CoralRaider improves malware to bypass protection.
According to a new report from Cisco Talos, the CoralRaider group uses CDNs to distribute malware in the United States, Great Britain, Germany, and Japan. The campaign is aimed at stealing credentials, financial information, and social media accounts.
CoralRaider uses LummaC2, Rhadamanthys, and Cryptbot infostilers that are widely available on shadow forums and distributed using the RAAS (Ransomware-as-a-Service) model. Based on an analysis of previous attacks, experts with an "average level of confidence" attribute the CoralRaider campaign.
Infection begins when the victim opens an archive with a malicious LNK shortcut that downloads and executes an encrypted HTA application from a subdomain controlled by hackers on the CDN Bynny platform. By using the CDN cache as a malware delivery server, the hacker avoids request delays and also bypasses network protection.
Then, through a number of PowerShell scripts and auxiliary utilities, such as FoDHelper.exe, changes the system settings to bypass User Access Control (UAC) and adds Windows Defender antivirus to exceptions.
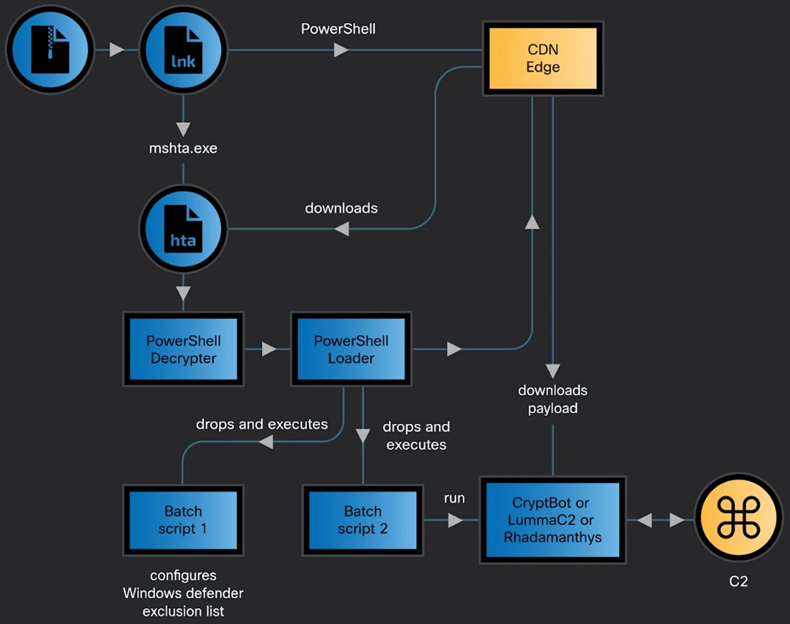
CoralRaider Infection Chain
The malware versions used include new features such as:
interception of RDP session data and recovery of expired Google account cookies (LummaC2 and Rhadamanthys);
advanced obfuscation and antianalysis mechanisms (LummaC2 and Rhadamanthys);
an expanded list of targeted applications, including password managers and authentication applications, which also threatens cryptocurrency wallets with two-factor authentication (CryptBot).
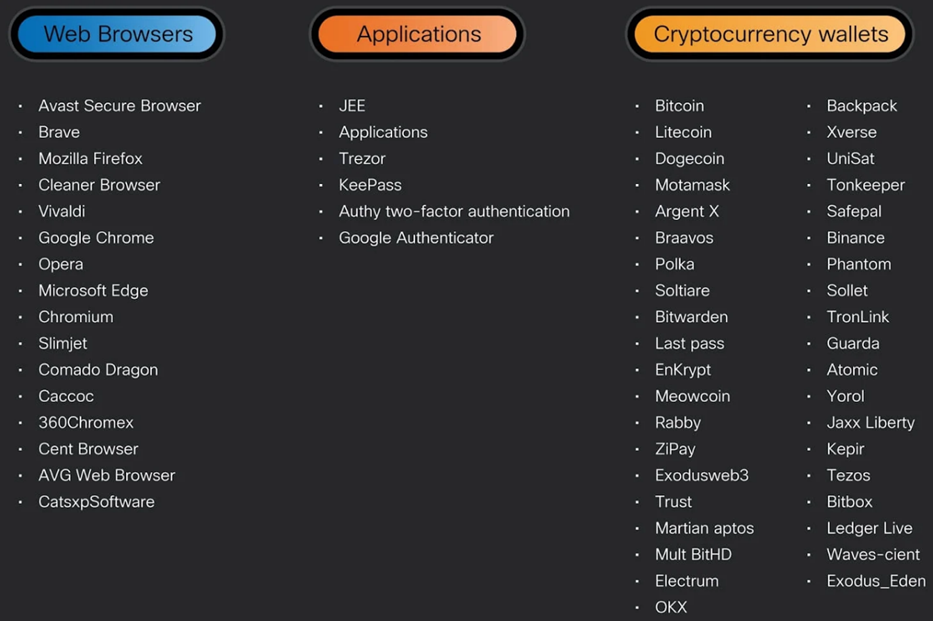
Apps targeted by the latest version of Cryptbot
According to the researchers, the CoralRaider group, presumably based in Vietnam, has been active since 2023 and previously used a Telegram bot to manage and exfiltrate data. While earlier attacks have more often focused on Asian and Southeast Asian countries, the latest operations cover a wider range of countries, including the United States, Nigeria, Pakistan, Ecuador, Egypt, the United Kingdom, Poland, the Philippines, Norway, Japan, Syria, and Turkey.
According to a new report from Cisco Talos, the CoralRaider group uses CDNs to distribute malware in the United States, Great Britain, Germany, and Japan. The campaign is aimed at stealing credentials, financial information, and social media accounts.
CoralRaider uses LummaC2, Rhadamanthys, and Cryptbot infostilers that are widely available on shadow forums and distributed using the RAAS (Ransomware-as-a-Service) model. Based on an analysis of previous attacks, experts with an "average level of confidence" attribute the CoralRaider campaign.
Infection begins when the victim opens an archive with a malicious LNK shortcut that downloads and executes an encrypted HTA application from a subdomain controlled by hackers on the CDN Bynny platform. By using the CDN cache as a malware delivery server, the hacker avoids request delays and also bypasses network protection.
Then, through a number of PowerShell scripts and auxiliary utilities, such as FoDHelper.exe, changes the system settings to bypass User Access Control (UAC) and adds Windows Defender antivirus to exceptions.

CoralRaider Infection Chain
The malware versions used include new features such as:
interception of RDP session data and recovery of expired Google account cookies (LummaC2 and Rhadamanthys);
advanced obfuscation and antianalysis mechanisms (LummaC2 and Rhadamanthys);
an expanded list of targeted applications, including password managers and authentication applications, which also threatens cryptocurrency wallets with two-factor authentication (CryptBot).

Apps targeted by the latest version of Cryptbot
According to the researchers, the CoralRaider group, presumably based in Vietnam, has been active since 2023 and previously used a Telegram bot to manage and exfiltrate data. While earlier attacks have more often focused on Asian and Southeast Asian countries, the latest operations cover a wider range of countries, including the United States, Nigeria, Pakistan, Ecuador, Egypt, the United Kingdom, Poland, the Philippines, Norway, Japan, Syria, and Turkey.
