Father
Professional
- Messages
- 2,602
- Reaction score
- 838
- Points
- 113
Content:
There are two main types of online fraud aimed at stealing users ' data and money-phishing and scam. Phishing is primarily a malicious technique designed to trick the victim into revealing confidential information, such as credentials or bank card details. A scam is a scam in which a user is persuaded by social engineering to transfer money to attackers on their own.
Around the 90s, a scam also appeared. When banks began to actively implement Internet banking systems, fraudsters sent SMS messages to users allegedly from relatives with a request to urgently transfer money to the details specified in the message.
By the early 2000s, the topic of charity had become popular in the scam: for example, after the massive earthquake in the Indian Ocean in 2004, users began to receive letters from fake charities asking them to donate money to victims. At the same time, phishers switched to payment systems and online banks. Since then the accounts were protected only by a password, it was enough for attackers to extract it in order to gain access to other people's money. To do this, the criminals sent emails on behalf of PayPal and other companies, where they asked users to go to a fake site with the service's logo and enter their credentials. To make the sites look plausible, the attackers registered many domains that are very similar to the original one, with a difference of two or three letters. An inattentive user might have mistaken such a site for a real bank or payment system resource. Also, fraudsters often used personal information from victims ' social networks to make their attacks more targeted, and therefore more successful.
Subsequently, online fraud became more sophisticated and convincing. Cybercriminals have successfully imitated the official websites of brands, making them almost indistinguishable from the original, and find new tricks for their victims. Services for creating fraudulent content appeared, phishing began to be used "in a big way", directing their attacks not only on personal finances and data of ordinary users, but also on political figures and large businesses.
In this article, we will look at the main trends in phishing, techniques and techniques of scammers that have become relevant in 2022.
To extract the information they need, attackers make the victim believe that she enters data on the official website of the company or service she is a user of, or reports it to an employee of the company. Often, fake sites don't look any different from the original, and even an advanced user will find it hard to spot the catch. Phishers skillfully copy the layout and design of official sites, add additional details to their pages, such as a support chat (usually broken), so that they inspire more trust, and even pull up real service sites as a background.

Phishing site with a support chat
Recently, along with online phishing, vishing-phone phishing — has been actively developing. Fraudsters either call the victim themselves, or use various tricks to force her to call them and then use the phone to extort her personal data and money.

Fake message about problems with Windows, to solve which the victim is forced to call fraudsters on their own
Also relevant is targeted phishing, or spear phishing, which targets a specific person or organization. Targeted phishing emails and pages are more personalized than mass mailings, so it is very difficult to distinguish them from legitimate ones.
For example, in the screenshot below, the attackers claim that the victim won a smartphone and ask her to pay a small commission for sending the prize, as well as provide an email address, date of birth, gender, phone number and home address.

Questionnaire for collecting personal data for sending a smartphone that was allegedly won in the lottery
In most cases, fraudsters try to convince the victim that they are really going to send her a prize, but they do not save the data themselves. However, some scam sites can "remember" all the information entered on them. This is done so that in the future, for example, you can send malicious emails on behalf of the victim using their name and email address.
In addition to promising easy earnings and winning valuable prizes, scammers actively lure users to non-existent dating sites. For example, they send an invitation to chat with a link to a fraudulent resource and attach attractive photos to it. Once on the fake site, the user sees that on this particular day they can get premium access to the online dating platform almost for nothing. You just need to subscribe and pay a small fee.
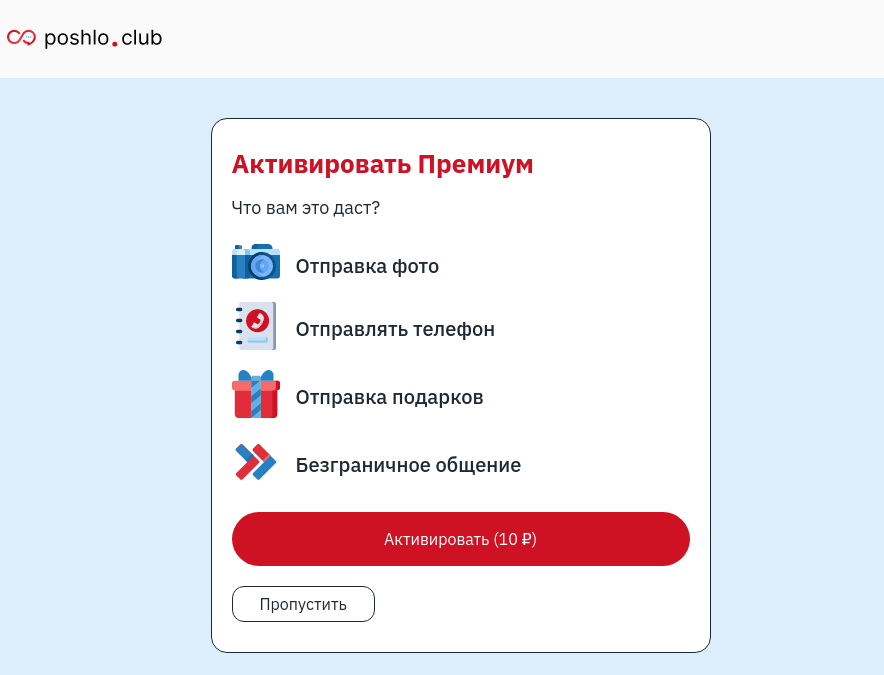
Offer to activate a premium account on a fake dating site
There are other ways to attract victims to scam sites: "selling" popular or even scarce goods, traveling with fellow travelers, and so on.In general, if something is popular with users, scammers can use it as bait.
In WhatsApp, a fraudulent message can come from both the cybercriminals themselves and from people in the victim's contact list. Attackers send messages on behalf of well-known brands or official bodies, but they do not disdain to involve users in the spread of fraud. In particular, to receive the gift promised in the message, they often require you to forward it to everyone or some of your friends.

Attackers force the victim to send a link to a fake prank to their WhatsApp contacts
Telegram has recently launched many channels that promise prize draws or get rich by investing in cryptocurrencies. In the chats of popular Telegram channels, too, you can often come across scammers who, under the guise of ordinary users, publish "favorable offers", for example, promise to help earn money. bots. To find out the secret of easy money, the user is asked to write a message to scammers or go to their channel.
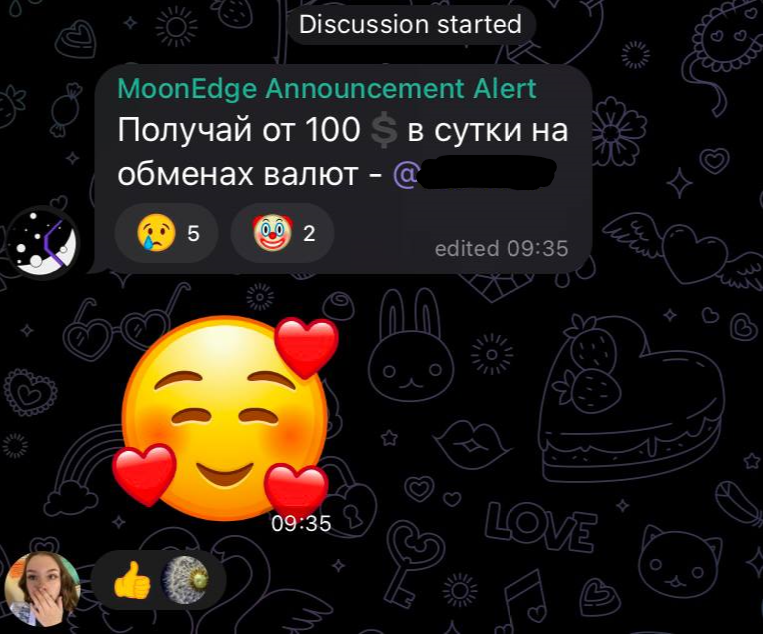
Comment in the Telegram channel chat promoting earnings on currency exchange

An Instagram account* that "plays" free smartphones
In addition, on marketplaces, scammers often comment on other users ' reviews of products, assuring potential buyers that this or that product can be bought much cheaper on another resource, and attaching a link to the scam site.
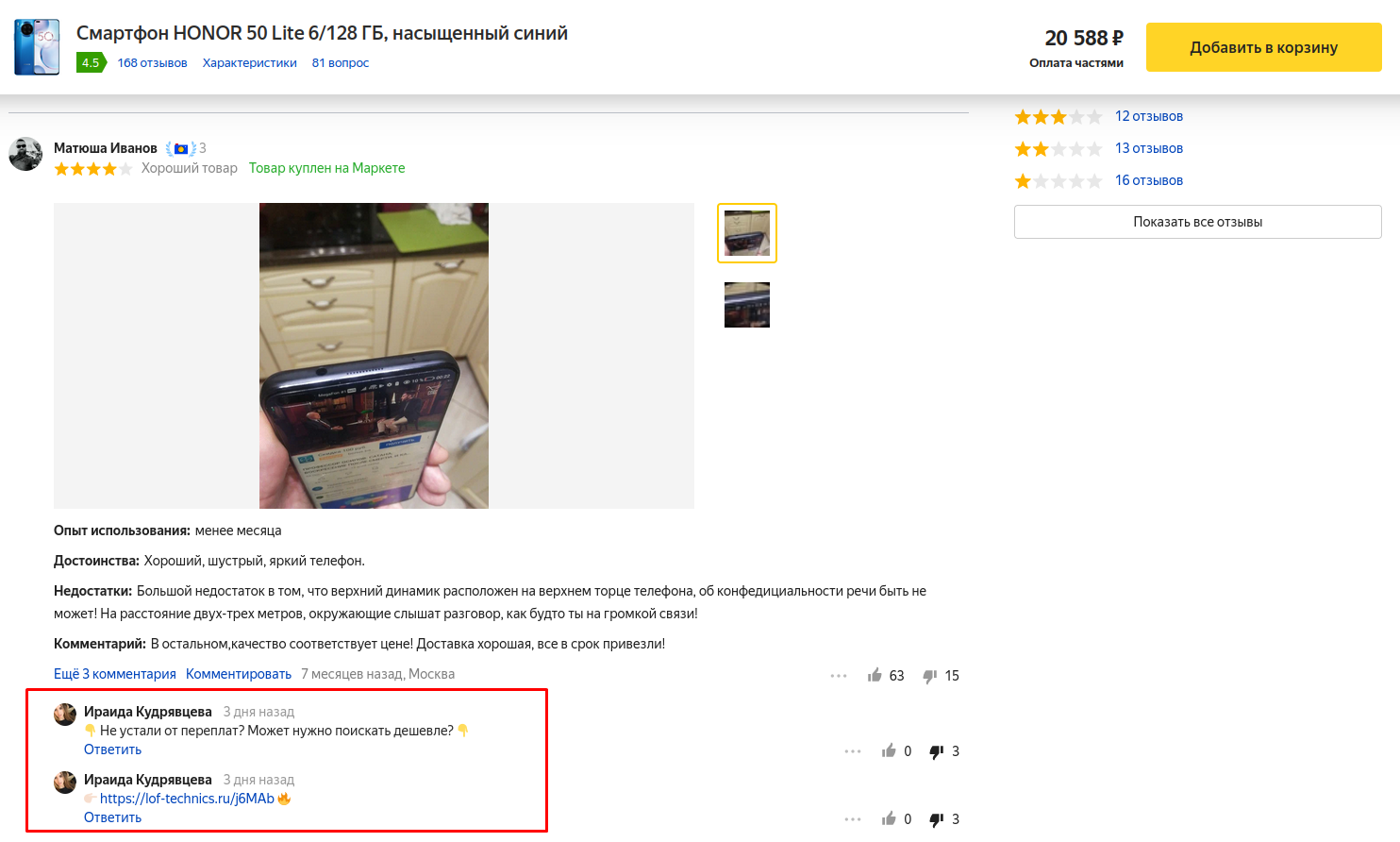
Scammers distribute links to scam sites under reviews of products purchased on marketplaces
Below are the main techniques that were encountered in phishing and scamming in 2022.
Domain spoofing involves registering a domain that is similar to the domain of the organization that the attackers are interested in. Phishers choose such domains so that the victim does not notice anything and does not consider the site suspicious. Domain spoofing can be divided into three types.

Distorted domain spelling Instagram.com, where the number 9 is used instead of the letter g
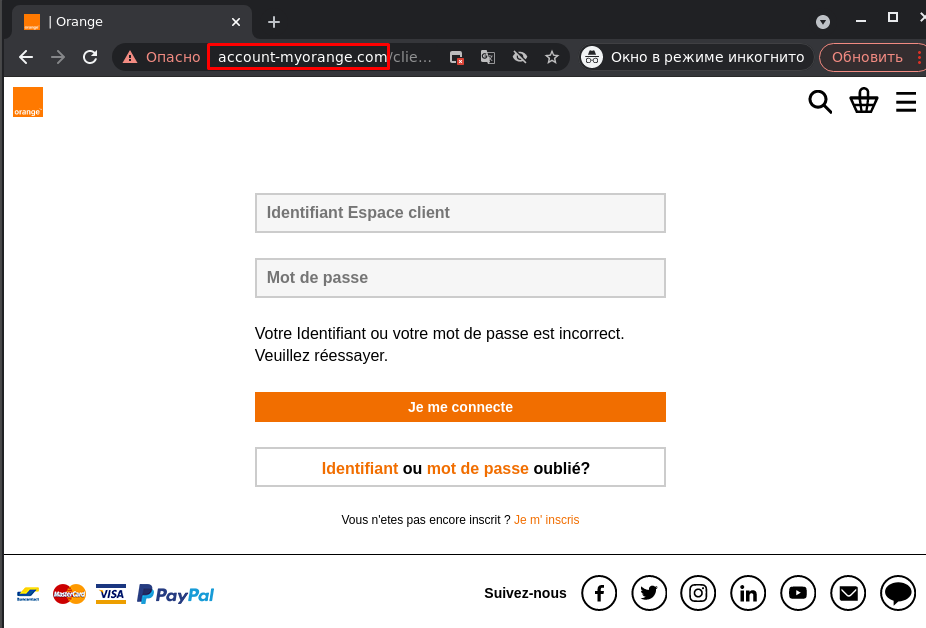
The word account has been added to the name of the bank in the domain

A legitimate site serves as a background for a phishing form
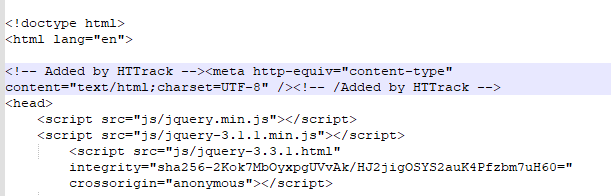
A comment in the HTML code of the phishing page indicating that the HTTrack program is being used
 [
[
An authorization form was created on the hacked site using an iFrame

The main page of the hacked site looks as usual

A phishing page was placed on the hacked site's subdirectory
For example, in the screenshot below, scammers under the guise of technical support for a popular crypto wallet lure users out of their identification data, such as an email address and a secret phrase, through a Google form.

Scammers try to extort confidential data using a Google form
Legitimate services eventually began to warn users that it is dangerous to pass passwords through their forms, and also implemented automatic protection, such as blocking forms containing certain keywords, such as "password" or password. And yet, thanks to the ability to massively create phishing questionnaires, attackers continue to use this method. To bypass the built-in protection, they often use text spoofing — they replace some of the characters in keywords with visually similar ones, for example, they write pa$$w0rd instead of password, making such words unrecognizable for automatic systems.
In addition to forms, attackers actively use cloud documents. In particular, they can send emails with a link to a document in a legitimate service that already contains a phishing link.
One of the methods of protection against detection is obfuscation, that is, distortion of the source code of the fraudulent page, which is invisible to the user, in order to make it difficult to detect the attack by automatic means. We discussed the types of obfuscation in detail in the article about the fish whale market.
Another way to protect a fraudulent site from detection is to use techniques that hide the page content from automatic analysis. Let's list some of them.
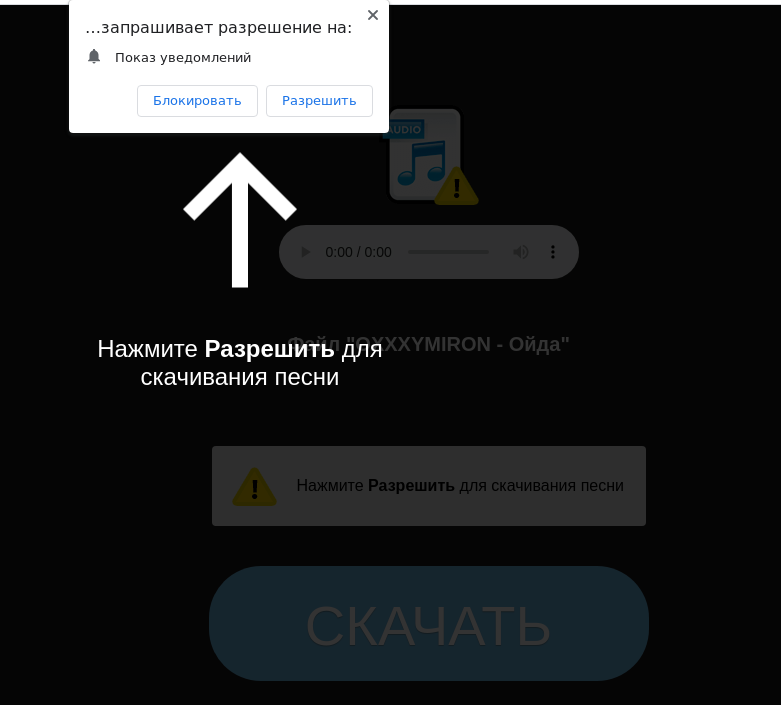
To download a song on a scam site, the user is asked to allow notifications in the browser from this resource[/CENTER]

Browser-in-browser attack: A pop-up window mimics a browser window with an address bar
In addition to the content, scammers try to hide the URLs of malicious sites from detection technologies. To do this, they can use the following.
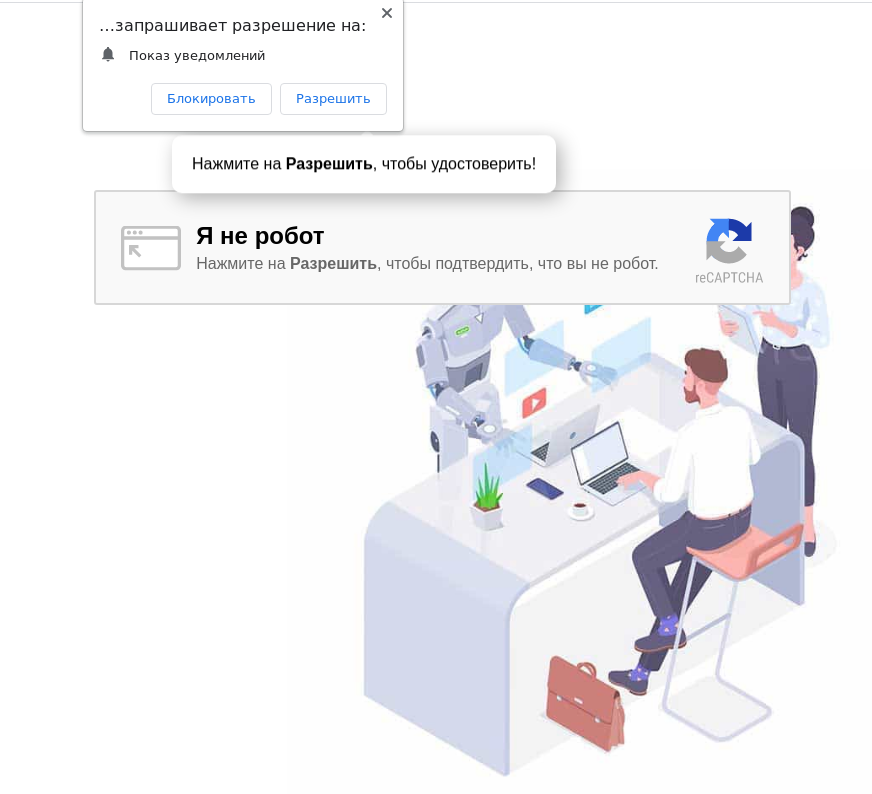
Fake CAPTCHA on a phishing page asking you to subscribe to browser notifications

Attackers use the victim's email domain to create content on a fraudulent site
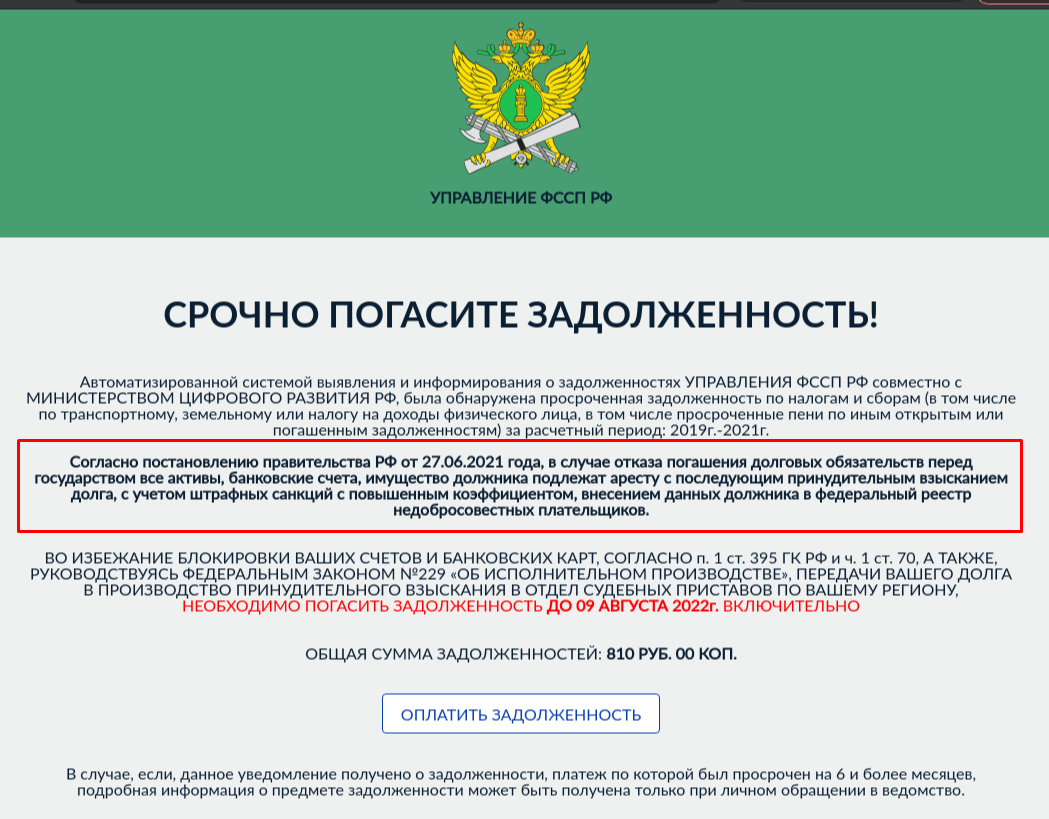
Scammers threaten to seize all the user's property and accounts if they don't pay off the fake debt.[/CENTER]

The scam site claims that the victim needs to urgently pay "COVID-19 related expenses" in order to receive the package

Attackers tempt users with a chance to win an Amazon gift card
At the same time, the number of cases of vishing is growing, because it is easier to put pressure on a person over the phone, leaving no time for reflection. At the same time, attackers use other available communication channels: email, popular instant messengers, social networks, and marketplaces.
Many methods are used to implement attacks, such as spoofing, social engineering, hacking sites, and hiding code and content. At the same time, methods of avoiding detection are also becoming more complex and evolving. Attackers are increasingly using one-time generated links with hashes to avoid being blocked by web threat detection technologies.
It is worth noting that scammers used and still use the most relevant topics as the reason for a particular malicious campaign. If a major event is taking place somewhere, a problem occurs that affects a large number of people, or a particular service or technology is gaining popularity, then it is likely that attackers will try to use this for their own purposes. So, during the coronavirus pandemic, there were massive scam campaigns for "paying material assistance", and with the rise in prices for cryptocurrencies last year, many fraudulent schemes related to cryptocurrency appeared. Therefore, you should always be vigilant online, especially when it comes to money: As much as you'd like to believe in luck falling out of the sky, if something sounds too good to be true, it's probably a hoax.
(c) OLGA SVISTUNOVA
- Phishing and scam history
- Phishing and scam: current types of fraud
- Phishing
- Scam
- Distribution
- Instant Messengers
- Social network
- Marketplaces
- Malicious methods: what phishing and scam consist of
- Spoofing
- Hacking websites
- Using the functionality of legitimate services
- Protection against detection
- Elements of social engineering
- Conclusion
There are two main types of online fraud aimed at stealing users ' data and money-phishing and scam. Phishing is primarily a malicious technique designed to trick the victim into revealing confidential information, such as credentials or bank card details. A scam is a scam in which a user is persuaded by social engineering to transfer money to attackers on their own.
Phishing and scam history
The term "phishing" was first used in 1996, when cybercriminals attacked users of the largest Internet service provider at that time, America Online (AOL). Scammers sent messages on behalf of AOL employees and required users to confirm their accounts or provide payment details. This method of fishing out personal data still exists and, unfortunately, brings results.Around the 90s, a scam also appeared. When banks began to actively implement Internet banking systems, fraudsters sent SMS messages to users allegedly from relatives with a request to urgently transfer money to the details specified in the message.
By the early 2000s, the topic of charity had become popular in the scam: for example, after the massive earthquake in the Indian Ocean in 2004, users began to receive letters from fake charities asking them to donate money to victims. At the same time, phishers switched to payment systems and online banks. Since then the accounts were protected only by a password, it was enough for attackers to extract it in order to gain access to other people's money. To do this, the criminals sent emails on behalf of PayPal and other companies, where they asked users to go to a fake site with the service's logo and enter their credentials. To make the sites look plausible, the attackers registered many domains that are very similar to the original one, with a difference of two or three letters. An inattentive user might have mistaken such a site for a real bank or payment system resource. Also, fraudsters often used personal information from victims ' social networks to make their attacks more targeted, and therefore more successful.
Subsequently, online fraud became more sophisticated and convincing. Cybercriminals have successfully imitated the official websites of brands, making them almost indistinguishable from the original, and find new tricks for their victims. Services for creating fraudulent content appeared, phishing began to be used "in a big way", directing their attacks not only on personal finances and data of ordinary users, but also on political figures and large businesses.
In this article, we will look at the main trends in phishing, techniques and techniques of scammers that have become relevant in 2022.
Phishing and scam: current types of fraud
Phishing
Phishing targets credentials in absolutely any Internet service: a bank, a social network, a government portal, an online store, a postal service, a delivery service, and so on. However, users of the most famous brands are most often at risk, because more people trust and use their services, and therefore the probability of a successful attack is higher.To extract the information they need, attackers make the victim believe that she enters data on the official website of the company or service she is a user of, or reports it to an employee of the company. Often, fake sites don't look any different from the original, and even an advanced user will find it hard to spot the catch. Phishers skillfully copy the layout and design of official sites, add additional details to their pages, such as a support chat (usually broken), so that they inspire more trust, and even pull up real service sites as a background.

Phishing site with a support chat
Recently, along with online phishing, vishing-phone phishing — has been actively developing. Fraudsters either call the victim themselves, or use various tricks to force her to call them and then use the phone to extort her personal data and money.

Fake message about problems with Windows, to solve which the victim is forced to call fraudsters on their own
Also relevant is targeted phishing, or spear phishing, which targets a specific person or organization. Targeted phishing emails and pages are more personalized than mass mailings, so it is very difficult to distinguish them from legitimate ones.
Scam
If phishing is also aimed at businesses, then the scam in most cases poses a threat to ordinary Internet users. Most often in scam schemes, the victim is promised a lot of money, a valuable prize, or something free or with a huge discount. The main purpose of fraudsters in this case is to get rich, but they can also collect personal data of the victim, which they can later sell or use in other schemes.For example, in the screenshot below, the attackers claim that the victim won a smartphone and ask her to pay a small commission for sending the prize, as well as provide an email address, date of birth, gender, phone number and home address.

Questionnaire for collecting personal data for sending a smartphone that was allegedly won in the lottery
In most cases, fraudsters try to convince the victim that they are really going to send her a prize, but they do not save the data themselves. However, some scam sites can "remember" all the information entered on them. This is done so that in the future, for example, you can send malicious emails on behalf of the victim using their name and email address.
In addition to promising easy earnings and winning valuable prizes, scammers actively lure users to non-existent dating sites. For example, they send an invitation to chat with a link to a fraudulent resource and attach attractive photos to it. Once on the fake site, the user sees that on this particular day they can get premium access to the online dating platform almost for nothing. You just need to subscribe and pay a small fee.

Offer to activate a premium account on a fake dating site
There are other ways to attract victims to scam sites: "selling" popular or even scarce goods, traveling with fellow travelers, and so on.In general, if something is popular with users, scammers can use it as bait.
Distribution
Most phishing and scam attacks start with sending emails with links to fraudulent sites, but today we can talk about the growing popularity of alternative attack vectors. There are many different services for communication and information exchange, which attackers also use to spread phishing links.Instant Messengers
One of the most important vectors for spreading phishing and scam threats is messengers such as WhatsApp and Telegram.In WhatsApp, a fraudulent message can come from both the cybercriminals themselves and from people in the victim's contact list. Attackers send messages on behalf of well-known brands or official bodies, but they do not disdain to involve users in the spread of fraud. In particular, to receive the gift promised in the message, they often require you to forward it to everyone or some of your friends.

Attackers force the victim to send a link to a fake prank to their WhatsApp contacts
Telegram has recently launched many channels that promise prize draws or get rich by investing in cryptocurrencies. In the chats of popular Telegram channels, too, you can often come across scammers who, under the guise of ordinary users, publish "favorable offers", for example, promise to help earn money. bots. To find out the secret of easy money, the user is asked to write a message to scammers or go to their channel.

Comment in the Telegram channel chat promoting earnings on currency exchange
Social network
Comments that offer easy profit can also be found in social networks, for example, under photos in popular accounts, where the probability that the message will be read is higher than on a page with a small number of subscribers. Attackers offer to follow the link in the profile header, write them a private message or join a secret group chat. In their correspondence, they will also be given a link to a phishing or scam site. Posts with the promise of a well-paid part-time job and a link to a mini-app are also common on VKontakte. In addition, in social networks, cybercriminals can write personal messages to users themselves, conduct promotional campaigns for their offers, and create fake accounts that promise to distribute valuable gifts, game coins, and gift cards. The latter are promoted using ads, hashtags, or mass marks of users in posts, comments, or photos.
An Instagram account* that "plays" free smartphones
Marketplaces
Marketplaces act as an intermediary between the user and the seller and, to a certain extent, ensure the security of the transaction for both parties. However, their functionality is also abused by scammers. For example, on Russian marketplaces, a very common scheme is when a seller for one reason or another does not want to communicate on the site and tries to transfer correspondence to third-party messengers. There, they can send the user a malicious link without fear of running into the built-in protection of the marketplace.In addition, on marketplaces, scammers often comment on other users ' reviews of products, assuring potential buyers that this or that product can be bought much cheaper on another resource, and attaching a link to the scam site.

Scammers distribute links to scam sites under reviews of products purchased on marketplaces
Malicious methods: what phishing and scam consist of
To implement their attacks, attackers use a variety of technical and psychological tricks that allow them to win over as many users as possible and at the same time reduce the risk of detection to a minimum.Below are the main techniques that were encountered in phishing and scamming in 2022.
Spoofing
Fraudsters often try to make the fake resource as similar as possible to the original one in order to increase the victim's level of trust in it. This technique is called spoofing. In the context of website spoofing, there are two main types of spoofing:- domain spoofing — forgery of the site's domain name;
- content spoofing is an imitation of the appearance of a legitimate site.
Domain spoofing involves registering a domain that is similar to the domain of the organization that the attackers are interested in. Phishers choose such domains so that the victim does not notice anything and does not consider the site suspicious. Domain spoofing can be divided into three types.
- Typesquatting — using the original domain name with typos, such as missing letters, extra characters, replacing one or two characters, or rearranging them.

Distorted domain spelling Instagram.com, where the number 9 is used instead of the letter g
- Combosquatting — using the name of the brand whose users are being targeted in the domain name, combined with additional words that are often related to authorization or network security. For example, it can be words such as login, secure, account, verify, and so on.

The word account has been added to the name of the bank in the domain
- IDN Homographs (Internationalized Domain NameHomograph — - writing fake site names using UTF table characters that are very similar to the Latin alphabet. For example, the most commonly used Cyrillic letters are a, c, e, o, p, x, y, which look identical to the Latin a, c, e, o, p, x, y.
- Legal IFrame Background — use an iFrame to load a legitimate site on a fraudulent resource, and then add a phishing form on top of it.

A legitimate site serves as a background for a phishing form
- HTML Spoofing is a visual imitation of a legitimate website, including by partially copying styles and HTML code. Often, scammers use software to create site mirrors, such as HTTrack and Website Downloader.

A comment in the HTML code of the phishing page indicating that the HTTrack program is being used
Hacking websites
Sometimes it's easier for scammers to hack into other people's sites to host malicious content than to create their own sites from scratch. Such phishing pages do not last long, as resource owners quickly detect and remove fraudulent content, as well as regularly cover up loopholes and fix vulnerabilities in their infrastructure. On the other hand, if attackers break into an abandoned site, phishing pages placed on it can survive for a long time. Phishers can use hacked sites in several ways.- iFrame Injection-inserting an authorization form or other part of a phishing page through an iFrame. While in the Legal IFrame Background method, fraudsters use an iFrame with a legal site as the background for a phishing form, in this case the page URL is legitimate, and the phishing form is loaded through the iFrame, which is most often self-made content using brand symbols.

An authorization form was created on the hacked site using an iFrame
- Subfolder Hijacking — partial hacking of a site and gaining access to its subdirectories to place fraudulent content on them. In such an attack, fraudsters can either use existing directories on a legitimate site, or create new ones.

The main page of the hacked site looks as usual

A phishing page was placed on the hacked site's subdirectory
- Site Swapping — a complete replacement of a legitimate site with a fraudulent one. The original content is most often deleted.
Using the functionality of legitimate services
Some Internet scammers do not bother to create or hack websites, but use the functions of services trusted by users for their own purposes. For example, a large number of attacks occur using forms for conducting surveys and collecting data (Google Forms, MS Forms, HubSpot Form Builder, Typeform, Zoho Forms, etc.).For example, in the screenshot below, scammers under the guise of technical support for a popular crypto wallet lure users out of their identification data, such as an email address and a secret phrase, through a Google form.

Scammers try to extort confidential data using a Google form
Legitimate services eventually began to warn users that it is dangerous to pass passwords through their forms, and also implemented automatic protection, such as blocking forms containing certain keywords, such as "password" or password. And yet, thanks to the ability to massively create phishing questionnaires, attackers continue to use this method. To bypass the built-in protection, they often use text spoofing — they replace some of the characters in keywords with visually similar ones, for example, they write pa$$w0rd instead of password, making such words unrecognizable for automatic systems.
In addition to forms, attackers actively use cloud documents. In particular, they can send emails with a link to a document in a legitimate service that already contains a phishing link.
Protection against detection
Fraudsters can use various techniques to protect themselves from detection. Some of them are quite effective, but they are not so common, as they require scammers to have deeper technical knowledge than many of them have.One of the methods of protection against detection is obfuscation, that is, distortion of the source code of the fraudulent page, which is invisible to the user, in order to make it difficult to detect the attack by automatic means. We discussed the types of obfuscation in detail in the article about the fish whale market.
Another way to protect a fraudulent site from detection is to use techniques that hide the page content from automatic analysis. Let's list some of them.
- Using images. If images with text are placed on the page instead of text, content engines will not be able to see and analyze the text, but users will read it.
- Notifications in the browser. Links to fraudulent resources can be distributed in browser notifications. Unlike emails and open web pages, browser notifications are processed in several stages, and not all anti-phishing engines analyze them. Accordingly, attackers can bypass at least some of the detection technologies in this way.

To download a song on a scam site, the user is asked to allow notifications in the browser from this resource[/CENTER]
- Pop-up windows. Fraudulent content opens in the site's pop-up window. Pop-ups are loaded later than the main window of the site, so they are also not seen by all anti-phishing technologies. In addition, pop-up windows give attackers additional tools to copy the appearance of a legitimate site. In particular, attackers can use the "Browser - in-the-Browser" method, when a pop-up window simulates a browser window with an address bar containing the URL of a legitimate site.

Browser-in-browser attack: A pop-up window mimics a browser window with an address bar
In addition to the content, scammers try to hide the URLs of malicious sites from detection technologies. To do this, they can use the following.
- Generated URLs-links are formed randomly using hashes. Each victim receives a unique link, which makes it difficult to block the malicious site.
- Short Link Services-attackers can mask the addresses of malicious resources using legitimate URL shortening services, such as bit.ly.
Elements of social engineering
Cybercriminals tricks often target people rather than information security vulnerabilities. Scammers use their knowledge of human psychology to deceive their victims. They can use both technical and purely psychological techniques to win the victim over.- Fake CAPTCHA-attackers imitate CAPTCHA technology on a fraudulent resource in order to convince the victim to perform an action of interest to them.

Fake CAPTCHA on a phishing page asking you to subscribe to browser notifications
- User-Related Dynamic Content — the page content changes depending on the user's data, such as their email address: for the domain, images are loaded from yandex. mail and inserted on the phishing page.

Attackers use the victim's email domain to create content on a fraudulent site
- Bullying and threats — attackers threaten the victim to make her lose her composure and commit actions of interest to them. For example, they may threaten legal prosecution and demand to "pay a fine" so that the victim is left alone. Attackers can also threaten to block your account in order to force the victim to click on a phishing link.

Scammers threaten to seize all the user's property and accounts if they don't pay off the fake debt.[/CENTER]
- Urgency. Attackers leave the recipient a limited amount of time to respond to their message in some way. This should make the victim act hastily and thoughtlessly.

The scam site claims that the victim needs to urgently pay "COVID-19 related expenses" in order to receive the package
- Pressure on pity. Malefactors try to arouse the victim's sympathy and, as a result, willingness to give money.
- A promise of benefits. Scammers entice the victim with incredibly profitable offers that are difficult to refuse.

Attackers tempt users with a chance to win an Amazon gift card
Conclusion
Most users are now more or less aware of current web threats. Many people have either experienced fraud on the Internet themselves, or learned about it from the news or other sources, so it is becoming increasingly difficult for attackers to gain the trust of their victims and new sophisticated techniques and tricks are being used. Instead of phishing and scam sites made "on the knee", high-quality fakes are increasingly common, such as imitating a browser window with the address of a legitimate site in a pop-up window or phishing pages with a legitimate site on the background loaded via an iFrame. We also see elements of targeted attacks in phishing and scams, such as downloading content related to the victim's email domain, or using data from major leaks to establish contact with them.At the same time, the number of cases of vishing is growing, because it is easier to put pressure on a person over the phone, leaving no time for reflection. At the same time, attackers use other available communication channels: email, popular instant messengers, social networks, and marketplaces.
Many methods are used to implement attacks, such as spoofing, social engineering, hacking sites, and hiding code and content. At the same time, methods of avoiding detection are also becoming more complex and evolving. Attackers are increasingly using one-time generated links with hashes to avoid being blocked by web threat detection technologies.
It is worth noting that scammers used and still use the most relevant topics as the reason for a particular malicious campaign. If a major event is taking place somewhere, a problem occurs that affects a large number of people, or a particular service or technology is gaining popularity, then it is likely that attackers will try to use this for their own purposes. So, during the coronavirus pandemic, there were massive scam campaigns for "paying material assistance", and with the rise in prices for cryptocurrencies last year, many fraudulent schemes related to cryptocurrency appeared. Therefore, you should always be vigilant online, especially when it comes to money: As much as you'd like to believe in luck falling out of the sky, if something sounds too good to be true, it's probably a hoax.
(c) OLGA SVISTUNOVA

