Father
Professional
- Messages
- 2,602
- Reaction score
- 837
- Points
- 113
How legitimate tools can help you bypass antivirus programs.
Reports Trend Micro that the Chinese group Winnti (APT41) uses a new malware UNAPIMON, which allows hackers to remain undetected and bypass detection systems.
Winnti has been conducting cyber espionage campaigns since 2012, targeting a wide range of organizations around the world, including governments, hardware vendors, and software developers. Trend Micro links the detected cyber espionage campaign to a cluster dubbed "Earth Freybug".
Trend Micro notes a high level of sophistication of techniques in campaigns using UNAPIMON. The attack begins by injecting a malicious process into a legitimate process "vmtoolsd.exe" from VMware Tools, which performs a remote scheduled task to run a batch file that collects system information, including network configurations and user information.
Next, the DLL Sideloading method is used to load UNAPIMON into memory and inject it into the process "cmd.exe".
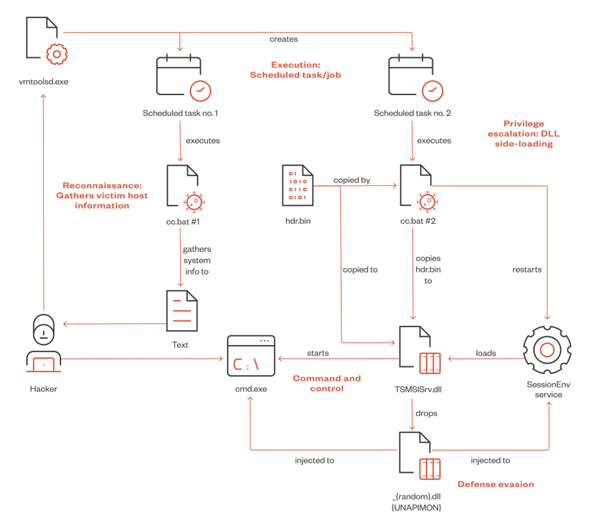
Winnti Attack Chain
UNAPIMON is a malicious C++ program delivered in DLL form that uses Microsoft workarounds to intercept the CreateProcessW API function, which allows the program to disable important API functions in child processes.
A special feature of UNAPIMON is the ability to bypass the interception of the API designed to track malicious activity, which makes UNAPIMON invisible to many security tools. This is achieved by modifying calls to the DLL creation, search, and replace process, as well as deleting temporary copies of the DLL to resume the main execution flow without detection.
The Trend Micro report highlights that the use of UNAPIMON is an example of a creative approach to malware development, demonstrating how simple and affordable technologies can be used for malicious purposes. For example, hackers use the official Microsoft debugging tool Detours to redirect any CreateProcessW calls from the process in which the DLL is loaded to an interceptor. This mechanism allows you to bypass behavior-based detection.
Trend Micro explains that most malware uses hooking to intercept calls, capture sensitive data, and change the behavior of the software. As such, UNAPIMON's uncoupling approach is an unusual method of evasion.
Reports Trend Micro that the Chinese group Winnti (APT41) uses a new malware UNAPIMON, which allows hackers to remain undetected and bypass detection systems.
Winnti has been conducting cyber espionage campaigns since 2012, targeting a wide range of organizations around the world, including governments, hardware vendors, and software developers. Trend Micro links the detected cyber espionage campaign to a cluster dubbed "Earth Freybug".
Trend Micro notes a high level of sophistication of techniques in campaigns using UNAPIMON. The attack begins by injecting a malicious process into a legitimate process "vmtoolsd.exe" from VMware Tools, which performs a remote scheduled task to run a batch file that collects system information, including network configurations and user information.
Next, the DLL Sideloading method is used to load UNAPIMON into memory and inject it into the process "cmd.exe".

Winnti Attack Chain
UNAPIMON is a malicious C++ program delivered in DLL form that uses Microsoft workarounds to intercept the CreateProcessW API function, which allows the program to disable important API functions in child processes.
A special feature of UNAPIMON is the ability to bypass the interception of the API designed to track malicious activity, which makes UNAPIMON invisible to many security tools. This is achieved by modifying calls to the DLL creation, search, and replace process, as well as deleting temporary copies of the DLL to resume the main execution flow without detection.
The Trend Micro report highlights that the use of UNAPIMON is an example of a creative approach to malware development, demonstrating how simple and affordable technologies can be used for malicious purposes. For example, hackers use the official Microsoft debugging tool Detours to redirect any CreateProcessW calls from the process in which the DLL is loaded to an interceptor. This mechanism allows you to bypass behavior-based detection.
Trend Micro explains that most malware uses hooking to intercept calls, capture sensitive data, and change the behavior of the software. As such, UNAPIMON's uncoupling approach is an unusual method of evasion.

