The complexity and targeting of attacks has increased compared to 2023.
Kaspersky ICS CERT experts analyzed the dynamics of cyber attacks on industrial systems in the first quarter of 2024. According to their data, the share of Russian computers of automated control systems (ACS) on which malicious objects were blocked was 23.6%. This indicator has decreased by 4.3 percentage points compared to the first quarter of 2023, but the attacks themselves are becoming more complex and targeted.
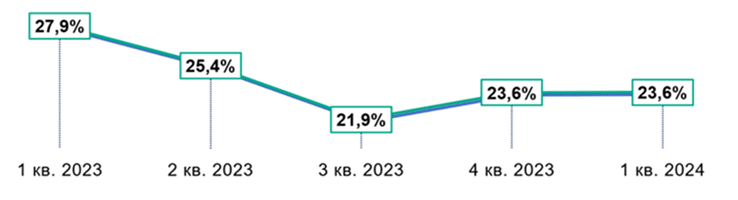
Percentage of automated control system computers in Russia where malicious objects were blocked, by quarter
In a number of industries, the share of automated control systems attacked in Russia exceeded the global average. In particular, in construction it was 24.2% against 23.7% in the world, and for engineering companies and automated control system integrators-27.2% against 24%, respectively. Attackers actively exploit the channel of suppliers and partners, attacking integrators and contractors, which is especially noticeable in Russia.
Phishing via Internet sites and e-mail is still one of the main vectors of initial compromise of systems. In the first quarter of 2024 in Russia, malicious resources were blocked on 7.5% of automated control system computers. A significant part of them was used to distribute malicious scripts and phishing pages, which were blocked on 4.6% of the automated control system.
Kaspersky ICS CERT notes that a successful attack on industrial systems can lead to a production shutdown, disruptions in logistics chains, and even cause harm to people and the environment. Attackers are improving their cyberattack tactics, but the human factor remains the main vulnerability - employees are caught in phishing mailings or violate cybersecurity requirements.
For reliable protection, Kaspersky Lab's automated Control System recommends timely software updates and installing patches, conducting security audits, using network traffic monitoring tools, training staff, applying state-of-the-art solutions for threat analysis and end-device protection, and ensuring the security of the corporate IT infrastructure.
Kaspersky ICS CERT experts analyzed the dynamics of cyber attacks on industrial systems in the first quarter of 2024. According to their data, the share of Russian computers of automated control systems (ACS) on which malicious objects were blocked was 23.6%. This indicator has decreased by 4.3 percentage points compared to the first quarter of 2023, but the attacks themselves are becoming more complex and targeted.

Percentage of automated control system computers in Russia where malicious objects were blocked, by quarter
In a number of industries, the share of automated control systems attacked in Russia exceeded the global average. In particular, in construction it was 24.2% against 23.7% in the world, and for engineering companies and automated control system integrators-27.2% against 24%, respectively. Attackers actively exploit the channel of suppliers and partners, attacking integrators and contractors, which is especially noticeable in Russia.
Phishing via Internet sites and e-mail is still one of the main vectors of initial compromise of systems. In the first quarter of 2024 in Russia, malicious resources were blocked on 7.5% of automated control system computers. A significant part of them was used to distribute malicious scripts and phishing pages, which were blocked on 4.6% of the automated control system.
Kaspersky ICS CERT notes that a successful attack on industrial systems can lead to a production shutdown, disruptions in logistics chains, and even cause harm to people and the environment. Attackers are improving their cyberattack tactics, but the human factor remains the main vulnerability - employees are caught in phishing mailings or violate cybersecurity requirements.
For reliable protection, Kaspersky Lab's automated Control System recommends timely software updates and installing patches, conducting security audits, using network traffic monitoring tools, training staff, applying state-of-the-art solutions for threat analysis and end-device protection, and ensuring the security of the corporate IT infrastructure.
