Father
Professional
- Messages
- 2,602
- Reaction score
- 837
- Points
- 113
Several companies have already fallen victim to enterprising hackers.
At the beginning of 2024, the MorLock group became active in cyberspace, attacking enterprises using ransomware. In a short period of time, at least 9 large and medium-sized Russian companies were attacked. F. A. C. C. T. specialists described the group's tactics in a new report.
MorLock attackers use the LockBit 3.0 and Babuk ransomware programs, which is typical for other cybergroups, but thanks to unique tactics, techniques and procedures (TTPs), MorLock is able to distinguish among others. The group prefers to operate in secret, without showing any activity on cyberforums and social networks. Contacts for ransom are transmitted through encrypted communication channels (the Session messenger).
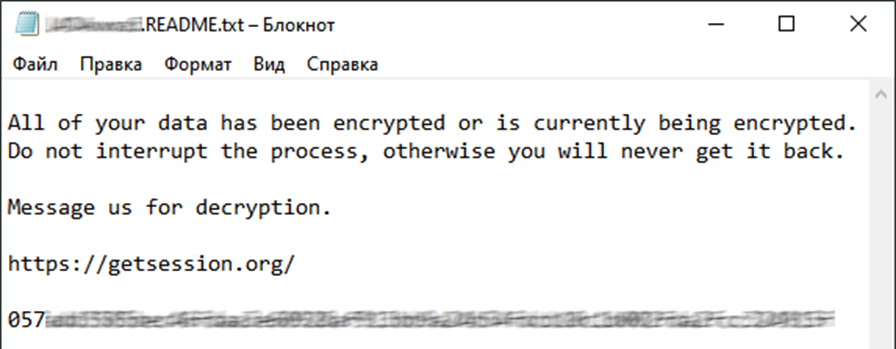
Ransom note
An interesting aspect of MorLock's work is the lack of data exfiltration before encryption, which reduces the attack time and reduces the chances of preventing an incident. In cases of a successful attack, the victim companies face ransom demands, which can reach hundreds of millions of rubles.
As an initial attack vector, MorLock often exploits vulnerabilities in publicly available applications, such as Zimbra, or compromised credentials purchased on closed trading platforms. For further distribution of malware in victim networks, tools are used – Sliver for post-exploitation and SoftPerfect Network Scanner for network intelligence. Some tools were downloaded by cybercriminals to hosts directly from official sites using the victim's web browser.
Another feature of MorLock is that if there is a "popular Russian corporate antivirus" on the victim's network, the attackers gain access to its administrative panel, disable protection, and use this vector to further spread malware.
MorLock's tools and methods are constantly evolving, and the list of compromise indicators is publicly available on GitHub, which allows IT professionals and victim companies to quickly respond to threats.
At the beginning of 2024, the MorLock group became active in cyberspace, attacking enterprises using ransomware. In a short period of time, at least 9 large and medium-sized Russian companies were attacked. F. A. C. C. T. specialists described the group's tactics in a new report.
MorLock attackers use the LockBit 3.0 and Babuk ransomware programs, which is typical for other cybergroups, but thanks to unique tactics, techniques and procedures (TTPs), MorLock is able to distinguish among others. The group prefers to operate in secret, without showing any activity on cyberforums and social networks. Contacts for ransom are transmitted through encrypted communication channels (the Session messenger).

Ransom note
An interesting aspect of MorLock's work is the lack of data exfiltration before encryption, which reduces the attack time and reduces the chances of preventing an incident. In cases of a successful attack, the victim companies face ransom demands, which can reach hundreds of millions of rubles.
As an initial attack vector, MorLock often exploits vulnerabilities in publicly available applications, such as Zimbra, or compromised credentials purchased on closed trading platforms. For further distribution of malware in victim networks, tools are used – Sliver for post-exploitation and SoftPerfect Network Scanner for network intelligence. Some tools were downloaded by cybercriminals to hosts directly from official sites using the victim's web browser.
Another feature of MorLock is that if there is a "popular Russian corporate antivirus" on the victim's network, the attackers gain access to its administrative panel, disable protection, and use this vector to further spread malware.
MorLock's tools and methods are constantly evolving, and the list of compromise indicators is publicly available on GitHub, which allows IT professionals and victim companies to quickly respond to threats.

