Now hackers not only steal from the victim, but also extort money from her.
Cybersecurity researchers from the information security company Trend Micro published a new analysis, according to which infostealer operators RedLine and Vidar have started using ransomware in their phishing campaigns. Attacks start with phishing emails that spread malicious attachments disguised as PDF or JPG files.
Experts note that in one investigated incident, an unnamed victim first downloaded an infostealer signed with Extended Validation Certificate (EV) code signing certificates, and then downloaded a ransomware program that was delivered in the same way.
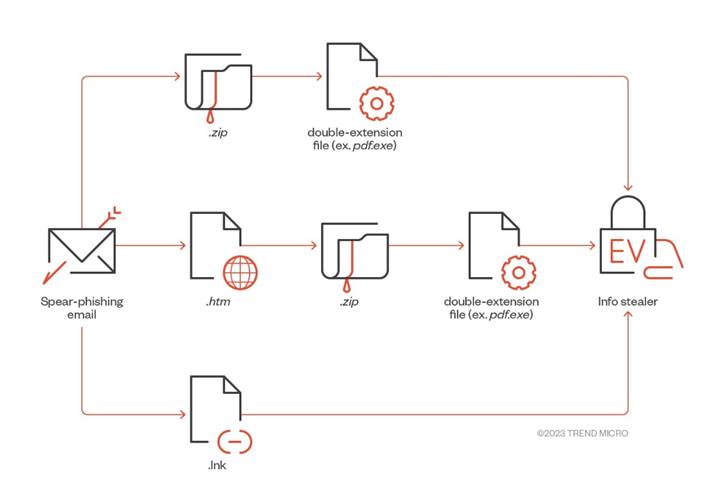
Infostealer infection chain
It is worth noting that, unlike the infostealer samples, the files used to deploy the ransomware did not have EV certificates. However, both types of malware originate from the same threat actor and are distributed in the same way, which suggests a division of labor between the "provider" of the payload and the operators.
Cybersecurity researchers from the information security company Trend Micro published a new analysis, according to which infostealer operators RedLine and Vidar have started using ransomware in their phishing campaigns. Attacks start with phishing emails that spread malicious attachments disguised as PDF or JPG files.
Experts note that in one investigated incident, an unnamed victim first downloaded an infostealer signed with Extended Validation Certificate (EV) code signing certificates, and then downloaded a ransomware program that was delivered in the same way.

Infostealer infection chain
It is worth noting that, unlike the infostealer samples, the files used to deploy the ransomware did not have EV certificates. However, both types of malware originate from the same threat actor and are distributed in the same way, which suggests a division of labor between the "provider" of the payload and the operators.
