The simulation environment will allow you to create invulnerable devices that do not need additional protection.
MITRE Corporation has introduced a new threat modeling framework, EMB3D, designed for manufacturers of embedded devices used in mission-critical infrastructures. The model provides a unified knowledge base about cyber threats, which allows you to better understand threats and the necessary security measures to prevent them.
EMB3D, like ATT&CK, is a "live model" to which new vulnerabilities and methods for their elimination will be added and updated as new threat actors, vulnerabilities, and attack vectors become available. However, EMB3D is specifically focused on embedded devices.
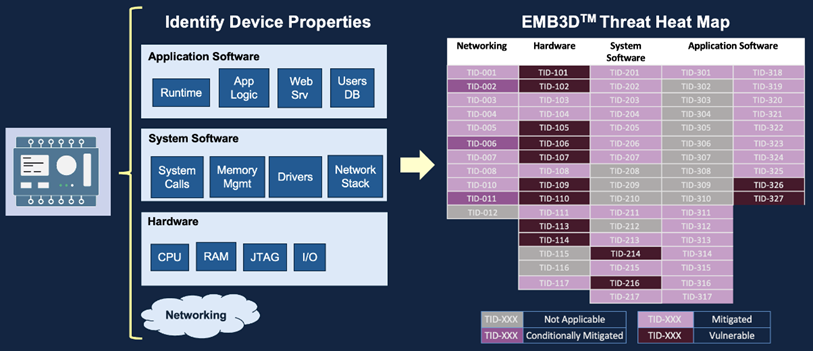
Comparison of disadvantages and individual device characteristics
The main goal of the model is to provide device manufacturers with a unified view of the various vulnerabilities in their technologies that are subject to attacks, and the security mechanisms to eliminate them. Just as ATT&CK offers a unified mechanism for tracking and communicating threat information, EMB3D aims to offer a central knowledge base for threats targeting embedded devices.
The EMB3D model will provide manufacturers of automated process control devices with the ability to understand the changing threat landscape and potential available mitigation methods early in the design cycle, leading to more secure devices. This concept will reduce the need to add post-production security measures, resulting in a more secure infrastructure and lower security costs.
When releasing the model, the main idea is to adopt a Secure by Design approach, allowing companies to release products with minimal vulnerabilities and secure default configurations.
The EMB3D model provides a detailed knowledge base about cyber threats, including those that are observed in real-world operating conditions or demonstrated through PoC. Threats are correlated with device characteristics to help users develop accurate threat models for specific devices. For each threat, technical security measures are proposed that manufacturers must implement to ensure the security of the device.
MITRE Corporation has introduced a new threat modeling framework, EMB3D, designed for manufacturers of embedded devices used in mission-critical infrastructures. The model provides a unified knowledge base about cyber threats, which allows you to better understand threats and the necessary security measures to prevent them.
EMB3D, like ATT&CK, is a "live model" to which new vulnerabilities and methods for their elimination will be added and updated as new threat actors, vulnerabilities, and attack vectors become available. However, EMB3D is specifically focused on embedded devices.

Comparison of disadvantages and individual device characteristics
The main goal of the model is to provide device manufacturers with a unified view of the various vulnerabilities in their technologies that are subject to attacks, and the security mechanisms to eliminate them. Just as ATT&CK offers a unified mechanism for tracking and communicating threat information, EMB3D aims to offer a central knowledge base for threats targeting embedded devices.
The EMB3D model will provide manufacturers of automated process control devices with the ability to understand the changing threat landscape and potential available mitigation methods early in the design cycle, leading to more secure devices. This concept will reduce the need to add post-production security measures, resulting in a more secure infrastructure and lower security costs.
When releasing the model, the main idea is to adopt a Secure by Design approach, allowing companies to release products with minimal vulnerabilities and secure default configurations.
The EMB3D model provides a detailed knowledge base about cyber threats, including those that are observed in real-world operating conditions or demonstrated through PoC. Threats are correlated with device characteristics to help users develop accurate threat models for specific devices. For each threat, technical security measures are proposed that manufacturers must implement to ensure the security of the device.
