CarderPlanet
Professional
- Messages
- 2,549
- Reaction score
- 724
- Points
- 113
A technique developed by researchers that relies on AI makes it possible to accurately determine the presence of a phishing site between the target service and its users. Such threats are usually poorly detected and rarely hit the blocklists.
To get started, a team from State University of New York at Stony Brook and Palo Alto Networks examined (PDF) 13 popular MitM phishing packs. The demand for such an advanced toolkit, packed in a ZIP file, has been growing lately: unlike conventional phishing toolkits, it allows you to steal credentials on the fly from user requests to the target service.
In a MitM attack scenario, a fake mirror site is placed between exchange points and intercepts traffic by extracting the necessary information from network packets. As a result, an attacker will be able to obtain not only logins and passwords, but also session cookies, as well as bypass two-factor authentication (2FA).
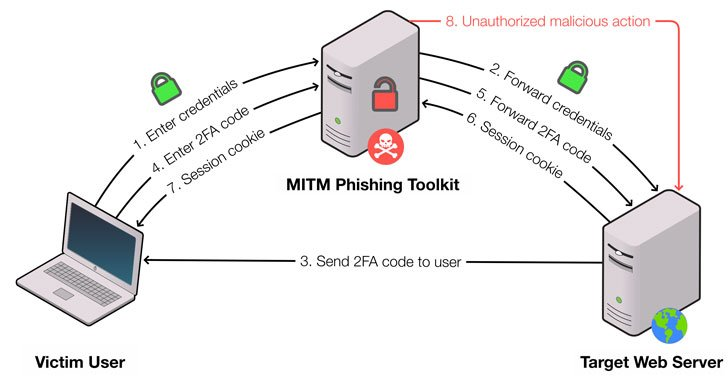
The reliability of phishing pages when using such a proxy is not so important: the illusion for the victim is supported by the ability to view other pages of the trap site after authentication. At the same time, the original service is also unlikely to notice the substitution.
As it turned out, such fakes live longer: the study showed that only 43.7% of domains and 18.9% of IP addresses associated with MitM phishing get into blocklists. The proposed method, according to the authors, allows you to get rid of the blind zone and increase the detection accuracy up to 99.9%.
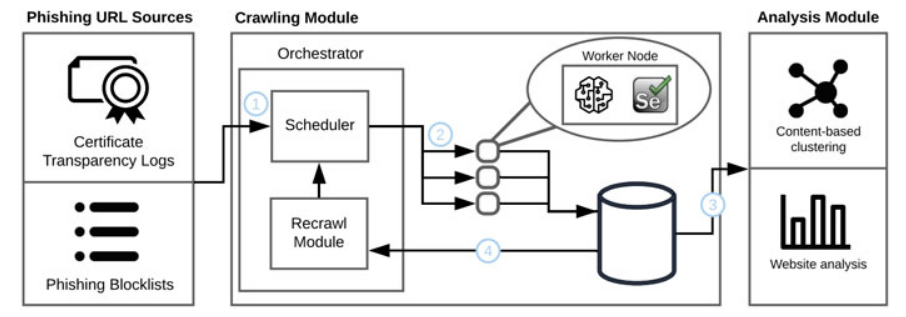
To identify cleverly hidden fakes, the researchers created a self-learning classifier that works with network data - TLS fingerprints, the time of transmission and reception of requests. The collection of samples for analysis was carried out by automated means - using the proprietary PHOCA tool, which looked for the necessary information in available phishing databases such as OpenPhish and PhishTank.
Delays were chosen as the main criterion: using a proxy server (in this case with a MitM fish pack) slows down the procedure for sending and confirming requests. When intercepting TLS requests, the deviation from the norm becomes even more noticeable.
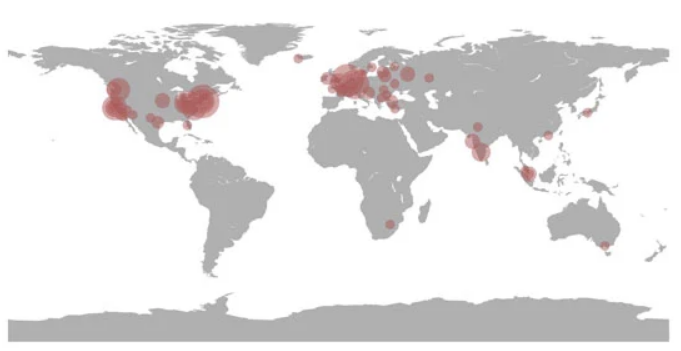
During the year, experimenters managed to identify 1,220 sites created for MitM phishing, mostly in the US and Europe, hosted by Amazon, DigitalOcean, Microsoft, or Google. Fakes have most often been imitated by Instagram, Google, Facebook, Microsoft Outlook, PayPal, Apple, Twitter, Coinbase, Yahoo, and LinkedIn. A study of 260 of these traps showed that in six months they received 6403 requests from users.
The PHOCA framework, according to the researchers, is easily integrated into existing infrastructure. It can, for example, extend the capabilities of a blocklist web service or shield a popular site from malicious requests generated by a phishing MitM pack. Testing has shown that a trial technique allows you to bypass the camouflage tools from the arsenal of such toolkits and effectively reveal previously hidden phishing content.
To get started, a team from State University of New York at Stony Brook and Palo Alto Networks examined (PDF) 13 popular MitM phishing packs. The demand for such an advanced toolkit, packed in a ZIP file, has been growing lately: unlike conventional phishing toolkits, it allows you to steal credentials on the fly from user requests to the target service.
In a MitM attack scenario, a fake mirror site is placed between exchange points and intercepts traffic by extracting the necessary information from network packets. As a result, an attacker will be able to obtain not only logins and passwords, but also session cookies, as well as bypass two-factor authentication (2FA).

The reliability of phishing pages when using such a proxy is not so important: the illusion for the victim is supported by the ability to view other pages of the trap site after authentication. At the same time, the original service is also unlikely to notice the substitution.
As it turned out, such fakes live longer: the study showed that only 43.7% of domains and 18.9% of IP addresses associated with MitM phishing get into blocklists. The proposed method, according to the authors, allows you to get rid of the blind zone and increase the detection accuracy up to 99.9%.
To identify cleverly hidden fakes, the researchers created a self-learning classifier that works with network data - TLS fingerprints, the time of transmission and reception of requests. The collection of samples for analysis was carried out by automated means - using the proprietary PHOCA tool, which looked for the necessary information in available phishing databases such as OpenPhish and PhishTank.

Delays were chosen as the main criterion: using a proxy server (in this case with a MitM fish pack) slows down the procedure for sending and confirming requests. When intercepting TLS requests, the deviation from the norm becomes even more noticeable.
During the year, experimenters managed to identify 1,220 sites created for MitM phishing, mostly in the US and Europe, hosted by Amazon, DigitalOcean, Microsoft, or Google. Fakes have most often been imitated by Instagram, Google, Facebook, Microsoft Outlook, PayPal, Apple, Twitter, Coinbase, Yahoo, and LinkedIn. A study of 260 of these traps showed that in six months they received 6403 requests from users.

The PHOCA framework, according to the researchers, is easily integrated into existing infrastructure. It can, for example, extend the capabilities of a blocklist web service or shield a popular site from malicious requests generated by a phishing MitM pack. Testing has shown that a trial technique allows you to bypass the camouflage tools from the arsenal of such toolkits and effectively reveal previously hidden phishing content.

