All information provided is for informational purposes only and does not encourage you to take actions that violate the law! We help you protect your confidential data.
In order for you to succeed, you should definitely subscribe to our projects in order to keep up to date with all the events.
Choosing a Stealer
The price is from$ 100 per month and up to$ 500 for a perpetual license. There are enough options. If there is not so much money, then we are looking for private software and take there within 1000-5000r any. You can't do any serious business with them, but it's good for you to get acquainted with them.
Getting logs
Purchased installations are almost identical everywhere, and 90% are simply resold from each other. I do not advise you to go and register on the stock exchange, as for me - it's not worth it. The most ideal log sources for us will be from google/facebook / email spam/shell.
Youtube will be the best option for us, the quality is higher than the exchange, and the costs will be zero if desired.
Selecting a vps for the stealer panel
Usually, when you buy a stiealer, you are immediately given recommended links to servers and the necessary characteristics. From myself, I will only add that RedLine stealer feels good on https://www.mvps.net / with a windows server for 16 euros / month.
Don't forget that your server can get banned at any time. You can use ded.im
A bare build usually has a ton of detectors, and you can get a block of the stealer license for using a non-encrypted build.
There are options for crypt through a bot, there are options directly through people.
I also recommend buying software for crypt and using it to crypt. So it will be much cheaper, and the quality will be plus/minus the same.
I will not advise any particular crypter, because if everyone uses one, then the crypt will die faster and gain detectors.
Connect to the vpn and log in https://hackforums.net/ - >Cryptography and Encryption market. Choose one. Be sure to check with the seller whether the crypter supports your stealer and preferably ask for a trial for the test. Or you can waste your money.
Checking the build / crypt for detections
You can't check anywhere, because your file can fly to the antivirus database and then you can forget about crypts, the file will instantly gain detection.
Free services:
https://antiscan.me/
https://kleenscan.com/
Paid services:
http://avcheck.net/
https://dyncheck.com/
The ideal option is to have 0 detectors. But this doesn't always happen. We will use the statistics below.
According to statistics from Stealer: more than 50% of people use windows defender, about 40% do not use antivirus software at all. The rest use Avast/kaspersky/McAfee. All other antivirus programs are very rare.
Accordingly, if you have 1-2 detekta and one of them is Windows defender-such a crypt is garbage and it will not suit us.
If we have 3-5 detectors and they are all not popular, but we see some names for the first time - this is our option if we can't completely get rid of the detectors.
dyncheck has a RunTime file check, which is more expensive, but will show a more realistic detection of your file.
Do not forget that all these checkers give only an approximate result and 2 checks in a row on the same service may have different detectors.
How to beat a bad stealer knock
A good percentage will be if you receive more than 70% of your logs. But it happens that just from scratch the knock fell. We spilled 1000 installs, but received 500 or even less.
Several reasons:
1. Your server where stillir is located has collected anti-virus detectors. This is completely normal. We periodically scan your server ip on the same sites where you check your file. If there are detections and the tap is dropped, you should change the server.
2. You need to change the port in the panel (if used).
3. Change the VPS or take a more expensive option.
4. Rewrite the file. Sometimes this happens and the rewrite helps.
5. Create a new build, especially if it was recently cleaned.
6. You are simply being deceived by someone who pours you installations.
Reducing detections/increasing detections
A small file weight has a positive effect on the number of logs, and adding an icon and cloning information from another file has a positive effect on reducing detections. Usually these functions are available in crypters or in the stealer panel.
For cloning, you should not use popular applications or files from windows folders. This can add detectors on the contrary.
Also, if your stealer drags tons of information from the computer, you may need to remove something and the percentage of knocking will increase.
Where to fill in our stealer
You can't upload the file to file sharing sites, because file sharing sites check files for viruses and you will receive bonus detectors.
You can upload the file in the archive and under a password.
For mass mailing lists, we do this:
Archive with the password +. txt file with the password is thrown into the archive and the archive itself is filled in. If we need to get a direct link to the file, then we buy a domain+hosting and upload it there. There may also be a problem that the browser will not allow you to download the file due to the fact that it is not downloaded much. We will fix this with an ssl certificate, an old domain(we buy it at auctions) , and by purchasing installations on your link.
The first thing to know is that the logs go into several hands and you need to work them out in the very near future. Or another person will do it for you. So everywhere and there are no exceptions.
If you buy two streams of 1000 installs at the same time, you get an intersection in your logs. As a result, logs will be received only from one thread, and the money for the second one will be wasted.
Buying 1000 installations and immediately after completing another 1000-you risk getting the same intersections, in the second stream there will be duplicate logs from the first stream. Buy 2000 or any desired amount in one stream at once. Or take a break between streams for at least a day.
You can always take fewer installs. 100, 250, or any other number. The price tag is indicated for 1000, respectively, for 100 you will pay 10 times less.
Don't forget that you can pause the stream or replace the file at any time(if there are detections). Do not wait until 1000 installs are spilled, if you see that you have received the desired log, then immediately pause it. Or maybe you need to leave on your own business, we also put a pause. This will help you avoid wasting your logs.
Example of a decorated stealer archive
Archive.
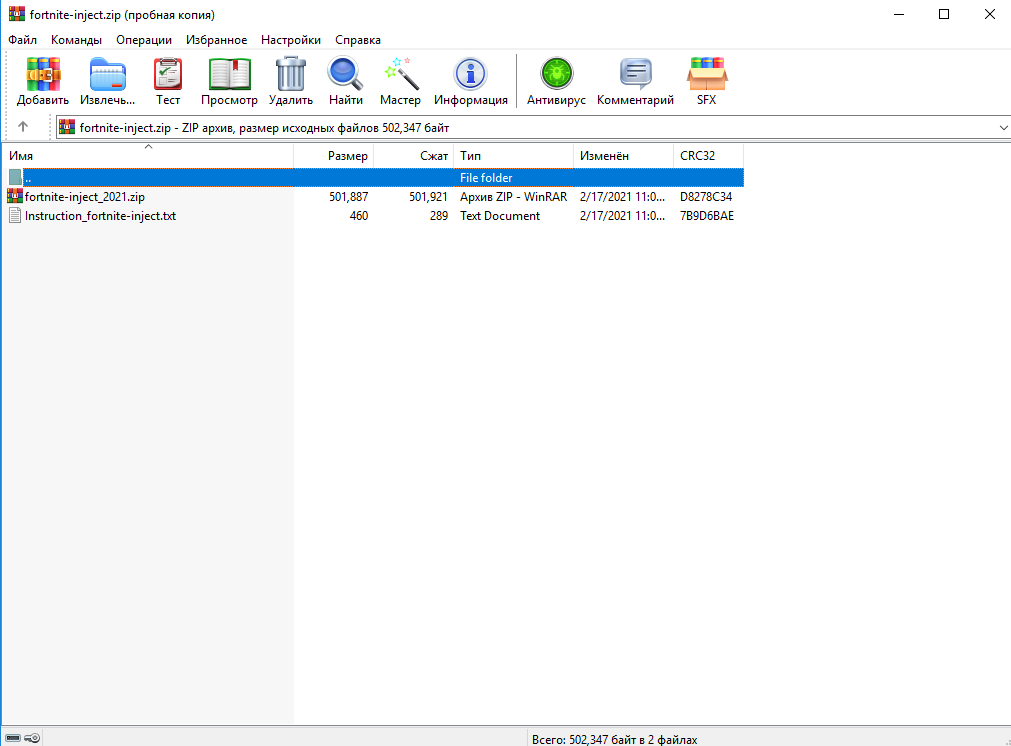
In the archive .txt file with instructions.
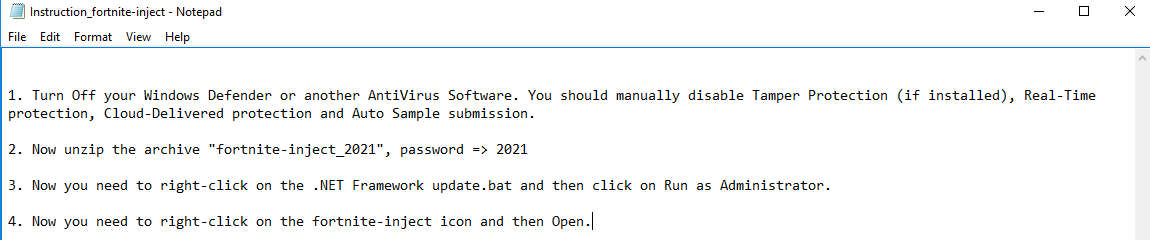
Archive with stealer and .bat file to kill windows defender. Files with a password.
The icon and description correspond to the file name.

At startup, the user receives a fake window with an error.
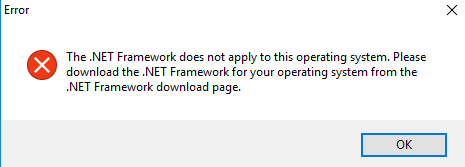

Almost any crypter has a fake error function and can add an icon\description.
Getting the logs of the countries we need
Installs are installations of your file on the user's computer. If the user is asleep and the computer is turned off, the file will not start accordingly.
Selecting night time for countries that you don't want to see in your logs. Or vice versa - we select daytime/evening time for the countries we need.
In order for you to succeed, you should definitely subscribe to our projects in order to keep up to date with all the events.
Choosing a Stealer
The price is from$ 100 per month and up to$ 500 for a perpetual license. There are enough options. If there is not so much money, then we are looking for private software and take there within 1000-5000r any. You can't do any serious business with them, but it's good for you to get acquainted with them.
Getting logs
Purchased installations are almost identical everywhere, and 90% are simply resold from each other. I do not advise you to go and register on the stock exchange, as for me - it's not worth it. The most ideal log sources for us will be from google/facebook / email spam/shell.
Youtube will be the best option for us, the quality is higher than the exchange, and the costs will be zero if desired.
Selecting a vps for the stealer panel
Usually, when you buy a stiealer, you are immediately given recommended links to servers and the necessary characteristics. From myself, I will only add that RedLine stealer feels good on https://www.mvps.net / with a windows server for 16 euros / month.
Don't forget that your server can get banned at any time. You can use ded.im
Crypting our StealerSomeone try to show me the clues)
A bare build usually has a ton of detectors, and you can get a block of the stealer license for using a non-encrypted build.
There are options for crypt through a bot, there are options directly through people.
I also recommend buying software for crypt and using it to crypt. So it will be much cheaper, and the quality will be plus/minus the same.
I will not advise any particular crypter, because if everyone uses one, then the crypt will die faster and gain detectors.
Connect to the vpn and log in https://hackforums.net/ - >Cryptography and Encryption market. Choose one. Be sure to check with the seller whether the crypter supports your stealer and preferably ask for a trial for the test. Or you can waste your money.
Checking the build / crypt for detections
You can't check anywhere, because your file can fly to the antivirus database and then you can forget about crypts, the file will instantly gain detection.
Free services:
https://antiscan.me/
https://kleenscan.com/
Paid services:
http://avcheck.net/
https://dyncheck.com/
The ideal option is to have 0 detectors. But this doesn't always happen. We will use the statistics below.
According to statistics from Stealer: more than 50% of people use windows defender, about 40% do not use antivirus software at all. The rest use Avast/kaspersky/McAfee. All other antivirus programs are very rare.
Accordingly, if you have 1-2 detekta and one of them is Windows defender-such a crypt is garbage and it will not suit us.
If we have 3-5 detectors and they are all not popular, but we see some names for the first time - this is our option if we can't completely get rid of the detectors.
dyncheck has a RunTime file check, which is more expensive, but will show a more realistic detection of your file.
Do not forget that all these checkers give only an approximate result and 2 checks in a row on the same service may have different detectors.
How to beat a bad stealer knock
A good percentage will be if you receive more than 70% of your logs. But it happens that just from scratch the knock fell. We spilled 1000 installs, but received 500 or even less.
Several reasons:
1. Your server where stillir is located has collected anti-virus detectors. This is completely normal. We periodically scan your server ip on the same sites where you check your file. If there are detections and the tap is dropped, you should change the server.
2. You need to change the port in the panel (if used).
3. Change the VPS or take a more expensive option.
4. Rewrite the file. Sometimes this happens and the rewrite helps.
5. Create a new build, especially if it was recently cleaned.
6. You are simply being deceived by someone who pours you installations.
Reducing detections/increasing detections
A small file weight has a positive effect on the number of logs, and adding an icon and cloning information from another file has a positive effect on reducing detections. Usually these functions are available in crypters or in the stealer panel.
For cloning, you should not use popular applications or files from windows folders. This can add detectors on the contrary.
Also, if your stealer drags tons of information from the computer, you may need to remove something and the percentage of knocking will increase.
Where to fill in our stealer
You can't upload the file to file sharing sites, because file sharing sites check files for viruses and you will receive bonus detectors.
You can upload the file in the archive and under a password.
For mass mailing lists, we do this:
Archive with the password +. txt file with the password is thrown into the archive and the archive itself is filled in. If we need to get a direct link to the file, then we buy a domain+hosting and upload it there. There may also be a problem that the browser will not allow you to download the file due to the fact that it is not downloaded much. We will fix this with an ssl certificate, an old domain(we buy it at auctions) , and by purchasing installations on your link.
The first thing to know is that the logs go into several hands and you need to work them out in the very near future. Or another person will do it for you. So everywhere and there are no exceptions.
If you buy two streams of 1000 installs at the same time, you get an intersection in your logs. As a result, logs will be received only from one thread, and the money for the second one will be wasted.
Buying 1000 installations and immediately after completing another 1000-you risk getting the same intersections, in the second stream there will be duplicate logs from the first stream. Buy 2000 or any desired amount in one stream at once. Or take a break between streams for at least a day.
You can always take fewer installs. 100, 250, or any other number. The price tag is indicated for 1000, respectively, for 100 you will pay 10 times less.
Don't forget that you can pause the stream or replace the file at any time(if there are detections). Do not wait until 1000 installs are spilled, if you see that you have received the desired log, then immediately pause it. Or maybe you need to leave on your own business, we also put a pause. This will help you avoid wasting your logs.
Example of a decorated stealer archive
Archive.

In the archive .txt file with instructions.

Archive with stealer and .bat file to kill windows defender. Files with a password.

The icon and description correspond to the file name.

At startup, the user receives a fake window with an error.


Almost any crypter has a fake error function and can add an icon\description.
Getting the logs of the countries we need
Installs are installations of your file on the user's computer. If the user is asleep and the computer is turned off, the file will not start accordingly.
Selecting night time for countries that you don't want to see in your logs. Or vice versa - we select daytime/evening time for the countries we need.
