Speaking at the Virus Bulletin conference, Intezer Labs analysts talked about which freely available tools (including open source ones) are most often abused by hackers. These tools can include various applications, libraries, exploits, and so on. Most often, we are talking about proof-of-concept exploits for vulnerabilities that are published by information security specialists, or freely available pentester utilities.
The existence of such tools has long been considered a very controversial phenomenon in the information security community. So, on the one hand, such tools can help information security experts prepare systems and networks, protecting them from potential attacks. On the other hand, they help attackers reduce the cost and time of developing their own tools, and also allow them to disguise their activity among legitimate tests and pentests.
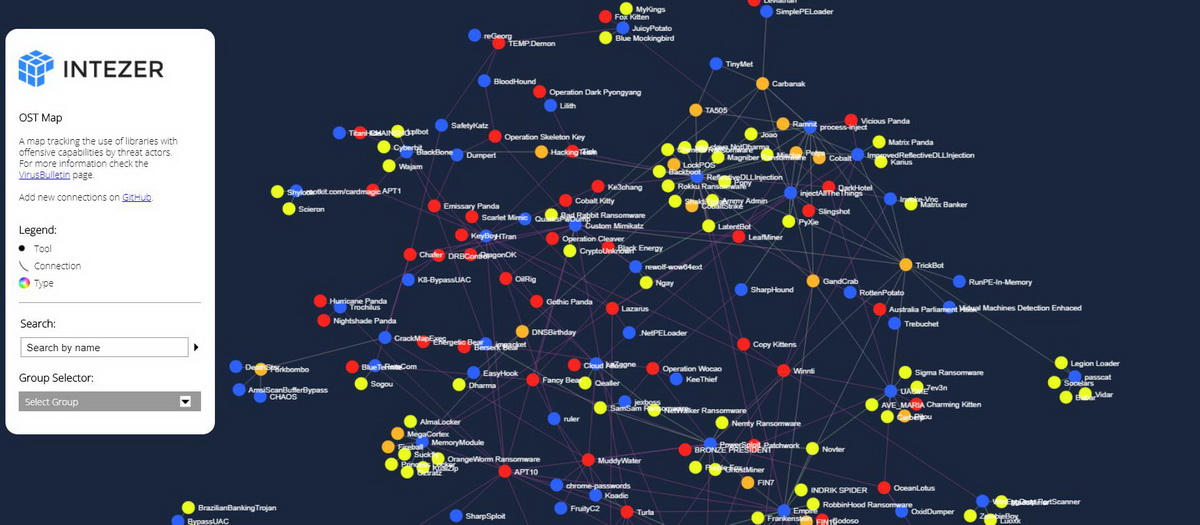
Intezer Labs experts say that usually debates on this topic are conducted based on the personal experience and beliefs of the participants in the discussion, and not on real data. The company decided to go the other way and collected data on 129 open source "offensive" tools, and then compared this data with malware samples and reports from colleagues to find out how widespread the use of such solutions among hackers is. The results were combined in this interactive map.
As it turned out, open source and just publicly available solutions are actively used by attackers of all stripes, from well-known government hack groups to small fraudsters. Many tools and libraries originally developed by cybersecurity researchers are now routinely used for cybercrime.
“We found the most popular libraries for memory injection and RAT tools. Thus, the most popular tool for memory injection is the ReflectiveDllInjection library, followed by the MemoryModule library. Empire, Powersploit and Quasar turned out to be the most popular among the RAT tools, ”said Intezer Labs.
It is also reported that Mimikatz is most often used for lateral movement, and UACME library is usually used to bypass UAC. That being said, Asian hacker groups are more likely to prefer Win7Elevate, most likely due to the large number of Windows 7 installations in the region.
Basically, only credential theft tools are not popular with criminals. Researchers believe that the reason is the availability of similar solutions with broader functionality on the black market and hacker forums.
In addition, Intezer Labs noticed that criminals rarely use tools that implement complex functions that require deep understanding for exploitation (even if their benefits are obvious). Therefore, the company believes that cybersecurity experts who plan to publish "offensive" hacking tools should keep this in mind and deliberately complicate their code to make it more difficult for attackers.
