Lord777
Professional
- Messages
- 2,577
- Reaction score
- 1,556
- Points
- 113
Many of those who read this at least once heard about "logs", first let's figure out what it is in general:
Log - a unit of user data, roughly speaking your log is your entire life on the Internet, all your passwords, logins, cookies, browser history(in some cases including incognito) is reflected in this very log. So most likely, if you've watched porn, the lair owner will see this porn in your story.
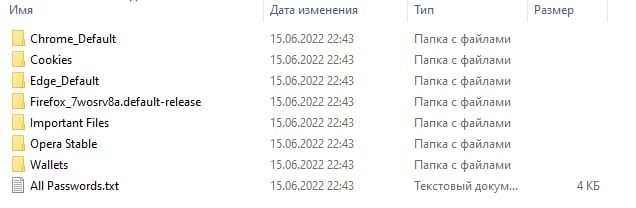
Random person's log
But what is so valuable about your usernames and passwords? In general, nothing, most of you in our work simply will not be useful, we do not need your VK contacts where you correspond with your girls, we are specific guys and we have specific sharavars for money, we need guys who have cash.
virus.exe = 123456
program.exe = 56789
[*]stealer.exe = 98765
[*]When you get a zombie vs plants file on your computer.if the antivirus understands that the only plant is the host of the computer, and calculates its hash, and its hash is 123456, the antivirus checks it with its database, and finds out that this is the name of the file virus.exe after that, another user (who was less lucky and the antivirus didn't know about the virus YET) fucked up the computer. And issues a warning to the user. Thus, as you do not change the file name, as you do not change the icon, if you are fired up - you will have to rebuild the file, or resort to cryptors
[/LIST]
Cryptors are the Biggest Hoax
A normal cryptor can change the same hash of the virus (build. Build file of the virus) from the same tables. But even this does not save from "palev" antiviruses in the future. It's all about the runtime analysis of modern antivirus programs. I will try to tell you in simple words what it is, so, we have the file " open.exe", it is encrypted, when it hits the computer, the antivirus does not swear at it because it did not find its signatures in the database(because it is encrypted again), everything is OK, but then there is such a chain of actions that sends most cryptors to a knockout:
But why does everyone use cryptors? They're useless!
Cryptors are useless, but only partially. The fact is that not all users have the "cloud analysis"feature enabled in the same Windows Defender(our runtime analysis). For example, if we infected 1000 users, 500 of them do not have antivirus software at all, because: "do you need it??? I'm fucking smart myself without any of your antivirus programs", 400 have the ability to run-time analysis disabled, because files open longer with it, and only 901 users have an antivirus and run-time analysis is enabled, EXACTLY BEFORE THIS USER, the VIRUS IS ELUSIVE! And cryptor helped us with this! But after 901 users, whose antivirus software has burned down that the virus is a virus, the file will not start for 902, even if the runtime analysis option is disabled. So, the user who has everything turned on is called the last patient)))) then, after it, the build will start only for those users who do not have antivirus programs, this does not happen immediately, in practice, after 901 users, another 200-300 people are quietly infected, before the virus is completely flooded with detectors.
Log - a unit of user data, roughly speaking your log is your entire life on the Internet, all your passwords, logins, cookies, browser history(in some cases including incognito) is reflected in this very log. So most likely, if you've watched porn, the lair owner will see this porn in your story.

Random person's log
But what is so valuable about your usernames and passwords? In general, nothing, most of you in our work simply will not be useful, we do not need your VK contacts where you correspond with your girls, we are specific guys and we have specific sharavars for money, we need guys who have cash.
But where do the logs come from?
Logs are obtained by means of stealers (read a virus that steals data), the stiller can be "picked up" when downloading crack on Photoshop, on porn sites, on pirated games, so be careful with such things. Most of those who read this will never pick up a serious stiller, for a very simple reason, serious stealers do not work in the CIS, you can pick up crafts of some schoolchildren and students, serious products, for example mars, do not work in the CIS.How to hide stillers (viruses)
Now each of us has an antivirus, most of them have the most powerful representative - Windows Defender (code name mssec), the most powerful because it is installed on every Windows user(10+), and on sevens its neutered version, or other antiviruses (Kaspersky, etc.), regardless of what it is installed on each microwave has the largest antivirus sample database. But even this does not help antivirus programs. It's all about cryptors, a good cryptor is able to change the signature of the sample and the virus becomes "clean" for the antivirus database, signature analysis (also called scantime) in a simplified form works like this:- to the file virus.exe its identification number is assigned in the antivirus system, for example, 123456
virus.exe = 123456
program.exe = 56789
[*]stealer.exe = 98765
[*]When you get a zombie vs plants file on your computer.if the antivirus understands that the only plant is the host of the computer, and calculates its hash, and its hash is 123456, the antivirus checks it with its database, and finds out that this is the name of the file virus.exe after that, another user (who was less lucky and the antivirus didn't know about the virus YET) fucked up the computer. And issues a warning to the user. Thus, as you do not change the file name, as you do not change the icon, if you are fired up - you will have to rebuild the file, or resort to cryptors
[/LIST]
Cryptors are the Biggest Hoax
A normal cryptor can change the same hash of the virus (build. Build file of the virus) from the same tables. But even this does not save from "palev" antiviruses in the future. It's all about the runtime analysis of modern antivirus programs. I will try to tell you in simple words what it is, so, we have the file " open.exe", it is encrypted, when it hits the computer, the antivirus does not swear at it because it did not find its signatures in the database(because it is encrypted again), everything is OK, but then there is such a chain of actions that sends most cryptors to a knockout:
- You are opening the file "открой.ехе"
- The antivirus intercepts the open event, and then puts it in a special isolated area in its memory(a virtual machine inside the antivirus) and looks at what it does, checks its behavior. This type of analysis is called runtime, or behavioral analysis in Russian
- Antivirus even before the file opens in your main machine detects that the file climbs into the password storage of Chrome, to sessions in Telegram, and immediately gives this behavioral fingerprint some kind of detector "Wacatac. B!ml" for example, by the way !ml at the end means that the detector is given by machine learning, in short, the detector issued artificial intelligence.
- Under the distribution immediately gets the hash of the stiller (remember those tables), as you can see, the cryptor did not help us, despite the fact that it provides FUD (Full undetected) antivirus programs in scanttime, which is also temporarily useful. For this reason, the crypt itself does not live long.
But why does everyone use cryptors? They're useless!
Cryptors are useless, but only partially. The fact is that not all users have the "cloud analysis"feature enabled in the same Windows Defender(our runtime analysis). For example, if we infected 1000 users, 500 of them do not have antivirus software at all, because: "do you need it??? I'm fucking smart myself without any of your antivirus programs", 400 have the ability to run-time analysis disabled, because files open longer with it, and only 901 users have an antivirus and run-time analysis is enabled, EXACTLY BEFORE THIS USER, the VIRUS IS ELUSIVE! And cryptor helped us with this! But after 901 users, whose antivirus software has burned down that the virus is a virus, the file will not start for 902, even if the runtime analysis option is disabled. So, the user who has everything turned on is called the last patient)))) then, after it, the build will start only for those users who do not have antivirus programs, this does not happen immediately, in practice, after 901 users, another 200-300 people are quietly infected, before the virus is completely flooded with detectors.

