLocation message was received six hours earlier and was passed by the signaling traffic filtering system as legitimate.
If a comprehensive approach to security was applied in the network, namely security monitoring with an integrated blocking system, then after a successful SendRoutingInfoForSM attack and an unsuccessful ProvideSubscriberInfo, the monitoring system would immediately notify the filtering module that it is necessary to update the list of prohibited nodes to block any traffic coming from of this node.
CONCLUSION
According to the results of the study, the security of mobile networks is still at a low level. The vast majority of networks are susceptible to vulnerabilities that allow intercepting voice calls and messages from subscribers, conducting fraudulent operations and disrupting the availability of services for subscribers.
The cybercriminals are well aware of the existing vulnerabilities, and we have already seen the consequences of their attacks, using the example of a recent incident that affected subscribers of a German telecom operator: money was stolen from users' bank accounts. Judging by the level of illegitimate activity detected by the PT TAD attack detection and prevention system, we can expect new similar incidents in the near future.
We noted that operators are aware of the security flaws in signaling networks and are starting to implement additional security measures to close vulnerabilities, including filtering and blocking signaling traffic. However, these systems cannot completely solve the problems associated with the features of the architecture of SS7 networks.
Dealing with criminals requires a comprehensive approach to security. It is necessary to regularly analyze the security of the signaling network in order to identify existing vulnerabilities and develop measures to reduce the risks of threats, and then keep the security parameters up to date. In addition, it is important to continuously monitor and analyze messages crossing network boundaries to identify potential attacks. This task can be performed by an attack detection and prevention system that allows early detection of illegal activity and blocking suspicious requests, or transferring information about unauthorized connections to third-party systems, thereby increasing the effectiveness of existing protection tools. This approach allows you to provide a high level of protection,
- SG.11. SS7 Interconnect Security Monitoring Guidelines.
- The UpdateLocation procedure returns information about the subscriber's profile. Nevertheless, we believe that the registration of a subscriber in a fake network primarily pursues other goals: redirecting an incoming call, intercepting an SMS, or denying a subscriber service.
ptsecurity.com

