Father
Professional
- Messages
- 2,602
- Reaction score
- 837
- Points
- 113
How did an ordinary network tool gradually turn into a powerful cyber weapon?
Recently, hackers are increasingly using the DNS tunneling method to track when victims open phishing emails and click on malicious links, as well as to scan networks for vulnerabilities.
DNS tunneling consists of encoding data or commands that are sent and received through DNS queries. This turns DNS, an essential component of network communication, into a hidden data channel.
Attackers encode data in various ways, such as Base16 or Base64, or use their own text encoding algorithms so that this data can be obtained when querying DNS records such as TXT, MX, CNAME, and Address.
DNS tunneling is often used by hackers to bypass firewalls and filters in operations with C2 infrastructure and VPN networks.
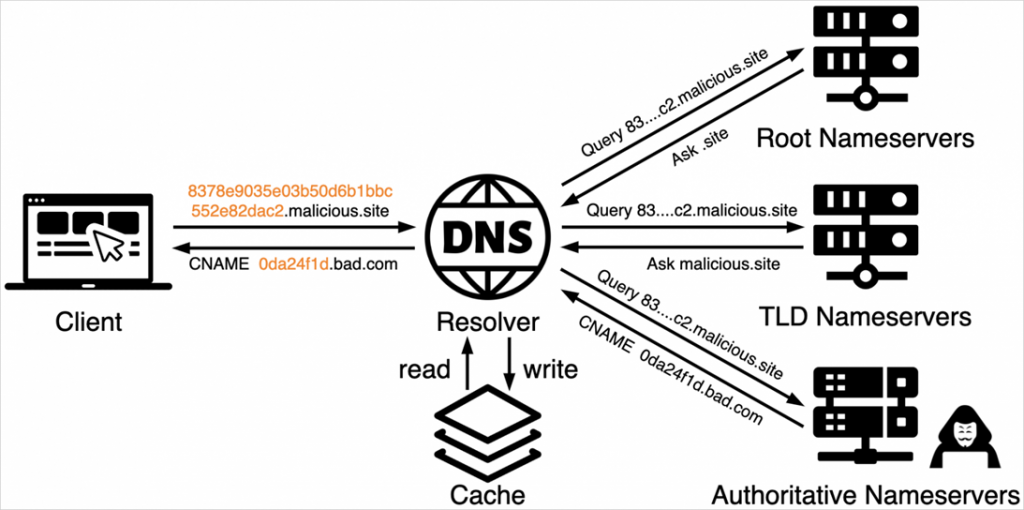
The Unit 42 research team from Palo Alto Networks recently discovered additional cases of DNS tunneling being used in malicious campaigns aimed at tracking victims and scanning networks.
The first campaign, called "TrkCdn", focuses on tracking victims interactions with phishing emails. Hackers embed content in an email that, when opened, performs a DNS query to subdomains controlled by the attackers.
These subdomains return a DNS response that leads to a server controlled by the attackers, which delivers malicious content such as ads, spam, or phishing materials.
The Unit 42 report also describes a campaign that uses DNS tunneling to track the delivery of spam messages, called "SpamTracker". This campaign is similar to TrkCdn, but is focused on monitoring spam delivery.
Another campaign discovered by analysts, called SecShow, uses DNS tunneling to scan network infrastructures. Hackers embed IP addresses and timestamps in DNS queries to map network configurations and detect potential vulnerabilities that can be exploited for intrusion, data theft, or denial of service.
Hackers choose DNS tunneling over more traditional methods to circumvent security features, avoid detection, and maintain operational flexibility.
Unit 42 researchers recommend that organizations implement DNS monitoring and analysis tools to track and analyze logs for unusual traffic patterns and anomalies, such as atypical or large queries. Experts also recommend limiting the use of DNS resolvers on the network for processing only necessary requests, in order to reduce the likelihood of DNS tunneling abuse.
Recently, hackers are increasingly using the DNS tunneling method to track when victims open phishing emails and click on malicious links, as well as to scan networks for vulnerabilities.
DNS tunneling consists of encoding data or commands that are sent and received through DNS queries. This turns DNS, an essential component of network communication, into a hidden data channel.
Attackers encode data in various ways, such as Base16 or Base64, or use their own text encoding algorithms so that this data can be obtained when querying DNS records such as TXT, MX, CNAME, and Address.
DNS tunneling is often used by hackers to bypass firewalls and filters in operations with C2 infrastructure and VPN networks.

The Unit 42 research team from Palo Alto Networks recently discovered additional cases of DNS tunneling being used in malicious campaigns aimed at tracking victims and scanning networks.
The first campaign, called "TrkCdn", focuses on tracking victims interactions with phishing emails. Hackers embed content in an email that, when opened, performs a DNS query to subdomains controlled by the attackers.
These subdomains return a DNS response that leads to a server controlled by the attackers, which delivers malicious content such as ads, spam, or phishing materials.
The Unit 42 report also describes a campaign that uses DNS tunneling to track the delivery of spam messages, called "SpamTracker". This campaign is similar to TrkCdn, but is focused on monitoring spam delivery.
Another campaign discovered by analysts, called SecShow, uses DNS tunneling to scan network infrastructures. Hackers embed IP addresses and timestamps in DNS queries to map network configurations and detect potential vulnerabilities that can be exploited for intrusion, data theft, or denial of service.
Hackers choose DNS tunneling over more traditional methods to circumvent security features, avoid detection, and maintain operational flexibility.
Unit 42 researchers recommend that organizations implement DNS monitoring and analysis tools to track and analyze logs for unusual traffic patterns and anomalies, such as atypical or large queries. Experts also recommend limiting the use of DNS resolvers on the network for processing only necessary requests, in order to reduce the likelihood of DNS tunneling abuse.

