How to become a victim of hackers in a couple of clicks.
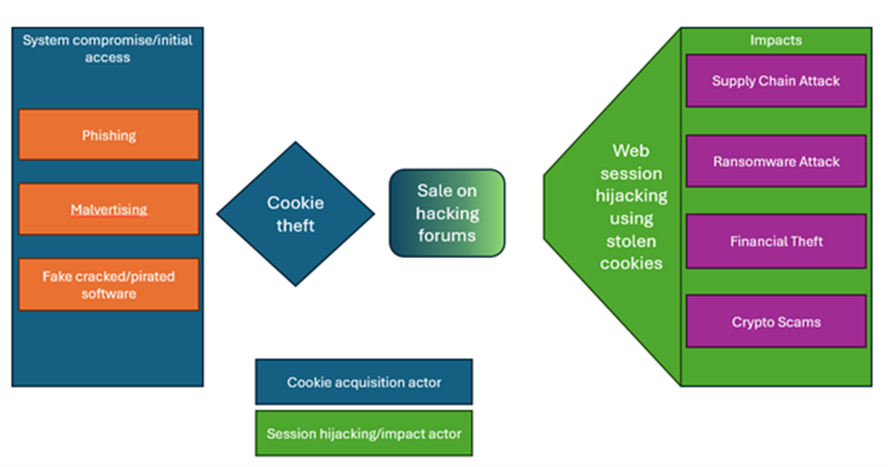
CyberArc experts report that attackers are developing new methods for accessing users personal data that do not require knowledge of passwords or multi-factor authentication requests. One of the most common techniques is to intercept web sessions by stealing cookies, which is made possible by the use of infostealers.
The main methods of infection are phishing, malicious advertising on Google and social networks, and imitation of pirated software, including programs and cheats for games. As soon as a user opens a malicious application, malware begins to act, targeting login data and sessions of various applications. The stolen data is sent to the attacker's server for further use or sale on various forums on the darknet or the public Internet.
Infostealer infection chain
The consequences of data theft can range from creating targeted attacks to accessing the company's code base or organizing attacks on the supply chain. In addition, stolen cookies can serve as entry points for ransomware operators, which leads to data leakage and halting operations.
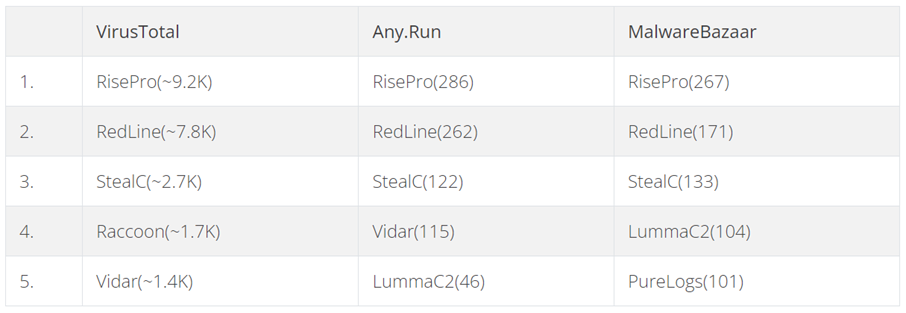
According to VirusTotal, Any.Run, and Malware Bazaar data for February 2024, the most successful stylers are RisePro, RedLine, StealC, LummaC, and Vidar. In addition to cookies, malware often steals other important browser files, as well as data from the Telegram, Discord, and Steam apps.
Top 5 infostealers by prevalence (according to MalwareBazaar)
RisePro stands out among others for its prevalence and leaves behind files such as "passwords.txt" which makes it easier for researchers and incident responders to identify the type of malware.
StealC is interesting because part of its configuration is stored on the server side, which is unique among this kind of malware.
LummaC2, although only ranked in one distribution rating, deserves attention because of its innovative approach to distribution and protection from analysis.
To minimize risks, it is important to raise awareness among users about the risks of downloading software from untrusted sources, as well as use solutions to prevent the launch of malware. In the era of digitalization, it is important not only to implement the latest security technologies, but also to maintain a high level of vigilance to protect against theft of credentials and sessions.
CyberArc experts report that attackers are developing new methods for accessing users personal data that do not require knowledge of passwords or multi-factor authentication requests. One of the most common techniques is to intercept web sessions by stealing cookies, which is made possible by the use of infostealers.
The main methods of infection are phishing, malicious advertising on Google and social networks, and imitation of pirated software, including programs and cheats for games. As soon as a user opens a malicious application, malware begins to act, targeting login data and sessions of various applications. The stolen data is sent to the attacker's server for further use or sale on various forums on the darknet or the public Internet.

Infostealer infection chain
The consequences of data theft can range from creating targeted attacks to accessing the company's code base or organizing attacks on the supply chain. In addition, stolen cookies can serve as entry points for ransomware operators, which leads to data leakage and halting operations.
According to VirusTotal, Any.Run, and Malware Bazaar data for February 2024, the most successful stylers are RisePro, RedLine, StealC, LummaC, and Vidar. In addition to cookies, malware often steals other important browser files, as well as data from the Telegram, Discord, and Steam apps.

Top 5 infostealers by prevalence (according to MalwareBazaar)
RisePro stands out among others for its prevalence and leaves behind files such as "passwords.txt" which makes it easier for researchers and incident responders to identify the type of malware.
StealC is interesting because part of its configuration is stored on the server side, which is unique among this kind of malware.
LummaC2, although only ranked in one distribution rating, deserves attention because of its innovative approach to distribution and protection from analysis.
To minimize risks, it is important to raise awareness among users about the risks of downloading software from untrusted sources, as well as use solutions to prevent the launch of malware. In the era of digitalization, it is important not only to implement the latest security technologies, but also to maintain a high level of vigilance to protect against theft of credentials and sessions.
