
A kind of trigger that caused the appearance of this article was a huge number of publications in a wide variety of publications, including quite technical ones. All these publications, without a single exception, sadly repeat the same mantra: use a strong lock code, turn on the fingerprint sensor, turn off Smart Lock, turn on two-factor authentication, update to the latest available OS version ... Let's not argue, all these things must be done - but absolutely, absolutely not enough.
You can choose the strongest lock code, but if your phone uses FDE encryption and you have not enabled Secure Startup, then the lock code can be at least a hundred characters long - encryption will still use the default_password phrase. Disabling Smart Lock is a necessary but insufficient step; Are you sure of the safety of the face scanning technology used in your device (if the phone is equipped with it)? Did you know that by simply logging into your computer, you can extract all your cloud passwords, and then simply reset the smartphone lock code? (Fortunately, it does not work for all devices, but you need to know about this possibility.) Finally, you need to be aware that if a password from the cloud (Google, Apple or Samsung) is received from your computer, then the phone itself will not be needed: the expert will extract all the necessary data from the cloud (and, most likely, there will be even more of them than in the phone itself).
In this article, we will not give sore advice "enable the lock code" or "upgrade to the latest version of the OS" (of course, you have already done this). Instead, we will try to provide an understanding of the full range of capabilities of "heavy artillery" that can be used against the owner of the phone by law enforcement and intelligence agencies to extract data.
As you know, the most difficult cases for experts to work - a de-energized telephone found in a silent body. It is in such circumstances that the search for all kinds of vulnerabilities in software and hardware usually begins. In ordinary situations, the police will come to the suspect's home, analyze the computer and retrieve the password cache from email clients and Chrome / Mozilla / Edge browsers. Then it is enough to go to the cloud with the found username and password, after which the rest is trivial. In some cases, you can remotely reset the lock password on your phone (today, fortunately, many manufacturers do not offer this by default). The phone can be connected to the "octopus" UFED,
After reading this article, you will become more fully aware of the opportunities to protect your data and the risks that remain even when you did everything right.
How your iPhone will be jailbroken
The difficulty of jailbreaking an iPhone differs depending on a number of factors. The first factor: the installed version of iOS (don't you think that the tips to "update to the latest available version" appeared out of the blue?), The complexity of the lock code and the state of the device (about it - below).First, about the iOS versions. If you still have any version of iOS 11 installed, I have bad news for you: for this OS, both brute-force cracking of the lock code and complete (and very fast) information retrieval through physical access are available. The complexity of the lock code and the state of the device (on / off, whether the USB restricted mode is activated, etc.) will affect the brute-force speed.
How will the iPhone with iOS 11 be jailbroken
If the phone was switched off: the speed of brute-forcing passwords will be very slow (one attempt every ten seconds). If you set a six-digit lock code, it will take forever to sort through it.If the phone was turned on and you unlocked it at least once after turning it on: the first 300,000 passwords will be tried very quickly; the brute-force speed is such that a four-digit lock code can be cracked within half an hour in a fully automatic mode. Output? Use a six-digit password.
If you managed to use the SOS mode (by holding down the power button and the volume button): the phone again switches to the "slow" search mode. The six-digit lock code is excellent protection in this case.
Finally, iOS 11.4.1 introduced USB restricted mode, which allows you to protect your device from hacking by brute-force passwords. Within an hour after the last unlocking, iOS will disable access to the USB port, after which it will become impossible to brute force passwords. In order for the protection to work, you need to leave the USB Accessories switch in the "off" position. However, recently rumors have been actively circulating that the developers of forensic systems have succeeded or are about to be able to bypass this protection. Output? Finally, upgrade to iOS 12!
How will the iPhone with iOS 12 be jailbroken
The iOS 12 situation is pretty interesting. Apple managed to close a number of vulnerabilities that made it possible to brute-force passwords on devices with iOS 11. Moreover, the USB restricted mode has been improved: now the USB port (or rather, the ability to transfer data through the physical Lightning connector) is disabled immediately as soon as you will lock the device screen. True, only if you have not connected your phone to a computer, wired audio system or other accessories for at least three days; if connected, it will be as before - in an hour. In addition, the USB port is now disabled when calling SOS mode (hold down the power and volume buttons).On the other hand, iOS 12 contains vulnerabilities that migrated to the system from the 11th version of the OS. In iOS 12 up to version 12.1.2, two important vulnerabilities were not closed, allowing, through privilege escalation, to gain full access to the file system without installing a full-fledged jailbreak. Accordingly, if a phone with iOS 12.1.2 or older falls into the hands of experts in an unlocked state, the data from it will fly away with a whistle. In iOS 12.1.3, some of the vulnerabilities were closed (not all: GrayKey is still able to extract an image of the file system), but only iOS 12.1.4, which was released just the other day, was able to completely secure devices from exploits known to date. Output? There is still something in the advice “update to the latest firmware version available”!
So, how exactly will they try to jailbreak your iPhone running iOS 12?
The safest option for you is if your phone falls into the hands of an expert when it is turned off. In this case, it will not be possible to start the search - at least until the developers figure out how to bypass the USB protection mode (by the way, they haven't figured it out yet).
If the phone was turned on and unlocked at least once after turning it on (but locked at the time of hacking), then you will not be able to do anything useful with it either. Yes, you can try connecting it to your computer to create a backup via iTunes; if you didn't manage to activate USB Protective Mode and if you've connected your iPhone to iTunes at least once, then the attempt may be successful. How to protect yourself? Set a long and complex password for your backup.
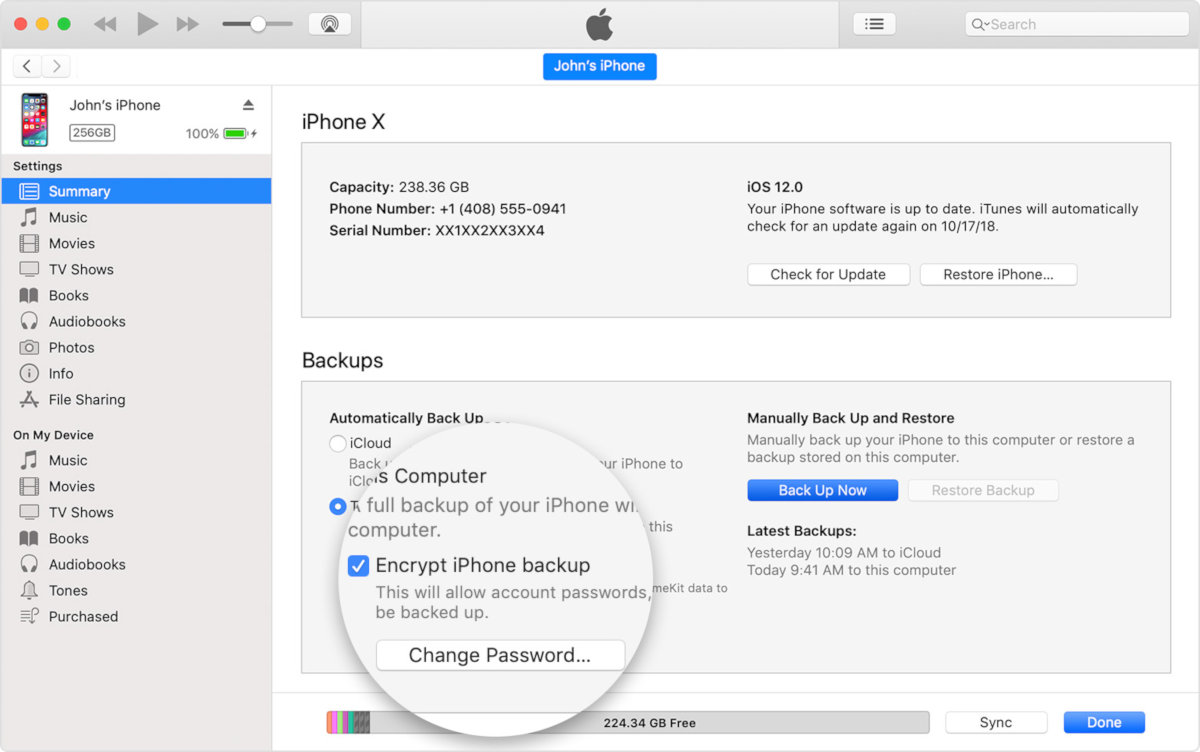
Yes, in iOS 12 (and in iOS 11) this password can be reset - but only from the iPhone itself and only if the lock code is known. Even then, you can further protect your password from being reset by setting a Screen Time password.
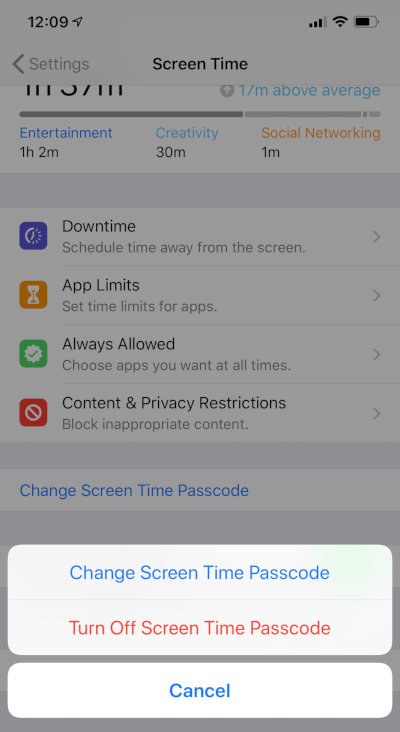
Screen Time password is not a panacea. Generally speaking, this is "child" protection, the function of protection against password reset for a backup copy is secondary in it. Nevertheless, it will not be possible to bypass it even by brute force: iOS will increase the delays until the brute force rate drops to one attempt per hour (starting from the tenth attempt).
If you took your unlocked phone
In an ideal world, the police would have to show their technical skills and use shiny devices just to try to hack your smartphone. In most cases, the police will simply try to extract as much information from your smartphone as possible within the framework of their powers in the shortest possible time. In a confident voice, “ask” to unlock the phone, and then take the unlocked phone to a separate room is the most typical case for (don't flatter yourself) petty offenders. Let's see what iOS can do to protect your data in this case.So, introductory: the iPhone is unlocked and handed over to the employee, but you did not give the lock code. (In brackets: and don't tell me if you don't have such a duty in the event of a routine detention.) What will happen next?
First, an employee can simply manually view the sections of interest in the device. Here are postings on social networks (I'm sure they won't find anything on you, but the article for likes is quite flexible), correspondence, SMS / iMessage messages, and, of course, photos.
The data of the "Health" application will be extracted, from which it will be possible to draw conclusions about what exactly you did at one time or another (in particular, it will be seen whether you were moving or sitting still, and if you were moving, then whether you were running). We know of more than one, not two, or even a dozen cases when routine detention suddenly turned into arrest and indictment based on information found in a smartphone.
How to protect yourself from analysis in this mode? No way, just not hand over the unlocked device to the police. You cannot refuse to give the phone at all, but to refuse to unlock it is still your right (there are exceptions, for example, when crossing the border; we wrote about them). Here we note that even on a device with an unlocked screen without a lock code, you will not be able to view passwords from the "keychain", or disable Find My iPhone, or reset the password from an iTunes backup, if you have set it, or even connect your phone to a computer: this now also requires a lock code.
Secondly, the phone can be connected to the GrayKey complex or the like (though there are actually no “similar” ones, but you never know? What if the Chinese hard drive duplicators learn to hack the iPhone?). In this case, only a fresh version of iOS can save: we recall that up to iOS 12.1.3 inclusive, there is no problem in order to extract an image of the file system from the device. The vulnerability was closed in iOS 12.1.4. How long? Not yet known.
Finally, they might try to extract data from the phone as a backup. To do this, you will at least need to connect your phone to your computer, for which an expert will need a screen lock code. You can try to get around this point by using the lockdown file from your computer. However, if you set a password for the backup and protect it from being reset using the Screen Time password, you can completely protect yourself from this side.
Output? If you have unlocked your iPhone and your phone is running the latest version of iOS (today it is 12.1.4), the employee will most likely have to confine himself to a “manual” analysis on the phone's screen.
How your Android smartphone will be hacked
As with the iPhone, the police will try to force you to unlock the device. If they succeed and you hand over the unlocked phone to the police, relax: the further does not depend on you; you gave everything you could. Unlike iOS, which tries to somehow protect you even in such situations, the investigator will receive from the screen of an unlocked smartphone:- of course, access to all contents of the memory card (virtual and real), including photos and videos;
- mail, correspondence in messengers, SMS texts;
- a complete list of passwords saved in Chrome (you can often find the password for your Google Account there - by the way, check if this is so);
- detailed location history. Very detailed;
- Google Fit data. They can be exported;
- calls, contacts.
Hacking screen lock code
I would really like to write a detailed article on how and with what you can hack a locked Android smartphone, but I'm afraid this is impossible: users have thousands of different models based on dozens of chipsets in hundreds of variations. Taking into account the variety of firmware, versions of Android itself and the availability of current security patches (the very problem of Android fragmentation), a situation has developed in which even the largest manufacturer of forensic products does not know what devices their complex works with ... “Try to connect” is the standard answer to the question whether complex X supports smartphone Y.For example, a simple question: is it possible to hack the lock code for a specific smartphone model, and most importantly - do you need to do this or can you do it like that? Numerous security articles unanimously recommend setting a strong lock code, keeping silent about the fact that for about every second smartphone it is completely useless. How to determine if it makes sense to bother with a complex lock code or if you need to dig in the other direction?
The answer is related to the encryption algorithm used in a particular device. As you remember, all smartphones that left the factory with Android 6 and later are required to encrypt user data by the time the initial setup is completed. However, encryption is not the same. Most older devices use what is known as Full Disk Encryption (FDE). In FDE mode, data on the user partition is encrypted using device credentials - an encryption key that is generated based on a certain hardware key and a phrase default_password.
Yes exactly - default_password protects all your data. And what, is it all gone? Anyone can take and decipher the information? Not really. The encryption key is generated inside the Trusted Execution Environment (TEE) at the time of device boot; a key that is unique for each device, which does not go beyond the TEE, is used as the initial data. If you remove the memory chip from the phone and copy the information from it, then it will not be possible to decrypt the data without the key from TEE. Accordingly, to decrypt information, you will need not only to pull data from the phone (for example, through EDL mode), but also to hack TEE or replace the bootloader. In principle, such "decrypting bootloaders" exist, for example, at Cellebrite for a number of models, and sometimes for entire families of models, united by a common chipset.
Even if your phone uses outdated FDE protection, you can reliably protect your data by activating Secure Startup mode. In this mode, the encryption key will be re-encrypted with the data of the hardware key and your lock code (instead of default_password). This method also has a drawback: the phone simply will not boot until the moment you enter the lock code; if your phone accidentally reboots, you won't even be able to answer the call until the phone boots up to the end.
This flaw is completely eliminated in a new file-by-file encryption scheme called File Based Encryption (FBE). FBE encrypted devices use user credentials to encrypt most information, including all personal data. At the same time, the executable files of applications, as well as some databases required to boot the device, will be encrypted using device credentials (that is, data exclusively from the hardware key). There is no Secure Startup mode when using FBE because it is unnecessary.
To decrypt the data of both FDE devices using Secure Startup mode and devices with FBE, you need to crack the lock code. The specific procedures differ depending on the chipset, but the general principle is the same: connect to the USB port and start the brute-force procedure.
Of course, phones have built-in protection against such attacks. We have already described the Qualcomm TrustZone, which runs the Trusted Execution Environment (TEE). It can run only so-called trustlets, a kind of micro-applications signed with a key that is verified by the TEE itself. This is where the passcode check is implemented (via the GateKeeper service). GateKeeper, in turn, limits the speed of brute-force passwords at the hardware level; you can't even go through a four-digit code quickly, and six digits can be iterated over indefinitely. It is GateKeeper that will prevent hacking the phone when Secure Startup is enabled or if FBE encryption is used.
If there is protection, then there will be attempts to break it. In particular, for Qualcomm processors up to and including Snapdragon 821, there is an exploit that allows you to launch your own trustlet for execution and bypass the brute-force limit. In reality, the developers of forensic systems treat this vulnerability as a toothache: on the one hand, the vulnerability exists, it is an eyesore; customers want it. On the other hand, it is very difficult to use it: for each device you need to write your own code, select offsets, test ... If we were talking about an iPhone, the number of current chipsets of which can be counted on one hand, such a vulnerability would have been supported yesterday. But hundreds of modifications of chipsets used in smartphones with Android (and each model,
For flagship smartphones on Qualcomm processors, the ability to extract data through vulnerabilities looks something like this:
- for old devices (up to Snapdragon 821 inclusive) with exploits, it is sometimes possible to hack passcode if Secure Startup is not installed (many methods have been found);
- for old devices with Secure Startup enabled or with FBE encryption, the search speed is limited by GateKeeper. An attack on a "cold" device (after a reboot or power on) is practically not implemented, except for a few popular models (the problem of the "elusive Joe");
- for new devices (with Snapdragon 835 and newer) EDL exploits are not available, the TEE exploit is not available, and even in rare cases when FDE encryption is used, it is quite difficult to decrypt the contents of the data section (but in some cases it is possible, exploits exist);
- Finally, for newer devices (SD835 and newer) using FBE encryption, no exploits work: the encryption key depends on the password, and the brute-force attack is very slow (GateKeeper).
How to protect your smartphone from lock code cracking and physical data extraction
First, check which encryption system is used on your device. To do this, run the following command through ADB:
Code:
$ adb shell getprop ro.crypto.typeIf the command returned the word file, then your smartphone is using FBE encryption.
If using FBE file-by-file encryption:
- set a lock code with a length of at least six digits (if the device allows);
- disable USB Debugging.
- go to the settings and delete the current lock code;
- create a new lock code. The system will ask if you want to enable Secure Boot Mode. Confirm the request;
- don't forget to disable USB Debugging.
General recommendations
What are the typical recommendations for Android security articles? It is more difficult to use the lock code or the pattern is more authentic; disable Smart Lock; update Android; enable two-factor authentication. The advice sounds logical, but at the same time extremely superficial, in the style of "information security for blondes." Meanwhile, for every second Android smartphone, the length of the lock code does not affect security in any way; disabling Smart Lock is useless if the user has turned on (or forgot to turn off) the USB debugging mode, and there is no point in checking for Android updates if your device manufacturer is delaying updates.First, let's make our list of recommendations, and then go through some of the points in detail.
- Lock code. It is needed, and preferably at least six digits. In this case, you should check which encryption mechanism is used in your smartphone - FDE or FBE, and if FDE, then you need to enable Secure Startup.
- Disable USB debugging mode. Any other actions are meaningless if this mode is enabled.
- You are probably aware that an unlocked bootloader is a security hole? We will not even consider such cases, but if there is an OEM unlock item in the Developer settings of your phone, and you are not going to unlock the bootloader in the near future, disable it.
- If your phone has a mode setting in which the device should be available when connected to a computer, select “Charge only”. Otherwise, it will be possible to copy the contents of the memory card from your locked phone, including photos and videos. If there is no such setting, then check what happens when you connect. Typically, in modern devices, the Charge only mode will be selected by default. If so, everything is in order; if File Transfer or MTP is selected by default, you can give up on security.
- Of course, the latest version of Android is good, and the latest security patches are a must. The only problem is that the overwhelming majority of manufacturers are ugly delaying updates, leaving the vulnerabilities found unpatched for many months (or even years). If your phone is not the current flagship (or the current flagship Samsung or LG), then you can forget about quick updates. But check the updates anyway.
- Smart Lock is an absolute evil in terms of security. Disable all types of Smart Lock, including face unlock (only in Smart Lock; if your phone is equipped with a 3D scanner with infrared illumination - this advice is irrelevant).
- At the same time, disable the phone lock delay if it is configured (Settings → Security & Location → Automatically lock → Immediately).
- Did you forget about the installation from unknown sources? You shouldn't keep this switch active, it really makes your phone vulnerable. By the way, there is no separate setting in Android 8; permission is issued to individual applications, you can manage the setting through the Special app access settings item.
- Just the other day, there was a scandal: it turned out that a number of applications for the iPhone record user actions and transmit screenshots in the form of analytics, including personal data, passport and credit card numbers. There was no scandal in Android: absolutely any application with Draw over other apps permissions or launched as an Accessibility service can do the same. Check if there is anything extra.
- And then there is such a thing as Device admin. Apps from this category can be used to remotely change the lock code, lock or unlock the device, and reset the settings to factory defaults. If it's Google Find My Phone or Exchange Admin installed by your employer, then you're fine. Make sure that there are no unnecessary items on the list.
- You probably already know about the backdoors built by vendors. Many manufacturers build analytics tools into their phones' firmware. From time to time it turns out that "analytics" is your contacts with passwords. By and large, nothing can be done about it. You can try to restrict analytics access to the Internet (for example, with the AdGuard application installed, by the way, from third-party sources - from the developer's website, and not from the Play Store), but if you have such a device in your hands, then all possible data has long been leaked. Just accept it.
- Finally, about the apps from the Play Store. Many of them have requested (and most likely received) the wildest permits. For example, you could give "Birds" access to the camera, microphone and contacts (why?), An advanced calculator - access to the location, and a beautiful photo gallery - permission to read and send SMS. Take the time and go to the list of application permissions; for most users, a simple analysis of the permissions issued comes as a big surprise.
- Do not store your Google Account password in Chrome. They will be looking for him first.
- Turn on two-factor authentication. No comments; we have written on this topic more than once or twice.
Delayed blocking
Once upon a time, entering a lock code was the only, slow and inconvenient way to unlock your phone screen. Many users found it inconvenient to enter a password all the time; they abandoned protection in favor of convenience and speed. Delayed blocking was a logical reaction to the problem from both Google and Apple.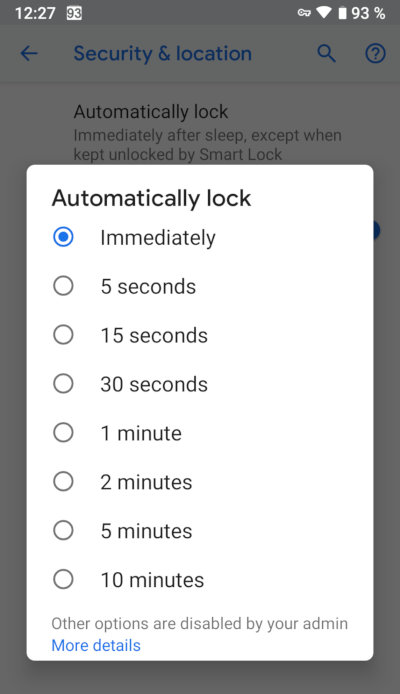
When the corresponding option was activated, it was possible to turn off the phone display with the button, turn it on again - and go directly to the home screen. The delay can be adjusted according to your own preference. Needless to say, blocking delay drastically reduces security? Imagine the situation: you are walking down the street, buried in your phone, and suddenly you rest against the chest of a policeman. Reflexively press the button to turn off the display, after which you are detained. They confiscate your phone, turn on the screen - and immediately go to your home screen. Passwords, lock codes, locked bootloader, encryption and many other things will no longer matter.
IOS has a similar setting: Settings → Touch ID & Passcode → Require Passcode. Its purpose is approximately the same as in smartphones with Android, with one important difference: if you use Touch ID or Face ID, in modern versions of iOS, the only available option is Immediately (that is, block immediately after the screen turns off) ... But if you turn off biometrics, leaving only the lock code, then other options will become available up to Never (ask for the lock code only after the first boot and from time to time in accordance with the constantly changing Apple policies) ... Please note that some options may not be available if an external security policy is installed on your device.
Smart Lock
Why is everyone so up against the Smart Lock feature? The fact is that this feature allows you to unlock your phone using methods that have nothing to do with security. Let's take a look at some examples.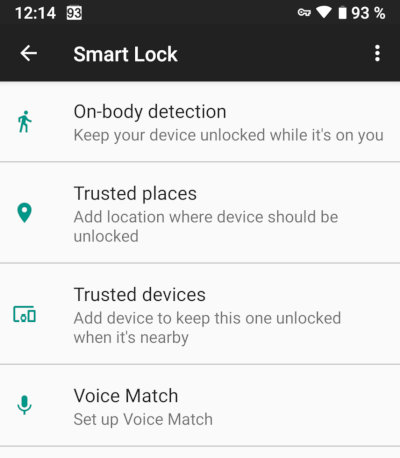
Face Unlock. Face unlock in the Smart Lock section has nothing to do with biometric authentication. This is just a comparison of the user's image with a photo taken with the front camera of the device. Such Face Unlock is easily fooled by flat photography. Please note: phones equipped with the Face Unlock biometric function (for example, Xiaomi Mi 8) will not have this item in the settings; in such devices, Face Unlock is subject to the same requirements and rules as fingerprint unlocking.
Trusted places. Automatically unlocks devices in the vicinity of the places you frequent. If the phone is pulled out of your pocket near your home, an intruder will have no problem unlocking it.
Trusted devices. If a trusted Bluetooth device is connected, the phone can be unlocked automatically. Trust me, the police will have no difficulty in using your smartwatch or tracker to unlock it.
Voice Match, On-body detection. To some extent experimental options that allow users to unlock the device less often with a lock code.
If Smart Lock is so insecure, why does Android even have one? Smart Lock is a heavy legacy from a time when entering a lock code or pattern was the only way to unlock your phone. The overwhelming majority of users did not like the fact that precious seconds were spent on unlocking the device (and unlocking the phone with gloves was another task); as a result, many did not install any protection at all. In order to somehow accustom users to setting the lock code, Google had to greatly lower the bar: so, there were options that allow you to delay the screen lock by 10-15 minutes from the moment of the last unlocking. Smart Lock - from the same opera. There is no reasonable need for either Smart Lock or delayed locking: modern fingerprint scanners work a little faster,
Face unlock
How safe is face unlocking? We didn't write about this in the iPhone section; they use a system with a sufficient level of technical safety. In smartphones with Android, manufacturers install face unlock modules, the security of which ranges from "good" to "the same Smart Lock, side view." For example, Samsung smartphones have a mode that combines a face image with scanning the iris of the eye; it will not be possible to deceive such a system with a 3D head model. Similar systems began to appear in the flagship devices of Huawei, Xiaomi and many others. At the same time, a number of devices use much more primitive systems based either on photography from the front camera or on a two-dimensional photo from an infrared sensor. It is quite possible to deceive such systems, sometimes very simple. As you correctly noted in the article "Face unlocking is not a good idea", the approach "My phone can do everything the same as your iPhone - and it costs ten times less!" will be more and more common.The legal aspect of face unlocking stands apart. A number of precedents have been set in the United States regulating the ability of the police to unlock a device by scanning a suspect's face. There are both positive (permission for unblocking by face was issued) and negative (permission was not issued or was issued illegally) precedents, and thanks to them, a fairly clear legal framework has been established, which in most cases the police will not cross ...
At the same time, in Russia, we have repeatedly heard about stories when the phone “accidentally” turned towards the detainee, after which it “by itself” was unlocked. In such cases, it is very difficult to prove that the phone was unlocked in violation of legal norms: Russian police officers are not yet equipped with body cameras, as in the United States.
Whether or not to use face unlocking is an open question, and the answer to it lies not only in the technical field; it's up to you to decide in any case. The author of this text uses this opportunity.
Unsafe security
And what can you do if you have a frankly "leaky" phone with an unlocked bootloader or a "Chinese" reflashed by cunning sellers? In this case, of course, there is no need to talk about serious security, but you can still do something.The first and easiest option: you have a phone in your hands, the bootloader of which is unlocked (for example, by the previous owner). Such situations are often complicated by the fact that a custom firmware is installed on the phone, there is root access, the system partition is modified, or it is completely unclear what is going on there. In most cases, such a phone can be returned to the "factory" state by flashing it to the factory firmware (where to download, they will advise on XDA or w3bsit3-dns.com), after which the bootloader can be locked with the fastboot oem lock command. We especially recommend doing this with Chinese devices, on which cunning sellers often (more often than you can imagine!) Install firmware with a wide variety of surprises.
Please note: this strategy will not work with fresh Xiaomi phones flashed from the Chinese stock to the "global" version of MIUI. If you try to lock the bootloader on such a device, you will get a "brick", which can be very, very difficult to recover. If you do decide to try it, at least set up a Xiaomi Account on your phone, so that later, if something goes wrong, you can use the Mi Unlock utility to unlock the bootloader.
But what if the bootloader cannot be locked (this is often the case on many Chinese devices)? So you're out of luck. However, if you purchased such a device, then, probably, security is the last of the problems of such a phone. In theory, even on such devices, encryption will work, which will not allow data to be read just like that. In practice, hacking such devices usually presents no problem. The only thing you can try to do is configure Secure Startup; in this mode, the data encryption key will be generated based on the lock code. A long enough lock code will increase the time it takes to crack.
What if you bought a phone that behaves strangely? At the slightest suspicion of malware in the firmware, go to the profile branch on w3bsit3-dns.com. It is likely that you are not alone with this problem, and the forum already has detailed instructions on how to remove or freeze malware.
But what if the manufacturer does not release updates, and malicious components are firmly registered in the firmware? Of course, it would be a smart move to get rid of such a device, but in the real world, so few people do. Therefore, a recommendation: try to unlock the bootloader (it won't get any worse) and install the official assembly of Lineage OS on your phone. In official Lineage builds (unlike, for example, Resurrection Remix), everything is fine with privacy, encryption, and over-the-air updates. Depending on the firmware version available for your device, both FDE and FBE encryption can be used; in the first case, we recommend setting up Secure Startup. If there are no Lineage assemblies or it is impossible to unlock the bootloader, then I would not give such a phone even to a child.
If they took the computer
After discussing the security of your data on a mobile device, let's talk about how computer analysis can affect the security of your mobile devices. If an expert has gained access to your computer, and you do not use full-disk encryption (for example, through BitLocker), then launching a simple utility and one or two lazy mouse clicks will extract all logins and passwords from all your accounts. Where? From your favorite browser's database: Chrome, Mozilla, Edge ... Do you use a password manager? If developing you as a suspect is of any interest, then the password keeper will try to guess the password for the database (here, however, the result is not guaranteed).What happens when passwords are retrieved? Depending on which smartphone you are using, the expert will launch another application that will retrieve all the information from the cloud from Apple, Google or, for example, Samsung. (In brackets: if you use a Samsung smartphone, do you know what exactly is stored in the corresponding cloud, even if you did not turn it on deliberately?)
If you use an iPhone, you can extract from the cloud:
- backups (by the way, not always; if you have a fresh version of iOS and two-factor authentication is activated, you won't be able to download the backup copy.However, if you still have old backups created by devices with iOS 11 or older, you will be able to extract them.: See what you have stored in the cloud and delete unnecessary backups!);
- synchronized data: contacts, notes, calendars, Safari browser bookmarks, and more;
- Photos (if you have iCloud Photo Library turned on), including recently deleted photos;
- call log and browser history;
- some map data;
- if they find out the lock code for your phone or the password from the Mac computer, then all cloud passwords (iCloud Keychain) and Health data (a log of your daily activity), as well as SMS and iMessage.
- backups and application data (by the way, in Android, it is in this category that call logs, SMS, as well as authentication tokens of individual applications will be stored);
- synchronized data: calendars, contacts, notes;
- Chrome passwords (there is no additional protection, as in iOS, for them);
- the most detailed history of the location over the past many years. Perhaps this point will be paid attention to in the first place;
- browser and search history. It is investigated without fail;
- Gmail mail, which you can use, for example, to reset passwords for other accounts.
If you have a Samsung phone, you can get some more out of Samsung's own cloud. We understand that for many readers Samsung's own cloud service will come as a surprise, and the fact that it turns out to store some data (and at some point you managed to agree with this) can be very surprising. In the Samsung cloud, you can find:
- backups (interestingly, Samsung stores not only application data, but also APKs in the cloud);
- Photos (unless you made a conscious effort to turn off photo sync to the cloud)
- Samsung Health data;
- Samsung watches and trackers backups.
- backups. It is rather scarce here: APK and phone settings are saved, but application data is not saved;
- contacts, SMS;
- photos if you have enabled sync.
Multi-layered protection can help.
First, keep your computer physically secure by enabling BitLocker to encrypt the system drive. By the way, make sure that the BitLocker Recovery Key is not leaked to the OneDrive cloud (you can check it here) or is not saved in Active Directory.
If you live in Russia, then you won't be able to just take and encrypt the system disk. In order to enable encryption, you need at least a professional edition of Windows and a hardware trusted boot module TPM 2.0. It is in the hardware module that the encryption key itself must be stored, with which the partition will be encrypted. TPM 2.0 modules have not received FSB certification; accordingly, all computers sold in the Russian Federation should not include this module by default, even if it is physically wired to the motherboard. Options? If it is possible to activate TPM 2.0 in the BIOS settings, do it and enable BitLocker. If this is not possible, then you can enable encryption of the system partition using BitLocker without the hardware module. You can do this manually by editing Windows Group Policies.
The next layer of protection is passwords for cloud accounts. For cloud services Google, Apple, Samsung, Xiaomi, use unique passwords, unlike all those stored in the browser storage. Launch your favorite, not the most beloved and completely unloved browsers and make sure that their storage does not contain the data of the above accounts. If you are using Chrome, sign out of your Google account. Erase your browser cache and cookies, then close all windows. Everything, for some time (until you log into your Google Account again) you are protected from the cloud attack vector.
The use of such a system will slightly affect the convenience of everyday use, but will significantly increase safety.
Lockdown
IPhone users have an additional risk factor: the lockdown file, aka iTunes pairing record. These files are created when you connect your iPhone or iPad to a computer that has iTunes installed; they are needed so that using iTunes you can synchronize the device with your computer without constantly entering the lock code. On the one hand, the presence of a pairing record mechanism is a convenience. On the other, vulnerability. For example, Elcomsoft tools allow you to use lockdown files to create a backup copy of your phone, even if the screen is locked (but the phone itself has been unlocked at least once since bootup). Under the same conditions, GrayKey's solution allows you to create a complete image of the file system (albeit so far only for iOS 11).How to protect yourself? On the one hand, you can delete lockdown files from your computer; on Windows 10 they are located in the C: \ Users \ <username> \ AppData \ Roaming \ Apple Computer \ MobileSync \ Backup folder (if you installed iTunes from the Apple website) or in the C: \ Users \ <username> \ Apple \ MobileSync folder \ Backup (if you're using the Microsoft Store version of iTunes).
But you can't just delete these entries on the iPhone; you can only reset all trusted entries at once via Settings → General → Reset → Reset Location & Privacy. By the way, to reset you will need to enter the lock code. Another way to delete trusted entries is to reset the Reset Network Settings. But Reset All Settings does not affect the trust records in any way (but it deletes the password for the backup copy).
How real are the risks associated with computer analysis? According to the police themselves, research on computers is rare. Typically, the police face the following obstacles:
- obstacles of a legal nature: the existing decree allows the search and analysis of evidence that the detainee had with him (but does not give permission to search the apartment);
- time limits: the work of the Expert Advisor is on stream. In routine cases, the expert does not have a month, week, or even several days to analyze in detail all available evidence;
- BitLocker password is extremely strong. Head-on attacks are doomed if the police cannot extract a ready-made encryption key through, for example, FireWire Attack;
- superficial examination: as a result of strict time frames, the contents of the hard disk are scanned for very specific files (photo and video materials, correspondence, messenger databases);
- even if a full analysis is undertaken, very often the required passwords are not found in the browser cache;
- even if the required passwords are there, there are no backups in the suspect's cloud at all, or there are enough fresh backups. Even for iOS, this is a typical situation: if you leave all the default settings, then the scanty 5 GB of free space in the cloud will be crammed with synced photos in no time. There will be no more space left for backups. But Android users will remain: both backups and photos in "standard" quality are not counted in the already generous quota of 15 GB.
