How an attacker can hack your account with a single phone.
A vulnerability in the call forwarding feature allows hackers to intercept phone calls and two-factor authentication (2FA) codes with minimal interaction with the victim. This is reported by safe researcher Jamison Vincenti O'Reilly in an interview with 404 Media.
The attack mechanism consists in deceiving the user by forcing them to dial a specific phone number through a fraudulent link with the prefix " tel://", when clicked on, the number specified after the slash will be dialed.
After clicking on the link and pressing the button, the phone automatically starts dialing the number, after which the automated voice informs about the call forwarding. However, there is no authentication mechanism that guarantees that the victim really wants to set up call forwarding.
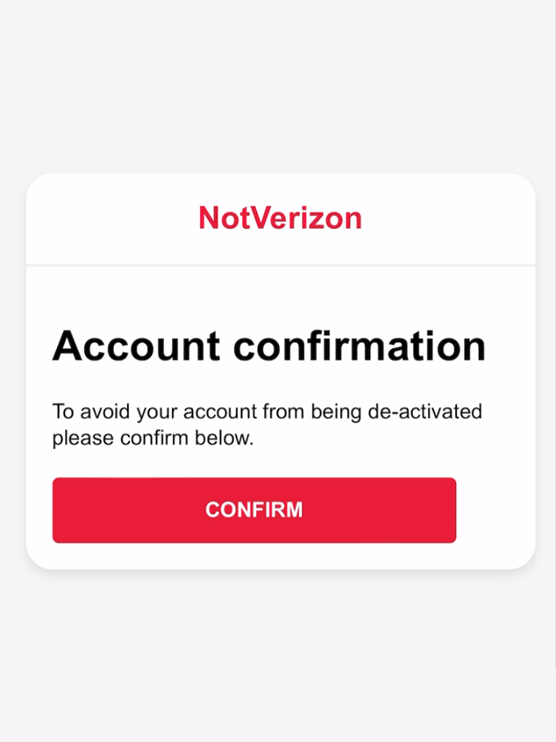
Screenshot of the phishing page. After clicking on the button, a call is made
The researcher emphasizes the severity of the threat, pointing out the possibility of intercepting not only calls, but also voice messages with two-factor authentication codes, which makes this vulnerability attractive to cybercriminals. An example is the ability to intercept authentication codes from Gmail, which are sometimes transmitted by voice.
According to a Google representative, the company restricts the use of calls in two-factor authentication only for numbers specified by the user, and recommends that you treat messages and links from unknown senders with caution.
In the video, O'Reilly explains that an attacker can call the victim by posing as a customer support agent, a representative of a telecommunications company, or an acquaintance of the victim (by forging the number). To intercept the victim's phone calls, the fraudster sends the victim a specially created SMS message asking them to call back.
Among the recommendations for eliminating the threat, the researcher suggests introducing additional authentication, for example, using PIN codes that are known only to the owner of the number. In response to the problem, Verizon, one of the carriers whose subscribers experienced the problem, expressed a serious attitude to data security and privacy issues, assuring that it will take appropriate measures to eliminate the flaw.
A vulnerability in the call forwarding feature allows hackers to intercept phone calls and two-factor authentication (2FA) codes with minimal interaction with the victim. This is reported by safe researcher Jamison Vincenti O'Reilly in an interview with 404 Media.
The attack mechanism consists in deceiving the user by forcing them to dial a specific phone number through a fraudulent link with the prefix " tel://", when clicked on, the number specified after the slash will be dialed.
After clicking on the link and pressing the button, the phone automatically starts dialing the number, after which the automated voice informs about the call forwarding. However, there is no authentication mechanism that guarantees that the victim really wants to set up call forwarding.

Screenshot of the phishing page. After clicking on the button, a call is made
The researcher emphasizes the severity of the threat, pointing out the possibility of intercepting not only calls, but also voice messages with two-factor authentication codes, which makes this vulnerability attractive to cybercriminals. An example is the ability to intercept authentication codes from Gmail, which are sometimes transmitted by voice.
According to a Google representative, the company restricts the use of calls in two-factor authentication only for numbers specified by the user, and recommends that you treat messages and links from unknown senders with caution.
In the video, O'Reilly explains that an attacker can call the victim by posing as a customer support agent, a representative of a telecommunications company, or an acquaintance of the victim (by forging the number). To intercept the victim's phone calls, the fraudster sends the victim a specially created SMS message asking them to call back.
Among the recommendations for eliminating the threat, the researcher suggests introducing additional authentication, for example, using PIN codes that are known only to the owner of the number. In response to the problem, Verizon, one of the carriers whose subscribers experienced the problem, expressed a serious attitude to data security and privacy issues, assuring that it will take appropriate measures to eliminate the flaw.
