The new "Steal-It" operation leaves no chance for the safety of confidential data.
A sophisticated malware operation known as "Steal-It" targets specific victims in Australia by using explicit images of models from the OnlyFans platform as bait. This is reported in a recent report by Zscaler researchers.
According to the study, the APT28 group, also known as Fancy Bear, is most likely behind the cyberattack. This group became famous for its interference in the American elections in 2016.
The "Steal-It" malware campaign discussed in Zscaler includes several different variations that differ in the tools used and the end goals.
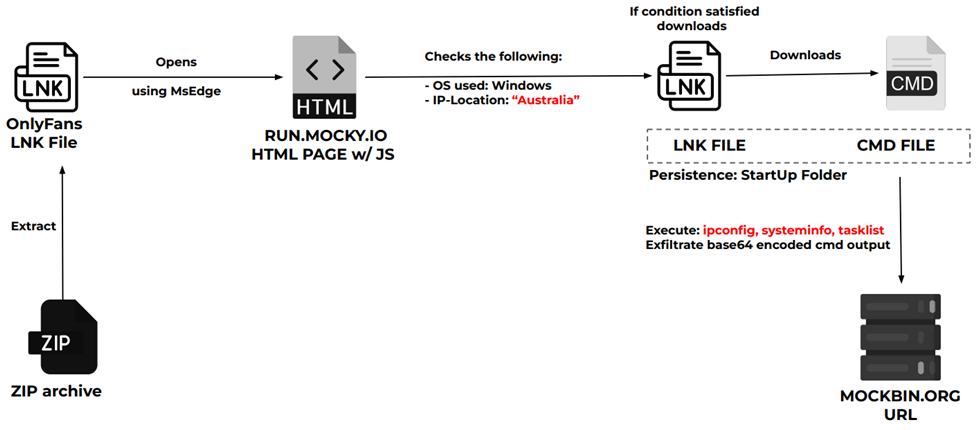
The initial phase of the malicious operation with OnlyFans bait begins with the victim downloading a ZIP archive with the name "best_tits.zip", which contains the malicious label "onlyfans.com-1.lnk".
Once executed, the malicious LNK file runs a command that opens the Microsoft Edge browser with a specific base64-encoded argument. This argument is a single-line JavaScript code that redirects the victim to an attacker's site that also contains malicious code.
To hide the malicious redirect, the malicious command also opens the real OnlyFans website in a different tab and pauses the script execution for 9 seconds.
After a short pause, the JavaScipt code opened on the background page performs a series of checks and starts performing malicious actions. So, if the victim's operating system is Windows and the victim's country of location is Australia, the code initiates downloading another malicious shortcut named "m8. lnk", which is immediately launched and placed in the Windows startup folder to establish persistence.
The code in the newly uploaded shortcut secretly collects system information about the victim's computer and sends it to attackers using the API of the legitimate Mockbin tool, simultaneously removing traces of its work from the target system.
Infection chain
Malicious campaigns that use explicit content to lure users are a very clever and cynical way to manipulate people. Although the curiosity of human nature can be understood, it is important to exercise caution and not fall for such tricks.
Cybercriminals often exploit our weaknesses, but we don't have to go along with them. Be vigilant and think about the consequences before opening suspicious files. After all, our online security depends primarily on ourselves.
A sophisticated malware operation known as "Steal-It" targets specific victims in Australia by using explicit images of models from the OnlyFans platform as bait. This is reported in a recent report by Zscaler researchers.
According to the study, the APT28 group, also known as Fancy Bear, is most likely behind the cyberattack. This group became famous for its interference in the American elections in 2016.
The "Steal-It" malware campaign discussed in Zscaler includes several different variations that differ in the tools used and the end goals.
The initial phase of the malicious operation with OnlyFans bait begins with the victim downloading a ZIP archive with the name "best_tits.zip", which contains the malicious label "onlyfans.com-1.lnk".
Once executed, the malicious LNK file runs a command that opens the Microsoft Edge browser with a specific base64-encoded argument. This argument is a single-line JavaScript code that redirects the victim to an attacker's site that also contains malicious code.
To hide the malicious redirect, the malicious command also opens the real OnlyFans website in a different tab and pauses the script execution for 9 seconds.
After a short pause, the JavaScipt code opened on the background page performs a series of checks and starts performing malicious actions. So, if the victim's operating system is Windows and the victim's country of location is Australia, the code initiates downloading another malicious shortcut named "m8. lnk", which is immediately launched and placed in the Windows startup folder to establish persistence.
The code in the newly uploaded shortcut secretly collects system information about the victim's computer and sends it to attackers using the API of the legitimate Mockbin tool, simultaneously removing traces of its work from the target system.

Infection chain
Malicious campaigns that use explicit content to lure users are a very clever and cynical way to manipulate people. Although the curiosity of human nature can be understood, it is important to exercise caution and not fall for such tricks.
Cybercriminals often exploit our weaknesses, but we don't have to go along with them. Be vigilant and think about the consequences before opening suspicious files. After all, our online security depends primarily on ourselves.
