Father
Professional
- Messages
- 2,602
- Reaction score
- 837
- Points
- 113
Corporate networks have fallen victim to new methods of attacks by North Korean hackers.
North Korean hackers used the eScan antivirus update mechanism to place bookmarks in corporate networks and distribute cryptocurrency miners using the GuptiMiner malware.
The Avast reports that the attackers used an AITM attack (adversary-in-the-middle, AitM attack) to intercept the standard virus definition update package and replace it with a malicious file (updll62.dlz), which contains both antivirus updates and the GuptiMiner cryptominer in the form of a DLL library (version.dll).
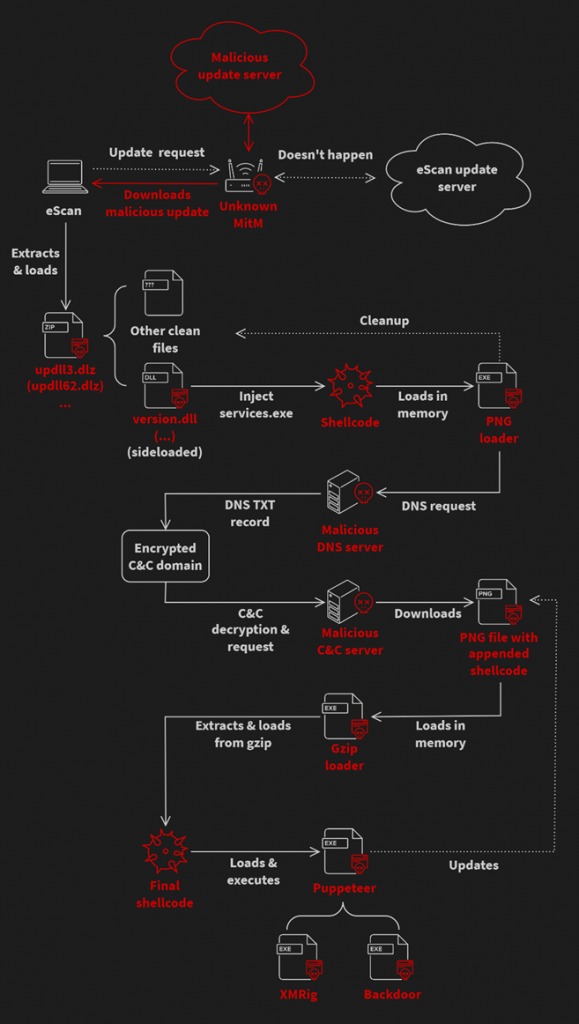
GuptiMiner Infection Chain
After unpacking and executing the service pack, the DLL file is loaded via legitimate eScan binaries, which gives the malware system privileges. The DLL then loads additional malicious modules, provides resilience on the infected host, manipulates DNS, inserts shellcode into legitimate processes, and performs other actions, including encrypting data in the Windows registry and extracting executable files from PNG images.
GuptiMiner also checks whether the system has more than 4 CPU cores and 4 GB of RAM to avoid sandboxing, and determines whether Wireshark, WinDbg, TCPView, 360 Total Security, Huorong Internet Security, Process Explorer, Process Monitor, and OllyDbg analyzers are active.
The researchers note that GuptiMiner may be linked to the North Korean hacker group Kimsuky. Among other things, the use of the domain "mygamesonline[.]org", which is often used in Kimsuky operations, was detected.
The report mentions that hackers deployed several types of malware, including two different backdoors and the Monero XMRig miner, which may be an attempt to divert attention from the main attack.
After disclosing the vulnerability, the manufacturer of the eScan antivirus software confirmed that the problem was resolved. eScan has also strengthened binary file authentication and switched to using encrypted HTTPS connections for updates.
Despite the improvements, Avast continues to detect new cases of GuptiMiner infection, which may indicate the use of outdated versions of eScan clients. A list of signs of GuptiMiner compromise that can help you defend against this threat is available on the GitHub page.
North Korean hackers used the eScan antivirus update mechanism to place bookmarks in corporate networks and distribute cryptocurrency miners using the GuptiMiner malware.
The Avast reports that the attackers used an AITM attack (adversary-in-the-middle, AitM attack) to intercept the standard virus definition update package and replace it with a malicious file (updll62.dlz), which contains both antivirus updates and the GuptiMiner cryptominer in the form of a DLL library (version.dll).

GuptiMiner Infection Chain
After unpacking and executing the service pack, the DLL file is loaded via legitimate eScan binaries, which gives the malware system privileges. The DLL then loads additional malicious modules, provides resilience on the infected host, manipulates DNS, inserts shellcode into legitimate processes, and performs other actions, including encrypting data in the Windows registry and extracting executable files from PNG images.
GuptiMiner also checks whether the system has more than 4 CPU cores and 4 GB of RAM to avoid sandboxing, and determines whether Wireshark, WinDbg, TCPView, 360 Total Security, Huorong Internet Security, Process Explorer, Process Monitor, and OllyDbg analyzers are active.
The researchers note that GuptiMiner may be linked to the North Korean hacker group Kimsuky. Among other things, the use of the domain "mygamesonline[.]org", which is often used in Kimsuky operations, was detected.
The report mentions that hackers deployed several types of malware, including two different backdoors and the Monero XMRig miner, which may be an attempt to divert attention from the main attack.
After disclosing the vulnerability, the manufacturer of the eScan antivirus software confirmed that the problem was resolved. eScan has also strengthened binary file authentication and switched to using encrypted HTTPS connections for updates.
Despite the improvements, Avast continues to detect new cases of GuptiMiner infection, which may indicate the use of outdated versions of eScan clients. A list of signs of GuptiMiner compromise that can help you defend against this threat is available on the GitHub page.

