The content of the article
In fact, it was almost impossible to get into the signaling network in traditional telephony technologies. But progress does not stand still, and from the beginning of the XXI century IP-telephony began to gradually replace the traditional one. Any personal computer can now have several free programs installed, and then knowledge of the SS7 protocols and programming skills, multiplied by the time spent, turns this computer into a powerful criminal tool - it would be a fantasy.
A bit of theory
But before we let our imagination run wild, let's make a small digression and delve into the technology of mobile communications. In telephone networks, including mobile ones, subscriber (voice or data) and service traffic (for example, for establishing a connection) are clearly separated. In fact, service traffic is the very same signaling system No. 7, which includes a certain set of protocols, rules and messages.
When communicating between operators, nodes in mobile communications are addressed not by IP addresses, but by Global Title addresses, the format of which resembles telephone numbers. The Global Title addresses must be included in the range of telephone numbers assigned to the telecom operator, and if at the national level the ranges are divided by regions, then the Global Title addresses of the network nodes must correspond to the regional ranges.
We will not describe the entire SS7 protocol stack here. Suffice it to say that for the interaction of the nodes of the core of the mobile operator, the MAP protocol is used - Mobile Application Part. The MAP protocol is aimed at the implementation of functions inherent in mobile networks, such as authentication and registration of a mobile device in the network, localization of the subscriber for making an incoming call, and support for a continuous voice communication channel when the subscriber moves. Each operation corresponds to a specific MAP message with its own set of parameters. Various messages are mentioned below, and by default they will all belong to the MAP protocol.
We are used to using regular telephone numbers for mobile communications. In technical terms of mobile communications, these numbers are called MSISDN - Mobile Subscriber Integrated Services Digital Network Number. This number is assigned to a subscriber when concluding a contract with a mobile operator. But in the depths of the communications network, subscribers are addressed by another identifier - IMSI (International Mobile Subscriber Identity), which is tied to a specific SIM card. The overwhelming majority of operations require addressing the subscriber exactly by IMSI, therefore, in order to carry out most attacks aimed at a specific subscriber, an attacker first of all needs to find out this identifier.
It should also be noted that the SS7 protocols do not provide opportunities for providing such functions as node authentication, filtering messages by access lists, dynamic routing of new network nodes. All this allows a potential attacker to achieve their goals.
Attack options
Prelude.
So, we assume that the attacker gained access to the SS7 network and wants to conduct a series of attacks on you, the reader. We assume that the attacker knows the phone number of the victim subscriber. As mentioned earlier, the first step for an attacker is to obtain an IMSI that matches the victim's phone number. For a better understanding of the process, I propose now to distract from the attack itself and first see how one of the simplest services in mobile communications works - the Short Message Service, “SMS”.
How SMS messages flow
First of all, it should be noted that SMS messages in mobile networks "go" through signaling channels, completely without affecting the voice and packet traffic channels. For any transaction between two subscribers, there is a source and a receiver. The subscriber, sending an SMS message, indicates the recipient's phone number and enters the text. However, the service fields of the message contain the address of the SMS center: this node is responsible for routing SMS messages (and its address is specified in each phone in the SMS settings). The flow chart of the SMS message is shown in Fig. one.

Fig. 1. Scheme of SMS message flow
There are no accidents
Getting IMSI and other delights
So, with the help of a message, the SendRoutingInfoForSMSMS center receives the IMSI of the subscriber and the address of the serving switch by the phone number. If we assume that Alex and Boris are subscribers of different networks in the SMS message flow scheme, then we will find that the message SendRoutingInfoForSMtravels between networks (Fig. 2).
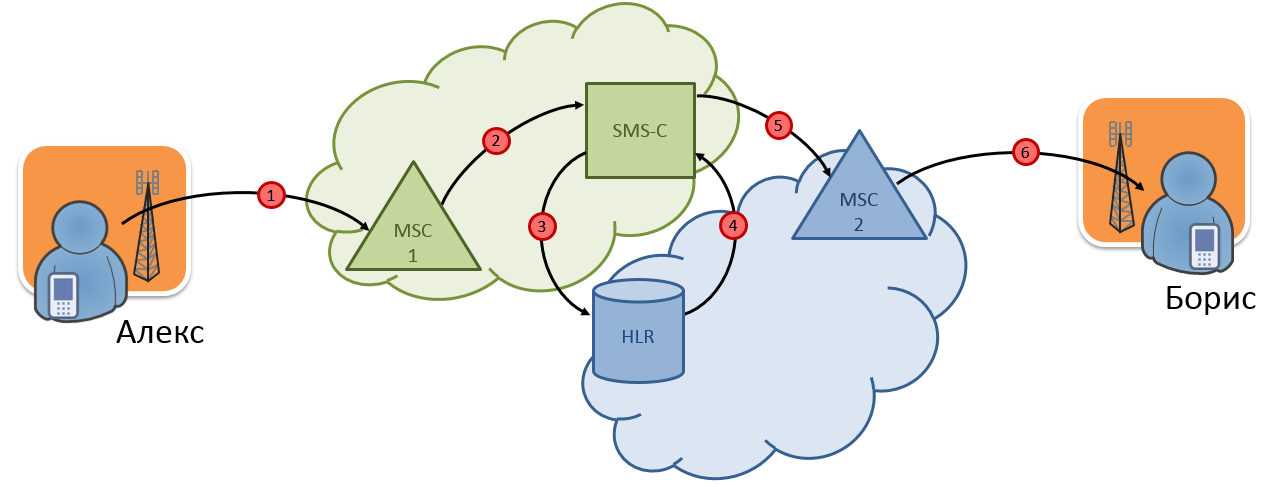
Fig. 2. Passage of SMS messages between networks
In order for the SMS center to make a request, it must "know" the HLR address of the foreign network. Although ... it's not really necessary. The SMS-center can send a message SendRoutingInfoForSMusing the recipient's subscriber's phone number as the Global Title. Since the Global Title addresses and telephone numbering are in the same range, the message will be delivered to the recipient's network, and then routed to the corresponding HLR via the telephone number. In the response message, HLR will disclose its address, and as parameters it will transmit the MSC address and IMSI of the subscriber.
As a result, it turns out that an attacker who has connected to the SS7 network can initially only know the number of the attacked subscriber to carry out his attacks. By sending the message SendRoutingInfoForSM, he will receive the HLR address, the MSC address and the IMSI of the subscriber.
Determining the location of the subscriber
Now let's move on to real attacks. The first thing that comes to mind is to determine where the subscriber is. Surely in the bowels of the mobile network there should be information about the current position of the subscriber. And in fact it is there, although its accuracy is not always the same. To clarify this issue, you will have to dive into communication technology again.
Structure of cellular networks
Everyone has seen antennas of base stations of cellular communications: in cities, they are dotted with almost all high-rise buildings. Outside urban areas, base station antennas are most often installed on special mast structures. Base stations provide radio coverage for the network, which ideally, of course, should be without blind spots. Base stations are connected to controllers - BSC (Base Station Controller) in the GSM standard and RNC (Radio Network Controller) in the UMTS standard. The controllers are connected to the MSC switch.
At the base station, as a rule, several antennas are installed, each of which covers its own sector, or cell. Each cell has a CID - Cell ID. Cells are grouped into groups called Location Area, and are identified by the LAC identifier - Location Area Code. Often, the Location Area includes all sectors whose base stations are connected to the same controller.
The identifier of the cell serving the subscriber at each point in time is stored in the controller's database. But controllers - both BSC and RNC - connect directly to the switch and have no connections to external networks. It is almost impossible to extract information from there.
Each MSC also has its own base - VLR (Visited Location Register), which stores information about all subscribers within the coverage area of this switch. There is even LAC and CID data for subscribers, but the CID value is updated only at the moment when the subscriber crosses the boundaries of the Location Area or performs any other active action. Although from a network point of view, changing information about a new LAC is the same activity as making a phone call.
A switch, unlike controllers, has a connection to external networks, and an attacker with access to SS7 can obtain information about the location of subscribers from its database.
Three-way
Now that we know how mobile networks are built, it will be easy for us to understand the attack technique. The first move absolutely repeats the steps for obtaining the IMSI of the subscriber and the address of the switch serving it. Let's repeat: this is done using a message SendRoutingInfoForSM(the attacker emulates the operation of the SMS center).
At this stage, it would be possible to immediately send a request to the switch database, but in this case we risk receiving not the most accurate information, since we cannot be sure whether the phone of a known subscriber performed any active actions in the cell where he is now. To know for sure, we need to force the subscriber's phone to perform similar actions, but this must be done so that the subscriber does not notice anything.
The standard for SMS messages implies the ability to form a message in such a way that it will be invisible to the subscriber, the so-called Silent SMS. The phone receives the message, but does not signal its receipt and does not display it in the list of received SMS.
On the second move, the attacker continues to emulate the operation of the SMS center. He sends a Silent SMS to the desired subscriber in a message MT-ForwardSM. The message itself is sent to the switch, the address of which was received in the first move, and the subscriber is addressed using IMSI. After passing this message, the information about the location of the subscriber in the switch base will be updated. It now contains information about the current LAC and CID.
There is very little left - to send a request to the switch to obtain data about the cell serving the subscriber. This is done by a message ProvideSubscriberInfothat is sent to the switch, the subscriber is addressed by IMSI. (As we remember, we already have both the switch address and the subscriber's IMSI.) In mobile networks, this message is used to transmit information about the location of the called subscriber for online billing. If the subscriber is in roaming, the corresponding charging scheme is activated.
The message ProvideSubscriberInforeturns the full set of serving cell identifiers: MCC - Mobile Country Code, MNC - Mobile Network Code, LAC, CID. There are many services on the Internet that allow for these four parameters to determine the geographic coordinates of the base station and even the approximate coverage area of the cell. In fig. 3 shows the result of determining my location at the time of this writing. The point marks the base station, and the building where I am sitting is indeed within the indicated circle.
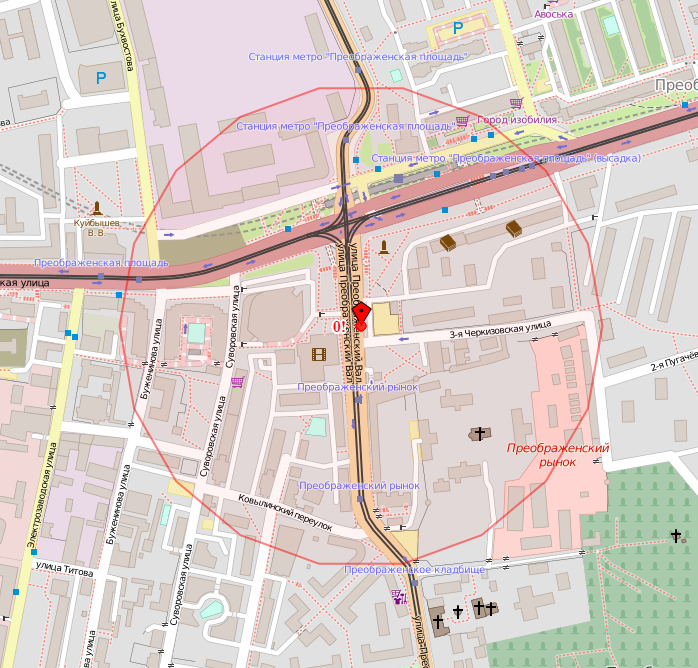
Fig. 3. Determining the location of the author of the article
Subscriber Availability Disruption (DoS)
The next attack is subscriber DoS. To understand the attack technique, let's again dive into the principles of mobile communication networks.
Subscriber registration in roaming
Consider the signal exchange and the main processes occurring in mobile networks when a subscriber leaves for another country and registers in the network of the operator's roaming partner (diagram in Fig. 4).
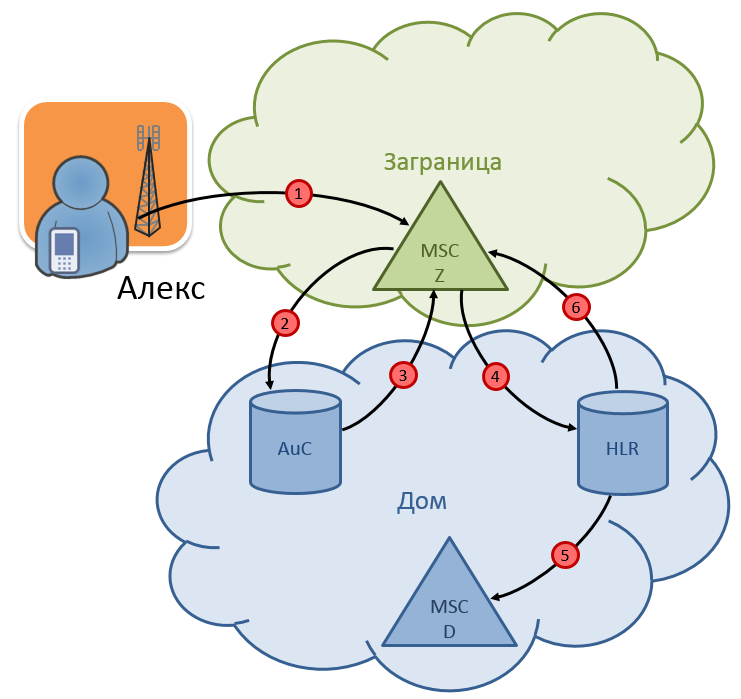
Fig. 4. Registration of the subscriber in the network of the roaming partner
Carrying out an attack
What remains for an attacker to do to send the subscriber to DoS for incoming calls? Just send a message UpdateLocationon behalf of the MSC to the subscriber's home network . The signal exchange diagram is shown in Fig. five.
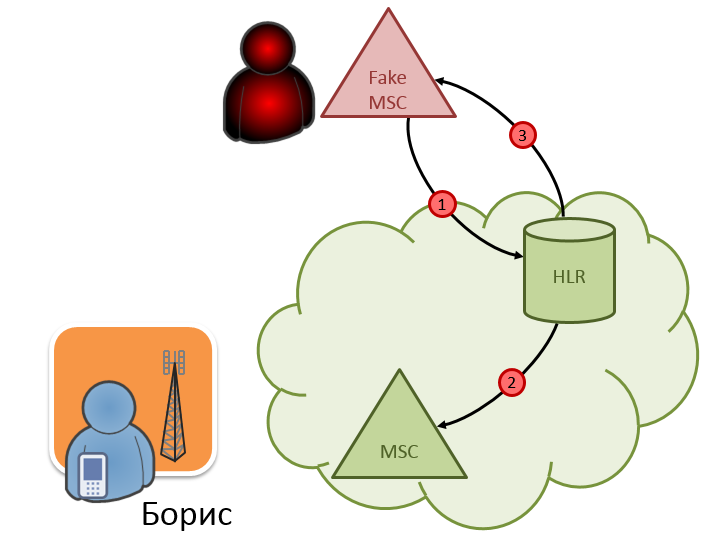
Fig. 5. DoS attack
Any of these actions initiates a procedure UpdateLocationthat updates the switch address in the HLR database to the real one.
Interception of SMS
Consequence of the previous attack.
We have already given all the theoretical basis required to understand the method of intercepting SMS messages. In fact, the interception of SMS is a consequence of the previous attack, if the attacker specifies the address of his equipment as a fake MSC. Let's take an example of how SMS messages are intercepted (Fig. 6). We believe that the attacker received all the necessary subscriber IDs for Boris and carried out a successful DoS attack on him, specifying the address of his node as a fake MSC.
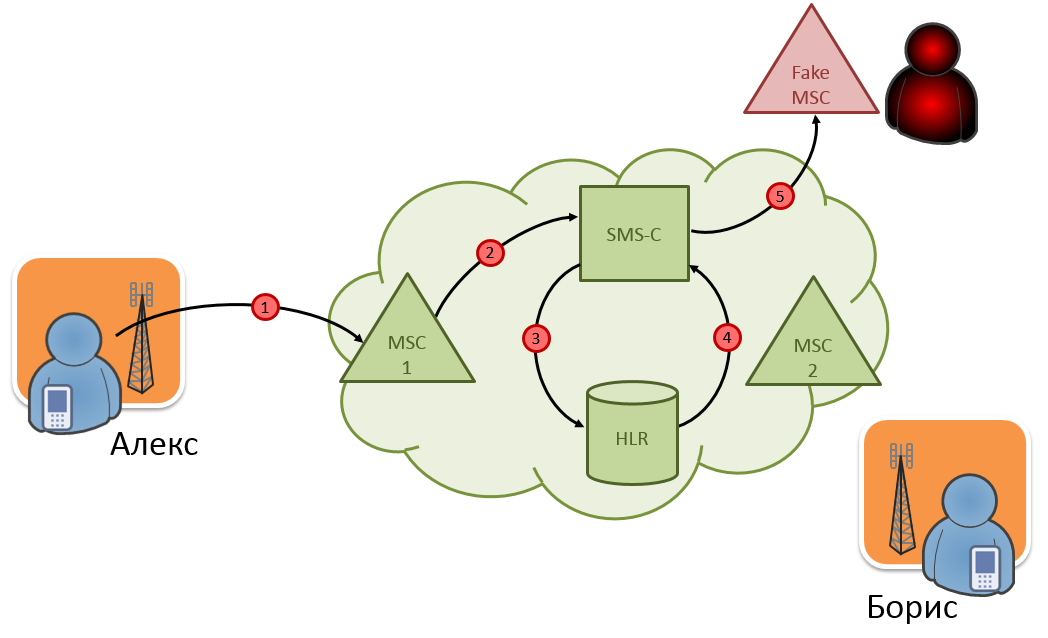
Fig. 6. Interception of SMS messages
Opportunities for an attacker
Let's suppose what benefit an attacker can get by intercepting SMS messages to a subscriber. It seems that this attack is ineffective in order to invade private correspondence: now people communicate mainly in messenger applications. It is much more interesting to get a one-time password from the bank to make a payment. Criminal groups that specialize in hacking bank card accounts often lack one-time passwords to withdraw funds.
Another of the attack scenarios in which SMS interception can be used is password recovery for various Internet services: for e-mail, social networks, and public service portals. All of these services may contain confidential information, and its value is the higher, the louder the victim has.
Almost all mobile operators request a password to access the subscriber's personal account via SMS. Having gained access to a personal account, an attacker can control services, transfer funds between accounts, and in some cases view the history of SMS messages.
Summing up
Finally, I would like to say a few words about how mobile operators view SS7 security. First, they believe (and rightly so) that it is impossible to get completely illegal access to the SS7 network. Secondly, there are agreements between all operators for traffic transmission, and even if malicious actions are suddenly noticed on the part of some operator, it will not be difficult to block the source address. Third, there are not many known cases of abuse of SS7 funds.
All three statements are perfectly valid. However, each of them has its own but.
First but. It is possible to get a connection to SS7, for example, under the guise of a VAS service provider. Most likely, this will not work in Russia, but there are countries with more loyal telecommunications legislation (or with strong corruption). In addition, one should not forget that state special services can also act as an attacker - for their country, of course, they are on the good side.
Second but. Before stopping malicious actions, they must be noticed. An extremely small number of operators constantly monitor SS7 networks for intrusions and attacks. And even if an attack through the SS7 network is noticed and stopped, no one will be able to tell when it started or how long it lasted.
Third but. Several cases of abuse related to SS7 have received widespread resonance and publicity in the media. One of them was reported by Edward Snowden, then the information was published in the Washington Post. We are talking about the SkyLock service, which allows tracking mobile subscribers, including through SS7 networks.

Fig. 7
How long has this service been running? How many subscribers were “under the hood” during its operation? How long would this service have lasted if it hadn't been for Snowden's messages? It is unlikely that we will ever get answers to these questions.
Another sensational case is wiretapping of Ukrainian mobile subscribers from the territory of Russia. Yes, this is also possible thanks to the capabilities of SS7! Several months passed from the beginning of the attacks to their detection and containment. The attacks were suppressed by administrative and technical methods, however, while the information leaks remained unnoticed, significant damage was caused to the operator and the state.
xakep.ru
- A bit of theory
- Attack options
- Determining the location of the subscriber
- Subscriber Availability Disruption (DoS)
- Interception of SMS
- Summing up
In fact, it was almost impossible to get into the signaling network in traditional telephony technologies. But progress does not stand still, and from the beginning of the XXI century IP-telephony began to gradually replace the traditional one. Any personal computer can now have several free programs installed, and then knowledge of the SS7 protocols and programming skills, multiplied by the time spent, turns this computer into a powerful criminal tool - it would be a fantasy.
A bit of theory
But before we let our imagination run wild, let's make a small digression and delve into the technology of mobile communications. In telephone networks, including mobile ones, subscriber (voice or data) and service traffic (for example, for establishing a connection) are clearly separated. In fact, service traffic is the very same signaling system No. 7, which includes a certain set of protocols, rules and messages.
When communicating between operators, nodes in mobile communications are addressed not by IP addresses, but by Global Title addresses, the format of which resembles telephone numbers. The Global Title addresses must be included in the range of telephone numbers assigned to the telecom operator, and if at the national level the ranges are divided by regions, then the Global Title addresses of the network nodes must correspond to the regional ranges.
We will not describe the entire SS7 protocol stack here. Suffice it to say that for the interaction of the nodes of the core of the mobile operator, the MAP protocol is used - Mobile Application Part. The MAP protocol is aimed at the implementation of functions inherent in mobile networks, such as authentication and registration of a mobile device in the network, localization of the subscriber for making an incoming call, and support for a continuous voice communication channel when the subscriber moves. Each operation corresponds to a specific MAP message with its own set of parameters. Various messages are mentioned below, and by default they will all belong to the MAP protocol.
We are used to using regular telephone numbers for mobile communications. In technical terms of mobile communications, these numbers are called MSISDN - Mobile Subscriber Integrated Services Digital Network Number. This number is assigned to a subscriber when concluding a contract with a mobile operator. But in the depths of the communications network, subscribers are addressed by another identifier - IMSI (International Mobile Subscriber Identity), which is tied to a specific SIM card. The overwhelming majority of operations require addressing the subscriber exactly by IMSI, therefore, in order to carry out most attacks aimed at a specific subscriber, an attacker first of all needs to find out this identifier.
It should also be noted that the SS7 protocols do not provide opportunities for providing such functions as node authentication, filtering messages by access lists, dynamic routing of new network nodes. All this allows a potential attacker to achieve their goals.
Attack options
Prelude.
So, we assume that the attacker gained access to the SS7 network and wants to conduct a series of attacks on you, the reader. We assume that the attacker knows the phone number of the victim subscriber. As mentioned earlier, the first step for an attacker is to obtain an IMSI that matches the victim's phone number. For a better understanding of the process, I propose now to distract from the attack itself and first see how one of the simplest services in mobile communications works - the Short Message Service, “SMS”.
How SMS messages flow
First of all, it should be noted that SMS messages in mobile networks "go" through signaling channels, completely without affecting the voice and packet traffic channels. For any transaction between two subscribers, there is a source and a receiver. The subscriber, sending an SMS message, indicates the recipient's phone number and enters the text. However, the service fields of the message contain the address of the SMS center: this node is responsible for routing SMS messages (and its address is specified in each phone in the SMS settings). The flow chart of the SMS message is shown in Fig. one.

Fig. 1. Scheme of SMS message flow
There are no accidents
- Subscriber Alex sends SMS to subscriber Boris. This message is sent via signaling channels to the mobile switch MSC-1 serving Alex's subscriber.
- The MSC-1 switch will understand that it is an SMS, see the address of the SMS center in the message and send an SMS to this address in MO-ForwardSMa MAP message . Let's dwell a little on this message. It contains the following data: MSISDN number of the sender, MSISDN number of the recipient, SMS text. And now the SMS center is faced with a daunting task. Firstly, further transmission of an SMS message requires knowledge of the IMSI of the recipient subscriber; secondly, the SMS center does not know anything about the location of the subscriber. Let's not forget that we are talking about mobile communications, and the subscriber may be in Moscow today, and tomorrow he will be in Oslo.
- But in fact, not everything is so bad, because the mobile network has a subscriber database - HLR, where the movements of subscribers are recorded with an accuracy of the switch. It is to this database that the SMS center turns to get the IMSI of the subscriber and the address of the switch serving it. The SMS center sends SendRoutingInfoForSMa MAP protocol message , where the MSISDN number of Boris's subscriber is specified as a parameter.
- As we said, the HLR database stores the address of the switch serving the subscriber at the moment. In addition, the HLR stores the MSISDN and IMSI mappings. It is these two parameters that HLR will give in the response message SendRoutingInfoForSM.
- Now the SMS center sends a message MT-ForwardSMto the received address of the switch, in which it transmits the SMS text, specifies the sender's MSISDN number (it will be displayed when receiving an SMS), and the recipient subscriber is addressed by IMSI.
- The receiving switchboard sends an SMS message to subscriber Boris, receiving data on the exact location of the subscriber in its database.
Getting IMSI and other delights
So, with the help of a message, the SendRoutingInfoForSMSMS center receives the IMSI of the subscriber and the address of the serving switch by the phone number. If we assume that Alex and Boris are subscribers of different networks in the SMS message flow scheme, then we will find that the message SendRoutingInfoForSMtravels between networks (Fig. 2).

Fig. 2. Passage of SMS messages between networks
In order for the SMS center to make a request, it must "know" the HLR address of the foreign network. Although ... it's not really necessary. The SMS-center can send a message SendRoutingInfoForSMusing the recipient's subscriber's phone number as the Global Title. Since the Global Title addresses and telephone numbering are in the same range, the message will be delivered to the recipient's network, and then routed to the corresponding HLR via the telephone number. In the response message, HLR will disclose its address, and as parameters it will transmit the MSC address and IMSI of the subscriber.
As a result, it turns out that an attacker who has connected to the SS7 network can initially only know the number of the attacked subscriber to carry out his attacks. By sending the message SendRoutingInfoForSM, he will receive the HLR address, the MSC address and the IMSI of the subscriber.
Determining the location of the subscriber
Now let's move on to real attacks. The first thing that comes to mind is to determine where the subscriber is. Surely in the bowels of the mobile network there should be information about the current position of the subscriber. And in fact it is there, although its accuracy is not always the same. To clarify this issue, you will have to dive into communication technology again.
Structure of cellular networks
Everyone has seen antennas of base stations of cellular communications: in cities, they are dotted with almost all high-rise buildings. Outside urban areas, base station antennas are most often installed on special mast structures. Base stations provide radio coverage for the network, which ideally, of course, should be without blind spots. Base stations are connected to controllers - BSC (Base Station Controller) in the GSM standard and RNC (Radio Network Controller) in the UMTS standard. The controllers are connected to the MSC switch.
At the base station, as a rule, several antennas are installed, each of which covers its own sector, or cell. Each cell has a CID - Cell ID. Cells are grouped into groups called Location Area, and are identified by the LAC identifier - Location Area Code. Often, the Location Area includes all sectors whose base stations are connected to the same controller.
The identifier of the cell serving the subscriber at each point in time is stored in the controller's database. But controllers - both BSC and RNC - connect directly to the switch and have no connections to external networks. It is almost impossible to extract information from there.
Each MSC also has its own base - VLR (Visited Location Register), which stores information about all subscribers within the coverage area of this switch. There is even LAC and CID data for subscribers, but the CID value is updated only at the moment when the subscriber crosses the boundaries of the Location Area or performs any other active action. Although from a network point of view, changing information about a new LAC is the same activity as making a phone call.
A switch, unlike controllers, has a connection to external networks, and an attacker with access to SS7 can obtain information about the location of subscribers from its database.
Three-way
Now that we know how mobile networks are built, it will be easy for us to understand the attack technique. The first move absolutely repeats the steps for obtaining the IMSI of the subscriber and the address of the switch serving it. Let's repeat: this is done using a message SendRoutingInfoForSM(the attacker emulates the operation of the SMS center).
At this stage, it would be possible to immediately send a request to the switch database, but in this case we risk receiving not the most accurate information, since we cannot be sure whether the phone of a known subscriber performed any active actions in the cell where he is now. To know for sure, we need to force the subscriber's phone to perform similar actions, but this must be done so that the subscriber does not notice anything.
The standard for SMS messages implies the ability to form a message in such a way that it will be invisible to the subscriber, the so-called Silent SMS. The phone receives the message, but does not signal its receipt and does not display it in the list of received SMS.
On the second move, the attacker continues to emulate the operation of the SMS center. He sends a Silent SMS to the desired subscriber in a message MT-ForwardSM. The message itself is sent to the switch, the address of which was received in the first move, and the subscriber is addressed using IMSI. After passing this message, the information about the location of the subscriber in the switch base will be updated. It now contains information about the current LAC and CID.
There is very little left - to send a request to the switch to obtain data about the cell serving the subscriber. This is done by a message ProvideSubscriberInfothat is sent to the switch, the subscriber is addressed by IMSI. (As we remember, we already have both the switch address and the subscriber's IMSI.) In mobile networks, this message is used to transmit information about the location of the called subscriber for online billing. If the subscriber is in roaming, the corresponding charging scheme is activated.
The message ProvideSubscriberInforeturns the full set of serving cell identifiers: MCC - Mobile Country Code, MNC - Mobile Network Code, LAC, CID. There are many services on the Internet that allow for these four parameters to determine the geographic coordinates of the base station and even the approximate coverage area of the cell. In fig. 3 shows the result of determining my location at the time of this writing. The point marks the base station, and the building where I am sitting is indeed within the indicated circle.

Fig. 3. Determining the location of the author of the article
Subscriber Availability Disruption (DoS)
The next attack is subscriber DoS. To understand the attack technique, let's again dive into the principles of mobile communication networks.
Subscriber registration in roaming
Consider the signal exchange and the main processes occurring in mobile networks when a subscriber leaves for another country and registers in the network of the operator's roaming partner (diagram in Fig. 4).

Fig. 4. Registration of the subscriber in the network of the roaming partner
- Subscriber Alex from the network called "Home" goes on vacation to the sea, leaving the plane, turns on the phone and gets into the network "Zagranitsa".
- The MSC Z switch, using the first digits of the IMSI, will determine the country and network from which the subscriber arrived, and send a request for subscriber authentication - a message to this network SendAuthenticationInfo.
- The node that is responsible for authentication and encryption key assignment is called AuC - Authentication Center. It determines the encryption key and other service information required for authentication and sends it back.
- After the subscriber is authenticated, you need to register him on the new MSC Z switch. The switch sends a registration request to the “Home” network - a message UpdateLocation. This message comes to HLR.
- Having received the message UpdateLocation, the HLR sends a message to the switch MSC D (where the subscriber was registered earlier) CancelLocation, telling him to free memory from Alex's subscriber profile. The HLR then updates the current switch address to MSC Z in its database.
- In response to the request for registration HLR sends to the MSC Z subscriber profile in a statement InsertSubscriberData. This profile contains the subscriber's connected services and addresses of intelligent platforms, if the subscriber is subscribed to the corresponding services. Most often, the online billing system acts as an intelligent platform, among other things.
Carrying out an attack
What remains for an attacker to do to send the subscriber to DoS for incoming calls? Just send a message UpdateLocationon behalf of the MSC to the subscriber's home network . The signal exchange diagram is shown in Fig. five.

Fig. 5. DoS attack
- The message is sent to HLR, the subscriber is addressed by the IMSI identifier (we already know how to receive the necessary data). Another of the message parameters UpdateLocationis the address of the new switch.
- The HLR in its database will untie the real switch.
- HLR will send the subscriber profile to the attacker's equipment.
- the subscriber will move to the coverage area of another switch;
- the subscriber will restart the phone;
- the subscriber will make a call or send an SMS message.
Any of these actions initiates a procedure UpdateLocationthat updates the switch address in the HLR database to the real one.
Interception of SMS
Consequence of the previous attack.
We have already given all the theoretical basis required to understand the method of intercepting SMS messages. In fact, the interception of SMS is a consequence of the previous attack, if the attacker specifies the address of his equipment as a fake MSC. Let's take an example of how SMS messages are intercepted (Fig. 6). We believe that the attacker received all the necessary subscriber IDs for Boris and carried out a successful DoS attack on him, specifying the address of his node as a fake MSC.

Fig. 6. Interception of SMS messages
- Subscriber Alex sends an SMS message to subscriber Boris, this message arrives at the switchboard serving the sender.
- The switch forwards the message to the SMS center. As we already know, this happens in MO-ForwardSMthe MAP message .
- The SMS center does not know where subscriber Boris is at the moment, so he sends a request to HLR in a message SendRoutingInfoForSM.
- Since a successful DoS attack was carried out on Boris's subscriber, the HLR database contains false information about his location. This false information will be given to the HLR SMS-center in a reply message SendRoutingInfoForSM.
- The SMS-center, without suspecting anything, will send an SMS-message in clear text to the received address in MT-ForwardSMthe MAP protocol message . And behind this address, as we have already said, our attacker is hiding.
Opportunities for an attacker
Let's suppose what benefit an attacker can get by intercepting SMS messages to a subscriber. It seems that this attack is ineffective in order to invade private correspondence: now people communicate mainly in messenger applications. It is much more interesting to get a one-time password from the bank to make a payment. Criminal groups that specialize in hacking bank card accounts often lack one-time passwords to withdraw funds.
Another of the attack scenarios in which SMS interception can be used is password recovery for various Internet services: for e-mail, social networks, and public service portals. All of these services may contain confidential information, and its value is the higher, the louder the victim has.
Almost all mobile operators request a password to access the subscriber's personal account via SMS. Having gained access to a personal account, an attacker can control services, transfer funds between accounts, and in some cases view the history of SMS messages.
Summing up
Finally, I would like to say a few words about how mobile operators view SS7 security. First, they believe (and rightly so) that it is impossible to get completely illegal access to the SS7 network. Secondly, there are agreements between all operators for traffic transmission, and even if malicious actions are suddenly noticed on the part of some operator, it will not be difficult to block the source address. Third, there are not many known cases of abuse of SS7 funds.
All three statements are perfectly valid. However, each of them has its own but.
First but. It is possible to get a connection to SS7, for example, under the guise of a VAS service provider. Most likely, this will not work in Russia, but there are countries with more loyal telecommunications legislation (or with strong corruption). In addition, one should not forget that state special services can also act as an attacker - for their country, of course, they are on the good side.
Second but. Before stopping malicious actions, they must be noticed. An extremely small number of operators constantly monitor SS7 networks for intrusions and attacks. And even if an attack through the SS7 network is noticed and stopped, no one will be able to tell when it started or how long it lasted.
Third but. Several cases of abuse related to SS7 have received widespread resonance and publicity in the media. One of them was reported by Edward Snowden, then the information was published in the Washington Post. We are talking about the SkyLock service, which allows tracking mobile subscribers, including through SS7 networks.

Fig. 7
How long has this service been running? How many subscribers were “under the hood” during its operation? How long would this service have lasted if it hadn't been for Snowden's messages? It is unlikely that we will ever get answers to these questions.
Another sensational case is wiretapping of Ukrainian mobile subscribers from the territory of Russia. Yes, this is also possible thanks to the capabilities of SS7! Several months passed from the beginning of the attacks to their detection and containment. The attacks were suppressed by administrative and technical methods, however, while the information leaks remained unnoticed, significant damage was caused to the operator and the state.
xakep.ru
