Father
Professional
- Messages
- 2,601
- Reaction score
- 836
- Points
- 113
In today's digital world, with a bunch of different services, applications, instant messengers, social networks and other means of communication, it may seem that the good old email has lost ground. However, in reality this is not the case: most of us still have to use e-mail, at least in order to register in all these many services, applications and social networks.
For the same reason, logins and passwords from mail services are a very tasty morsel for cybercriminals. Let's talk about how bad people use phishing to get these logins and passwords to hack someone else's mail.
Phishing emails are the most common way to hack mail
The vast majority of fraudulent emails aimed at stealing logins and passwords from e-mail services imitate messages on behalf of the services themselves. When hunting home users, phishers imitate well-known mailers. And when trying to get corporate accounts, they pretend to be a work mail service - in this case, the letter comes simply from the name of the mail server.
Counterfeits for well-known mail services are much more common. Scammers try to make such letters as convincing as possible. The arsenal of tricks is standard: the sender's address, similar to the real one, logos, auto-signatures, links to official resources, the general style of writing, and so on.
A phishing email that scares the user by deleting a mailbox
Scammers often send phishing emails pretending to be messages from work mail to general addresses (including administrators), but sometimes such emails also come to the addresses of specific employees whose mail somehow ended up in spam databases.
More or less serious companies, not to mention large ones, have their own mail servers for e-mail correspondence. Attackers also hunt for logins and passwords from such mail. Often, poor design of their letters immediately reveals a fake - for example, addresses of senders on free mail services, errors in the text, etc. - but even such a letter may seem real to an inexperienced employee.
Example of a phishing email warning that the storage quota has been exceeded
In this letter, phishers simulate a warning about exceeding the quota.
When attackers launch an attack targeting a specific organization, they usually collect more information about it in advance in order to send out the most believable letters. It is also worth noting that in order to make it convincing and unique, scammers embed the victim's email addresses in phishing links, so that when they go to a fake page, the email address is already specified and all that remains is to enter the password from the mail.
What types of phishing emails are there?
Plain text requesting information
Fraudsters send messages on behalf of postal services, in which, under one pretext or another, they ask the recipient to send them an email address, password and other information. Usually, an email address other than the one specified in the sender field is given as a contact to reply.
This type of phishing emails was popular enough until scammers mastered other, more effective ways to steal personal information.

Example of a phishing email with a request to send an account password.
Phishing email with a text request for account information, including a password. In no case should you send something in response to such requests
Email with a link to a phishing site
Phishing messages with links are by far the most common in junk mail traffic. Fraudsters can use an unlimited number of links, change them from letter to letter within one mailing list, create very similar to legitimate phishing pages, automate the collection and processing of stolen data.
However, it is the address of the link that can immediately give out scammers: domains that have nothing to do with organizations, errors in the spelling of domains that look like legitimate ones, littering.
Therefore, attackers try to hide the link addresses. To do this, they hide them behind a text fragment or image. In some cases, a phrase like "Update your mailbox" serves as the text fragment. And sometimes the real address of the mail service is put in the text part of the link, while the “link” part actually contains the address of the phishing site.

Example of a phishing email with a phishing link.
Most phishing emails contain links to phishing pages - you should not follow these links
Phishing attachments
Phishing emails can also contain attachments, usually files with the extension html, pdf, or doc.
Doc and pdf attachments often contain phishing email text and a fraudulent link. Attackers use this option when they want to make the text of the message in the message itself as short as possible and similar to legitimate correspondence in order to bypass spam filters.

Example of a phishing email with a phishing PDF attachment.
Sometimes phishers attach PDF or DOC documents to emails with links to phishing sites inside
The html files are used instead of a link - in fact, the html from the attachment is a ready-made phishing page. The advantage from the point of view of scammers is that the attached html file works completely autonomously - it does not need to be posted on the Internet. At the same time, it also has all the functionality that fraudsters need.

Example of a phishing email with a phishing attachment in HTML format.
In this case, the login and password entry form is contained directly in the phishing email. In no case do not enter anything into such forms in letters.
What they write about in phishing emails
Account issues
As for the text of the letters, it is most often at the beginning that a problem is reported with the victim's account. This can be reaching the storage limit, problems with the delivery of letters, unauthorized login to the account, accusations of sending spam, some other notifications of violations, and so on.
Usually, this is followed by an indication of what needs to be done - most often to confirm or update account information - by clicking on a link or opening an attachment. Also, in order to intimidate the recipient, it is mentioned that the account will be deleted or blocked if the actions specified in the text are not followed.
Scammers almost always indicate specific time frames - from several hours to several weeks. Most often it is 24 hours - it looks believable at the same time, and does not allow the victim to relax and forget about the letter.
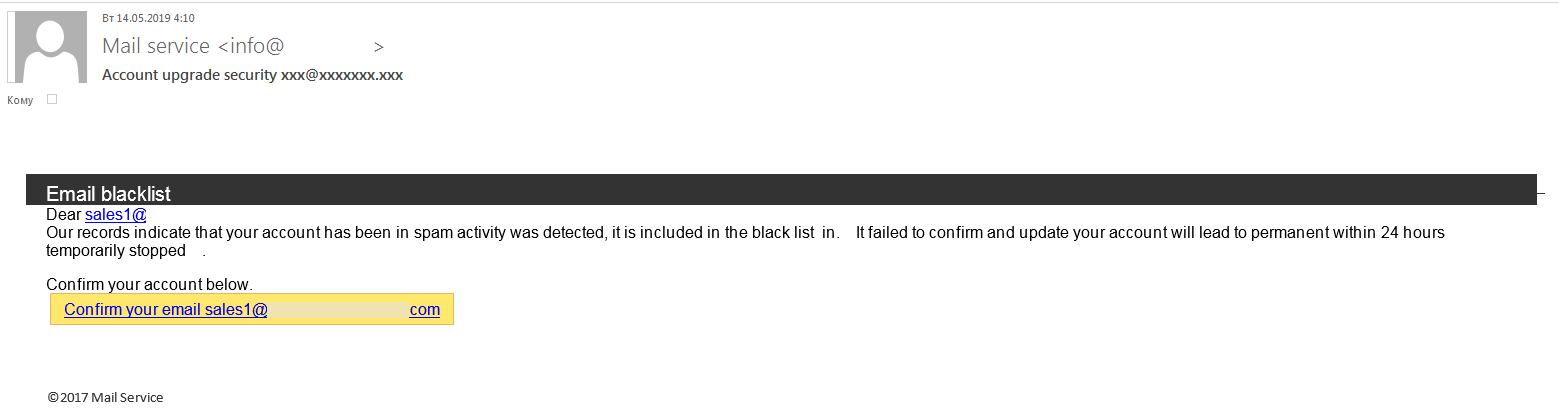
Example of a phishing email with limited time for user reaction.
"Within 24 hours, your account will be deleted for sending spam." Threats and time limits are typical techniques used in phishing emails
Imitation of business correspondence
Among phishing emails aimed at stealing mail, there are also atypical examples. The text of the message may not say anything about mail and mail account. The letter may look, for example, like a real business correspondence.
It should be noted that the number of emails imitating business correspondence has been increasing in the past few years. Basically, it is malicious attachments that are sent in this way, but phishing aimed at stealing personal data occurs. It can be difficult for an ordinary user to recognize a fraudulent email - this is exactly what cybercriminals are counting on.
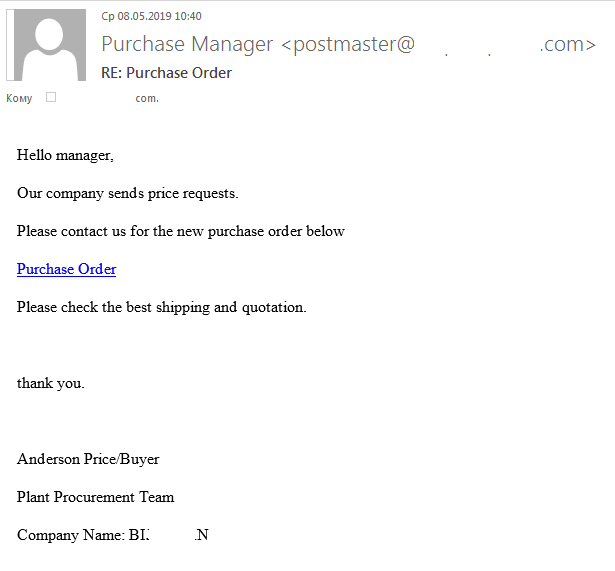
An example of a phishing email that mimics business correspondence.
When phishers hunt corporate accounts, they often imitate business correspondence.
Some users will not suspect deception and will follow a link where they will be asked to enter their email addresses and passwords to view a non-existent document.
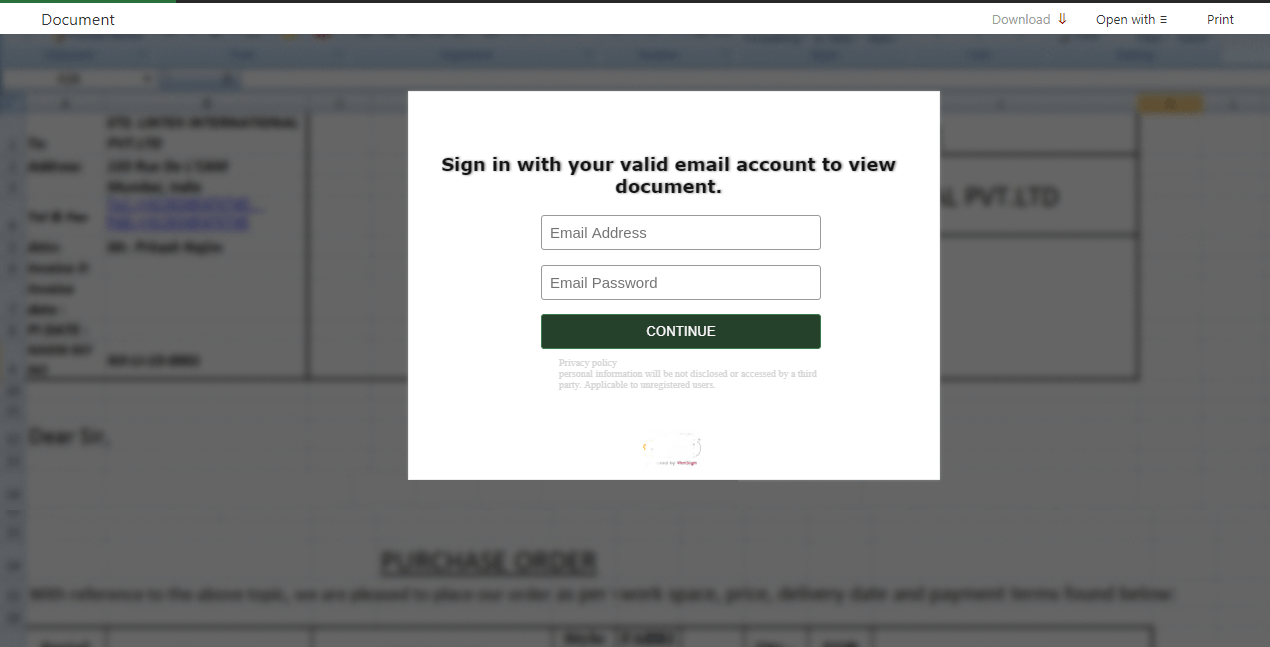
An example of a phishing site that requires logging in to view a document.
The phishing site offers to log in to view a certain document, the link to which was sent in the phishing email
What are phishing pages?
With the format and content of the letters sorted out, now let's look at how phishing pages might look. And also let's talk about those elements that are worth paying attention to in order to recognize a fake.
The first thing you need to pay close attention to is the link address. It is he who immediately betrays the scammers. Typical signs of cheating are:
This is understandable, because few people remember exactly what the official login page for a particular service looks like. Therefore, in order to create a convincing phishing page, fraudsters sometimes just need to use the main memorable elements: a characteristic color scheme, a logo, and so on.
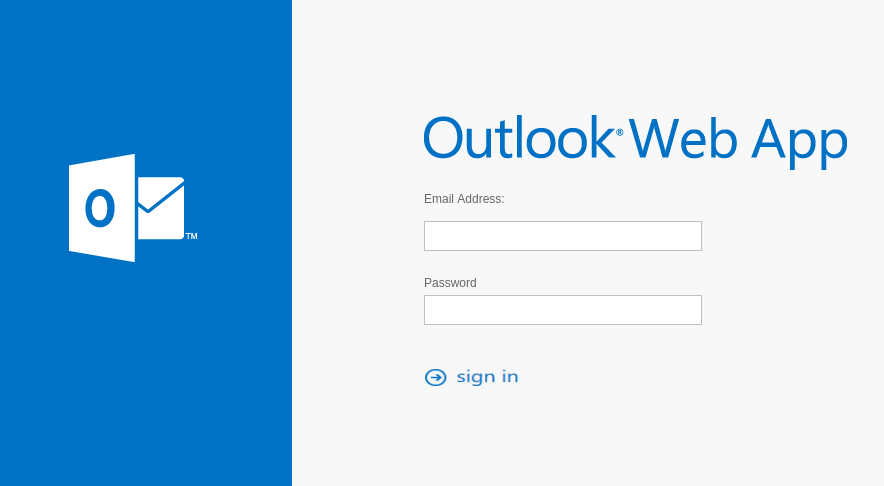
An example of an email login page on a phishing site.
Simulate the login page for the mail service
Phishing pages designed to steal logins and passwords from free mail services are characterized by the presence on one page of links to several services at once.
When you click on any of the links in the example below, a pop-up window appears that simulates the login page for the corresponding resource. Thus, fraudsters collect data from several accounts at once, using just one page, and not creating it separately for each.

An example of a universal phishing site with the ability to use different accounts to log in.
This phishing site mimics the ability to log in using accounts on different mailers
In addition, you can significantly expand the number of potential victims and send phishing emails not from a specific service, but of any general content (for example, the above-described variant with business correspondence), where, according to the context, you can use a similar phishing page with the most popular services, and the user himself will choose exactly the one he uses.
Another example of simulating the mail login page.
The time-limited trick, which we talked about when we talked about phishing emails, is sometimes used on phishing pages as well. When clicking on a fraudulent link on the page, a countdown begins, during which a user who has fallen into the bait of hackers supposedly has to enter his data.
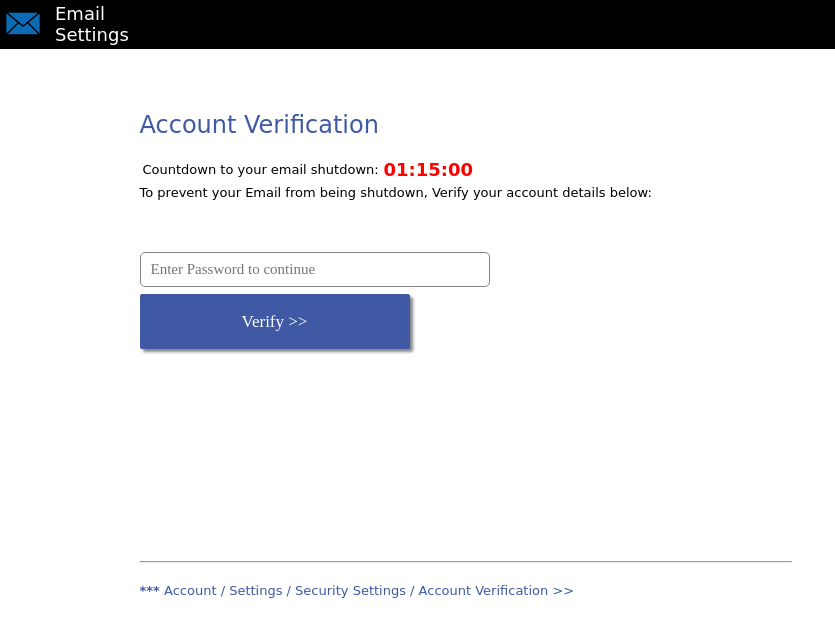
Example of a phishing page with a time limit.
Some phishing pages also rush the user.
After entering the data on the phishing page, there are several possible scenarios for further developments. Sometimes the site just becomes unavailable or shows an error message. In other cases, the user is informed that incorrect data was entered and asked to re-enter.
Now, perhaps the most dangerous option is gaining popularity: after entering the data, the phishing page redirects the user to the real login page in the mail of the corresponding service. The user thinks that something just glitched, enters the login and password again, gets into his account and forgets about this strange episode.
How to recognize phishing emails
media.kasperskydaily.com
For the same reason, logins and passwords from mail services are a very tasty morsel for cybercriminals. Let's talk about how bad people use phishing to get these logins and passwords to hack someone else's mail.
Phishing emails are the most common way to hack mail
The vast majority of fraudulent emails aimed at stealing logins and passwords from e-mail services imitate messages on behalf of the services themselves. When hunting home users, phishers imitate well-known mailers. And when trying to get corporate accounts, they pretend to be a work mail service - in this case, the letter comes simply from the name of the mail server.
Counterfeits for well-known mail services are much more common. Scammers try to make such letters as convincing as possible. The arsenal of tricks is standard: the sender's address, similar to the real one, logos, auto-signatures, links to official resources, the general style of writing, and so on.
A phishing email that scares the user by deleting a mailbox
Scammers often send phishing emails pretending to be messages from work mail to general addresses (including administrators), but sometimes such emails also come to the addresses of specific employees whose mail somehow ended up in spam databases.
More or less serious companies, not to mention large ones, have their own mail servers for e-mail correspondence. Attackers also hunt for logins and passwords from such mail. Often, poor design of their letters immediately reveals a fake - for example, addresses of senders on free mail services, errors in the text, etc. - but even such a letter may seem real to an inexperienced employee.
Example of a phishing email warning that the storage quota has been exceeded
In this letter, phishers simulate a warning about exceeding the quota.
When attackers launch an attack targeting a specific organization, they usually collect more information about it in advance in order to send out the most believable letters. It is also worth noting that in order to make it convincing and unique, scammers embed the victim's email addresses in phishing links, so that when they go to a fake page, the email address is already specified and all that remains is to enter the password from the mail.
What types of phishing emails are there?
Plain text requesting information
Fraudsters send messages on behalf of postal services, in which, under one pretext or another, they ask the recipient to send them an email address, password and other information. Usually, an email address other than the one specified in the sender field is given as a contact to reply.
This type of phishing emails was popular enough until scammers mastered other, more effective ways to steal personal information.

Example of a phishing email with a request to send an account password.
Phishing email with a text request for account information, including a password. In no case should you send something in response to such requests
Email with a link to a phishing site
Phishing messages with links are by far the most common in junk mail traffic. Fraudsters can use an unlimited number of links, change them from letter to letter within one mailing list, create very similar to legitimate phishing pages, automate the collection and processing of stolen data.
However, it is the address of the link that can immediately give out scammers: domains that have nothing to do with organizations, errors in the spelling of domains that look like legitimate ones, littering.
Therefore, attackers try to hide the link addresses. To do this, they hide them behind a text fragment or image. In some cases, a phrase like "Update your mailbox" serves as the text fragment. And sometimes the real address of the mail service is put in the text part of the link, while the “link” part actually contains the address of the phishing site.

Example of a phishing email with a phishing link.
Most phishing emails contain links to phishing pages - you should not follow these links
Phishing attachments
Phishing emails can also contain attachments, usually files with the extension html, pdf, or doc.
Doc and pdf attachments often contain phishing email text and a fraudulent link. Attackers use this option when they want to make the text of the message in the message itself as short as possible and similar to legitimate correspondence in order to bypass spam filters.

Example of a phishing email with a phishing PDF attachment.
Sometimes phishers attach PDF or DOC documents to emails with links to phishing sites inside
The html files are used instead of a link - in fact, the html from the attachment is a ready-made phishing page. The advantage from the point of view of scammers is that the attached html file works completely autonomously - it does not need to be posted on the Internet. At the same time, it also has all the functionality that fraudsters need.

Example of a phishing email with a phishing attachment in HTML format.
In this case, the login and password entry form is contained directly in the phishing email. In no case do not enter anything into such forms in letters.
What they write about in phishing emails
Account issues
As for the text of the letters, it is most often at the beginning that a problem is reported with the victim's account. This can be reaching the storage limit, problems with the delivery of letters, unauthorized login to the account, accusations of sending spam, some other notifications of violations, and so on.
Usually, this is followed by an indication of what needs to be done - most often to confirm or update account information - by clicking on a link or opening an attachment. Also, in order to intimidate the recipient, it is mentioned that the account will be deleted or blocked if the actions specified in the text are not followed.
Scammers almost always indicate specific time frames - from several hours to several weeks. Most often it is 24 hours - it looks believable at the same time, and does not allow the victim to relax and forget about the letter.

Example of a phishing email with limited time for user reaction.
"Within 24 hours, your account will be deleted for sending spam." Threats and time limits are typical techniques used in phishing emails
Imitation of business correspondence
Among phishing emails aimed at stealing mail, there are also atypical examples. The text of the message may not say anything about mail and mail account. The letter may look, for example, like a real business correspondence.
It should be noted that the number of emails imitating business correspondence has been increasing in the past few years. Basically, it is malicious attachments that are sent in this way, but phishing aimed at stealing personal data occurs. It can be difficult for an ordinary user to recognize a fraudulent email - this is exactly what cybercriminals are counting on.

An example of a phishing email that mimics business correspondence.
When phishers hunt corporate accounts, they often imitate business correspondence.
Some users will not suspect deception and will follow a link where they will be asked to enter their email addresses and passwords to view a non-existent document.

An example of a phishing site that requires logging in to view a document.
The phishing site offers to log in to view a certain document, the link to which was sent in the phishing email
What are phishing pages?
With the format and content of the letters sorted out, now let's look at how phishing pages might look. And also let's talk about those elements that are worth paying attention to in order to recognize a fake.
The first thing you need to pay close attention to is the link address. It is he who immediately betrays the scammers. Typical signs of cheating are:
- extraneous domains not related to organizations;
- the names of the organizations in the path instead of the domain - for example, www.example.com/outlook/,
- spelling mistakes;
- automatically generated sequences of characters in the link address;
- characters from other languages, similar to the basic Latin alphabet - ç instead of c, á instead of a, and so on.
This is understandable, because few people remember exactly what the official login page for a particular service looks like. Therefore, in order to create a convincing phishing page, fraudsters sometimes just need to use the main memorable elements: a characteristic color scheme, a logo, and so on.

An example of an email login page on a phishing site.
Simulate the login page for the mail service
Phishing pages designed to steal logins and passwords from free mail services are characterized by the presence on one page of links to several services at once.
When you click on any of the links in the example below, a pop-up window appears that simulates the login page for the corresponding resource. Thus, fraudsters collect data from several accounts at once, using just one page, and not creating it separately for each.

An example of a universal phishing site with the ability to use different accounts to log in.
This phishing site mimics the ability to log in using accounts on different mailers
In addition, you can significantly expand the number of potential victims and send phishing emails not from a specific service, but of any general content (for example, the above-described variant with business correspondence), where, according to the context, you can use a similar phishing page with the most popular services, and the user himself will choose exactly the one he uses.
Another example of simulating the mail login page.
The time-limited trick, which we talked about when we talked about phishing emails, is sometimes used on phishing pages as well. When clicking on a fraudulent link on the page, a countdown begins, during which a user who has fallen into the bait of hackers supposedly has to enter his data.

Example of a phishing page with a time limit.
Some phishing pages also rush the user.
After entering the data on the phishing page, there are several possible scenarios for further developments. Sometimes the site just becomes unavailable or shows an error message. In other cases, the user is informed that incorrect data was entered and asked to re-enter.
Now, perhaps the most dangerous option is gaining popularity: after entering the data, the phishing page redirects the user to the real login page in the mail of the corresponding service. The user thinks that something just glitched, enters the login and password again, gets into his account and forgets about this strange episode.
How to recognize phishing emails
- If the domain in the sender's address does not belong to the organization on whose behalf the letter was written, and even more so if the mailbox is registered on free mail services, then this is a sure sign of a fraudulent letter. Official mailings always come from official addresses.
- If the address of the link on which the letter invites you to go contains extraneous domains, spelling errors, special characters, then this is an unambiguously fraudulent resource.
- If in the text of the letter you are told that there are unexpected problems with your account, you are persuaded to follow the link and enter your username and password, and you are given a certain amount of time for this, then the letter was written by scammers.
media.kasperskydaily.com

