Father
Professional
- Messages
- 2,602
- Reaction score
- 837
- Points
- 113
The attackers targeted the entire globe, without any exceptions.
Since April of this year, millions of phishing emails have been sent through the Phorpiex botnet as part of a large-scale campaign using the LockBit Black ransomware. The New Jersey Cybersecurity and Communications Integration Center (NJCCIC) warned about this.
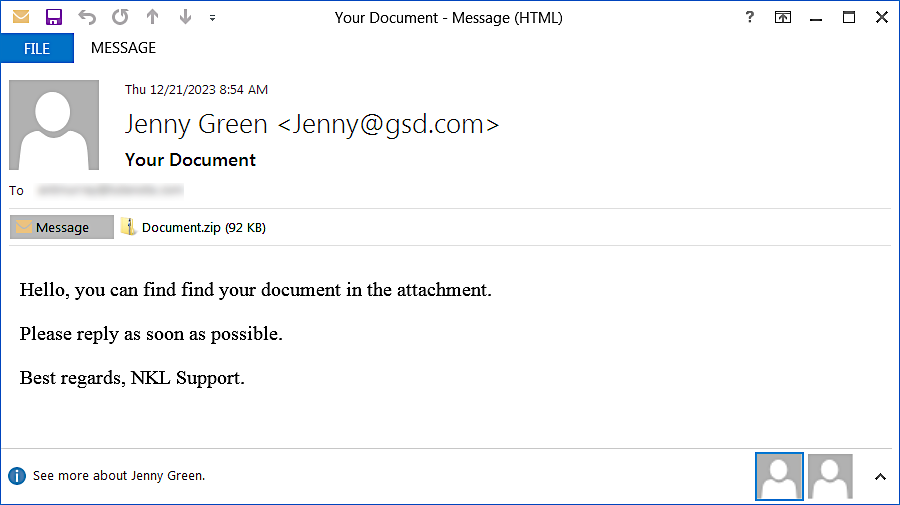
Attackers most often send emails with the topics "your document "and" photo of you??? "on behalf of" Jenny Brown "or"Jenny Green". The attachments contain a ZIP archive with an executable file that installs LockBit Black on recipients ' systems at startup, encrypting all their data.
The LockBit Black used in this attack is probably based on LockBit 3.0, which leaked to the network in September 2022. However, the current campaign is not linked to the original LockBit grouping.
Emails are sent from more than 1,500 unique IP addresses around the world, including Kazakhstan, Uzbekistan, Iran, Russia, and China.
The attack begins when the recipient opens a malicious ZIP archive and runs the executable file. This file downloads LockBit Black from the Phorpiex botnet infrastructure and executes it on the victim's system. Ransomware steals confidential data, shuts down some system services, and encrypts files.
Proofpoint, which has been investigating these attacks since April 24, reported that the attackers targeted companies in various industries around the world. Despite the low complexity of the operation, its scale and the use of ransomware as the initial malicious load make this malicious campaign stand out qualitatively.
"Since April 24 and during the week, Proofpoint has observed large-scale campaigns with millions of messages distributed through the Phorpiex botnet and delivering LockBit Black," Proofpoint researchers said. "This is the first time that we have seen such volumes of LockBit Black delivery via Phorpiex."
The Phorpiex botnet, also known as Trik, has been active for over a decade. Initially, it was a worm that spread through USB devices, Skype chats, and Windows Live Messenger, and then turned into a Trojan controlled via IRC and spreading spam.
Over time, the botnet significantly increased in quantity, controlling more than a million infected devices, but then its infrastructure was disabled, after which the source code of the project was put up for sale. One of the authors of the botnet called the reason for the sale a shift in the interests of developers who are more disinterested in supporting and developing Phorpiex.
Previously, the Phorpiex botnet was also used to send millions of emails with threats and spam, as well as to introduce a malicious module that replaces cryptocurrency addresses in the Windows clipboard with those controlled by attackers.
To protect against phishing attacks, NJCCIC recommends using risk mitigation strategies, endpoint protection solutions, and email filtering.
Since April of this year, millions of phishing emails have been sent through the Phorpiex botnet as part of a large-scale campaign using the LockBit Black ransomware. The New Jersey Cybersecurity and Communications Integration Center (NJCCIC) warned about this.
Attackers most often send emails with the topics "your document "and" photo of you??? "on behalf of" Jenny Brown "or"Jenny Green". The attachments contain a ZIP archive with an executable file that installs LockBit Black on recipients ' systems at startup, encrypting all their data.

The LockBit Black used in this attack is probably based on LockBit 3.0, which leaked to the network in September 2022. However, the current campaign is not linked to the original LockBit grouping.
Emails are sent from more than 1,500 unique IP addresses around the world, including Kazakhstan, Uzbekistan, Iran, Russia, and China.
The attack begins when the recipient opens a malicious ZIP archive and runs the executable file. This file downloads LockBit Black from the Phorpiex botnet infrastructure and executes it on the victim's system. Ransomware steals confidential data, shuts down some system services, and encrypts files.
Proofpoint, which has been investigating these attacks since April 24, reported that the attackers targeted companies in various industries around the world. Despite the low complexity of the operation, its scale and the use of ransomware as the initial malicious load make this malicious campaign stand out qualitatively.
"Since April 24 and during the week, Proofpoint has observed large-scale campaigns with millions of messages distributed through the Phorpiex botnet and delivering LockBit Black," Proofpoint researchers said. "This is the first time that we have seen such volumes of LockBit Black delivery via Phorpiex."
The Phorpiex botnet, also known as Trik, has been active for over a decade. Initially, it was a worm that spread through USB devices, Skype chats, and Windows Live Messenger, and then turned into a Trojan controlled via IRC and spreading spam.
Over time, the botnet significantly increased in quantity, controlling more than a million infected devices, but then its infrastructure was disabled, after which the source code of the project was put up for sale. One of the authors of the botnet called the reason for the sale a shift in the interests of developers who are more disinterested in supporting and developing Phorpiex.
Previously, the Phorpiex botnet was also used to send millions of emails with threats and spam, as well as to introduce a malicious module that replaces cryptocurrency addresses in the Windows clipboard with those controlled by attackers.
To protect against phishing attacks, NJCCIC recommends using risk mitigation strategies, endpoint protection solutions, and email filtering.

