Teacher
Professional
- Messages
- 2,669
- Reaction score
- 819
- Points
- 113
Playing on the victim's curiosity increases the scammers chances of success.
Cybersecurity experts at Check Point found a sharp increase in the number of attacks using fake voice messages in email. In the past two weeks alone, researchers have identified more than 1,000 incidents in which attackers use corporate phone systems to send fraudulent notifications.
The main attack method is sending emails containing phishing links under the guise of voice mail messages. That is, at first glance, the email contains a built-in MP3 player, which in fact turns out to be a link that allegedly redirects the victim to the login page of the service from which he received this email. It is there, according to legend, that the victim will be able to listen to the sent voice message.
Needless to say, scammers use the most popular companies in their mailings that employees of the attacked organization can actually work with. And the imitation of a recorded message to voice mail only inflames the victim's curiosity, in connection with which she hastily enters authorization data on a fake page belonging to hackers.
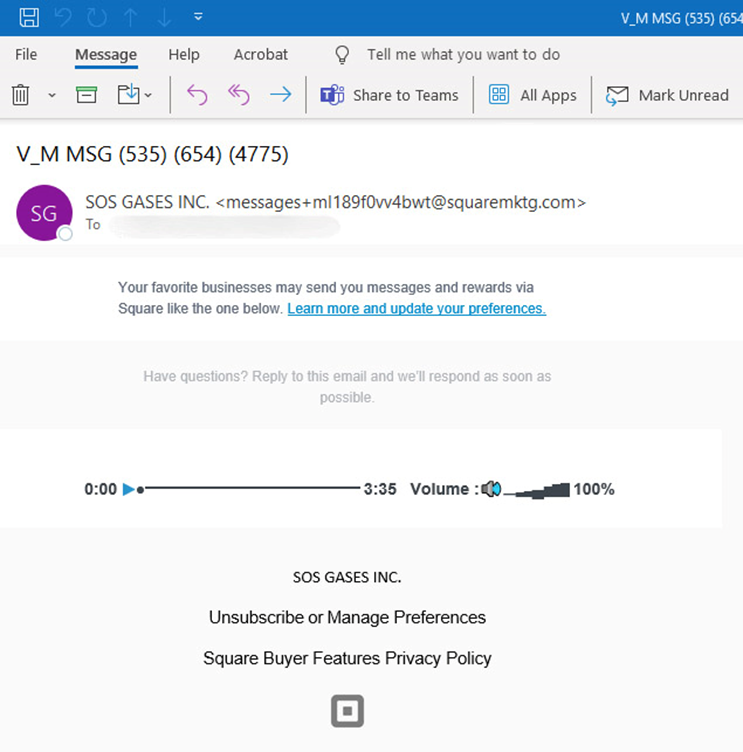
Phishing email with an MP3 player
In the example above, analyzed by Check Point specialists, the attackers disguised themselves as the Square payment processing service by sending emails with fake voice messages. The subject line of the email contained a phone number that was invalid when checked through Google.
This attack requires the active participation of the user-opening the link and entering personal information, but, as mentioned above, hackers play on the curiosity of their victims, so this method works successfully.
Cybersecurity experts at Check Point found a sharp increase in the number of attacks using fake voice messages in email. In the past two weeks alone, researchers have identified more than 1,000 incidents in which attackers use corporate phone systems to send fraudulent notifications.
The main attack method is sending emails containing phishing links under the guise of voice mail messages. That is, at first glance, the email contains a built-in MP3 player, which in fact turns out to be a link that allegedly redirects the victim to the login page of the service from which he received this email. It is there, according to legend, that the victim will be able to listen to the sent voice message.
Needless to say, scammers use the most popular companies in their mailings that employees of the attacked organization can actually work with. And the imitation of a recorded message to voice mail only inflames the victim's curiosity, in connection with which she hastily enters authorization data on a fake page belonging to hackers.

Phishing email with an MP3 player
In the example above, analyzed by Check Point specialists, the attackers disguised themselves as the Square payment processing service by sending emails with fake voice messages. The subject line of the email contained a phone number that was invalid when checked through Google.
This attack requires the active participation of the user-opening the link and entering personal information, but, as mentioned above, hackers play on the curiosity of their victims, so this method works successfully.

